Docker for Pentester: Image Vulnerability Assessment
We are moving from virtualization to containerization and we are all familiar with the container services such as docking or quay.io. You can pick a dock image for a particular application by selecting several choices. As you know, when a developer works with a container, it not only packs the program but is part of the OS, and we do not know whether the connect libraries have been patched or vulnerable.
So, we will show “how to perform a container audit and vulnerability assessment” in any infrastructure in this role.
Table of Contents
Prerequisites
Clair
- Installation
- Docker Image Vulnerability Scanning
Bench-security
- Installation
- Container Hardening
Prerequisites
At your host machine, Install docker and pull an image, you want to scan.
Clair: Vulnerability
Installation
CoreOS has created an awesome container scan tool called Clair. Clair is an open-source project for the static analysis of vulnerabilities in apps and Docker containers. You can clone the package with the help of git, using the following command
git clone https://github.com/arminc/clair-scanner.git
The scanner is developed in go language, therefore golang on your local machine over which is docker is running.
apt install golang

Build the library to install all dependencies of the Clair.
cd clair-scanner make build

make cross

As you can see, we have the following file in the bucket list.
If in your host machine, you don’t have a docker image, you can pull a new image, as we did here to illustrate vulnerability assessment.
docker pull ubuntu:16.04
Now, run the docker image of the Clair that will listen at local port 5432.
docker run -d -p 5432:5432 --name db arminc/clair-db:latest

Also, run the docker image for postgres to link Clair scan with the help of the following command.
docker run -p 6060:6060 --link db:postgres -d --name clair arminc/clair-local-scan:latest

Now, let’s use the Clair for scanning the vulnerability of a container or docker image, with the help of the following command.
Syntax: ./clair-scanner -ip <docker ip> -r output.jason <docker-image>
./clair-scanner --ip 172.17.0.1 -r report.json ubuntu:16.04
Booom!!!! And we got the scanning output which is showing 50 unapproved vulnerabilities.

Bench-Security: Container Hardening
The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production. The tests are all automated and are inspired by the CIS Docker Benchmark v1.2.0.
So, as you can see, we have a few docker images on our host.

Let’s start docker audit for container hardening by executing a set of command as shown here.
docker run -it --net host --pid host --userns host --cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /etc:/etc:ro \
-v /usr/bin/containerd:/usr/bin/containerd:ro \
-v /usr/bin/runc:/usr/bin/runc:ro \
-v /usr/lib/systemd:/usr/lib/systemd:ro \
-v /var/lib:/var/lib:ro \
-v /var/run/docker.sock:/var/run/docker.sock:ro \
--label docker_bench_security \
docker/docker-bench-security

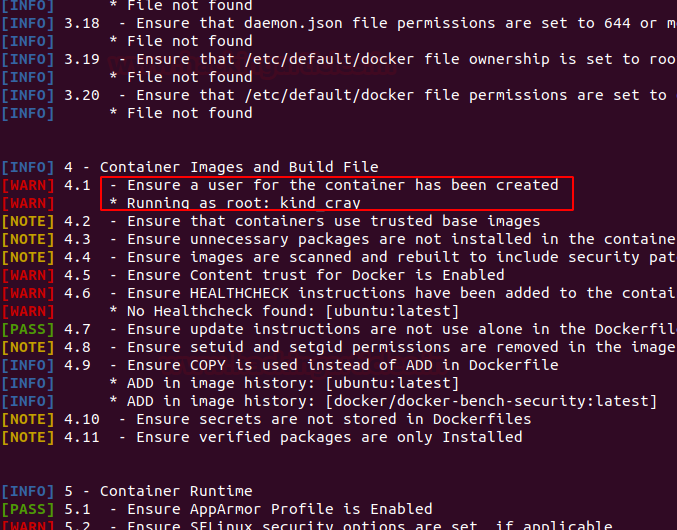
The output results as Info, Warning, Pass and Notes for each of the configuration recommendations as mention below:
- Host Configuration
- Docker Daemon Configuration
- Docker Daemon Configuration Files
- Container Images and Build Files
- Container Runtime
- Docker Security Operations
Let me explain this in a better way: You can observe in the highlighted session that it has created alert against root privilege for running the docker image.
To fix such type of misconfiguration, stop the running process for docker and then again, run the docker image with low privilege user access as shown below.
docker stop $(docker ps -aq) docker rm $(docker ps -aq) docker run -itd --user 1001:1001 ubuntu docker exec -it <container-id> /bin/bash

If the loophole is closed, use the bench again for cross-validation and this time ensure you have passed the warning. As you can see, this time we got the Green sign that shows we got the loopholes patched.
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here
make Build is getting failed with below error :
I’m trying to execute it on Ubuntu18.04 which have docker setup
root@kubeworker2:~/clair-scanner# make build
CGO_ENABLED=0 go build
clair.go:10:2: cannot find package “github.com/coreos/clair/api/v1” in any of:
/usr/lib/go-1.10/src/github.com/coreos/clair/api/v1 (from $GOROOT)
/root/go/src/github.com/coreos/clair/api/v1 (from $GOPATH)
docker.go:10:2: cannot find package “github.com/docker/docker/client” in any of:
/usr/lib/go-1.10/src/github.com/docker/docker/client (from $GOROOT)
/root/go/src/github.com/docker/docker/client (from $GOPATH)
main.go:8:2: cannot find package “github.com/jawher/mow.cli” in any of:
/usr/lib/go-1.10/src/github.com/jawher/mow.cli (from $GOROOT)
/root/go/src/github.com/jawher/mow.cli (from $GOPATH)
main.go:9:2: cannot find package “github.com/mbndr/logo” in any of:
/usr/lib/go-1.10/src/github.com/mbndr/logo (from $GOROOT)
/root/go/src/github.com/mbndr/logo (from $GOPATH)
reporter.go:6:2: cannot find package “github.com/olekukonko/tablewriter” in any of:
/usr/lib/go-1.10/src/github.com/olekukonko/tablewriter (from $GOROOT)
/root/go/src/github.com/olekukonko/tablewriter (from $GOPATH)
utils.go:14:2: cannot find package “gopkg.in/yaml.v2” in any of:
/usr/lib/go-1.10/src/gopkg.in/yaml.v2 (from $GOROOT)
/root/go/src/gopkg.in/yaml.v2 (from $GOPATH)
Makefile:8: recipe for target ‘build’ failed
make: *** [build] Error 1