Shodan a Search Engine for Hackers (Beginner Tutorial)
Many people have described Shodan as a search engine for hackers, and have even called it “the world’s most dangerous search engine”. It was developed by John Matherly in 2009, and unlike other search engines, it looks for specific information that can be invaluable to hackers. John Matherly is an Internet Cartographer, hence the shodan.
Shodan is a type of search engine that allows users to search for Internet-connected devices and explicit website information such as the type of software running on a particular system and local anonymous FTP servers. Shodan can be used much in the same way as Google but indexes information based on banner content, which is meta-data that servers send back to hosting clients. For the best results, Shodan searches should be executed using a series of filters in a string format.
So, in conclusion, we can say that Shodan is a search engine for finding specific devices, and device types, that exist online. It is like an internet map that lets us see which device is connected to which or ports are open on a specific device or what operating system a certain system is using, etc. Rather than to locate specific content on a particular search term, SHODAN is designed to help the user find specific nodes (desktops, servers, routers, switches, etc.) with specific content in their banners.
What Shodan can do?
Shodan pulls service banners from servers and devices on the web, mostly port 80, but also ports 21 (ftp), 22 (SSH), 23 (telnet), 161 (SNMP), and 5060 (SIP). Since almost every new device now has a web interface (maybe even your refrigerator) to ease remote management, we can access innumerable web-enabled servers, network devices, home security systems, etc. Shodan can find us webcams, traffic signals, video projectors, routers, home heating systems, and SCADA systems that, for instance, control nuclear power plants and electrical grids. If it has a web interface, Shodan can find it! Although many of these systems communicate over port 80 using HTTP, many use telnet or other protocols over other ports. Keep that in mind when trying to connect to them.
How to use Shodan?
Understanding shodan is very important at first you might find it complex but once you get to know it you will find it very handy in use and very resourceful too. So, now let us learn how to work with fascinating search engine. To use shodan to your advantage you have
Follow the steps to register. After registration, a link will be sent to your e-mail ID for your activation of account on Shodan. Once your account is activated login to Shodan and now that you are logged in you are free to search for anything.
Here are some examples for which you can use shodan to search up the things you want.
Webcam
When you search for webcam, it will show you all the webcam present in the world. It will show the results as shown in the image below :

Traffic Signals
Searching about traffic signals or traffic signals camera then it will show you all the traffic surveillance camera present.

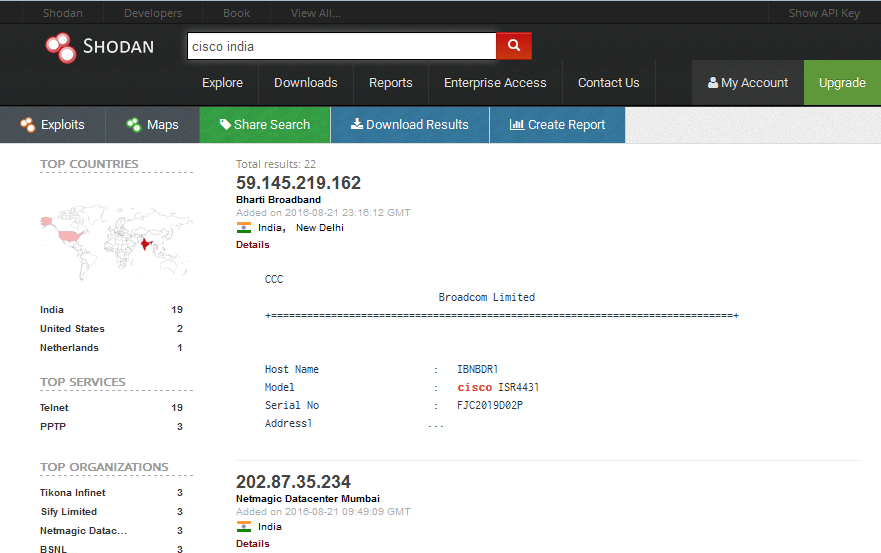
Cisco
Searching about Cisco will show you all the Cisco routers in the world but you can search them by country. Like, here, I have found Cisco routers in India and the result is below image :
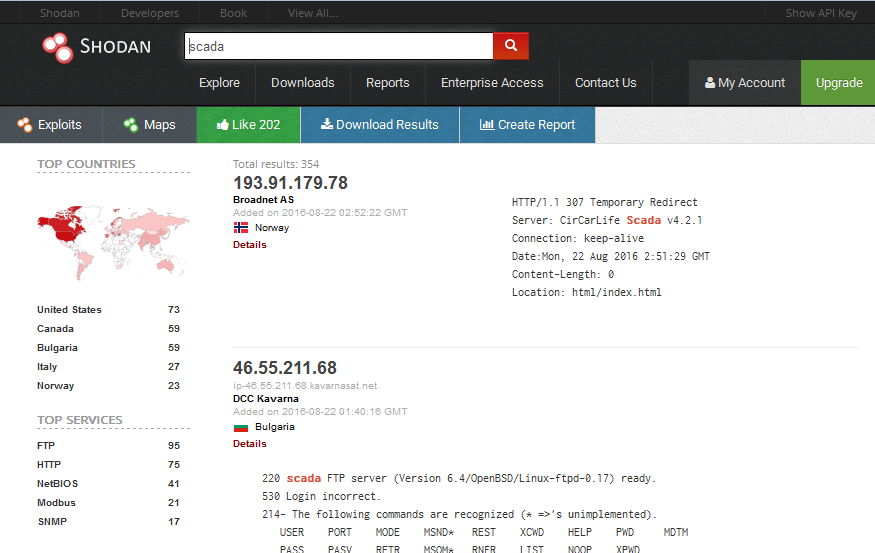
Scada
You can also search about Scada and you will get its information around the whole world as shown :
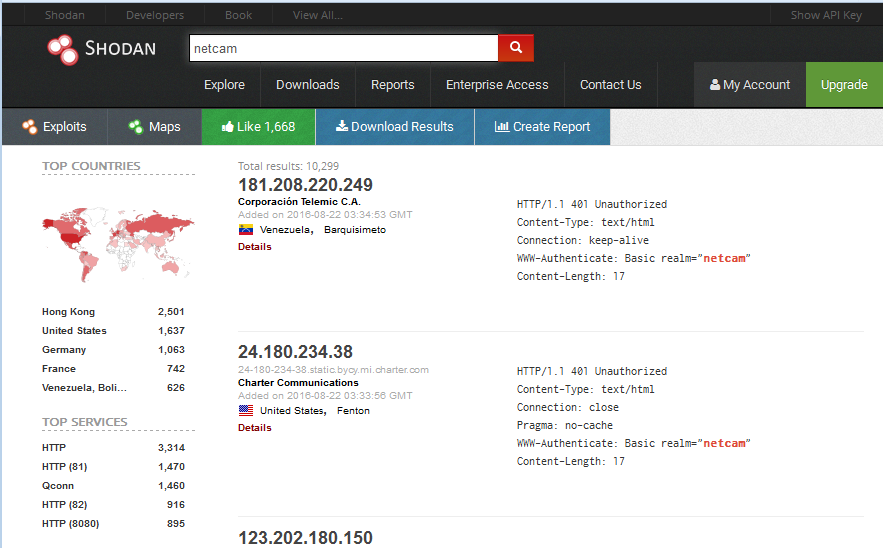
netcam
Shodan can also show you about all the netcams in the world and you can access them too for testing.
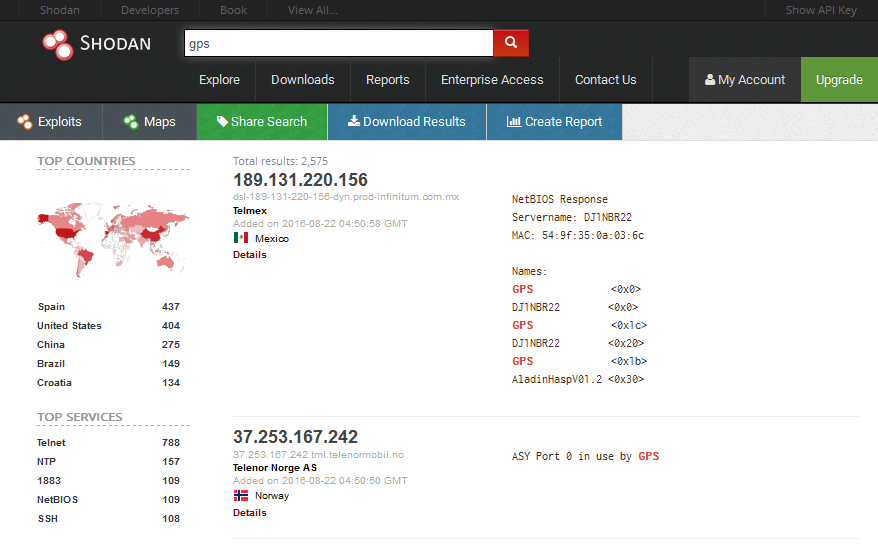
GPS
Shodan even lets you find all the GPS devices all over the world and for this, you just have to type GPS in the search box.
Port
Not only the devices but it can help to find which port is open in which device. For example, I have here searched port: 1723. Now we all know this port is used for VPN so through this we can know which device is using VPN as shown in the image below :

When you search for port: 3389 it will show the operating system used by the device too which can be very useful.
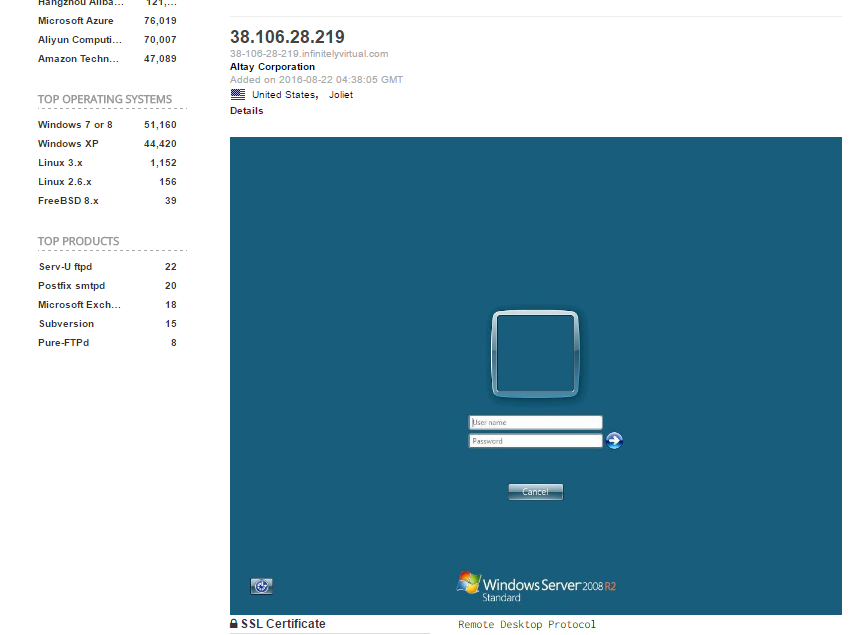
This is how Shodan is useful for hackers as it gives all the information necessary to collect that too all over the world. And so you can manipulate this information as you desire.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
I saw you posted something about spyse.com but didn’t see anything like this. Would be awesome to have a tutorial for beginners.