Comprehensive Guide on Honeypots
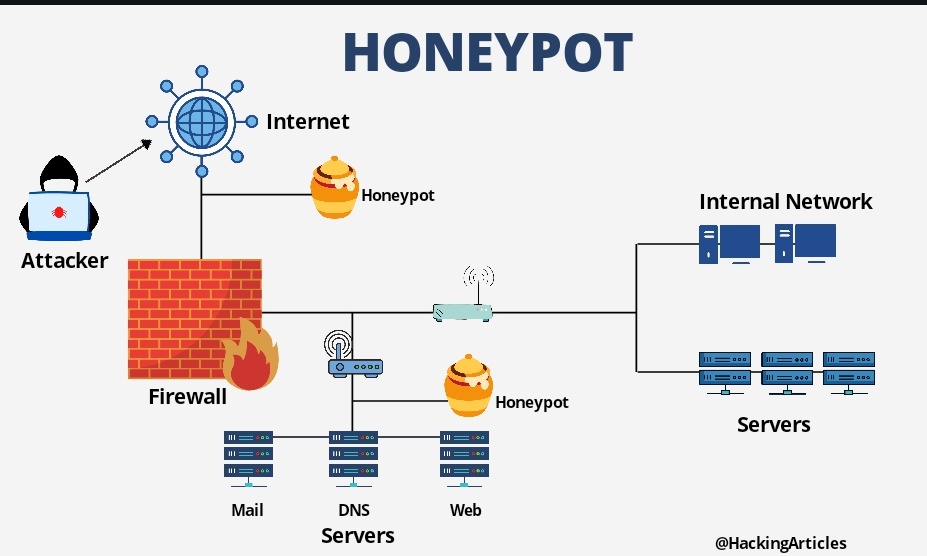
Honeypots are generally hardware or software that are deployed by the security departments of any organization to examine the threats that are possessed by the attackers. Honeypots usually act as baits for an organization to gather information on the attacker and alongside protect the real target system.
Table of Contents
- What are Honeypots
- Working of Honeypots
- Types of Honeypots
- Based on the design
- Based on the deployment
- Based on their deception technology
- Installation and working of Honeypots
- In Windows system
- In Android smartphone
- In Linux system
What are honeypots?
Honeypots are a type of Internet security resource which is used to entice cybercriminals to deceive them when they try to intrude inside the network for any illegal use. These honeypots are generally set up to understand the activity of the attacker in the network so that the organization can come up with stronger prevention methods against these intrusions. The honeypots do not carry any valuable data as it a fake proxy that helps in logging the network traffic.
Working of honeypots
In an organization as an IT administrator, you would want to set up a honeypot system that might look like a genuine system to the outside world. The kind of data that honeypots generally capture:
- Keystrokes entered and typed by the attacker.
- The IP address of the attacker
- The usernames and different privileges used by the attackers
- The type of data that the attacker had accessed, deleted or that was altered.
Types of Honeypots
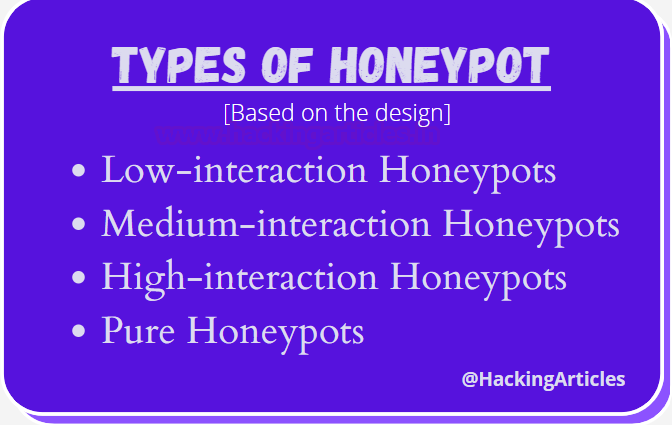
Low-Interaction Honeypots: They match a very limited number of services and applications that are present in the network or on the system. This type of honeypot can be used to keep track o UDP, TCP, and ICMP ports and services. Here we make use of fake databases, data, files, etc as bait to trap attackers to understand the attacks that would happen in real-time. Examples of a few Low-Interaction tools are Honeytrap, Specter, KFsensor, etc.
Medium-Interaction Honeypots: They are based on imitating real-time operating systems, and has all its applications and its services as that of a target network. They tend to capture more information as their purpose is to stall the attacker so that the organization gets more time to respond to the threat appropriately. Examples of a few medium-interaction tools are Cowrie, HoneyPy, etc.
High-Interaction Honeypots: They are genuine vulnerable software that is run on a real operating system with various applications that a production system would generally have. The information gathered using these honeypots is more resourceful but they are difficult to maintain. An example of a High-interaction tool is honeynet.
Pure Honeypots: These honeypots usually imitate the actual production environment of an organization which makes an attacker assume it to be a genuine one and invest more time exploiting it. Once the attacker tries to find the vulnerabilities, the organization will be alerted and hence any kind of attack can be prevented earlier.

Production Honeypots: These honeypots are usually installed in the organization’s actual production network. They also help in finding any internal vulnerability or attack as they are present in the network internally.
Research Honeypots: They are high-interaction honeypots but they are set with a focus of research in the areas of various governmental or military organizations to gain more knowledge on the behaviour of the attackers.

Malware Honeypots: They are the kind of honeypots that are used to trap malware in a network. Their purpose is to attract the attacker or any malicious software and allow them to perform certain attacks where can be used to understand the pattern of the attack.
Email Honeypots: These honeypots are hoax email address which is used to attract the attackers across the internet. The emails that are received by any malicious actor can be monitored and examined and can be used to help the fall for phishing email scams.
Database Honeypots: These honeypots pose as actual databases that are vulnerable in name and usually attract attacks like SQL injections. They are meant to lure the attackers into thinking that they might contain sensitive information like credit card details which will let the organization understand the pattern of the attacks performed.
Spider Honeypots: These honeypots are installed with the purpose to trap the various web crawlers and spiders which tend to steal important information from the web applications.
Spam Honeypots: These honeypots consist of hoax email servers to attract the spammers to exploit vulnerable email elements and give details about the activities performed by them.
Honeynets: these are nothing but a network of honeypots which are installed in the virtual and isolated environment along with various servers to record the activities of the attackers and understand the potential threats.
Honeypots can be deployed in various environments. Today we will see the installation and working of honeypots in windows, Android and Linux environment.
Windows System
Today we will be looking at the famous honeypot software called HoneyBOT. which can be downloaded from here. Switch on your kali Linux as the attacker machine and the windows system as your host machine.
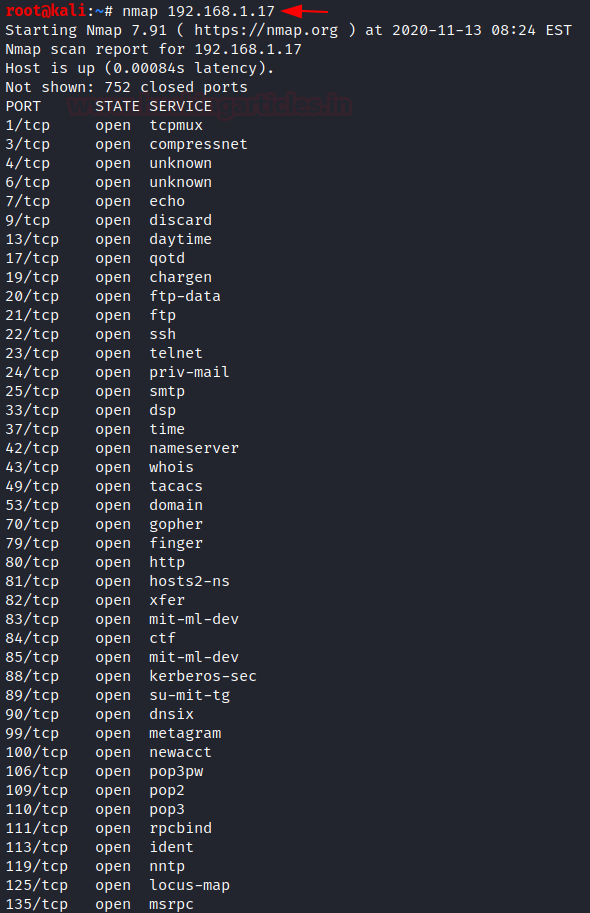
Let us first do a nmap scan on the host machine when the honeypot is not installed.
nmap -sV 192.168.1.17

Now in your Windows system install the HoneyBOT software and configure it, click on yes to proceed.

Check all the parameters that you want in your honeypot and click on Apply to proceed.

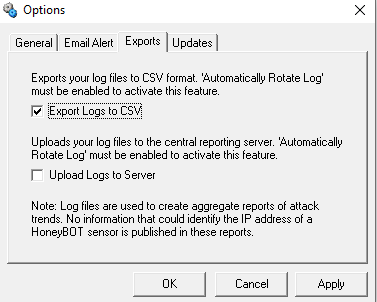
To get email reports on your honeypot, add the recipient email address and click on apply.

If you want to save the honeypot logs into CSV format, you can apply this setting.
On the attacker, machine performs a nmap scan and there you will see so many fake services that are open due to the presence of honeypot in the system.
Let us try connecting to FTP from the attacker machine to the host machine.

Where you see the log has been generated of the attacker’s IP and the port that he was connected on.
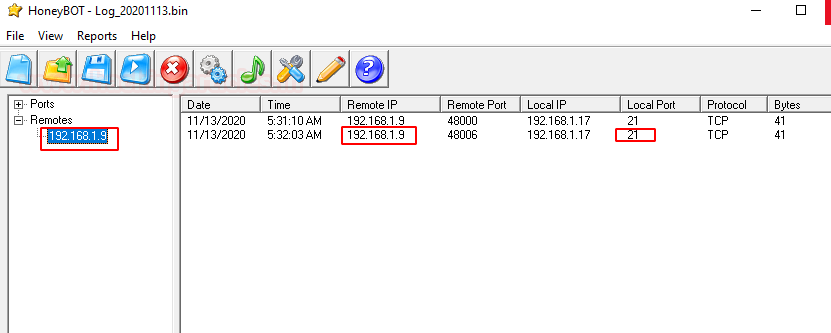
Here you can see a detailed report on the connection that is created by the attacker.
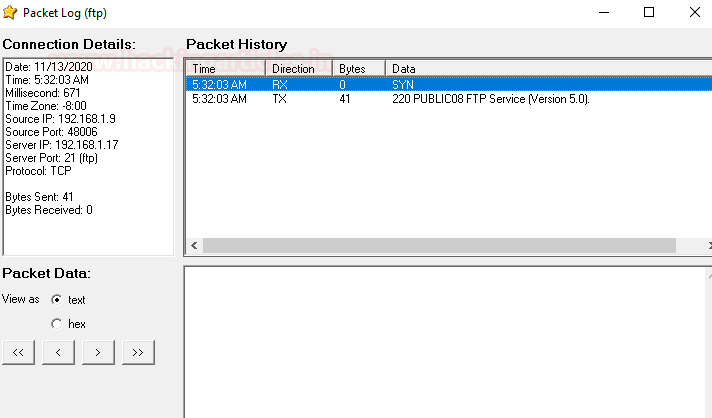
Similarly, an SSH connection was initiated on port 22 from another operating system.

Now you can see that log for the same has been generated for the connection created on port 22.

Android Honeypot
The honeypots can also be installed in android phones using the google play store. Here we have downloaded Hostage honeypot.

On switching on the application, it looks safe.

Now let us check the IP address of your android device and let’s proceed.

Let’s turn on the attacker system and let’s conduct a nmap scan on the IP address of the android device.

An alert will be generated on the android device when the nmap scan was connected.

A log will be created and we can see the IP of the attacker system and te ports that were attacked.
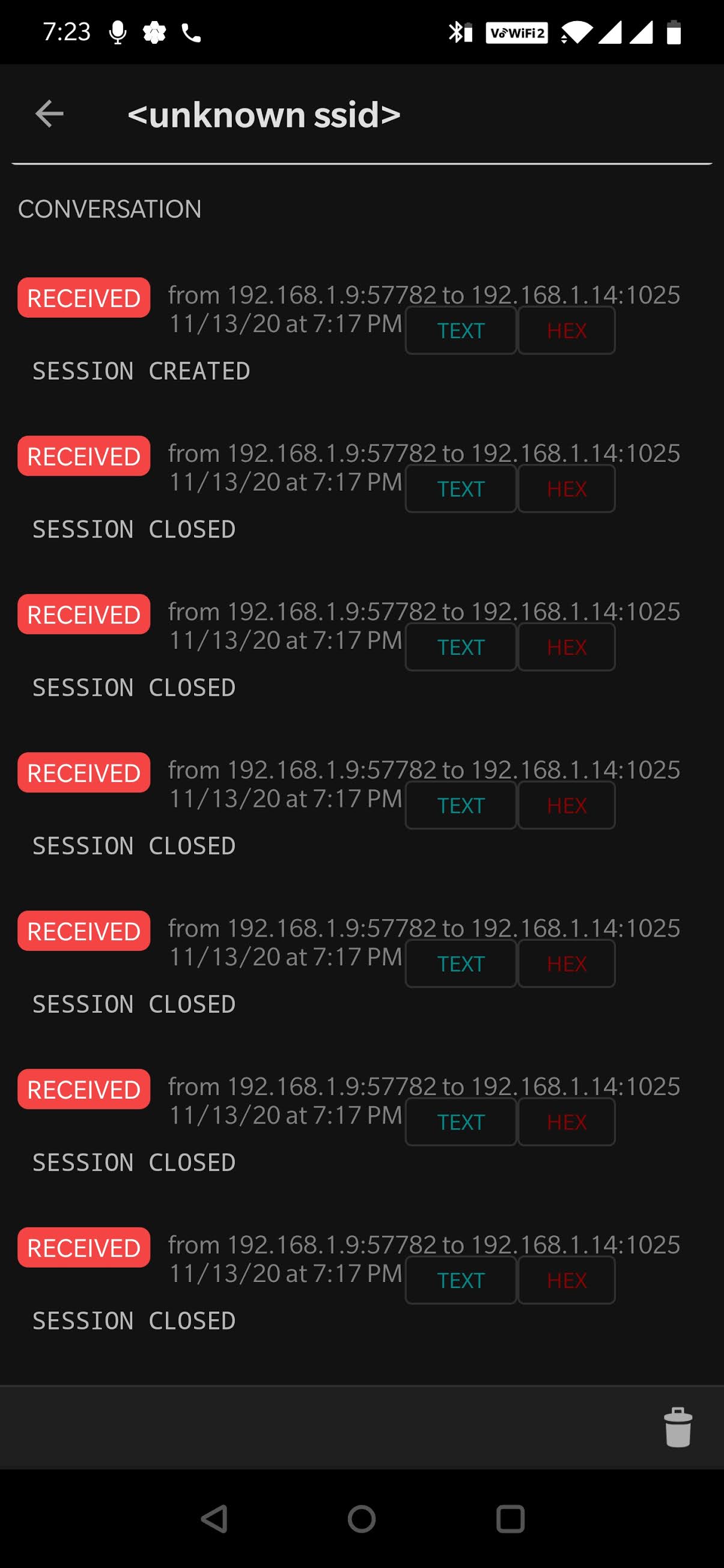
Linux Honeypot
We can install a honeypot in a Linux machine as well. Here we have demonstrated using Pentox which can be easily installed in Ubuntu.
wget http://downloads.sourceforge.net/project/pentbox18realised/pentbox-1.8.tar.gz tar -zxvf pentbox-1.8.tar.gz

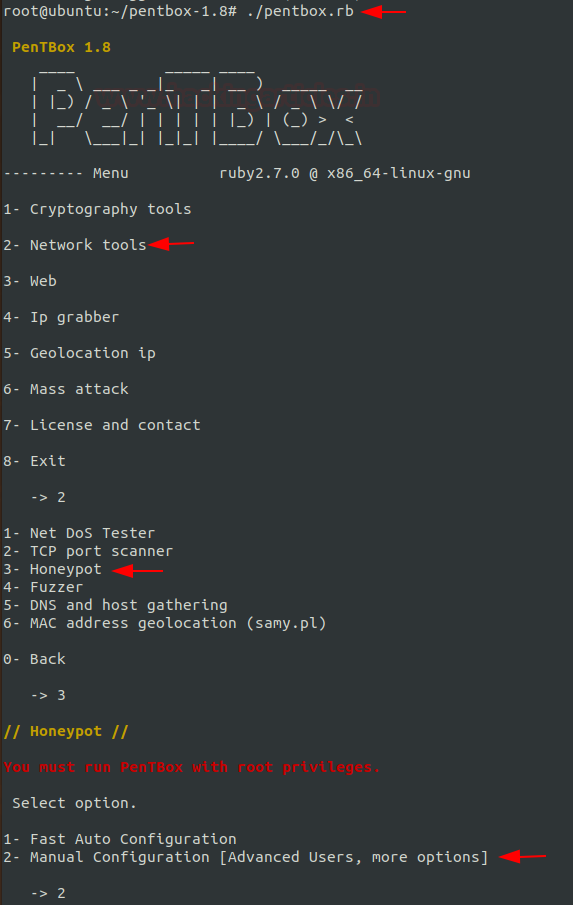
Once, it is installed, let us start using pentbox. Select the network tools and honeypot from the menu to install the honeypot. Go along with manual configuration to install according to your preferences for a honeypot.
./pentbox.rb
Now you can open the fake port according to your preference and insert a fake message. You can also provide the option to save the log and save the name of the log. You can see that the honeypot is activated on the required port and similarly you can manually activate honeypots for other ports.

Turn on the attacker machine, and scan the host machine using nmap. The results of the open ports and services are displayed below.

Here the attacker machine is trying to connect with the host machine using telnet.

For every attempt of intrusion that was made, it gets alerted and a log is created where the attacker IP and port is recorded.

Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
provided link is not working to download honeybot