Metasploit for Pentester: Clipboard
In this series of articles, we will be focusing on the various mechanisms of the Metasploit Framework that can be used by Penetration Testers. Here, we will be discussing the External API extension provided by Metasploit. Among other things, it provides the ability to target the clipboard of the target.
Table of Content
- Introduction
- Starting Clipboard Monitoring
- Getting a File from Clipboard
- Dumping Clipboard Data
- Pausing the Clipboard Capture
- Purging Clipboard Capture
- Setting Clipboard Data
- Stopping Clipboard Capture
- Conclusion
Introduction
During the late 2014s, the Metasploit got an update featuring a functionality similar to the OJ TheColonial Reeves Extended API (extapi). It is originally intended for the Windows targets only, but it was refined and developed over time. It included 3 functionalities:
Service Management: With the help of this Meterpreter users will be provided a service management interface. It will allow them to get a more detailed read of services running on the target, including the start-up status and services that can interact with the desktop.
Window Management: With the help of this users will be able to enumerate all open Windows. This will help the penetration testers to find out if the target is worth connecting via VNC at a particular time.
Clipboard Management: At last, the one that we will be discussing in detail in this post. It allows the attacker to read from the target’s clipboard and write to it as well. It is not limited to text but you can use it to download files and images too.
To begin, we need to have a meterpreter shell on a target machine. We will then use the load command to get the external api module loaded in the session as demonstrated below.
load extapi

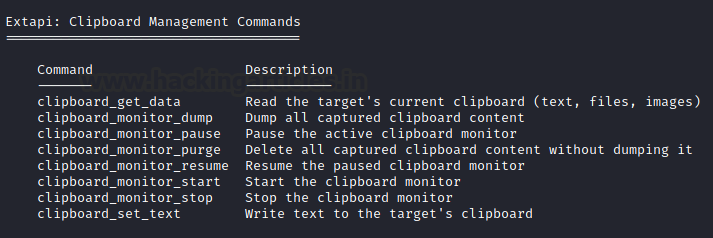
Running the help command will generate the command that can be run from the meterpreter shell but with the addition of the command that are part of the Extapi module as well. Here, we can see that we have the command for reading the target’s clipboard data, dump captured clipboard data, Initialize, Pause, Resume and Terminate the capturing of the Clipboard data and setting the data to the target clipboard as well.
Starting Clipboard Monitoring
This module doesn’t not indefinitely capture the clipboard data as the clipboard gets overwritten time to time as soon as the target copies another data into the memory. This data can range from text to files. It is surprising the amount of data that can be obtained from the clipboard. To initialize the capture, we will use the clipboard_monitor_start command.
clipboard_monitor_start

Getting a File from Clipboard
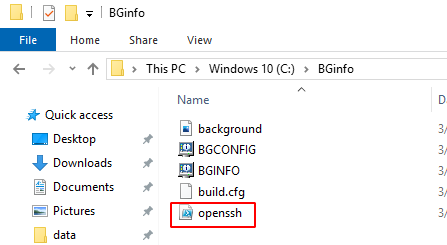
After starting the clipboard monitoring using the command in the previous section, we move to our target machine to stimulate the Copying of files. Here we can see that inside a directory we are copying a PowerShell script file named OpenSSH. It is quite possible that it might contain a key that can be used to connect via SSH service.
Back to our attacker machine to the meterpreter shell. Here, we run the get data command to retrieve the file copied on the clipboard.
clipboard_get_data

Dumping Clipboard Data
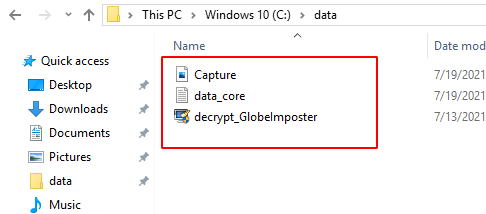
We just grabbed a singular file from the target but what if we want to get multiple files that are copied on its clipboard. To stimulate this, we again get back to the target machine. Here, we see that the target has an image file, text file and an application file inside a directory by the name of data. As the target user, we copied all the files inside the directory.
Back to our attacker machine to the meterpreter shell. Here, we run the dump command to retrieve the files copied on the clipboard. We can see that the OpenSSH file was downloaded again. It is because we initialized the capture earlier, so any files that were copied since then will be retrieved.
clipboard_monitor_dump

Pausing the Clipboard Capture
It is possible to get a large capture that could result in a failure and the amount of data transfer can raise some flags. Hence, it is recommended to pause the capture when you are not actively gathering the clipboard data from the target machine. If you ever want to un pause the capture, use the resume command.
clipboard_monitor_pause

Purging Clipboard Capture
The next command to discover is another that can help while working with the clipboard data. The amount of data captured by the clipboard can be overwhelming or maybe you just want to remove the captured data altogether. In such scenarios, you can use the purge command. In the demonstration, we tried to dump the capture after running the purge and we can see that there is no data in the capture.
clipboard_monitor_purge

Setting Clipboard Data
While introducing the clipboard commands, we said that it is possible to set the clipboard of the target machine as well. We need to use the set text command for this task. We take the text that we want to be stored inside the clipboard of the target user and then use it as a parameter between the double quotes as demonstrated in the image below.
clipboard_set_text “You have been hacked”

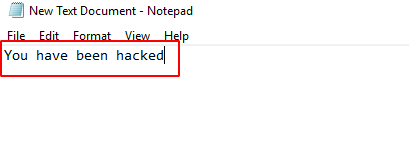
To stimulate the response from the target end, we move back to the Target machine and open a text editor. Then we paste onto the text editor to find the same text stored inside the clipboard as we set through our attacker machine.
Stopping Clipboard Capture
Similar to the Pausing of the Clipboard. There is a command to stop the capture altogether. The difference between the both is that while Paused capture can be resumed but the stopped cannot be resumed and the data that is captured is not accessible after the fact.
clipboard_monitor_stop

Conclusion
Concluding this article, we can say that this was one of the lesser-known mechanisms of the Metasploit Framework that can be used by any Penetration Tester. We will be discussing about the External API extension provided by Metasploit later.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn