Retro TryHackMe Walkthrough
Today it is time to solve another challenge called “Retro”. It was created by DarkStar7471. It is available at TryHackMe for penetration testing practice. The challenge is of hard difficulty even if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. The breakdown of the Machine with redacted flags is as follow:
Level: Hard
Penetration Testing Methodology
- Network Scanning
- Nmap Scanning
- Enumeration
- Browsing HTTP service
- Directory Bruteforce using dirb
- Enumerating user Wade
- Enumerating password for Wade
- Exploitation
- Connecting RDP service
- Reading User Flag
- Privilege Escalation
- Enumerating Bookmarks in Chrome
- Enumerating Recycle Bin
- Exploiting CVE-2019-1388
- Getting Administrator Access
- Reading Root Flag
Walkthrough
There are two flags in this machine to discover. After Booting up the target machine from the TryHackMe: Retro Page, an IP will be assigned to the machine and will be visible on that page as well.
IP Address: 10.10.167.18
Network Scanning
We will start a Nmap scan with the -sV for performing a Version Scan and -sC for default scripts on the target machine.
nmap -sV -sC 10.10.167.18

We have two services running on the target machine. We have 80 (HTTP) and 3389 (RDP). Since we don’t have the credentials for accessing the RDP service at this moment, we will be enumerating with the HTTP Service.
Enumeration
To enumerate the HTTP service, we open the IP address of the target machine in the Web Browser and found the default page for the IIS Deployment.
http://10.10.167.18/
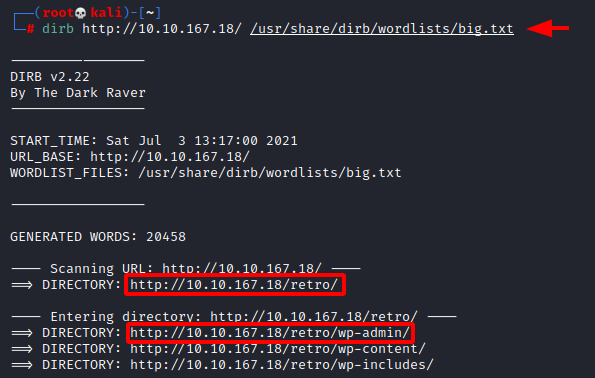
Since we were not able to get any information from the IIS page, we decided to perform a Directory Bruteforce. We tried to use the dirb tool with its default wordlist, but we were not able to extract any information. Hence, we moved onto the big.txt wordlists and after running for a while we were able to get the /retro/ directory. Inside the /retro/ directory we were able to find the /wp-admin/ page. This confirms that the website hosted on the /retro/ is a WordPress Deployment.
dirb http://10.10.167.18/ /usr/share/dirb/wordlists/big.txt
We opened the retro webpage on our web browser. From the presence of the /wp-admin/ it was clear that this is a WordPress Deployment and it seems like a blog for the old arcade-based games. There seems to be a kind of theme that has been added to this website. On the home page, we have a blog post by the title of Tron Arcade Cabinet. We can see that it was written by a user Wade. This user can be helpful down the road.
http://10.10.167.18/retro/

Clicking on the User Wade, we were redirected to the author section that has the collection of blog posts by Wade. We checked them out but there didn’t seem any hints or secrets. This is when our attention was shifted from blogs to comments. We found that Wade has commented on the blog post regarding Ready Player One.
http://10.10.167.18/retro/index.php/author/wade/

Exploitation
Browsing the Ready Player One blog post we saw that Wade has commented a word to remember parzival. This seems an interesting word, there may exist a user by the name of Wade and password parzival.
http://10.10.167.18/retro/index.php/2019/12/09/ready-player-one/#comment-2

We were not able to enumerate the RDP service due to the lack of credentials before. Now that we suspect that we have a set of credentials, let’s try to connect to the service. We will be using xfreerdp for accessing the RDP service. There exist many other tools that you can use for the same. We provided the username wade and password parzival.
xfreerdp /u:wade /p:parzival /v:10.10.167.18

We were able to connect to the RDP service with the credentials we suspected. As soon as we connect, we see that we have the user.txt file on the Desktop. We open the file to find the user flag as demonstrated below.

Privilege Escalation
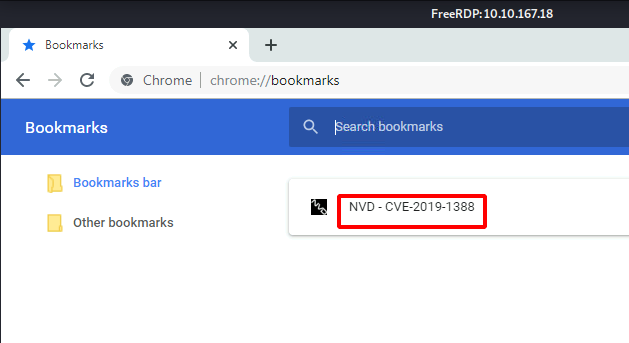
Now that we have the user flag and the access of the Wade user, we need to figure out the method for elevating access to the Administrator. Other than the text file we had two other icons on the Desktop. We opened Google Chrome and found a link bookmarked. It was for the Vulnerability CVE-2019-1388. Since we don’t have Internet Access on the target machine, we copied the link and opened it on our local machine. We found that it is a privilege escalation vulnerability inside the Windows Certificate Dialog. We read a couple of articles about it online to understand the vulnerability.
To exploit the vulnerability, we require an HTML help control file. We were about to download and transfer the file to the target machine when it came to us that we haven’t checked the Recycle Bin. During our previous assessment, we saw that there exist some files inside the Recycle Bin. We opened it to find the exploit file that is required to elevate privileges. We dragged and dropped it on the desktop.

To exploit, we need to run the hhupd file as Administrator and when asked for the password, we will open the certificate linked to the file. Opening the certificate will open an Internet Explorer session with elevated access. We will then use that to get a command prompt with elevated access.
Note: During our assessment, there were times where we were not able to open Internet Explorer. We contacted the author of the machine and we were told that this occurs because of creating the vulnerability. He suggested that we restart the machine and open an instance of Internet Explorer before running the hhupd file.
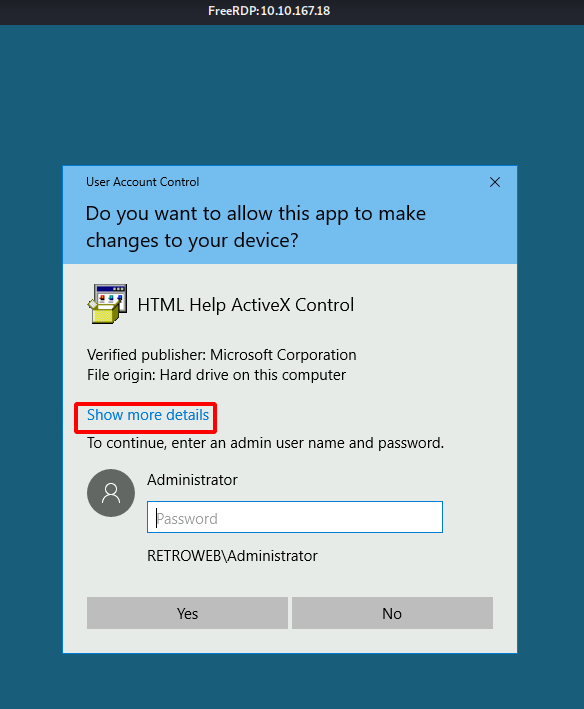
After getting the hhupd file to the Desktop, we right-click on the file and choose the Run As Administrator option. We are presented with a dialogue box asking for the password Administrator. Since we don’t have the password, we click on the Show more details option as demonstrated below.
Clicking on the Show more details option will expand the dialog box to show another option Show information about the publisher’s certificate. Click on that option as shown in the image below.

As soon as we click on the Show information about the publisher’s certificate option, we see a new window pop up. It has the properties for the certificate. Under the General tab, we see that this certificate was issued by VeriSign Commercial Software Publishers CA. There is a link to see the information about the Issuer. Click on the link as shown in the image below.

We are asked which software do we want to use for opening this link. We have the options to choose from Google Chrome and Internet Explorer. We can run the exploit using Google Chrome but it is not reliable. There might be times where you will get the session but it will not be an elevated one. So, we choose Internet Explorer.

This opens an Internet Explorer as the SYSTEM. Close the other windows and wait for the Internet Explorer to finish loading. You will get the This page can’t be displayed error since the machine is not connected to the internet. After it has finished loading click on the Cog icon on the right-hand side as shown in the image below.
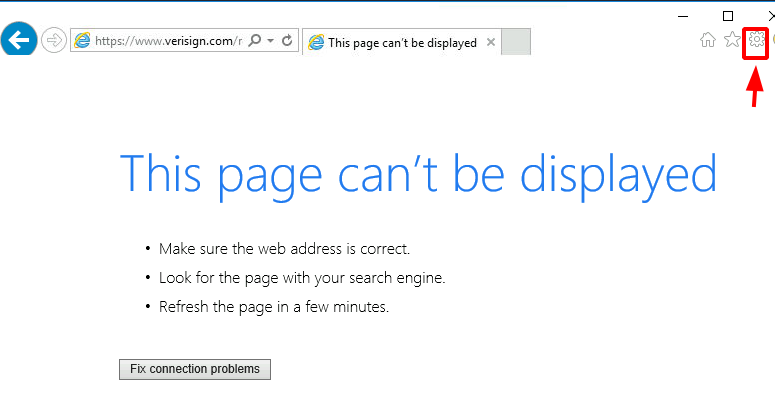
Clicking the Cog icon, a drop-down menu will appear, choose the File option. It will open another menu. Choose the Save as an option as demonstrated below.
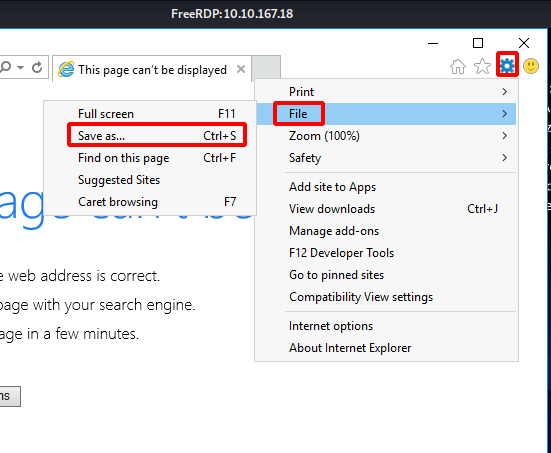
Clicking on the Save as an option will open a window where we are required to provide the location where we want to save the webpage. Browse the following location:
C:\Windows\System32
And type *.* in the File name as demonstrated below. This will allow for listing all the files and not just the .mht format file. We need to do this because we need the cmd.exe file listed here.

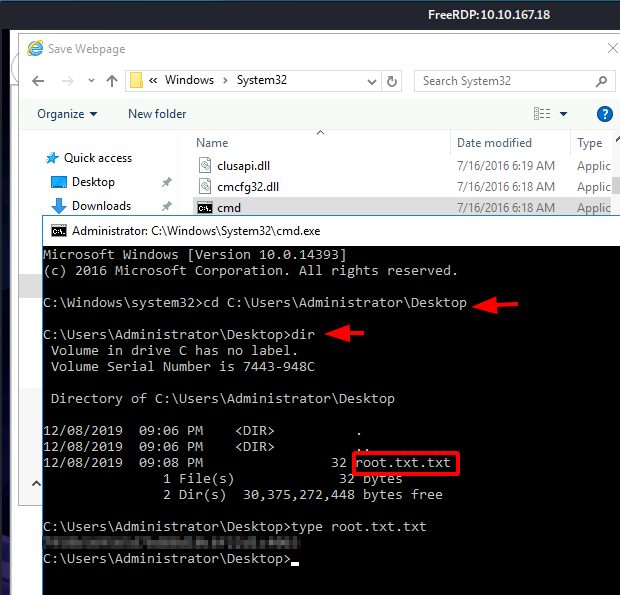
Scroll through the System32 directory and look for cmd.exe. Upon locating cmd, right-click on the file and choose the Open option from the drop-down menu. Don’t choose Run as Administrator here.

Clicking the Open option will open an instance of Command Prompt with elevated access. We can now move into the Administrator directory and browse the root.txt.txt file on its Desktop. Reading the flag contents using type command and conclude this machine.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn