Fast Incident Response and Data Collection
In this article, we will gather information utilizing the quick incident response tools which are recorded beneath. All these tools are a few of the greatest tools available freely online. Through these, you can enhance your Cyber Forensics skills.
Table of Contents
- Live Response Collection-Cederpelta Build
- CDIR(Cyber Defense Institute Incident Response) Collector
- Fast IR Collector
- Panorama
- Triage-Incident Response
- IREC -IR Evidence Collector | Binalyze
- DG Wingman
Introduction
Incident Response
- Incident response, organized strategy for taking care of security occurrences, breaks, and cyber attacks.
- IR plan permits you to viably recognize, limit the harm, and decrease the expense of a cyber attack while finding and fixing the reason to forestall future assaults.
Data Collection
- Data collection is the process to securely gather and safeguard your client’s electronically stored information (ESI) from PCs, workstations, workers, cloud stores, email accounts, tablets, cell phones, or PDAs.
Proof of Concept
Live Response Collection-Cederpelta Build
Live Response Collection -cedarpelta, an automated live response tool, collects volatile data, and create a memory dump. .This tool is created by BriMor Labs.
You can download the tool from here.
The live response is a zone that manages gathering data from a live machine to distinguish if an occurrence has happened. Such information incorporates artifacts, for example, process lists, connection information, files stored, registry information, etc.
It supports Windows, OSX/ mac OS, and *nix based operating systems. This instrument is kind of convenient to utilize on the grounds that it clarifies quickly which choice does what.
Let’s begin by exploring how the tool works:
The live response collection can be done by the following data gathering scripts
- Secure-Complete: Picking this choice will create a memory dump, collects volatile information, and also creates a full disk image. All the information collected will be compressed and protected by a password.
- Secure-Memory Dump: Picking this choice will create a memory dump and collects volatile data. All the information collected will be compressed and protected by a password.
- Secure- Triage: Picking this choice will only collect volatile data. All the information collected will be compressed and protected by a password.
- Complete: Picking this choice will create a memory dump, collects volatile information, and also creates a full disk image.
- Memory dump: Picking this choice will create a memory dump and collects volatile data.
- Triage: Picking this choice will only collect volatile data.
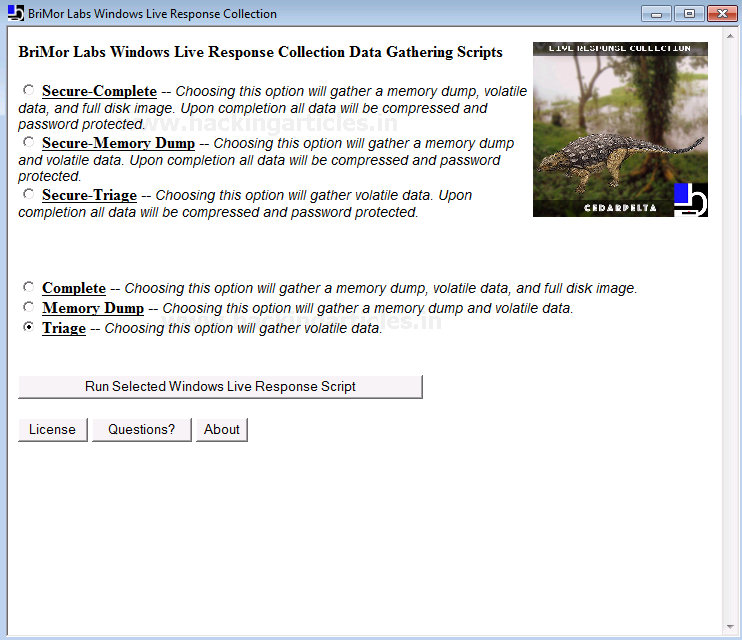
The process of data collection will begin soon after you decide on the above options. This might take a couple of minutes.
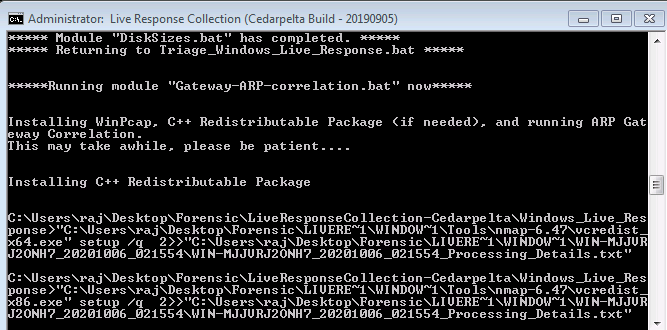
After, the process is over it creates an output folder with the name of your computer alongside the date at the same destination where the executable file is stored.
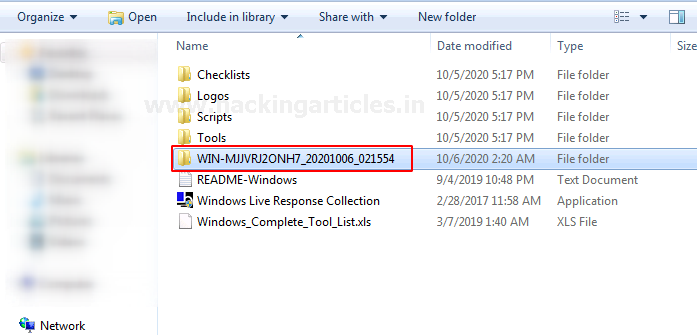
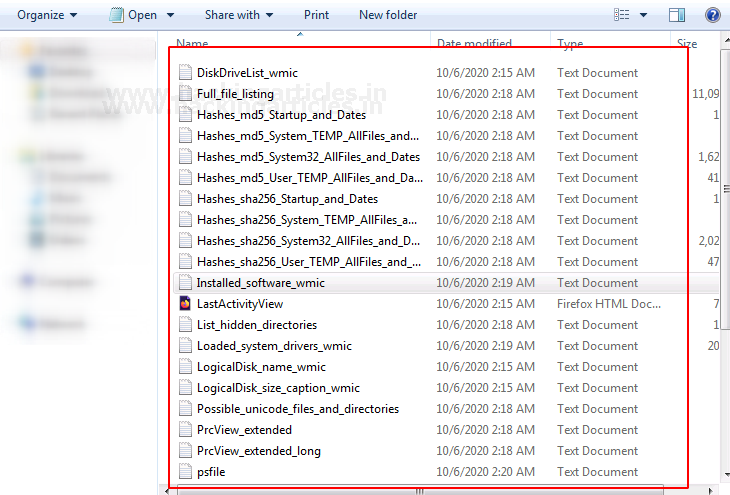
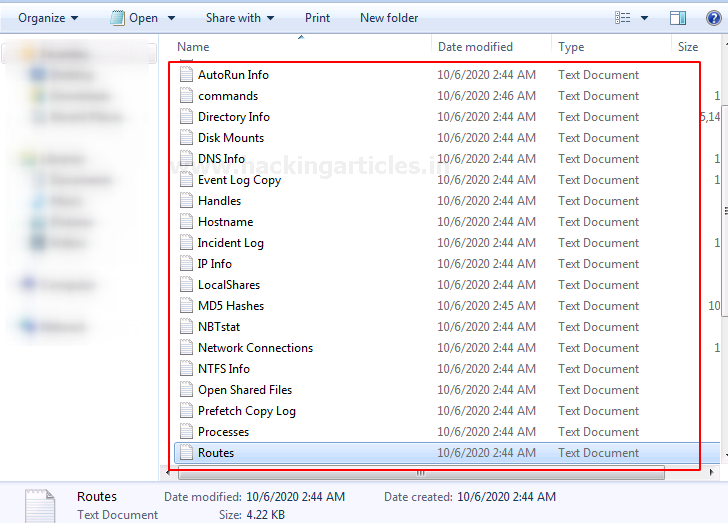
The output folder consists of the following data segregated in different parts.
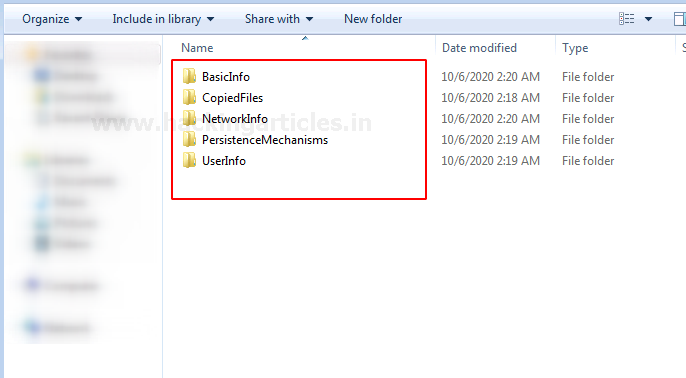
These are few records gathered by the tool. You can check the individual folder according to your proof necessity. It collects RAM data, Network info, Basic system info, system files, user info, and much more.
CDIR (Cyber Defense Institute Incident Response) Collector
CDIR (Cyber Defense Institute Incident Response) Collector is a data acquisition tool for the Windows operating system. The tool is created by Cyber Defense Institute, Tokyo Japan. The tool collects RAM, Registry data, NTFS data, Event logs, Web history, and many more.
You can download the tool from here.
Let’s begin by exploring how the tool works:
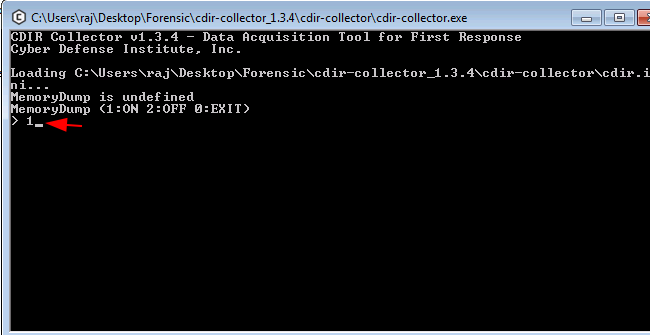
There are three options
- To initiate the memory dump process (1: ON)
- To stop the memory dump process and (2: OFF)
- Exit (0: EXIT)
After successful installation of the tool, to create a memory dump select 1 that is to initiate the memory dump process (1:ON)
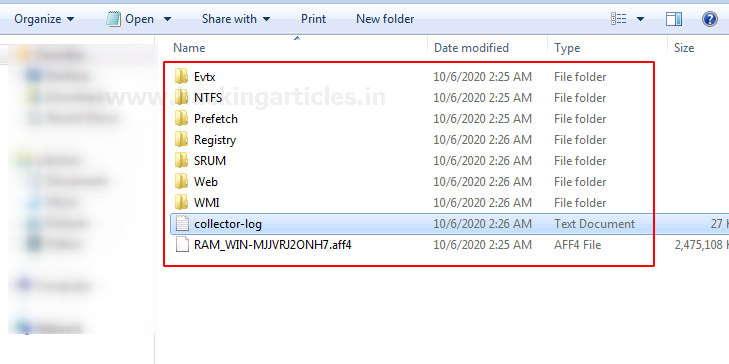
Soon after the process is completed, an output folder is created with the name of your computer alongside the date at the same destination where the executable file is stored.
Fast IR Collector
Fast IR Collector is a forensic analysis tool for Windows and Linux OS. It gathers the artifacts from the live machine and records the yield in the .csv or .json document. Windows and Linux OS. This tool is created by SekoiaLab.
You can download the tool from here.
Let’s begin by exploring how the tool works:
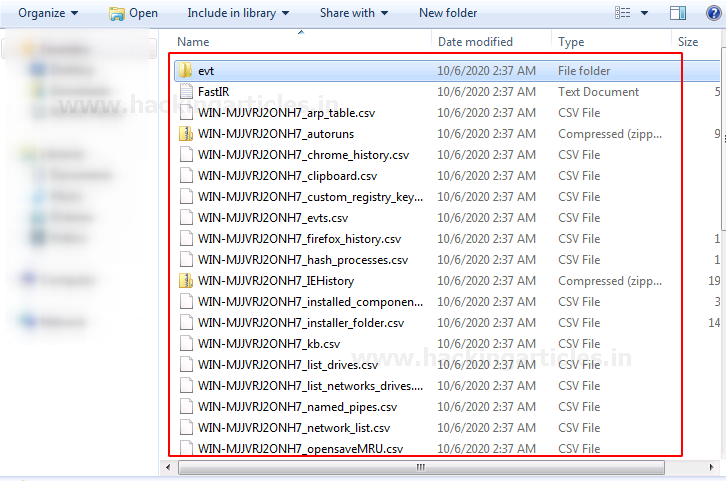
You just need to run the executable file of the tool as administrator and it will automatically start the process of collecting data.

Results are stored in the folder by the named output within the same folder where the executable file is stored.
Panorama
Panorama is a tool that creates a fast report of the incident on the Windows system.
You can download the tool from here.
Let’s begin by exploring how the tool works:
- Run the Panorama.exe on the system.
- Choose “Report” to create a fast incident overview.
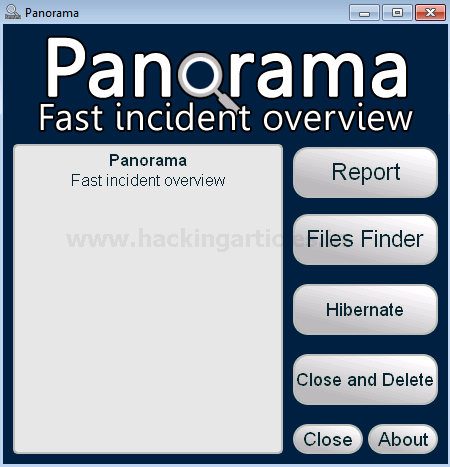
The browser will automatically launch the report after the process is completed.
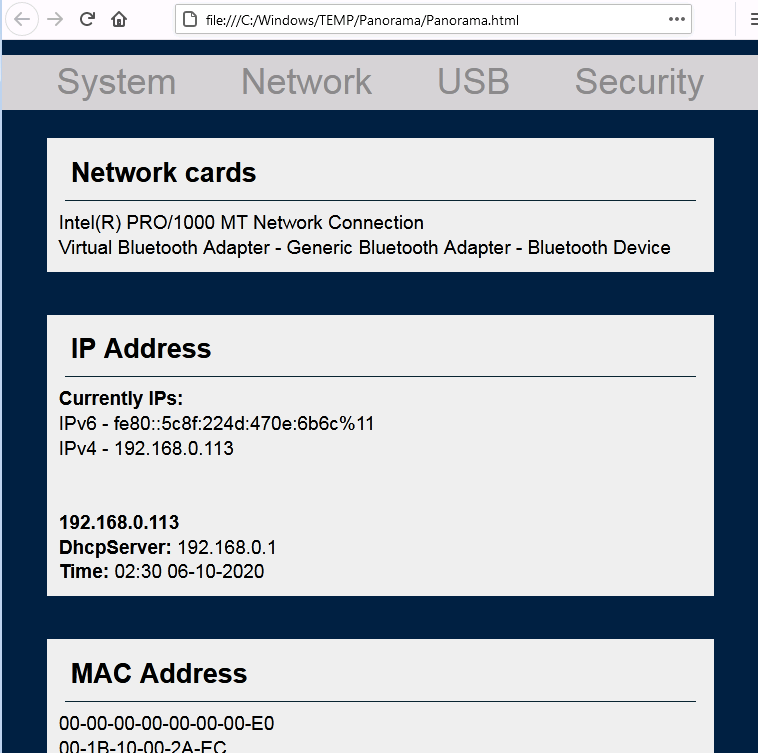
The report data is distributed in a different section as a system, network, USB, security, and others.
Triage
Triage is an incident response tool that automatically collects information for the Windows operating system. Triage-ir is a script written by Michael Ahrendt.
You can simply select the data you want to collect using the checkboxes given right under each tab. Triage IR requires the Sysinternals toolkit for successful execution.
Download here.
Let’s begin by exploring how the tool works:
- Run the executable file of the tool.
- Select “Yes” when shows the prompt to introduce the Sysinternal toolkit.
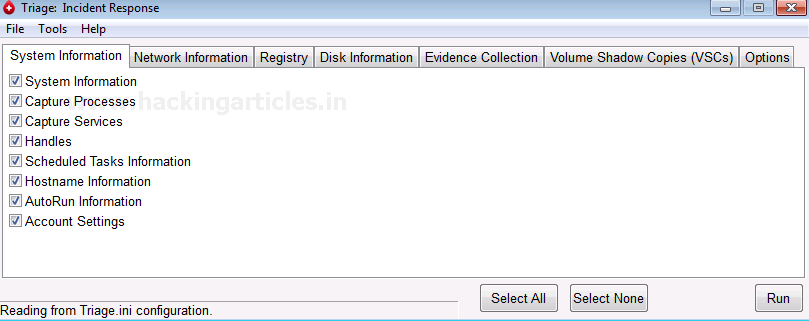
Click on “Run” after picking the data to gather. The process of data collection will take a couple of minutes to complete.
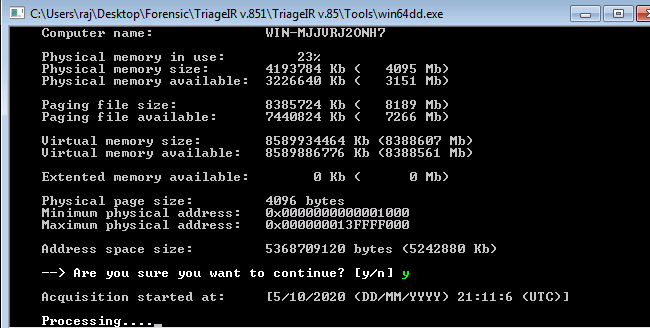
The data is collected in the folder by the name of your computer alongside the date at the same destination as the executable file of the tool.
IREC – IR Evidence Collector | Binalyze
IREC is a forensic evidence collection tool that is easy to use the tool. It is an all-in-one tool, user-friendly as well as malware resistant. This tool is created by Binalyze. A paid version of this tool is also available.
Download the tool from here.
Let’s begin by exploring how the tool works:
You can collect data by two means:
- Collect evidence: This is for an in-depth investigation.
- RAM and Page file: This is for memory only investigation
Here we will choose, “collect evidence.” for in-depth evidence. Click start to proceed further.

The process has been begun after effectively picking the collection profile.
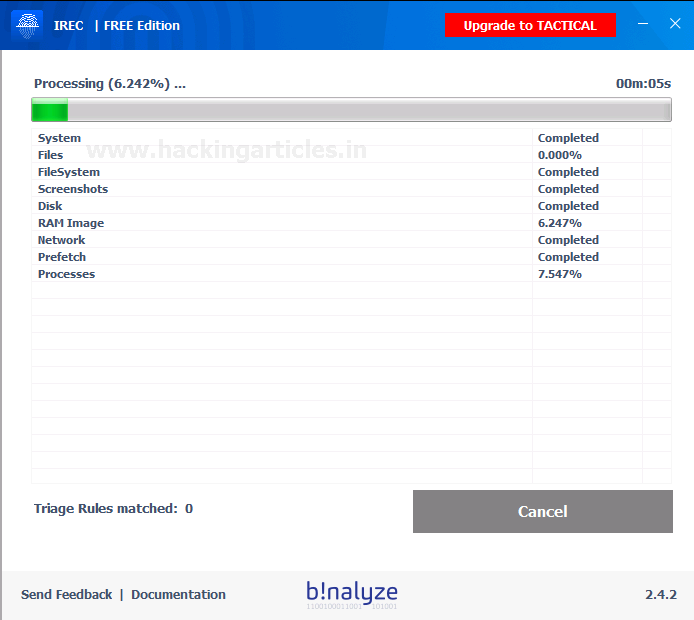
The process is completed. You can analyze the data collected from the output folder.

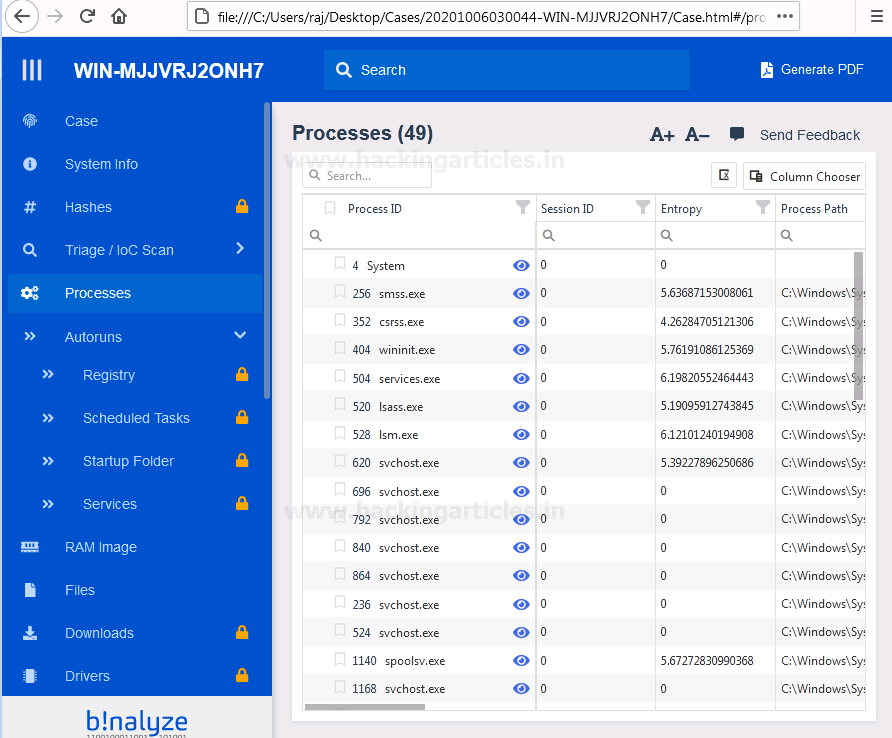
The output will be stored in a folder named cases that will comprise of a folder named by PC name and date at the same destination as the executable file of the tool.

Here is the HTML report of the evidence collection. The HTML report is easy to analyze, the data collected is classified into various sections of evidence. You can also generate the PDF of your report.
DG Wingman
DG Wingman is a free windows tool for forensic artifacts collection and analysis. The tool is by DigitalGuardian. This tool collects artifacts of importance such as registry logs, system logs, browser history, and many more. Also allows you to execute commands as per the need for data collection.
You can download the tool from here.
Let’s begin by exploring how the tool works:
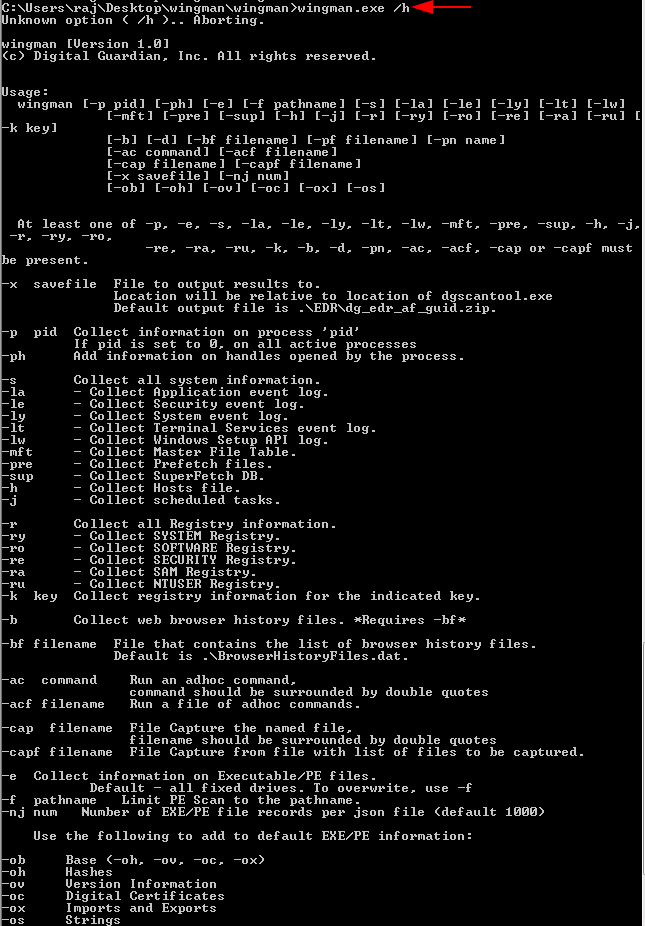
- Run the executable file of the tool.
- Use the command wingman.exe/h, this gives you a rundown of commands along with their capacities.
For example, in the incident, we need to gather the registry logs. We will use the command
wingman.exe -r

All the registry entries are collected successfully.
These are the amazing tools for first responders. And they even speed up your work as an incident responder. These tools come handy as they facilitate us with both data analyses, fast first responding with additional features.
Author: Vishva Vaghela is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
Please could I have this article?
Thanks
Thank you for your review. We highly suggest looking into Binalyze AIR, that is the enterprise edition of IREC.