CTF Collection Vol.1: TryHackMe Walkthrough
Today we’re going to solve another Capture The Flag challenge called “CTF collection Vol.1 “. It’s available at TryHackMe for penetration testing practice. This lab is not difficult if we have the right basic knowledge of cryptography and steganography. The credit for making this lab goes to DesKel, you can surf it from here. So, let’s get started and learn how to break it down successfully.
Level: Easy
Table of Content
Task 1 Author note
Task 2 What does the base said?
Task 3 Meta meta
Task 4 Mon, are we going to be okay?
Task 5 Erm……Magick
Task 6 QRrrrr
Task 7 Reverse it or read it?
Task 8 Another decoding stuff
Task 9 Left or right
Task 10 Make a comment
Task 11 Can you fix it?
Task 12 Read it
Task 13 Spin my head
Task 14 An exclusive!
Task 15 Binary walk
Task 16 Darkness
Task 17 A sounding QR
Task 18 Dig up the past
Task 19 Uncrackable!
Task 20 Small bases
Task 21 Read the packet
[TASK 2] What does the base say?

In this task, we can conveniently recognize that the value is base64 encoded. We will then attempt to decode it using the base64 decoder.

And there is how we got our 2nd flag easily.
[TASK 3] Meta meta

As the role name itself specifies the term meta, therefore, we are clear that here we have to take out the metadata of the image. Thereby we’ve used the EXIF tool as it is the most powerful one.
exiftool findme.jpg /root/Downloads/Findme.jpg

And as expected we get our 3rdflag in the metadata of the file stating in the parameter of owner name.
[TASK 4] Mon, are we going to be okay?
This task was based on steganography because in the task description they are indicating that “something is hiding” where it’s gone fishy, moreover there is one file to download.
So, here we thought they are talking about steganography and decided to use steghide.
steghide extract –sf /root/Downloads/Extinction.jpg
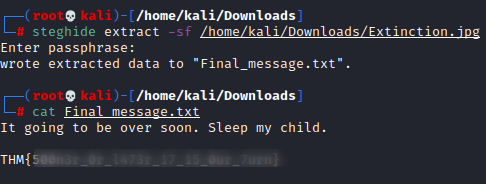
But Interestingly we got another file bind within it when we used to extract the data from the image. And here our arrow goes on point!! We got our 4th flag in this text file.
[TASK 5] Erm……Magick

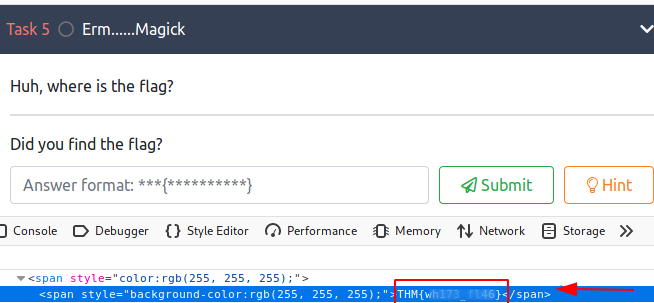
This task was interested and easiest one. Here we got a bit stuck as there was no file or not no clue from there. So, then we decided to see hints and thus it drops

So, the thing that comes to mind is that check the code and when we inspected the element, we got the flag directly over there, or alternately we can also get the flag by highlighting the phrase.
[TASK 6] QRrrrr
This was the simplest one since the title indicates QR” and it was a QR picture when we downloaded the file. So, we already know that the next move is to scan the code.
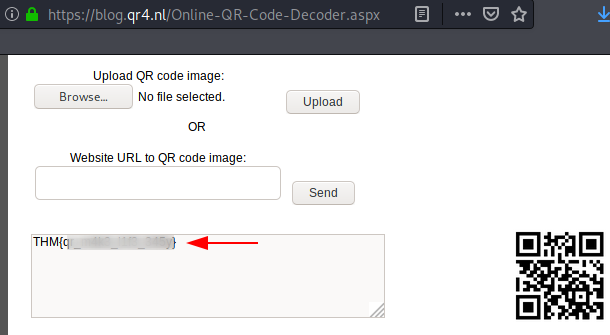
AND BOOM!! We got our flag only after scanning it.
[TASK 7] Reverse it or read it?
In this task, we should only know about the command to open the elf file (a type of .exe). As soon as we open the file with the following command, we got the flag listed
strings hello.hello

[ Task 8 ] Another decoding stuff

Here, as it says, it is a decoding task which is like most of the cryptography challenges. And we were also led to the base58 algorithm as clues, so we use the online base58 decoder directly.

And within a second We got our 8th flag by just decoding it.
[Task 9 ] Left or right

We all need a basic presence of mind in this task as it explains that it is a rot 13 algorithm that is a special case of Ceaser cipher encryption technique in which we replace the plain character with the next 13th letter.

So, here we tried rot13 decoder but it didn’t work, so here our next step was to brute force on shift that is 14,15,16 and so on, as this is all about Ceaser cipher substitute

And we got our flag on the 7th shift
[Task 10] Make a comment

This assignment was the same as Task 5. There was no encoding and no files. So here we thought performing the same steps of task 5 because this task was looking alike as task 5 – No file, No clue in the title. So, here we had to do the inspection again and look for our flag.
And luckily, we received our 10th flag after looking for a while.
[TASK 11] Can you fix it??

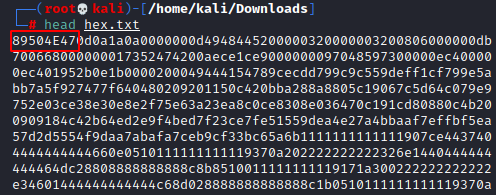
This was the most interesting task of the entire lab. As there was a corrupted png but so here we tried to extract the hexadecimal code of that image but after studying a while, we found that its magic numbers vary from the regular magic number.
Magic numbers are initial 8 characters or numbers in hexadecimal code of any file.
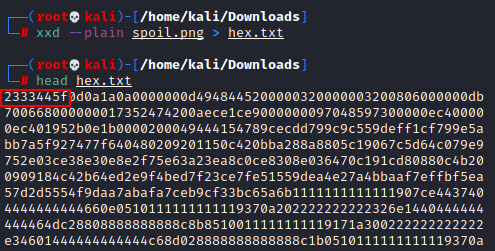
So as we searched on google and we found that the standard magic numbers of the png image are 89 50 4E 47
We have to just replace it.
Now our last step is to render the image from updated hexadecimal code which we did use cyber chef where we have to render the image from updated code
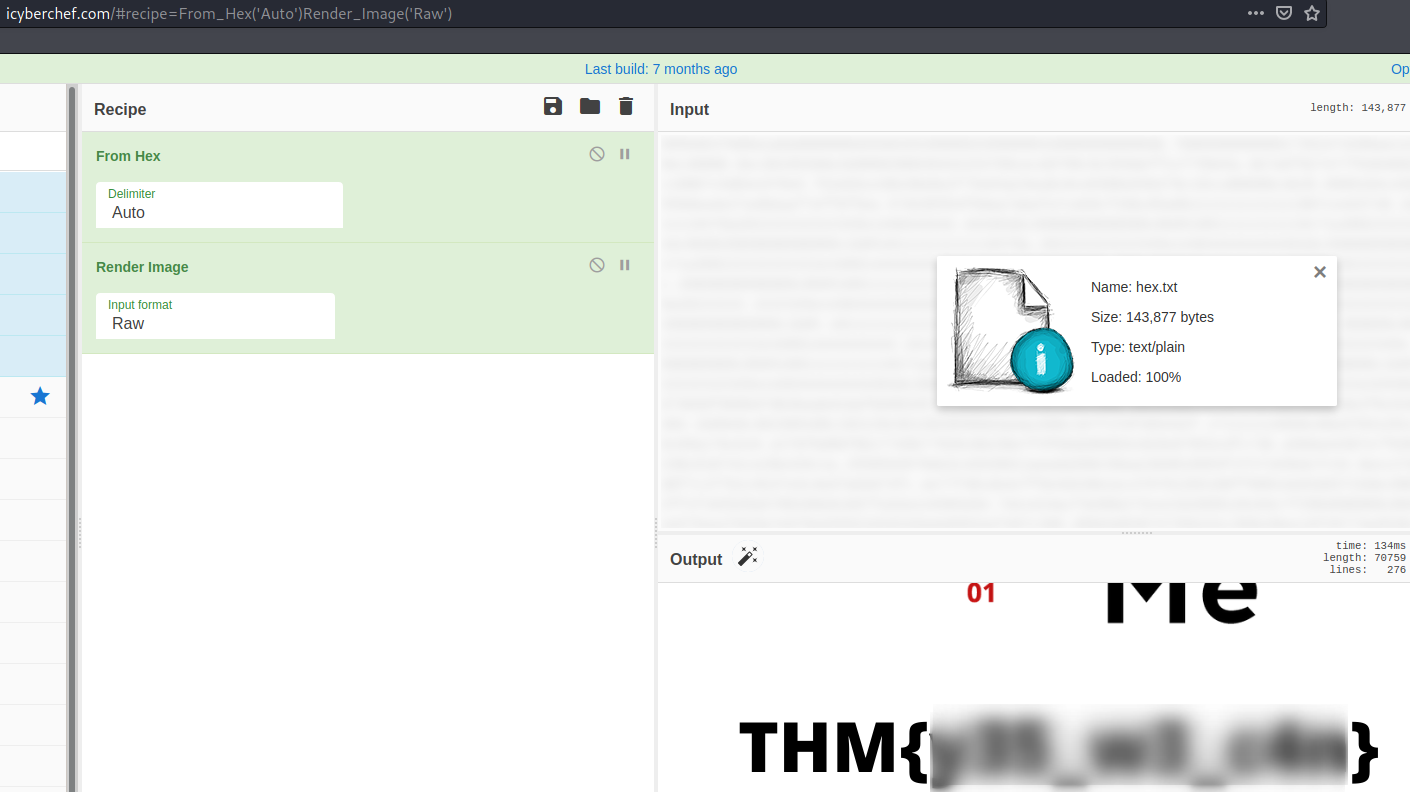
And hence we got our 11th flag in the image
[TASK 12] Read it
In this task, our flag is present on the social media account of tryhackme. But our confusion was to explore on which platform either Twitter or something else.

But provided hint cleared it for us. So here we got a chance to explore our google dork technique. And the perfect dork came to be
inurl:"reddit.com" &intext:"THM" & intitle:"tryhackme"

After going through it we can easily spot our flag where the flag was hidden in the image

[TASK 13] Spin my head

This task was spinning my mind as it told me to decode it but we were clueless about it that’s why we had to go for a hint, and they indicated to its “BINARYFUCK”

So, we directly go to binaryfuck decoder and hence we got our 13th flag just by decoding it.
[TASK 14] An exclusive!

In this task, we got 2 strings but we didn’t know what to do with these strings but our saviour hint shows to XOR these strings.

Now we can relate exclusive and XOR.

So, we can do it easily, as many tools are available online. And we got our 14th flag without effort.
[TASK 15]Binary walk

As this task name suggests a binary walk and clue also directed us to binwalk, it is a tool binwalk that is helpful in steganography. But it is only used to extract the hidden file from the images.
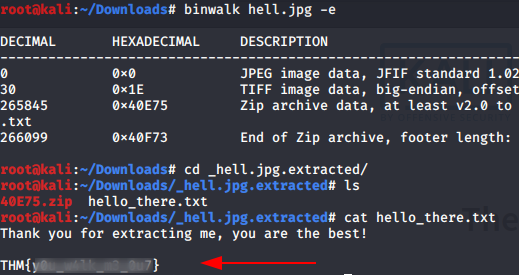
So, we extracted files from jpg and found one txt file. And thus, we got our 15th flag in this file.
[TASK 16]Darkness

In this task our hint is stegsolve. Stegsolve is a steganographic image analyzer, solver, and data extractor.

We have to evaluate our image by filtering various colours in an image using stegsolve. We can download stegsolve with these terminal commands
wget http://www.caesum.com/handbook/Stegsolve.jar -O stegsolve.jar chmod +x stegsolve.jar
Now just we have to open the image with the stegsolve

In the first go, it is just the black image but we have to constantly analyze the image under different colours so the odd one can shine out like this.
And hence we got our 16th flag
[TASK 17] A sounding QR
This task is quite similar to task 6. In this task, we got a QR image and we will scan it and fetch information from there.
But interestingly we got a link over there which redirects to an audio link

But after listening to it carefully in slow motion we got our 17th flag.
[TASK 18] Dig up the past
In this task as a title relates to the past the only thing that pops up in our mind is the Wayback machine and the time and date in the description make our doubt clear.
So, for checking past captures or archives of any site we can use the Wayback Machine. After analyzing the output, we can see there is a capture of the website on 2nd Jan 2020

But when we visited that website, we got our 18th flag.
[TASK 19] Uncrackable!

We have an embedded text in this role so that we can attempt to decipher it. So, we tried it with Ceaser cipher and several other methods, but we get to know this from clues that this is vigenere cipher.
But now the problem begins because while decoding it we require a key.
So there is a strange thing that we can notice is all flags are in the format of THM{………} but in this task flag format is TRYHACKME{………} that’s why we used it as a key and got another encoded value.
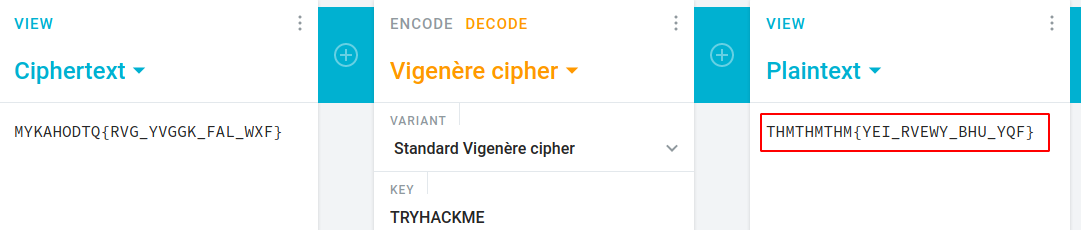
It looks like we found another constant THMTHMTHM. Now we can either attempt to decrypt consecutively using the same key that is TRYHACKME or we can also use THMTHMTHM as a key to decode MYKAHODTQ{RVG YVGGK FAL WXF}

But we got our 19th flag by using THMTHMTHM as a key
[TASK 20] Small bases
This task was also of cryptography. In this task, the hints say (dec-> hex -> ASCII) we have to simply follow these tips that are converting decimal to hex first
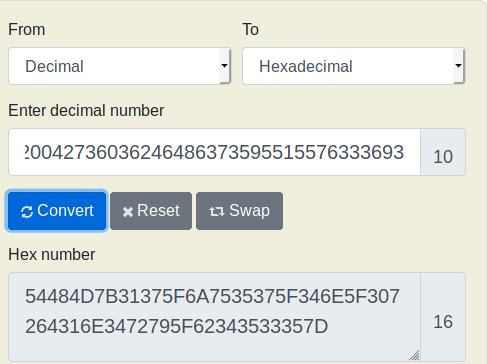
Then Hex to ASCII

And hence we got our 20th flag
[TASK 21] Read the packet

In this task when we download the file it’s a pcapfile. So, it cleared that it’s a Wireshark file
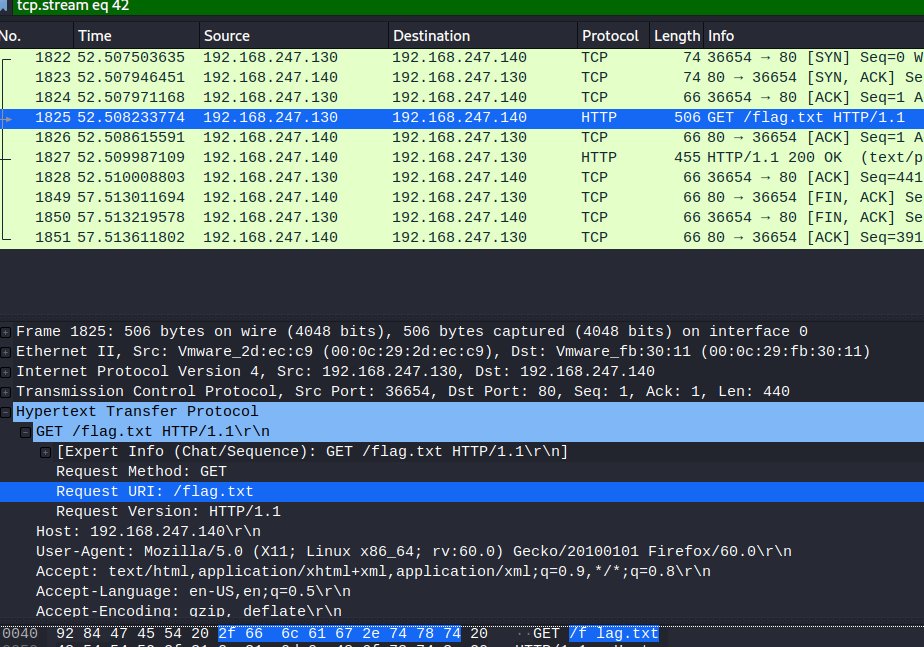
And as the task name suggests we have to read any packet which is in any packet so after applying many filters and searching we get to the request over which flag.txt has been sent so we have to just open up that file with the help of stream.

And here we go we secured our last flag.
MISSION ACCOMPLISHED!!
Author: Dheeraj Gupta is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast in the field of Network & Cyber Security. Contact Here