Comprehensive Guide on Dirsearch
In this article, we will learn how we can use Dirsearch. It is a simple command-line tool designed to brute force directories and files in websites. Which is a Python-based command-line website directory scanner designed to brute force site structure including directories and files.
Table of Content
- Introduction to Dirsearch
- Setup
- Target URL
- Save Output in Different Formats
- No Colour
- Quite mode
- Normal scan vs Recursive scan
- Post method
- Delay request
- Version scan
Introduction to Dirsearch
Dirsearch is a professional command-line method for the brute force of web server folders and files. It has now become the top Web content scanner with 6 years of success.
It provides users with the ability to explore complex web content as a feature-rich tool, with many wordlist vectors, high accuracy, impressive performance, advanced connection/request settings, modern brute-force techniques and nice results.
It is a strong competitor in the directory scanner arena, with features such as multi-threading, proxy support, request latency, user agent randomization, and support for multiple extensions.
It is being actively developed by @maurosoria and @shelld3v.
Setup
It is a Python-written method used to brute-force web directories and files that are secret. It can run on Windows, Linux, and macOS, and provides a simple but powerful interface for the command line.
We are installing this tool in our kali, using the git-clone command to install Dirsearch web content scanner tool.
git clone https://github.com/maurosoria/dirsearch.git
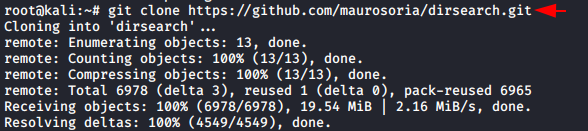
After installing this tool, we need to navigate through its directories and search for dirsearch.py. Now, all we need just run this python written tool with [-h] parameter through this we can see all its parameter with their functions.
./dirsearch.py -h
Let’s get started
Target URL
We can use our web content scanner on a specific targeted URL with the help of [-u] parameter. To get appropriate results we need to make sure that it is an authenticated URL follow this command to get the desired results.
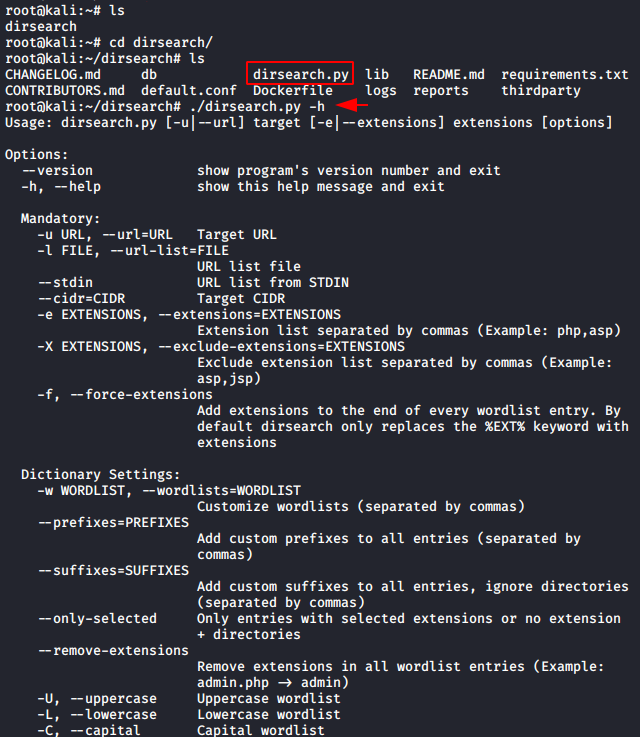
./dirsearch.py -u http://testphp.vulnweb.com/
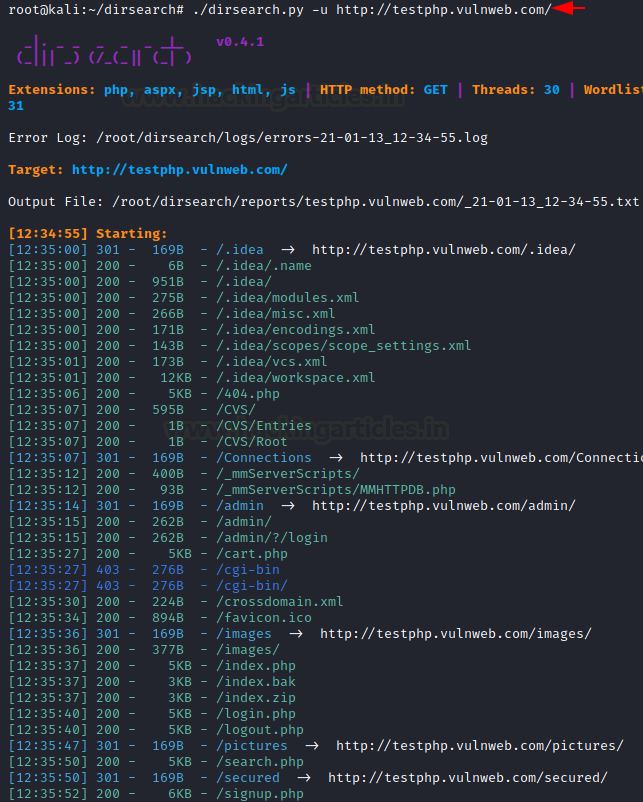
As we can see we got some web directories and web pages.
Save Output in Different Formats
We can save our output which we get from the attack in different-different formats to learn further from them. This parameter helps us to get through those details of these formats. Let’s explore them one by one.
Save output in Simple format
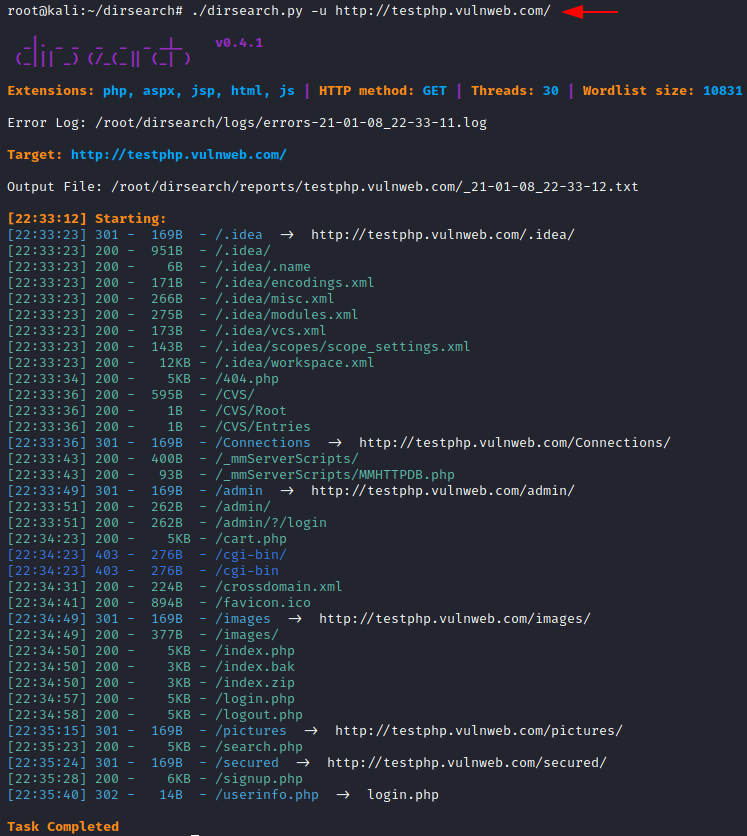
We can save our result in the simple format with the help of [–simple-report] parameter. Through this feature, we can better analyse the results which we got from this attack. Follow this command to proceed further.
./dirsearch.py -u http://testphp.vulnweb.com/ --simple-report=report
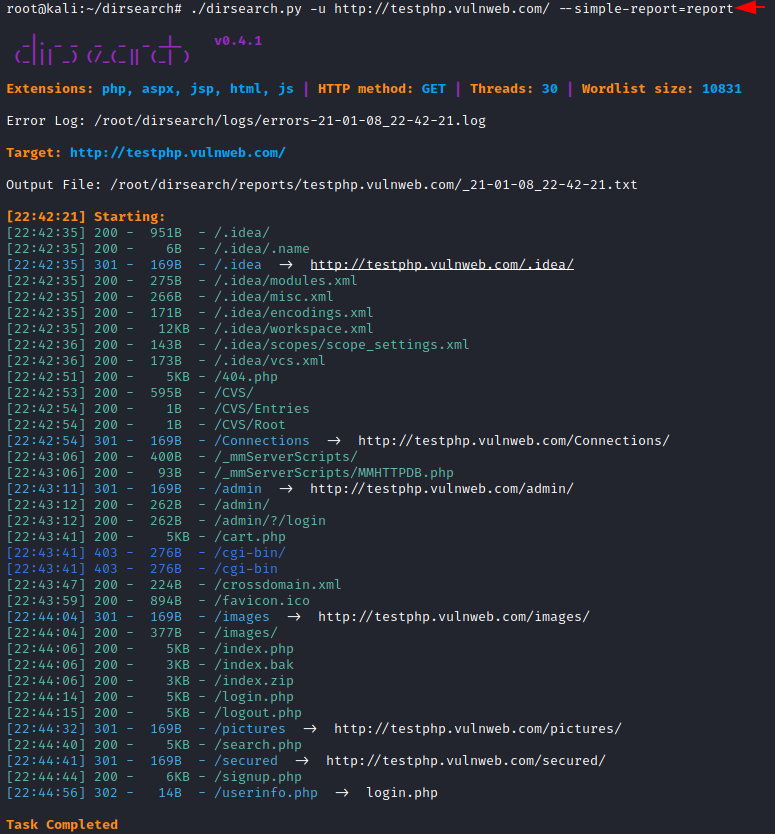
After creating this report, we can cross verify its location in the system. Now use nano command to see this report.

As we can clearly see that our simple format result is successfully created. Now, we can analyse our results easily.

Save output in JSON format
JSON is an open standard file format and data exchange format that stores and transmits data objects consisting of attribute-value pairs and array data types using human-readable text. It is a very common data format with a wide variety of uses, such as being used in AJAX systems as a substitute for XML. With this method, we can build this kind of output result format by just following these commands.
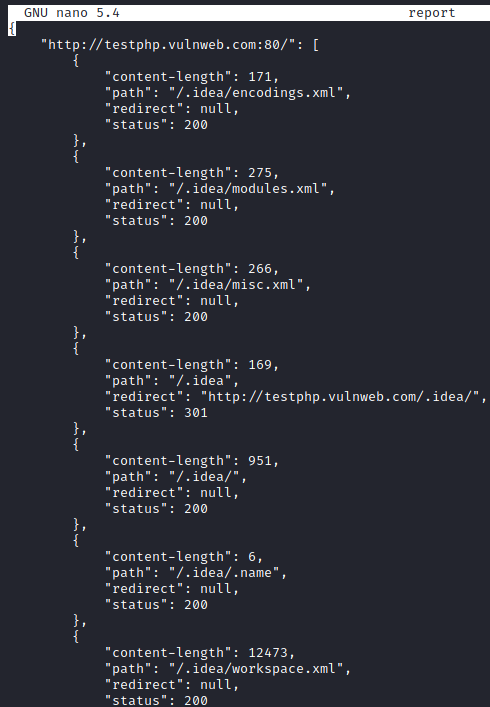
./dirsearch.py -u http://testphp.vulnweb.com/ --json-report=report
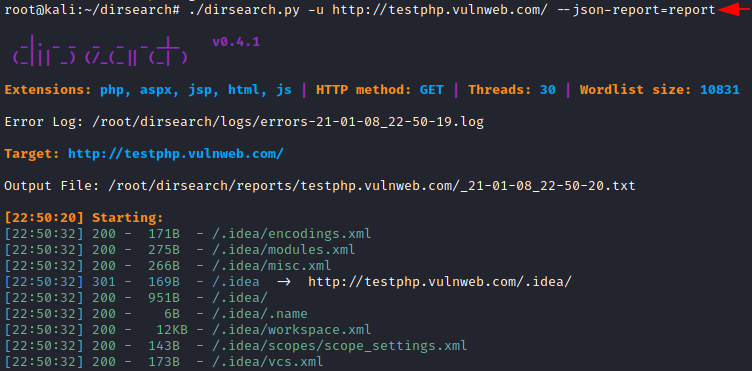
Similarly, as above we are using nano command to start analysing our result.
Save output in XML format
Extensible Mark-up Language (XML) is a mark-up language that specifies a collection of rules that are both human-readable and machine-readable to encode documents in a format. By using some commands, we can build our XML format result copy with this tool.
./dirsearch.py -u http://testphp.vulnweb.com/ --xml-report=report
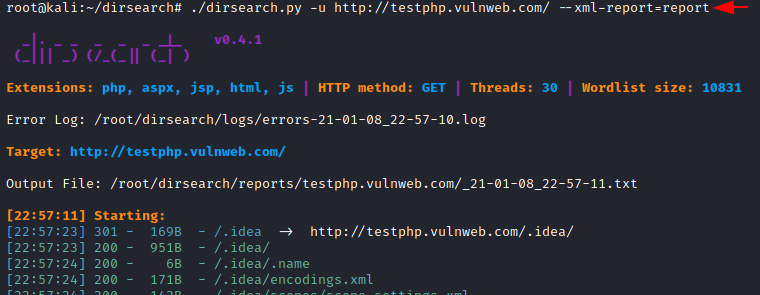
Similarly, as above we are using nano command to start analysing our result.

Save output in Markdown format
For creating formatted text using a plain-text editor, Markdown is a lightweight mark-up language. In 2004, John Gruber and Aaron Swartz created Markdown as a mark-up language that, in its source code form, appeals to human readers. We can build our markdown format result copy by using this command with this tool.
./dirsearch.py -u http://testphp.vulnweb.com/ --markdown-report=report
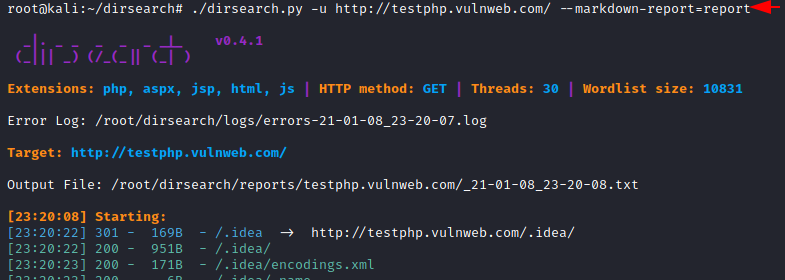
Similarly, as above we are using nano command to start analysing our result.
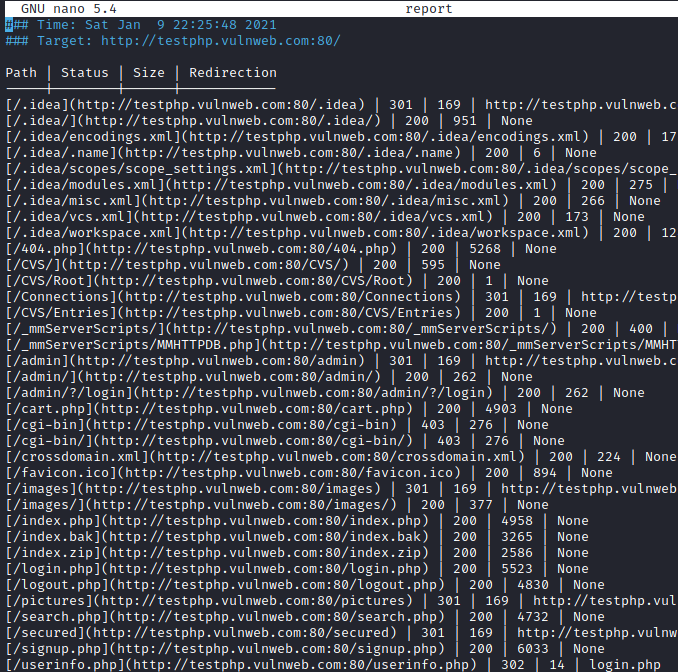
Save Output in CSV format
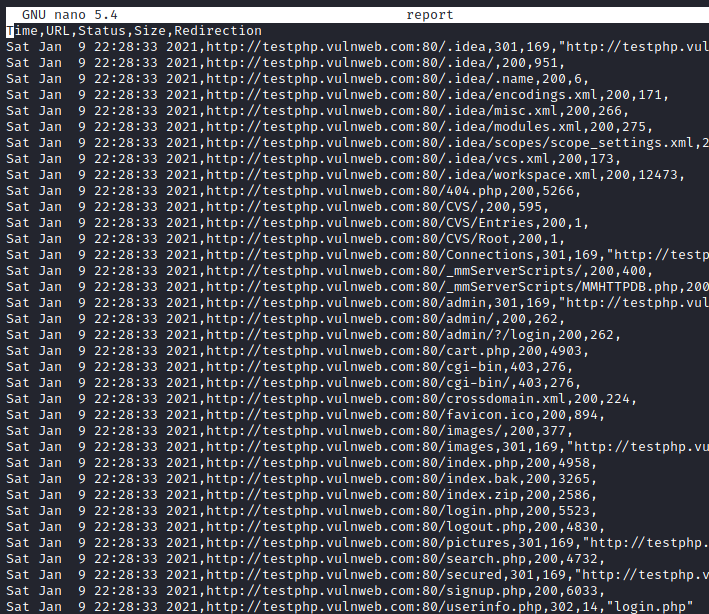
A comma-separated value file is a delimited text file that separates values using a comma. A data record is any line of the file. Each record, separated by commas, consists of one or more fields. By using some commands, we can build our CSV result copy with this method.
./dirsearch.py -u http://testphp.vulnweb.com/ --csv-report=report
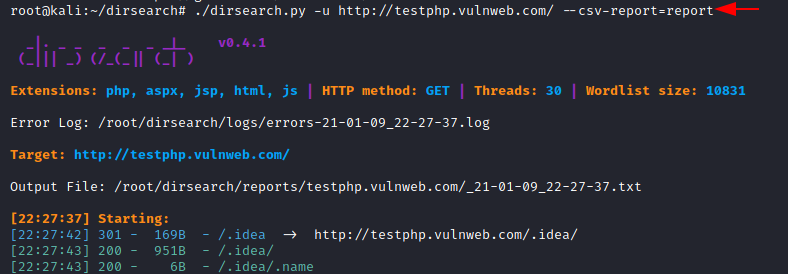
Similarly, as above we are using nano command to start analysing our result.
Save output in Plain format
Simple text is a loose term for knowledge in computing that only represents characters of readable content, but not its graphical representation or other artefacts. It may also include a limited number of whitespace characters, such as spaces, line breaks, or tab characters, that affect the simple arrangement of text. By using some commands, we can create a plain text results copy with this method.
./dirsearch.py -u http://testphp.vulnweb.com/ --plain-text-report=report

Similarly, as above we are using nano command to start analysing our result.
No Colour
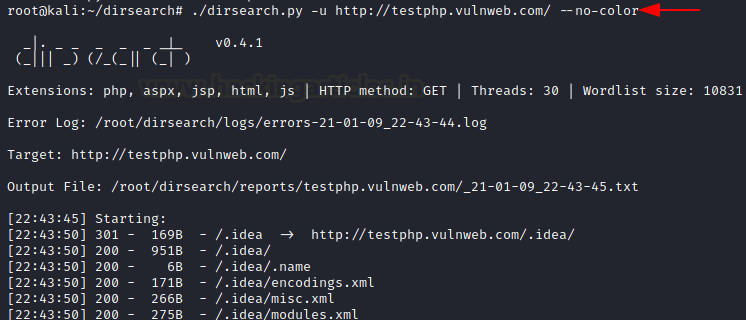
If colours are bothering us from concentrating on our analysis or results. We can remove all the colours occurs in our results from the attack, by using [–no-colour] parameter we can achieve this function. Follow this command to get these results.
./dirsearch.py -u http://testphp.vulnweb.com/ --no-color
Quite Mode
Quite mode is used in a more hush-hush manner to run dirsearch. If you’re the type of person who doesn’t want a huge banner telling everybody what you’re doing on your system, you’ll like this choice. Basically, this allows for a cleaner screen as it executes the commands you send it, without the funny cow showing up on top.
Just use this [-q] parameter with this command to see the results
./dirsearch.py -u http://testphp.vulnweb.com/ -q

Normal scan vs Recursive scan
The method of scanning everything in a folder, including subfolders, is known to all of us. We compare a normal scan against a recursive scan in this section.
Firstly, we only use the [-u] parameter in the normal scan to get through victim URLs. In order to begin this scan, follow this instruction.
./dirsearch.py -u http://testphp.vulnweb.com/
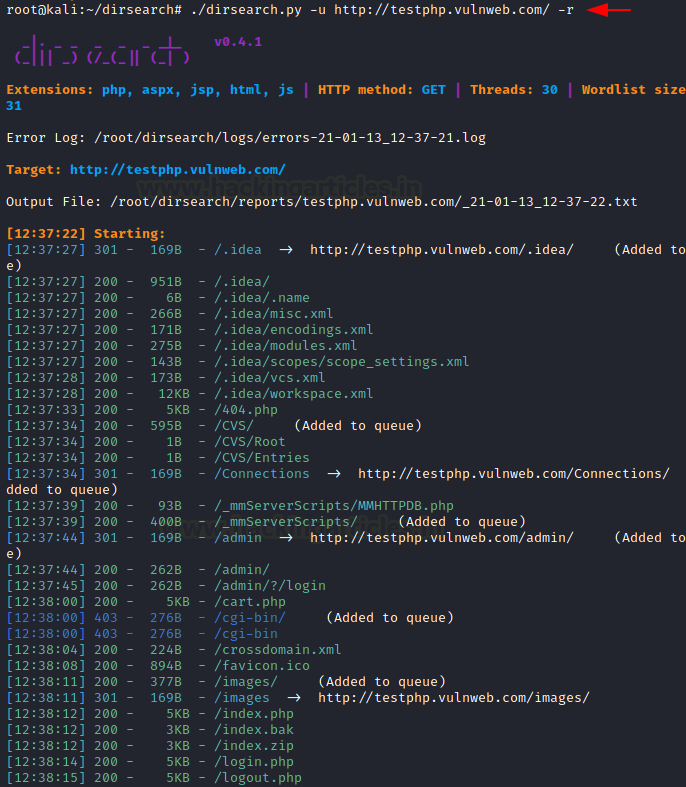
Now, secondly, in the same command, when we use the parameter [-r] along with it. By just initiating this attack on the victim, it will help us go through each folder and its sub folders.
./dirsearch.py -u http://testphp.vulnweb.com/ -r
As we can see these results, with specific wording, it attaches some more results, such as added to the queue in the ongoing attack.
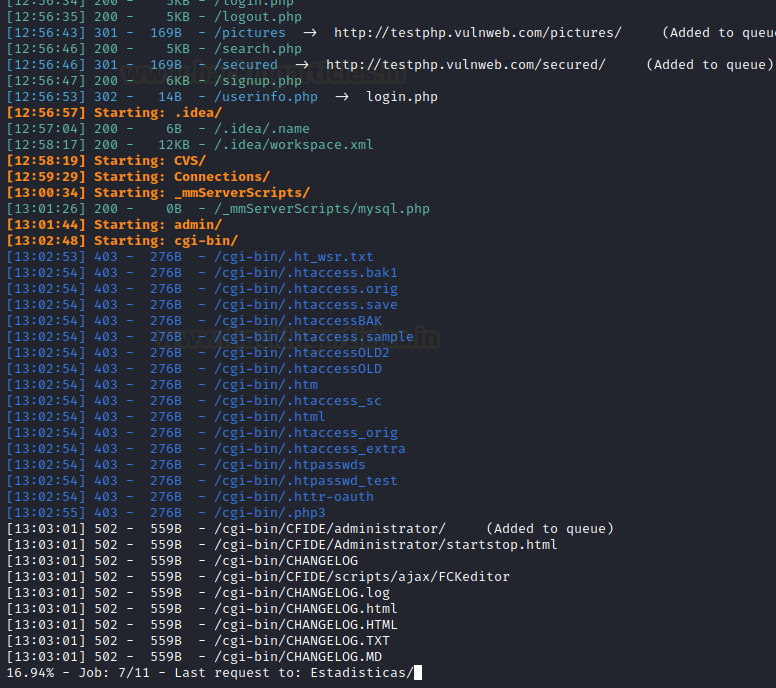
Now, after completing the usual scan for some time, it will go through each and every sub-folder for the recursive scan. As we can see clearly in this screenshot, it goes for the victim’s subfolders and tells us about our attack’s incomplete work.
Post method
We know that, for a given resource, HTTP defines a set of request methods to indicate the required action to be performed.
But in the post method, POST is an HTTP supported request method used by the World Wide Web. The POST request method, by design, requires a web server to accept the data enclosed in the request message body, most likely to store it. It normally works with the GET HTTP method, which is used in the name or value pair to append the form data to the URL. If you use GET, the URL length will remain restricted. This enables users to submit the result of the bookmark.
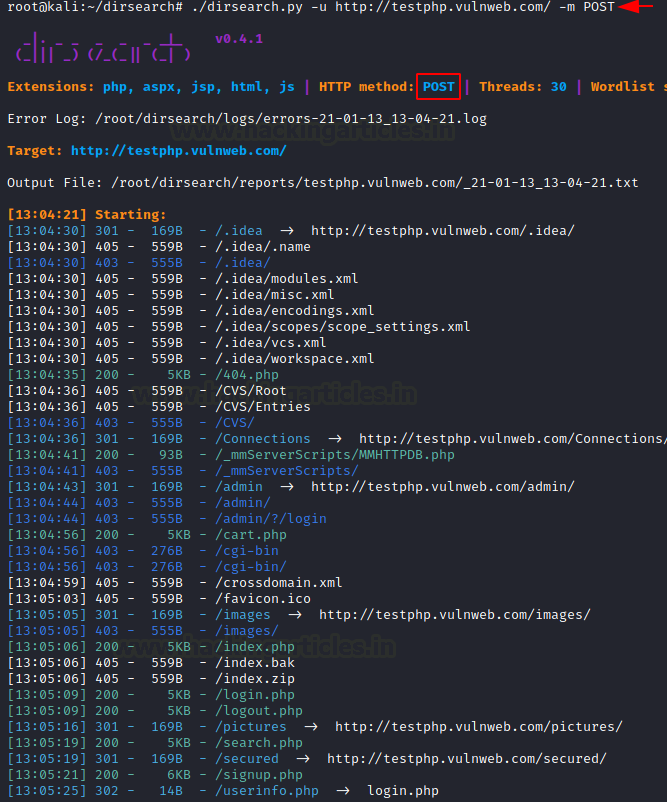
Now, we are exploring this other side with the help of [-m] parameter with this command.
As we can these results are different and unique in comparison to the GET request method which we performed earlier. It shows some different web pages and web directories.
./dirsearch.py -u http://testphp.vulnweb.com/ -m POST
Delay request
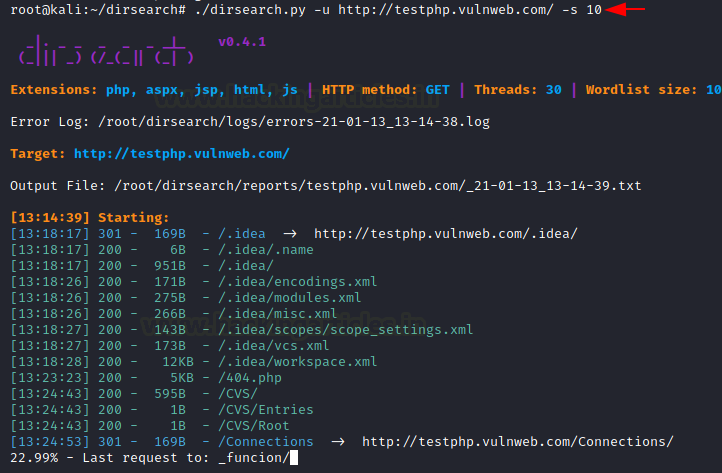
It just another normal scan with some specific delay between each and every request in our attack. These sort of things provide proper exposure of a particular request. We can achieve this feature with the help of [-s] parameter with specified time in seconds.
./dirsearch.py -u http://testphp.vulnweb.com/ -s 10
Version scan
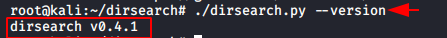
As we all know that our dirsearch web content scanner is constantly being updating with the time. Some feature will add in the with the demand of time. We can use [–version] parameter to see that, if our tool is up to date or not.
./dirsearch.py --version
This is our first instalment in the series of Dirsearch’s Beginners Guide. Cantered on some of Dirsearch’s core functions. In this incredible method, stay tuned for more advance option.
Author: Shubham Sharma is a passionate Cybersecurity Researcher, contact LinkedIn and Twitter.
As modern websites block the directory fuzzing, you should also include guide to use proxies in dirsearch. Amazing artical BTW.